CVE-2025-11560: Wordpress - Team Members Showcase Reflected XSS
Technical breakdown of CVE-2025-11560.
Overview
This post provides a technical breakdown of CVE-2025-11560, a reflected cross-site scripting (XSS) vulnerability discovered in the WordPress Team Members Showcase plugin.
For more information on the methodology and infrastructure used to discover this vulnerability, see my blog post: CVE Hunting Setup.
Affected Plugin: Team Members Showcase
Vulnerability Type: Reflected XSS
CVE ID: CVE-2025-11560
Affected Versions: < 3.5.0
Severity: 7.1/High
Status: Patched
Plugin Information
Team Members Showcase is a WordPress plugin with over 4,000 active installations. It allows users to display team members and staff profiles in various layouts such as grids, sliders, and tables. It is used by businesses, educational institutions, and organizations to create professional team showcases.
Vulnerability Details
Root Cause
The plugin does not properly sanitize and escape user input before outputting it back on the page, leading to reflected XSS.
Affected Parameter/Endpoint
Endpoint: /wp-admin/edit.php?post_type=wps-team-members&page=taxonomies&taxonomy=<XSS-payload>
Vulnerable Parameter: taxonomy
File: wps-team/includes/traits/taxonomy.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
// Source
public function add_taxonomies_menu() {
global $pagenow;
if ( $pagenow !== 'edit-tags.php' ) {
return;
}
$taxonomy = $_GET['taxonomy'];
$this->load_taxonomies_template( $taxonomy );
?>
<script>window.location.href.indexOf('/edit-tags.php') > -1 && document.querySelector(`a[href='edit.php?post_type=wps-team-members&page=taxonomies']`).parentElement.classList.add('current');</script>
<?php
}
// Sink
const data = {
action: 'wpspeedo_team_ajax_handler',
route: 'save_taxonomy_settings',
taxonomy: '<?php echo $taxonomy; ?>',
_wpnonce: '<?php echo wp_create_nonce( '_wpspeedo_team_nonce' ); ?>',
settings: $(this).serializeArray()
};
Vulnerability Flow:
- Source (Line 7): The
$taxonomyvariable is populated directly from the$_GET['taxonomy']parameter without any input validation or sanitization. This allows an attacker to inject arbitrary data through the URL. - Propagation: The unsanitized
$taxonomyvalue is passed through$this->load_taxonomies_template( $taxonomy )and remains accessible within the template scope. - Sink (Line 18): The
$taxonomyvariable is directly echoed into a JS context using<?php echo $taxonomy; ?>without proper escaping. Since this output occurs within a JS string literal, an attacker can break out of the string context and inject malicious JS code.
An attacker can craft a payload that closes the JS string context (e.g. </script><script>alert(1)</script>) to execute arbitrary JS code in the victim’s browser.
Proof of Concept
Prerequisites
- WordPress installation
- Team Members Showcase plugin version
< 3.5.0installed
Installing the plugin
1
ddev wp plugin install wps-team --activate-network
Exploitation Steps
Once the plugin is activated, navigate to Team > Taxonomies in the WordPress admin panel. You will see several tabs such as Groups, Locations, Languages, etc. Clicking on any of these reveals the taxonomy parameter we previously identified as vulnerable via source-code analysis. 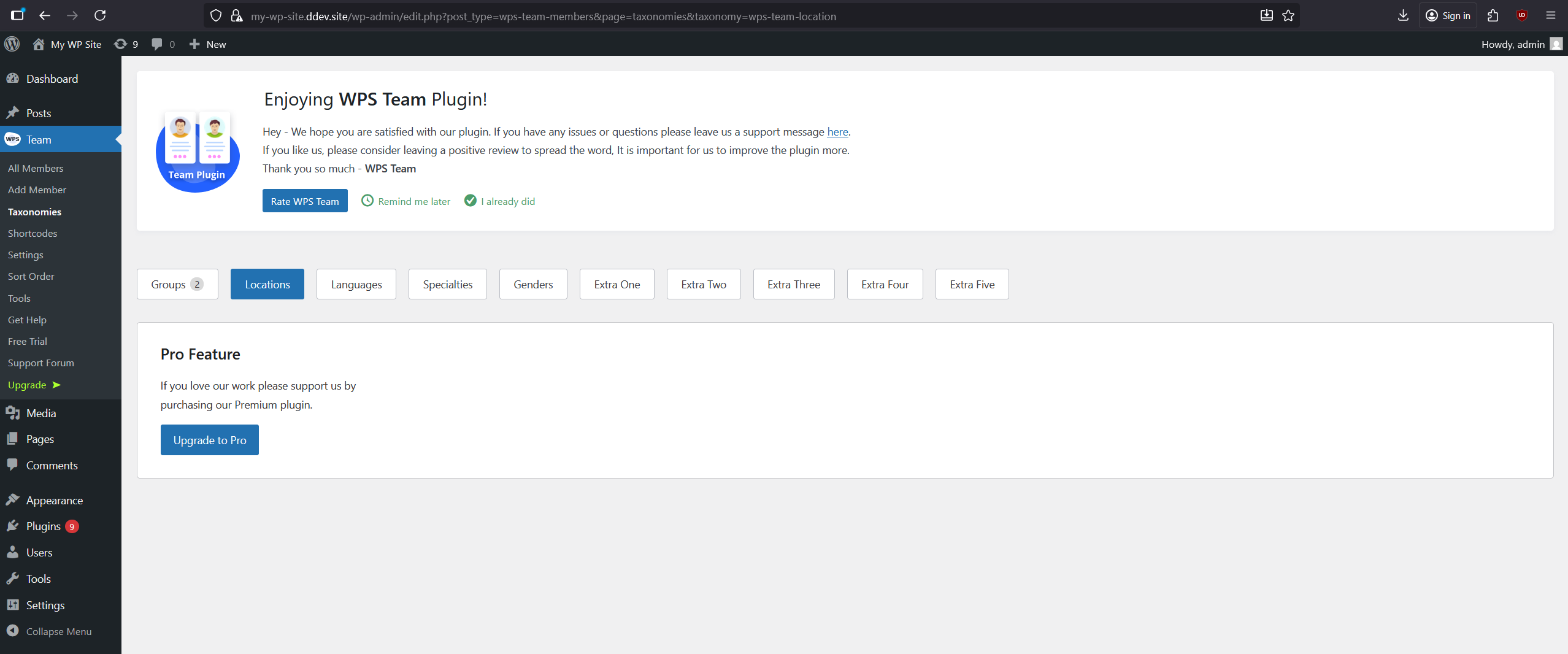
By closing the <source> tag and injecting a simple XSS payload into the vulnerable taxonomy parameter, we can trigger reflected XSS: 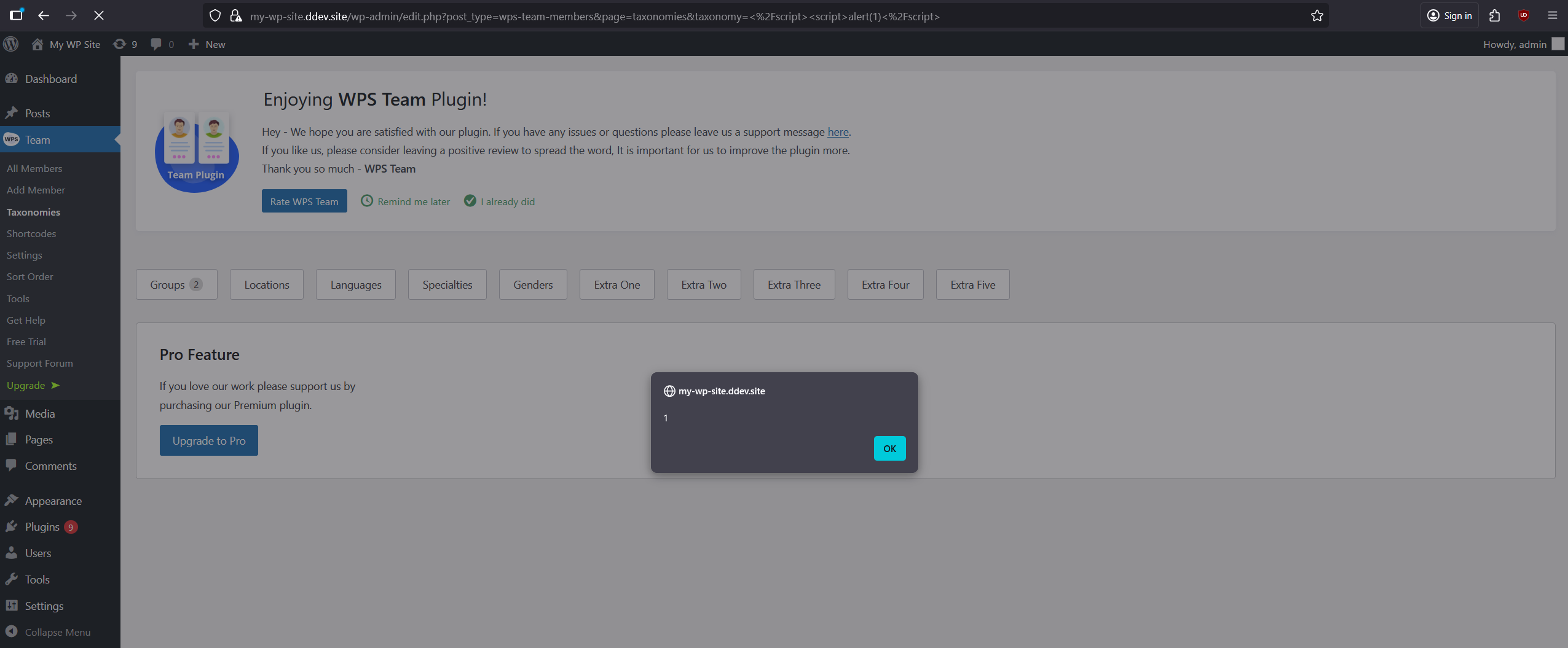
The payload needs to be URL-encoded!
Impact
What an attacker can achieve by exploiting this vulnerability:
- Session hijacking
- Cookie theft
- Phishing attacks
- etc.
Mitigation
- Update to version 3.5.0 or higher
Timeline
- [7/10/2025] - Vulnerability discovered
- [8/10/2025] - Vendor notified
- [9/10/2025] - CVE assigned
- [22/10/2025] - Patch released
- [22/10/2025] - Public disclosure
References
Disclosure: This analysis is for educational purposes only. Always test vulnerabilities in controlled environments with proper authorization.